The COVID-19 pandemic has changed people permanently—some became more fearful and suspicious, while others saw opportunities where no one thought.
Some people identified good options to help others and stop the spread of the virus, but others found opportunities to make money out of deception and dishonesty, especially in the cyber world.
Nicholas Davis, a cybersecurity professor and writer for the World Economic Forum, recently warned that the world should be prepared for a COVID-like “global cyber pandemic” capable of spreading faster and farther than any biological virus ever could, but with equal or more significant economic consequences.
It is not only the virus that will disrupt our lives, but its indirect consequences, such as more cases of cyber fraud and cyberattacks. As Davis puts it, a cyber pandemic is likely as inevitable as a future pandemic involving a biological disease.

What will happen after the COVID-19 pandemic is over? Will the cyber fraud schemes and cases continue to grow? And will this new cyber-disease pandemic continue to spread long after COVID-19 is gone?
We did some research to compile the most comprehensive and up-to-date list of global cyber fraud statistics to help paint a clearer picture of what’s to come (globally or regionally) and how we can prepare.Table of Contents
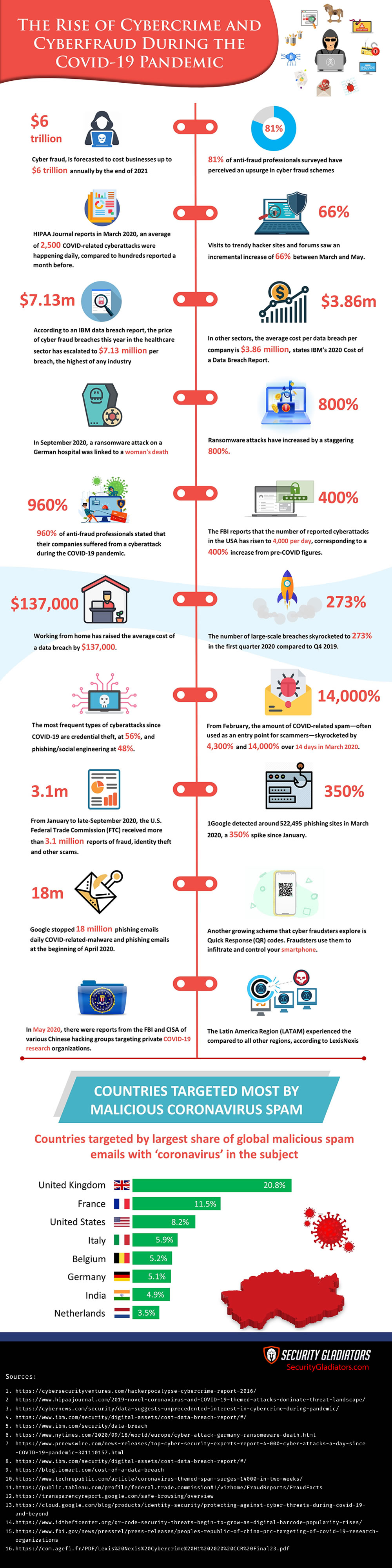
1. Alarming Global COVID-Related Cyber Fraud Statistics
Today’s cyber threat actors are motivated by one thing: To exploit and monetize virtual vulnerabilities. This is precisely what the COVID-19 pandemic brought—the so-called “new normal,” with new behaviors, activities and inclinations.
Since the beginning of 2020, as the world redirected all of its resources and focus to the health crisis, cyber fraudsters jumped to this new surface like sharks into free fish.
According to Interpol’s COVID-19 cyberthreats report, cybercriminals are attacking the computer networks and systems of individuals, businesses and organizations to capitalize on a time when cyber defenses are low. But the threat that has increased the most throughout the COVID-19 outbreak is cyber fraud.
A fraud analysis survey conducted by Statista in October 2020 shows a significant increase in cyber fraud risk expected over the next year globally. The below graph shows the increment of fraud risks observed since the beginning of the COVID-19 crisis.
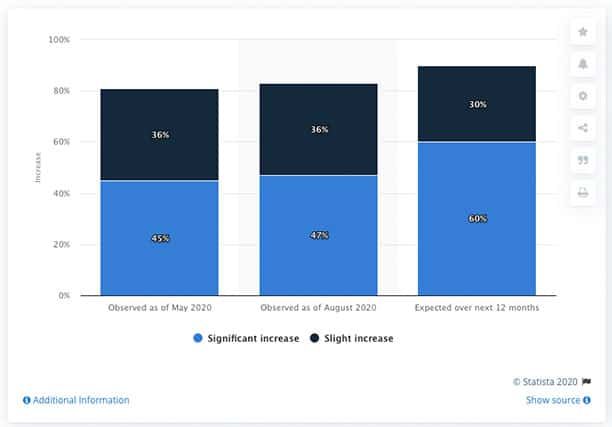
In May 2020, 45% of fraud examiners noticed a significant rise in cyber fraud risk. Also, 60% of fraud analysts expect substantial growth in cyber fraud risks over the next year.
If the trends are correct, the fraud analysis expects that by October 2021, cyber fraud is likely to increase from 30% to 60%.
A Year Full of Surprises
The topic of COVID-19 has been used in malicious campaigns globally, according to research from Trend Micro. Since the beginning of 2020, there have been around 300,000 detected virtual threats that take advantage of the COVID-19 crisis. The same report from Trend Micro also highlighted the coronavirus-related emails with malicious attachments sent to users as early as February 2020.
HIPAA Journal reports that while the COVID-19 pandemic was at its peak in March 2020, an average of 2,500 COVID-related cyberattacks were happening daily, compared to hundreds reported a month before.
Cyberattacks have increased 40% worldwide during the COVID-19 pandemic, and so has the willingness to learn how to execute them. Visits to trendy hacker sites and forums saw an incremental increase of 66% between March and May.
COVID-19’s contagion infection reproductive rate (R0) is being used as a reference to measure the rapid pace of cyberattacks. These are very alarming statistics. The rate (R0) of cyberattacks is estimated to be far above 27. To compare, the R0 of COVID-19 is anywhere between two and three (considering social distancing).
Social Engineering Experts

In May, a new group of cybercriminals identified as Vendetta impersonated Taiwan’s top infectious disease officials in an unlawful operation to steal sensitive information from national users. Vendetta sent spear-phishing emails to a high-ranking group of government officials, requesting them to pursue coronavirus tests. But the email attached a remote access hacking instrument.
Like many other hacker groups, this one emerged in the spring of 2020 amidst the COVID-19 pandemic. These types of groups are social engineering masters. They imitate government agencies in multiple languages, and so far, they have been found operating in Australia, Austria and Romania.
How Is the Health Sector Affected?
According to an IBM data breach report, the price of cyber fraud breaches this year in the healthcare sector has escalated to $7.13 million, the highest of any industry.
Although the health sector has been top-ranked for 10 years in a row, the current year’s figures increased 10.5% from last year, according to Security Intelligence, which is the most significant increment in all sectors. In other sectors, the average cost per data breach per company is $3.86 million, states IBM’s 2020 Cost of a Data Breach Report.
Note:
Over one week in April 2020, 450 active World Health Organization email addresses and passwords were leaked on the internet. The leaked data also included email addresses and passwords belonging to thousands of other people working on coronavirus response efforts.More Disturbing Global Cyber Fraud Statistics Related To COVID-19
The new remote work era also poses significant cybercrime and cyber fraud risks globally. In a survey conducted by the Ponemon Institute, 60% of respondents stated that their companies suffered from a cyberattack during the COVID-19 pandemic.
A Gartner survey from April 2020 found that 52% of compliance managers identified data breaches and cyber fraud as the most critical third-party threats for their companies.
Further, according to Palo Alto’s Unit42 threat report, around 1,767 high-risk coronavirus-related domain designations are generated per day. And in April, BleepingComputer reported that over 500,000 Zoom user accounts were hacked and traded on the dark web illegally.
2. What Has Changed: Pre-COVID vs. COVID

Since cybercriminals are taking advantage of the health crisis to capitalize on critical vulnerabilities, any analysis of 2020 cybersecurity threats must be examined through that lens. Cyber fraud attacks centered around the fear of COVID-19 increased by five times in March compared to the month before, according to Bitdefender Labs.
As more aspects of life, work and play moved online amid global lockdowns in early-2020, the number of cybercrimes had doubled from mid-2019 to July 2020.
As also highlighted in the previous section, cyberattacks have been most recurrent in the healthcare and financial sectors throughout the COVID-19 pandemic.
One cyberattack targeting Universal Health Services (UHS) shut down the systems of 400 healthcare facilities across the U.S. Reportedly, the attack did not successfully breach patient’s data. Still, it caused an interruption in treatments and delays in diagnoses.
Deathly Cybercrimes
Some cybercrimes during the epidemic have ended in a more tragic outcome: Death.In September 2020, a ransomware attack on a German hospital was linked to a woman’s death. The health facility had to shut down their system due to the ransomware, affecting incoming emergency patients.
Pre-COVID, cyber fraud operations against healthcare facilities usually only caused financial damage. But in 2020, the attacks have become more dangerous, putting patients’ health at stake while healthcare systems take a hit to their revenue and reputation.
Note:
According to research from Mimecast, email phishing attacks hit 90% of healthcare organizations over the last year. Ransomware attacks have increased even more, by a staggering 800%.Timeline: The FBI Reports
Data from the U.S. Federal Bureau of Investigation reveals deep insights into the ongoing cybercrime crisis running pervasively through the coronavirus pandemic.
The FBI reports that the number of reported cyberattacks has risen to 4,000 per day, corresponding to a 400% increase from pre-COVID figures.
The following timeline shows the progression of FBI cybercrime statistics pre-COVID to late-2020:
- Pre-COVID: In 2019, the FBI’s Internet Crime Complaint Center (IC3) registered 23,775 reports and around $1.7 billion in financial losses associated with Business Email Compromise (BEC) fraud schemes.
- Amid the COVID-19 pandemic: In April 2020, the FBI published a series of reports anticipating the rise of cyber fraud attacks due to the coronavirus pandemic. These attacks span various attack vectors, from PPE-related fraud schemes to cryptocurrency scams to online extortion.
- In October, U.S. authorities published a press release confirming the incremental increase in BEC fraud. These attacks targeted municipalities to purchase personal protective equipment or medical supplies to combat COVID-19.
New Demands in Online Banking
During the pandemic’s peak, 91% of the world’s inhabitants (or 7.1 billion people) were restricted from moving and experienced some form of lockdown. This is an entirely new scenario compared to 2019.
As a result, many financial services companies in the virtual identity network experienced a new level of demand for online banking requests from January to June 2020, according to a report from LexisNexis. More financial services customers went fully online for the first time, and mobile banking registrations grew exponentially at the start of the lockdowns.
Businesses’ New Battleground
This radical change forced an abrupt transition to remote work and life, which increased the virtual world’s complexity (and hostility). But businesses can’t adapt so quickly—countless small and mid-sized businesses, as well as large corporations, are still working to assess their cybersecurity needs and innovate in this area.
Now, over half of the world’s workforce is working remotely because of the pandemic. This change triggered countless security threats (some known and others unknown).
Employees with computers at home don’t have the same data policies as if they were working at the office. They also have a myriad of remote access methods. So, keeping data safe in this new scenario becomes complex.
Jaw-Dropping Remote Work Statistics
- 50% of business employees work remotely, a significant upsurge of 114% from the beginning of the pandemic. (Gartner, 2020)
- 47% of personnel cited interruptions as the cause for getting caught by a phishing scam while working remotely. (Tessian, 2020)
- 52% of legal and compliance managers identified third-party cyber risks due to remote working. (Gartner, 2020)
- Working from home has raised the average cost of a data breach by $137,000. (IBM, 2020)
- 76% of remote workers identify that working outside the office would increase the time to recognize and prevent a breach. (IBM, 2020)
- The number of large-scale breaches intensified steeply in strength and frequency from 2019 to 2020, skyrocketing to 273% in the first quarter. (IOMART 2020)
3. Cybercrime During the 2020 Covid-19 Pandemic Infographic
If you would like to use the infographic on your own web property then just copy and paste this code into your own site. Please always make sure to give credit back to us if you use it.
<figure class="aligncenter size-full"><img src="https://securitygladiators.com/wp-content/uploads/2020/12/Cybercrime-covid19-stats-infographic-sources-2.jpg" alt="An infographic featuring cyberfraud covid-19 statistics by SecurityGladiators.com" /><figcaption><em>Image via </em><a href="https://securitygladiators.com" target="_blank" rel="noopener"><em>SecurityGladiators.com</em></a></figcaption></figure>
4. Top Cyber Fraud Cases, Stats and Their Consequences
At the beginning of the pandemic, various security agencies and international organizations, including Interpol, Europol, the FBI and the United Nations, have been warning of the rise of cyber fraud. Many new malicious sites and phishing campaigns seek to steal personal information, sell fake COVID-19 treatments and offer health goods at inflated prices—many of which never arrive.
Trend Micro’s latest quarterly update released in November shows that in the first quarter of 2020, users had received 907,000 spam messages related to COVID-19. But by the third quarter, it increased to 3,818,307.
Additionally, from Trend Micro’s November report:
- During Q1, 737,000 new malware threats related to COVID-19 were detected, in contrast to only 15,513 during Q3.
- Hits on malicious URLs related to COVID-19 dramatically increased from 48,000 in Q1 to 1,025,301.
- Email threats increased 220% and malicious URLs increased 260% over just one month from February to March 2020.
- From Q2 to Q3, email threats decreased by 46.9%, but still, malicious URLs hits related to COVID-19 increased by 47.4%.
The Rise of Fake Medical Products
In March, Interpol seized around 34,000 counterfeit masks and many other counterfeit medical products through an international law enforcement operation dubbed Operation Pangea XIII. The agency also shut down over 2,500 retail websites, links, social media pages associated with selling illicit pharmaceuticals in 90 countries. The operation led to 121 arrests.
The lack of control, reliability and altered prescriptions are some of the life-threatening impacts posted by these stolen and fake products. Although it’s difficult to estimate the cost of cyber fraud during the pandemic, experts estimate these illicit operations could be worth billions of US dollars.
Warning:
The tools these cyber fraudsters are using are the same as ever. They are only tailoring the messages’ wording and widening their audience to spark interest, using the timely COVID-19 pandemic as a lure. The objective remains the same: Capture the victims’ attention and make them fall into the trap.But the rise of fear, isolation and desperation during the COVID-19 crisis only widens consumers’ defenselessness to these virtual fraud campaigns. Victims are anxiously working on getting vital goods that were often out of stock at the start of the pandemic.
The Cost of Cyber Fraud
Between Feb. 1 and mid-March 2020, ActionFraud registered approximately £970,000 in losses in the U.K. related to coronavirus scams. The majority of these cyber fraud campaigns were linked to fake online sales, including masks, baby formula, tampons and hand sanitizer.
These crimes have not only been happening in the U.K. but around the world. Cyber fraudsters used stolen identities to commit additional door-to-door crimes. And in some cases, they were trying to exploit quarantined victims by offering them groceries and medical supplies that were high in demand.
According to the Ponemon Institute Report:
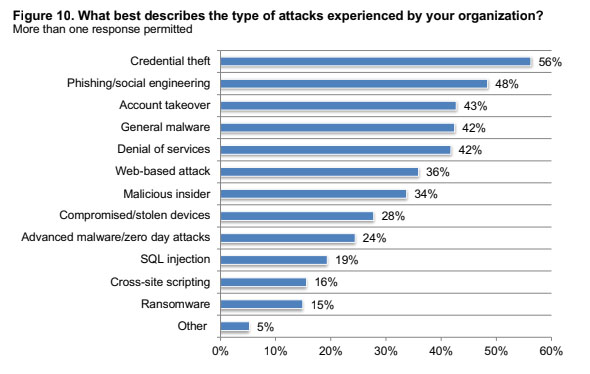
The most frequent types of cyberattacks since COVID-19 are credential theft, at 56%, and phishing/social engineering at 48%. Additionally, 58% of survey respondents said they suffered a compromise to their IT functions and faced interruptions in their operations and a loss of about $2.4 million. – Ponemon Institute, Cybersecurity in the Remote Work Era Report
Scams, BEC and Phishing Schemes
From the start of the COVID-19 crisis, the cyber world has experienced an abrupt increase in coronavirus-related scams. From February, the amount of COVID-related spam—often used as an entry point for scammers—skyrocketed by 4,300% and 14,000% over 14 days in March 2020.
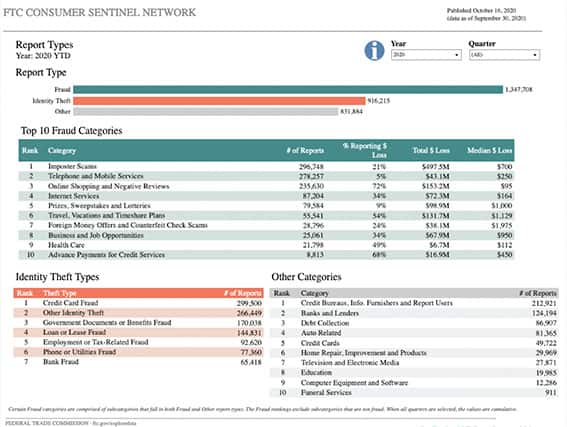
From January to late-September 2020, the U.S. Federal Trade Commission (FTC) received more than 3.1 million reports of fraud, identity theft and other scams. Of that number, imposter scams, telephone/mobile services scams, online shopping scams and internet services scams were the top four categories with the most reports this year.
Furthermore, a COVID-19 cyber threat analysis compiled by the United Nations Office on Drugs & Crime shows that in a single 24-hour period between April 14 to April 15, 2020…
- 170,387 spam emails were found to contain “corona” or “COVID” in the subject line.
- 19,694 unique IP addresses were used to send those emails.
- 8,391 unique email domains were used to send those emails.
- 583 of those emails were found to have an infected attachment. If the victim clicked on that attachment, the attacker could take full control of the target’s computer.
This massive cyber fraud scheme happened in just a day, and it was only related to emails. So, one could visualize the global effect of all other COVID-related cyber fraud schemes altogether.
Note:
Most email phishing scams are combined with one or more cyber fraud schemes. The majority will include malware, which takes advantage of unsuspecting victims by gathering personal credentials that can be used to cover tracks for criminal activities.Phisher’s Lure
The majority of phishing scams go after individual data. These cybercriminals use COVID-19 as a lure and mix it with online shopping and government aid, dating and romance, fake charities, and employment scams.
In a COVID-19 monitoring report, TrendMicro identified phishing email attempts claiming to be relief or healthcare organizations asking for donations in Bitcoin. The emails were sent by a group dubbed the “COVID19Fund,” posing to be associated with legitimate health organizations. They ask for aid and provide a cryptocurrency wallet where people could donate.
In August, Interpol reported that some of the top COVID-19 spear-phishing tactics contained scams pretending to be: Government officials, healthcare experts, coronavirus treatments and vaccines, contact-tracing applications and philanthropic organizations.
Other Shocking Phishing Facts and Stats
Cybercriminals send a high volume of emails in online fraud campaigns, often including about 150,000 to 175,000 emails at once. Some dark web sites sell coronavirus-related phishing email kits at different prices, ranging from $150 to $1,000. (UNODC, May 2020)
- Email phishing attacks increased abruptly by 667% from February to March. About 2% of the 468,000 worldwide email threats identified by Barracuda Networks were COVID-19-related. From those, 54% were identified as scams, 34% as brand impersonation attacks, 11% blackmail, and 1% as Business Email Compromise (BEC) exploits. (Barracuda Networks, March 2020)
- Google detected around 522,495 phishing sites in March 2020, a 350% spike since January. (Google Transparency Report, 2020)
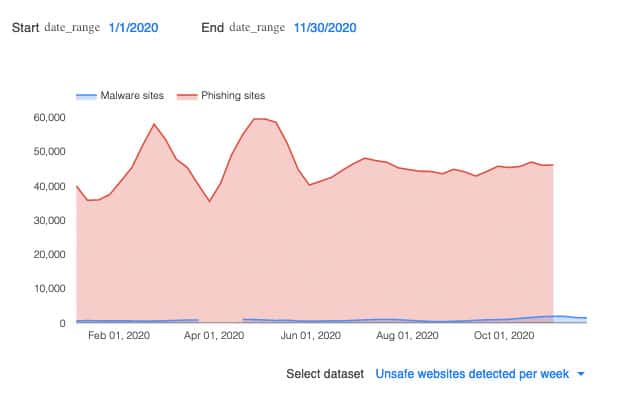
Malware, Malicious Websites and Other Cyber Fraud Schemes
Cyber fraud has been traditionally related to scams, BEC, phishing, credit card theft, and countless other criminal actions. But nowadays, the term has been used interchangeably with the word “cybercrime” and a wide range of cyberattacks, malware and malicious sites.
Recent trends show a sizable rise in website spoofing, scams that direct a victim to a fake website with malware, cross-site scripting and ransomware. These scams focus on stealing personal information to be used in illegal operations.
From February to March, an Interpol partner registered a 569% increase in malicious domain registrations, including malware and phishing, as well as a 788% spike in high-risk registrations.
Note:
According to the U.N.’s Office on Drugs & Crime, around 9,000 coronavirus-themed domains were registered online by the end of March 2020. Some of those domains contain malicious links meant to scam unsuspecting visitors.But phishing emails are still the easiest and most popular channels of online fraud. Google stopped 18 million daily COVID-related-malware and phishing emails at the beginning of April 2020.
Email phishing attempts are often accompanied by malware. Cyber fraudsters usually attach malware in emails targeted to healthcare organizations and enterprise firms to gain access or monetary gain. In June, a report published by Malwarebytes researchers emphasized the increase in scamming, phishing and other schemes that ended in COVID-related malware attacks known as AveMaria and DanaBot.
COVID-19-related ransomware attacks have also been a common cyberattack vector during the pandemic. One pervasive trend is the targeting of Remote Desktop Protocol (RDP) systems, which are often used by teams working from home in the pandemic. One study found that more than half of ransomware attacks also involved RDP.
New Deadly Ransomware Variants
In the U.S., some previously dormant hacker groups have restarted operations and developed a novel type of scheme: “Double-extortion” ransomware attacks.

Trickbot, although recently deactivated by Microsoft in October 2020, became a popular way to send numerous double-extorsion ransomware attacks to companies through DDoS-for-hire services. Emotet and Ryuk, other ransomware programs, were the most common ransom-DDoS systems used to target healthcare facilities during the pandemic.
Double extortion schemes also exploited the widespread fears around COVID-19. According to research from CheckPoint, double extortion schemes became a trend in the first quarter of 2020.
According to Zohar Pinhasi, a cyber counter-terrorism expert and founder of the cybersecurity firm MonsterCloud, reports inform that ransomware attacks are up 800% during the COVID-19 pandemic. From the perspective of the cybercriminals behind these attacks, Pinhasi says, “they have stepped on a gold mine.”
Emerging Threats: Cryptojacking and Fake QR Codes
Cryptojacking (also known as malicious cryptomining) is a new online threat. It initially comes as a trustworthy application or service, but underneath, it infects the device with malware that aims to utilize its computing resources to mine cryptocurrency.Cryptojacking is also leveraged from COVID-19 fear. Kaspersky has reported a global increment of cryptojacking incidents during this year. At the end of Q1, Singapore experienced a threefold increase in cryptojacking (about 11,700 attempts), becoming the most significant increase in the area. Cybersecurity experts believe that this increase in cryptojacking cases could be tied to the number of people working from home due to the COVID-19 lockdowns.

Another growing scheme that cyber fraudsters explore is Quick Response (QR) codes. COVID-19’s new contactless reality has increased the use of physical QR codes for menus, prices and other pieces of information. Fraudsters are looking for ways to leverage QR codes as an attack channel.
According to a consumer survey from MobileIron:
- 72% have scanned a QR code in the past month.
- 54% have noticed an increase in QR codes since the pandemic began.
- 67% believe QR codes make life more comfortable during the epidemic.
- 58% want to see QR codes used more broadly in the future.
- 48% have concerns about QR codes but use them anyway.
Mobile devices are an attractive entry point for hackers due to their ease, fast response and trustworthy characteristics. Victims handle mobiles without too much care and are less alert than with their computers. Criminals will print fake QR codes and post them around to direct victims to fake websites and trap them.
Fraudulent QR code attacks have been continuously increasing worldwide, but India has seen daily incidents leveraging the COVID-19 pandemic. Even before the pandemic, police in Belgium have previously warned about the security of using QR codes to buy second-hand products online.
5. Analysis of Relevant Global COVID-Related Cyber Fraud Statistics (By Country)
By the end of 2019, more than 50% of internet operators had suffered from some type of cyber fraud scheme, which usually consisted of malicious social media, email spam and malware. According to 2019 data from Statista, India had the largest percentage of users that suffered some sort of cyberattack (80%), followed by the U.S. at 61% and France at 60%.
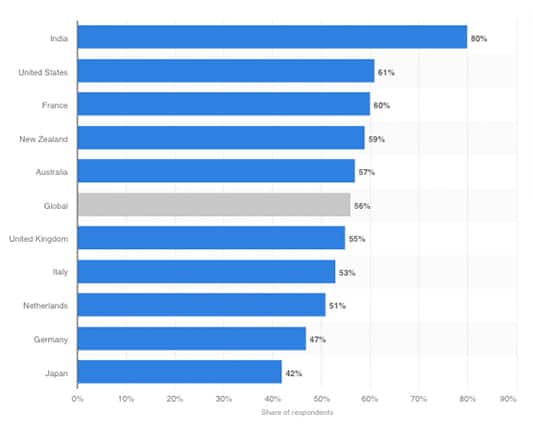
At the time of this global ranking pre-pandemic, COVID-19 hadn’t crossed the minds of hackers, fraudsters and victims alike. But the pandemic has now changed how people behave in their own countries and communities. Global statistics (post-COVID-19) from different security agencies indicate that COVID-related cyber fraudsters establish a de facto standard in the cybersecurity world.
So let’s have a closer look at the COVID-19 and post-COVID-19 related cyber fraud and cybercrime statistics.
The below map from Bitdefender shows the number of COVID-related threats reported by a unique IP address, not the number of reports.
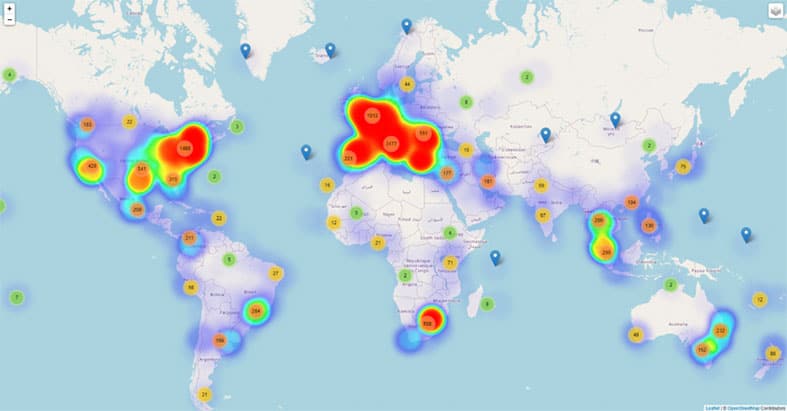
These numbers establish a connection between the countries that suffered the most during the COVID-19 pandemic.
Cyber fraudsters leveraged the anxiety and terror that COVID-19 originated, especially in places like the U.S., Spain, Italy, the U.K. and South Africa. These criminals grounded their scams around fake news and ignorance to direct users to malicious sites to install malware.
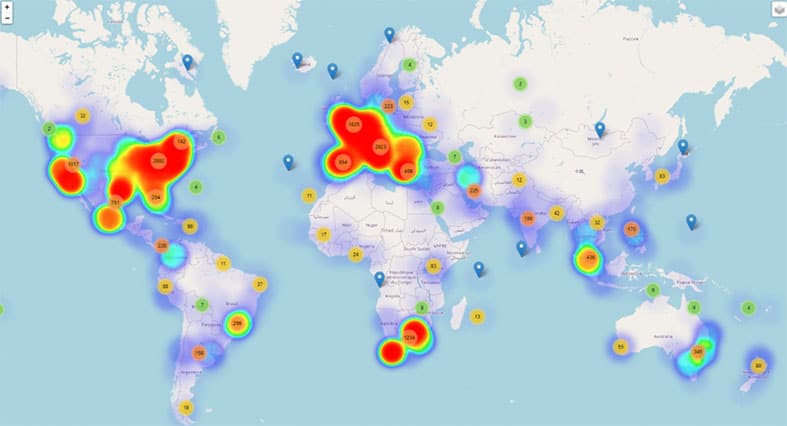
As soon as April hit with the pandemic spreading its course, the cases of coronavirus-related threats soared throughout these countries.
The top 10 affected countries with COVID-themed threats in April were:
- United States
- South Africa
- Italy
- Canada
- United Kingdom
- Spain
- Germany
- France
- Australia
- Mexico
Note:
Notice that the Asia-Pacific (APAC) region is out of the top 10. But, there was a similar tendency like APAC for the rest of the world: The increment of reports of cyber threats related to COVID-19 during March and April. Like other regions, APAC was also hit with an overload of information and misinformation about COVID-19 in the form of spam, phishing, fake news and attack tactics.Rise of COVID-Themed Cyberattacks
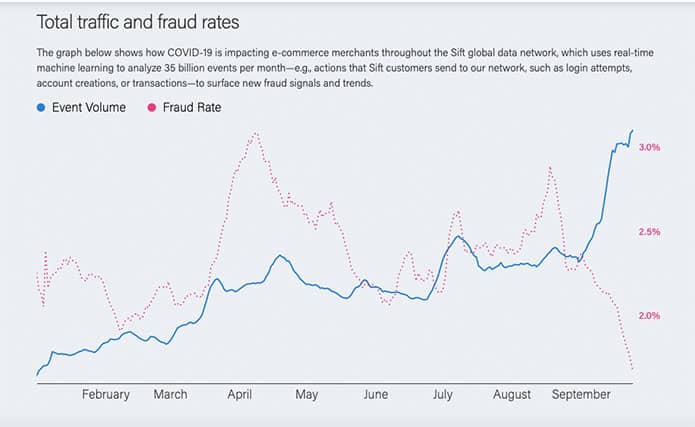
The graph below via Sift shows the impact of global cyber fraud in e-commerce related to COVID-19. The chart reports how coronavirus data shifts are directed to cyber fraud during the pandemic’s peak months.
According to the graph, Sift received more “event volume” and reduced the fraud rate at the beginning of September.
In line with the international COVID-related cybercrime statistics, TrendMicro’s users across the globe also experienced a shocking increase in cyber threats:
- Malicious email attacks increased from 4,028 to 897,711 in March.
- Malicious URLs rose from 9,497 to 34,197.
- Malicious files also grew from 67 to 534.
TrendMicro analysts identified the top countries that experienced the highest increment of COVID-related spam attacks (with malicious attachments) from January to March 27, 2020:
- The United Kingdom increased by 20.8%
- France increased by 11.5%
- The United States increased by 8.2%
- Italy by 5.9%
- Belgium by 5.2%
- Germany by 5.1%
- India by 4.9%
- The Netherlands by 3.5%

Remote Desktop Protocols (RDP) attacks relate to the pandemic also experienced similar behavior.
Data from Kaspersky and the following graph by SecureList shows a global increment of 41% RDP brute-force attacks starting at the beginning of the pandemic in March 2020.
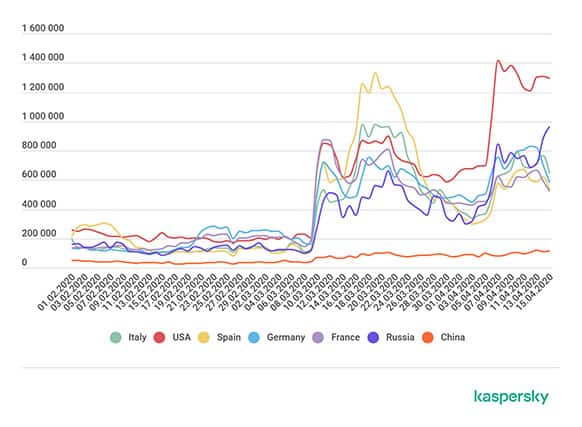
The countries most affected by RDP-brute force attacks included:
- Italy
- Spain
- US
- Germany
- France
- Russia
These are the same countries that were initially impacted by the coronavirus. In the U.S., RDP attacks grew exponentially from about 200,000 daily in January to 800,000 in March and 1.4 million in April.
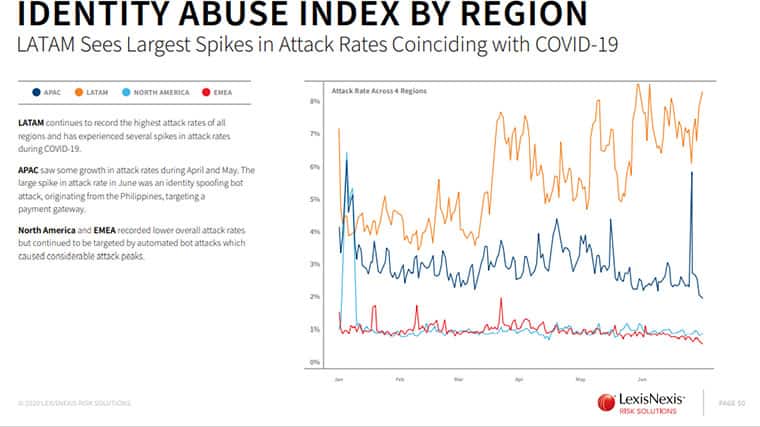
Identity Abuse Threats (Per Region)
Identity abuse threats have also increased globally since the end of March 2020. The Latin American Region (LATAM) region appears to be the most significant in this area. The growth of identity abuse threats in the LATAM region goes with the increasing rates of COVID-19 cases.
Contrary to global COVID-related cyber threats, identity abuse crimes did not vary much in other regions, such as North America, Europe and the Middle East.
Cryptojacking Per Region
The following cyber frauds increased significantly during the first and second quarters of 2020: Cryptojacking, mobile threats, Botnets (DDoS), infostealers, banking attacks and ransomware. But according to the graph below by Statista, 22% of cyber threats worldwide accounted for crypto-jacking, with APAC the region most commonly affected by this type of attack.
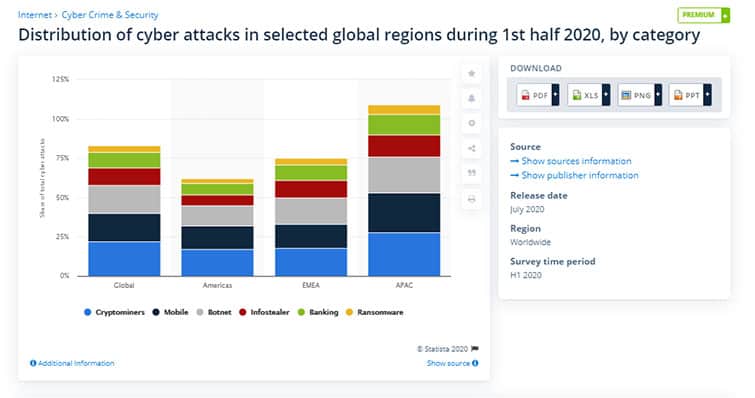
LATAM, APAC and EMEA have all experienced growth in automated bot attacks. Additionally, the APAC region reported the most significant incidence of botnet threats (see the below graph LexisNexis). According to Interpol, most attacks measured by “Botnet” size are sent from Japan, India and Australia.
In May, amid the first COVID-19 wave of infections in Europe, multiple supercomputer centers in Scotland, Switzerland, Germany and Spain supporting academic research about COVID-19 were shut down for a few days due to cryptojacking infections.
Larger Attack Surfaces and Powerful Attack Vectors
With the larger attack surface, thanks to the emerging IoT (Internet of Things) devices, work-from-home policies and access to mobile broadband, cyber fraudsters can generate more powerful and recurrent attacks. Their scams and threats also pose higher risks that have become more difficult to alleviate.
Some more regional and country-specific COVID-19 cybersecurity stats:
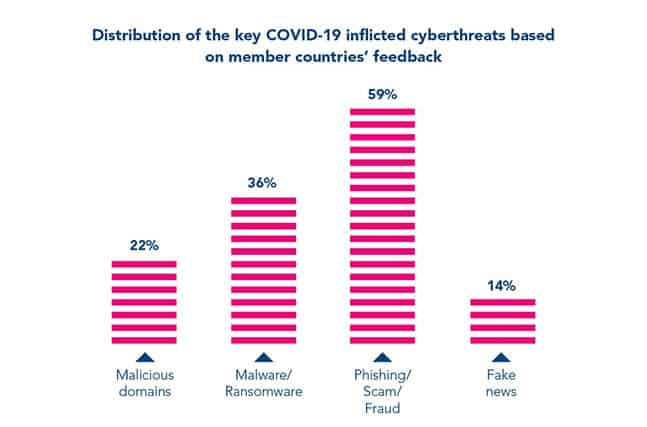
- According to an Interpol report, the most significant COVID-19-themed cyber threats in the Association of Southeast Asian Nations (ASEAN) are phishing/scam/fraud at 59%, malware/ransomware at 36%, malicious domains at 22% and fake news at 14%.
- Gartner forecasts that North America (Canada and the U.S.) will spend close to $191 billion on government IT.
- According to the Microsoft 365 Defender Threat Intelligence Team, South Korea was the first and largest focus for targeting cyber fraud and COVID-19 related scams. This was due to the virus’s early arrival.
- In the U.K., the collective loss from COVID-related scams sums up to £11 million.
- In May 2020, there were reports from the FBI and CISA of various Chinese hacking groups targeting private COVID-19 research organizations.
- The Latin America Region (LATAM) experienced the highest attack rates compared to all other regions, according to LexisNexis. The peak in attack correlates with the onset of the COVID-19 (from March to June 2020). Countries like Brazil and Mexico move up dramatically regarding the most massive volumes of attacks.
- The U.K. is facing a GDPR data privacy challenge related to the COVID-19 testing and tracing program.
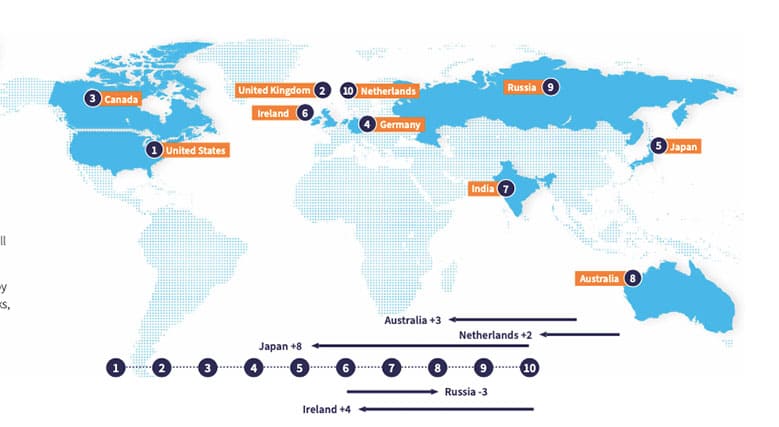
Top Countries with Covid-19-Related Malicious Detections 2 Jan -25 nov 2020
The below map and table shows the COVID-19-related Malicious File Detections. This is data provided by McAfee Advanced Programs Group (APG) and relates to cyber frauds or phishing that attempt to lure targets into malicious links or to download files. These links/files contain trojans most of the time.
TOP COUNTRIES WITH COVID-19-RELATED MALICIOUS DETECTIONS
| RANKING | COUNTRY | STATS |
| 1 | United States | 1,302,262 |
| 2 | Spain | 1,188,506 |
| 3 | Estonia | 399,869 |
| 4 | South Africa | 372,299 |
| 5 | India | 356,349 |
| 6 | Italy | 299,600 |
| 7 | Germany | 226,099 |
| 8 | Brazil | 187,916 |
| 9 | Ukraine | 176,507 |
| 10 | Saudi Arabia | 128,904 |
| 11 | China | 104,981 |
| 12 | Turkey | 104,006 |
| 13 | Israel | 88,105 |
| 14 | Belgium | 33,015 |
| 15 | Mexico | 30,921 |
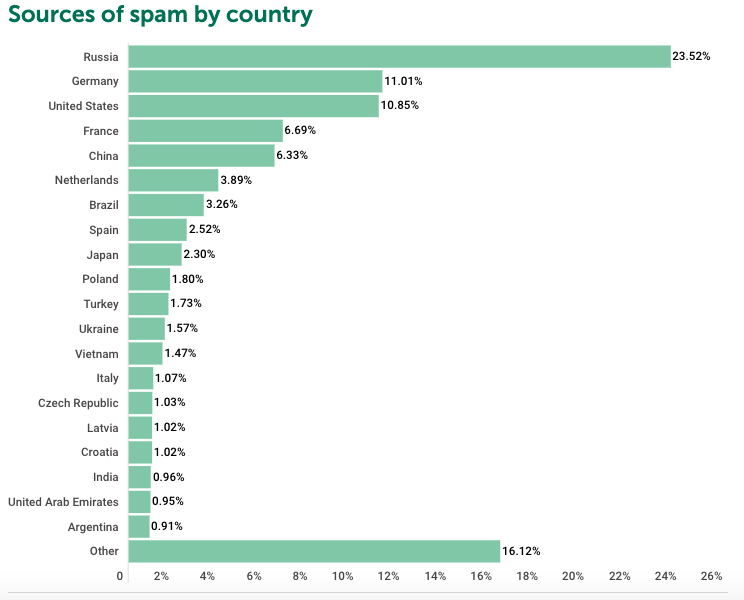
Top Countries targeted by Spam and Phishing During COVID-19 Times.
Data from Securelist, Kaspersky’s cyber threat research and reports. Spam and Phishing started to use COVID-19 as a theme during Q2, but picked up in Q3. Cyber Fraud statistics here show correlation with all COVID-19 timings for each country.
Data and Image Source: Secure List’s First Quarter, Second Quarter and Third Quarter.
First, Second, and Third Quarter’s Spam by Country.
TOP COUNTRIES TARGETED BY SPAM
| Quarter 1 | Quarter 2 | Quarter 3 | ||||||
|---|---|---|---|---|---|---|---|---|
| Ranking | Country | % | Ranking | Country | % | Ranking | Country | % |
| 1 | Russia | 20.74% | 1 | Russia | 18.52% | 1 | Russia | 23.52% |
| 2 | United States | 9.64% | 2 | Germany | 11.94% | 2 | Germany | 11.01% |
| 3 | Germany | 9.41% | 3 | United States | 10.65% | 3 | United States | 10.85% |
| 4 | France | 6.29% | 4 | France | 7.06% | 4 | France | 6.69% |
| 5 | China | 5.22% | 5 | China | 7.02% | 5 | China | 6.33% |
| 6 | Brazil | 3.56% | 6 | Netherlands | 4.21% | 6 | Netherlands | 3.89% |
| 7 | Netherlands | 3.38% | 7 | Brazil | 2.91% | 7 | Brazil | 3.26% |
| 8 | Vietnam | 2.55% | 8 | Turkey | 2.89% | 8 | Spain | 2.52% |
| 9 | Spain | 2.34% | 9 | Spain | 2.83% | 9 | Japan | 2.30% |
| 10 | Poland | 2.21% | 10 | Japan | 2.42% | 10 | Poland | 1.80% |
| 11 | India | 2.20% | 11 | Poland | 2.21% | 11 | Turkey | 1.73% |
| 12 | Ukraine | 2.15% | 12 | Vietnam | 2.01% | 12 | Ukraine | 1.57% |
| 13 | Japan | 1.94% | 13 | Ukraine | 1.82% | 13 | Vietnam | 1.47% |
| 14 | Croatia | 1.88% | 14 | Hungary | 1.11% | 14 | Italy | 1.07% |
| 15 | Turkey | 1.50% | 15 | India | 1.09% | 15 | Czech Republic | 1.03% |
| 16 | Great Britain | 1.13% | 16 | Great Britain | 1.09% | 16 | Latvia | 1.02% |
| 17 | Lithuania | 1.10% | 17 | Czech Republic | 1.07% | 17 | Croatia | 1.02% |
| 18 | Czech Republic | 1.07% | 18 | Italy | 1.06% | 18 | India | 0.96% |
| 19 | Indonesia | 1.01% | 19 | Croatia | 0.99% | 19 | United Arab Emirates | 0.95% |
| 20 | Argentina | 0.99% | 20 | Latvia | 0.90% | 20 | Argentina | 0.91% |
| 21 | Other | 19.67% | 21 | Other | 16.18% | 21 | Other | 16.12% |
Quarter 2
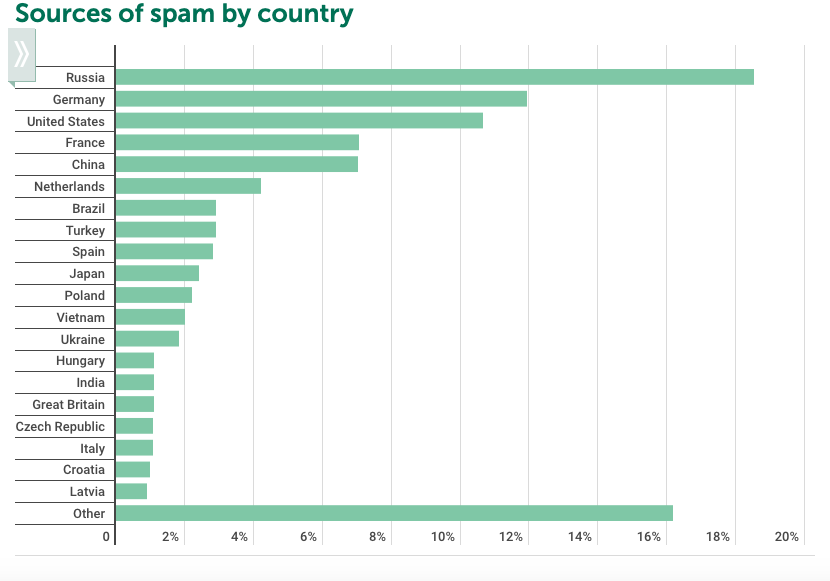
Quarter 3
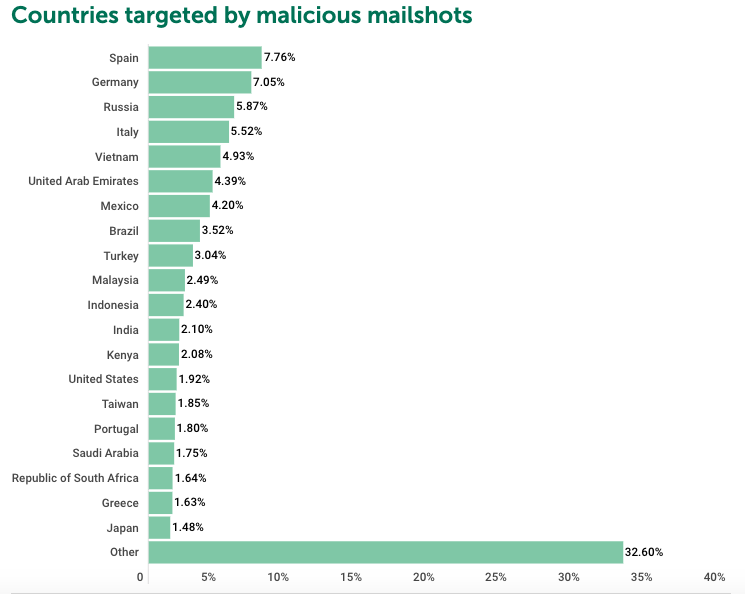
Second and Third Quarter’s Top Countries Targeted by Malicious Mailshots
| Quarter 2 | Quarter 3 | ||||
|---|---|---|---|---|---|
| Ranking | Country | % | Ranking | Country | % |
| 1 | Spain | 8.38% | 1 | Spain | 7.76% |
| 2 | Russia | 7.37% | 2 | Germany | 7.05% |
| 3 | Germany | 7.00% | 3 | Russia | 5.87% |
| 4 | Vietnam | 5.75% | 4 | Italy | 5.52% |
| 5 | Italy | 4.97% | 5 | Vietnam | 4.93% |
| 6 | United Arab Emirates | 4.37% | 6 | United Arab Emirate | 4.39% |
| 7 | Mexico | 3.62% | 7 | Mexico | 4.20% |
| 8 | Brazil | 3.44% | 8 | Brazil | 3.52% |
| 9 | Turkey | 2.76% | 9 | Turkey | 3.04% |
| 10 | Malaysia | 2.49% | 10 | Malaysia | 2.49% |
| 11 | Taiwan | 2.28% | 11 | Indonesia | 2.40% |
| 12 | India | 2.22% | 12 | India | 2.10% |
| 13 | Indonesia | 2.21% | 13 | Kenya | 2.08% |
| 14 | Greece | 2.06% | 14 | United State | 1.92% |
| 15 | United States | 1.67% | 15 | Taiwan | 1.85% |
| 16 | Portugal | 1.66% | 16 | Portugal | 1.80% |
| 17 | Hong Kong | 1.65% | 17 | Saudi Arabia | 1.75% |
| 18 | South Africa | 1.58% | 18 | Republic of South Africa | 1.64% |
| 19 | Kenya | 1.54% | 19 | Greece | 1.63% |
| 20 | Japan | 1.40% | 20 | Japan | 1.48% |
| 21 | Other | 31.59% | 21 | Other | 32.60% |
Quarter 2
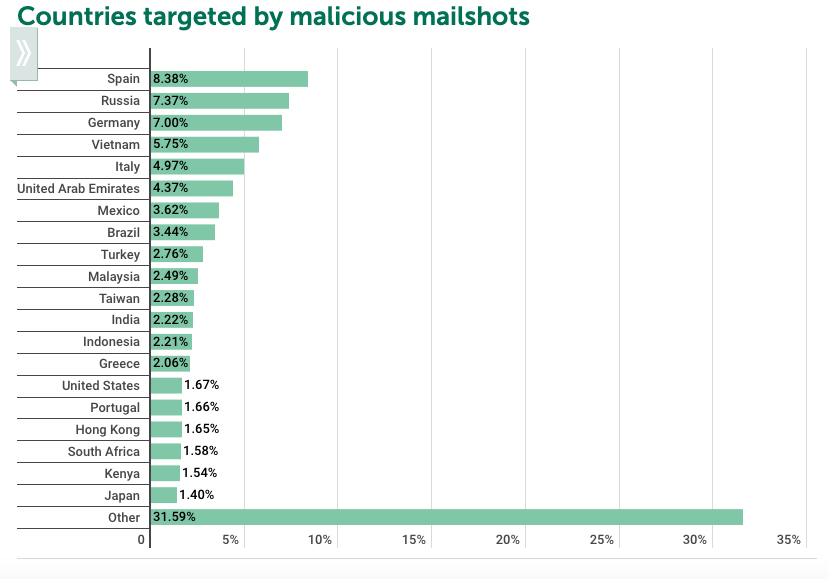
Quarter 3
Phishing Attacks. Quarter 1, 2, and 3.
TOP COUNTRIES TARGETED BY PHISHING ATTACKS
| Q1 | Q2 | Q3 | ||||||
|---|---|---|---|---|---|---|---|---|
| Ranking | Country | % | Ranking | Country | % | Ranking | Country | % |
| 1 | Venezuela | 20.53% | 1 | Venezuela | 17.56% | 1 | Mongolia | 15.15% |
| 2 | Brazil | 14.95% | 2 | Portugal | 13.51% | 2 | Israel | 15.24% |
| 3 | Australia | 13.71% | 3 | Tunisia | 13.12% | 3 | France | 12.15% |
| 4 | Portugal | 12.98% | 4 | France | 13.08% | 4 | Brazil | 11.85% |
| 5 | Algeria | 12.12% | 5 | Brazil | 12.91% | 5 | Nepal | 10.85% |
| 6 | France | 11.71% | 6 | Qatar | 11.94 % | 6 | Cameroon | 10.87% |
| 7 | Honduras | 11.62% | 7 | Bahrain | 11.88% | 7 | Portugal | 10.85% |
| 8 | Greece | 11.58% | 8 | Guadeloupe | 11.73% | 8 | Belgium | 10.83% |
| 9 | Myanmar | 11.54% | 9 | Belgium | 11.56% | 9 | Australia | 10.72% |
| 10 | Tunisia | 11.53% | 10 | Martinique | 11.34% | 10 | New Zealand | 9.58% |
Trends and Final Words
Although the internet is a fantastic tool for collaboration, research and communication, it is also a playground for scammers, phishers and hackers. And as the internet expands and grows its surface, criminals have more opportunities to be creative and develop more phishing attacks, scams and other types of cyber fraud.

We might have powerful artificial intelligence and deep learning algorithms to stop known scams and threats. Still, nothing could have ever predicted something like the COVID-19 pandemic, and of course, its aftermath.
Following the trends from COVID themed scams, there is no doubt that cyber fraud segments like phishing scams, fake QR codes, ransomware and malware will not disappear but will become more automatic and case-targeted.
These scams will even use the same tools that were made to fight against them: Artificial intelligence.
Additionally, with the rising interest in using the dark web for hacking, we will likely see criminals building strong underground communities, impenetrable by the authorities. Cyber frauds will be further developed by the minds of expert black-hat hackers and pushed outwards by the army of script kiddies.
Final Words
- The COVID-19 virus has not only provoked an extraordinary global pandemic but a noteworthy increment in cyber fraud. Fraudsters are taking advantage of victims amidst the global crisis and monetizing widespread fear and doubt.
- Globally, all regions and countries have experienced a significant increase in COVID-related cyber fraud and threats during the pandemic, targeting authorities, businesses and individuals.
- Globally, the most popular COVID-19 related fraud schemes are phishing scams and virtual counterfeit of healthcare products and services.

