Distributed Denial of Service (DDoS) attacks refer to a class of cyber attacks that use different techniques to block users from accessing a particular service or website. DDoS attacks have risen to prominence in recent years as the number of organizations affected by DDoS attacks has gone up consistently. DDoS attacks are important because if an organization that relies on servers connected to the internet does not take proper measures against DDoS attacks, DDoS attacks can disrupt all business operations.
Business owners and home users alike need to have a basic understanding of how distributed denial of services attacks work and what mitigating measures can be taken. Even after taking the right precautions, companies and individual users must understand that distributed denial of service attacks are impossible to completely prevent. Even the security measures that reduce the chances of a successful denial of service attack are costly and require a great amount of effort to manage. Nevertheless, to make sure that the organization or a network can respond quickly and appropriately to distributed denial of service attacks, it is very important to know as much about distributed denial of service attacks as possible.

Table of Contents
How Does a DDoS Attack Work?
Distributed Denial of Service attacks or DDoS attacks work by attacking a service or website using multiple compromised devices simultaneously to overwhelm target networks and make those networks or servers inoperable.
To get started, hackers usually compromise a large number of IoT devices. To do that, the hackers will usually target individual devices with malware. Once the malware infects an IoT device, the hackers gain complete control of the device and can give the compromised IoT device commands remotely. After that, the hackers connect that compromised IoT device with another compromised IoT device. Eventually, these compromised devices make a botnet.
Note:
The botnet can contain any number of compromised IoT devices, from a few hundred to thousands. Moreover, these IoT devices can become a part of a botnet from any corner of the globe. Once a threshold botnet size is reached, the hackers can use the botnet to send malicious requests to target services or a single target service.Such malicious requests are in such huge numbers that they overload the target networks’ or servers’ CPU resources and server RAM. When the target network or server is unable to cope with the sudden increased traffic, the network or server becomes clogged or shuts down.
How Long Does a DDoS Attack last?

The length of a DDoS attack can be anywhere from a minute to weeks. Knowing what is a DDoS attack is not just about the methods hackers use to launch DDoS attacks. Some types of DDoS attacks take longer to gain the critical mass required to overwhelm networks and hence develop properly. Other types can quickly damage a network and finish the objective in a short amount of time.
A report from Radware recently mentioned that around 30% of cyber attacks lasted for less than an hour. Another report from TechRepublic mentioned that DDoS attacks can last up to around 330 hours. Convert that to days and 330 hours is equal to around 14 days. Generally, the more complex a DDoS attack, the longer the DDoS attack lasts. That’s not just because the DDoS attack is complex but also because new types of DDoS attacks are difficult to counter and guard against.
What Are the Motivations of Attackers for DDoSing?

Anyone with malicious intent, sufficient resources and the right personnel can launch DDoS attacks. Of course, any type of DDoS attack would eventually have a hacker or a team of hackers behind the DDoS attack. The motivation behind the DDoS attack can and does vary.
- Sometimes someone may launch a DDoS attack with no reason behind the DDoS attack. That is, other than trying to learn a concept or improve hacking skills.
- At times the attacker can come from within an organization where an employee mistakenly disrupts communications which leads to significant downtime. This can happen if the network administrator does not configure a server properly. In other words, not all DDoS attacks have malicious intent behind them.
- Hackers launch DDoS attacks to draw an individual’s or organization’s resources away from another type of attack which may be taking place at the same time. Since resources would be spent dealing with the DDoS attack, any other type of attack’s success rate is likely to be higher.
- Newly trained hackers may target a network or an organization with a DDoS attack to improve the attack, expand current capabilities and make incremental changes to their DDoS attack. Doing this helps hackers launch more potent future DDoS attacks against the same organization or another unrelated target.
- Activists can sometimes learn how to launch DDoS attacks and then target government departments and companies that do not carry out business according to the hackers’ ideals. This is especially true when the target organization is political. Banks and think tanks are also targeted because of such motivations.
- Hackers who do not get their compensation after a successful ransomware attack may launch a DDoS attack against the ransomware victim to coerce the victim to pay up.
- Competitors in various industries may hire DDoS services through the dark web to gain an advantage over a rival company or product developer by taking out their services or website.
- Nation-states sometimes launch DDoS attacks against other countries to bring down critical infrastructure to hurt the economy of the target country.
- Online gangs can also learn the skills necessary to launch DDoS attacks against rival gangs or unsuspecting targets. Such gangs continue to vandalize each other’s operations and infrastructure to gain more influence in a given area. Genuine businesses that have nothing to do with online gang wars can also get caught up in gang wars and suffer from DDoS attacks.
- Seasoned hackers may launch DDoS attacks against law enforcement agencies that are trying to disrupt their operations.
Which Industries Are Being Targeted?

DDoS attacks target companies working in various industries, the foremost of which is online retail. Online retailers get the brunt of DDoS attacks for obvious reasons that include hackers wanting to disrupt online retailers’ operations so they lose business. Online retailers can also lose future customers which may affect their growth rate at the end of the year. This is where competitors are prone to hiring hacking teams that can launch DDoS attacks to get ahead and profit.
Hackers also target online retailers to damage their reputations. Once customers and business associates know their payment details and personal data are not safe with the targeted online retailer, they will not return for future business. The type of data hackers are usually after includes personal details, financial records and purchasing history.
Hackers also launch DDoS attacks against online retailers to get their hands on intellectual property. This way, hackers can either sell the data or offer the intellectual property data to a competitor or a start-up business which cuts down the time newcomers take to catch up to established brands.
Another industry that hackers target with DDoS attacks is the financial services industry. The obvious reason to attack the finance industry is to steal funds and discover other ways to realize a financial gain. As previously mentioned, hackers target financial services to damage their reputation and access their data which is usually confidential and highly sensitive.

Disrupting financial service’s infrastructure pays off greatly since companies in the finance industry typically deal either with big clients or important ones. The type of data hackers are usually after in the case of financial services is personal data, credit card information and the usernames and passwords of personnel who can authorize funds transfer or access confidential information.
Just like in the case of online retailers, financial instructions also sit on terabytes of transaction data, risk analysis algorithms and other future product data. Hackers want to steal that information to sell it.
Governments are not safe from DDoS attacks either. Hackers target government departments to stop them from providing services to their citizens and carrying out their administrative work. The kind of data hackers are after is usually related to the intellectual property along with Social Security numbers and other personal details. Any research that has been funded publicly must have a record with a specific government department. Nation-state hackers launch DDoS attacks to shut those systems down and steal state secrets. Other common reasons why hackers target government agencies include eavesdropping, committing espionage and stealing technology.
Moreover, online activities generate a massive amount of data. Hackers target cloud services to steal that data. Other typical reasons include eavesdropping, causing damage to the service’s reputation and preventing cloud services from serving their clients.

Generally, hackers target any and all companies that are in the online services industry. Whether that is Netflix (offering streaming services), The New York Times (an online news publication) or the internet service provider itself. The reason why hackers target such services is to access the data they have stored on their servers. Apart from that, eavesdropping and damaging the reputation of the target company are always reasons hackers launch DDoS attacks against companies that have servers connected to the internet.
ISPs offer essential services that allow people to connect to the wider internet and complete tasks. Hackers sometimes want to disrupt the environment surrounding such activities to either benefit financially from all the data ISPs have on their users or to set things up for future attacks.
The online gaming industry is another favorite DDoS hacking target. Sometimes online video game streamers end up on the wrong end of a DDoS attack either as collateral damage or as a target of a group of fans that disagree with the streamer on an issue. Other times, hackers get paid to disrupt specific online gaming sessions so that a group of professional e-athletes gains an advantage over their rivals. Potentially, an esports organization could pay hackers to hack another esports organization and steal data related to player salaries, team tactics and practice schedules to both gain a competitive advantage and use the data to negotiate better deals for themselves from sponsors.
What Is a DDoS Attack?

A Distributed Denial of Service attack or DDoS attack is a class of cyber attacks where hackers use multiple devices that work together to attack a single target device or network. The main feature of a DDoS attack is a botnet which is a collection of compromised devices that hackers can give commands to and have it attack a given network, server or device.
The method hackers use to make DDoS attacks effective is to compromise a large number of vulnerable devices connected to the internet to create a botnet. Then the hackers use that botnet as the source of generating extra traffic that will eventually flood the target network or server until the target is clogged or shuts down. Once a network or a server gets jammed, there is no way for the service in question to serve regular users with legitimate requests. This leads to loss of business, revenue and future customers.
This is important:
Individuals and companies need to know more about DDoS attacks because DDoS attacks are getting more complex and are increasing in number. The other reason to give DDoS attacks proper consideration is the massive shift of business to the digital world because of various external factors such as the cost of maintaining a brick-and-mortar store and pandemics.DDoS attacks have gained more importance in the eyes of cybersecurity firms and experts because of how DDoS attacks have evolved. DDoS attacks now have the ability to make use of multiple attack vectors. The vast majority of current DDoS protection programs simply are not prepared for these types of cutting-edge DDoS attacks. Now DDoS attacks clog entire networks and can come from multiple sources. DDoS attacks are more potent than ever as new DDoS attacks can leverage thousands of compromised devices and IP addresses.

Another reason it is important to know more about DDoS attacks is the fact that modern DDoS attacks can continue to do damage to a target network for days rather than hours. In any competitive industry, that is a long enough period of time to seriously hit the target company financially.
As mentioned before, the reputational damage that a firm can suffer during and after a DDoS attack is another important reason to not only know more about DDoS attacks but to actively guard against them. In the age of social media, it doesn’t take long for a firm under attack to not only start losing current customers but also prospective ones. Employees working for firms that do not take DDoS attacks seriously may also think twice about switching to a different firm to enhance their resume.
What Does DDoS Mean?

The term DDoS stands for Distributed Denial of Services. DDoS attacks are a type of Denial of Service (DoS) cyber attack. DDoS attacks get their name from the fact that DDoS attacks make servers and websites unavailable to genuine user requests, hence the term “denial of service”. That is in stark contrast to normal cyber attacks that aim to compromise the security measures installed to protect the target website or server. However, modern DDoS attacks can sometimes act as a distraction so that other types of cyberattacks have an easier time bringing down the security infrastructure of the target company or website.
What Are the Types of DDoS Attack?
The DDoS attack types are zero-day DDoS attacks, Advanced Persistent DoS, NTP Amplification, Application-level DDoS attack, Slowloris, Fraggle attack, Smurf attack, Ping of Death attack, HTTP Flood, UDP Flood and SYN Flood attack. The most popular DDoS attack is SYN Flood because SYN Flood exploits the vulnerabilities present in the TCP protocol.
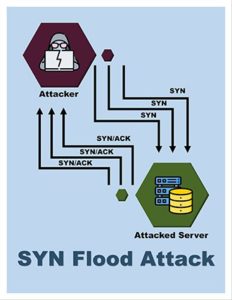
More concretely, the SYN Flood DDoS attack takes advantage of the three-way handshake process that has to happen in a TCP connection. Essentially, in order to initiate the handshake, the user’s device or the host contacts the desired server to receive a response in the form of a synchronized message. This synchronized message is sometimes shortened to SYN message.
The server in question then sends a message back to the host confirming that the server has received the message. That server message is known as the acknowledgment flag or ACK flag.
Once a server sends the ACK message back, this action closes the connection.
Things change in a SYN Flood DDoS attack where hackers use spoof messages and send those messages to the server. Because of these spoof messages or connection requests, the server is unable to close the connection as the hacker’s device refuses to respond. Eventually, the server is bogged down and the website it serves goes down along with it.
What Are the DDoS Attack Tools?
DDoS tools are used to launch DDoS attacks against individuals and organizations.
The foremost of these tools is called DDoS Attack. DDoS Attack is a tool that hackers and testers use to launch base DDoS attacks. The DDoS Attack tool comes in the form of an application and can help hackers scan multiple sources looking for event logs and can detect various Distributed Denial of Service interactions.
The purpose of the DDoS Attack tool is to detect control servers and check if any commands are being communicated to them. DDoS Attack offers real-time response, users have the option of filtering IPs or timeframes among many other parameters. This tool can also detect other kinds of malicious activities that can take place between a control server and command.
There is the Low Orbit Ion Cannon (LOIC) that is an open-source DDoS stress testing tool. LOIC allows the user to carry out UDP and TCP layer DDoS attacks via a WYSIWYG interface. The tool has spawned derivatives that allow users to launch DDoS attacks via their web browsers. LOIC is free and helps network administrators test network resilience. LOIC can create DDoS attacks completely online. Of course, users first have to go through an authentication process to prove they own the website they want to test.
RUDY is a DDoS attack tool that belongs to the type “low and slow.” With the help of a point-and-click user interface, the owner of the website can launch DDoS attacks easily. RUDY allows the user to open multiple HTTP POST requests. To launch the DDoS attacks, the connections have to remain open for a long period of time. RUDY and similar DDoS attack tools build slowly over time but eventually overload the server or network for a successful DDoS attack.

DDoS Simulator or DDoSIM is one of the many DDoS attack tools that users utilize to create DDOS attacks and test a target server. Users can use DDoSIM on a Linux machine as well. DDoSIM has the ability to calculate the capacity of the target server and then indicates the level of application-specific DDoS attack required to overwhelm the server. DDoSSIM can also use TCP connections to launch DDoS attacks against specific servers. Using a random network port, DDoSIM can flood the network with TCP connections.
The High Orbit Ion Cannon (HOIC)is another type of DDoS attack tool that has, in many cases, replaced the previously mentioned LOIC tool. The HOIC DDoS attack tool is actually an enhanced version of LOIC. The HOIC DDoS attack tool offers more customization options and DDoS capabilities. HOIC can launch DDoS attacks by exploiting the HTTP protocol and supports 50 people attacking a target server together. This makes DDoS attacks via HOIC DDoS attack tools difficult to protect against.
History and Examples of DDoS Attacks

DDoS attacks are so popular now that no one needs the full form of the acronym DDoS anymore. But that wasn’t always the case. Even the earliest DDoS attacks had the capacity to disrupt vital digital and hardware infrastructure. Generally speaking though, DDoS attacks have primarily brought down networks. Historically, for companies, DDoS attacks have led to a loss of revenue and disgruntled customers.
Even though DDoS attacks have always had damage potential, DDoS attacks have still managed to evolve to a great extent. Each iteration of DDoS attacks is more potent and more dangerous. Moreover, one can’t deny the effort hackers have put into making DDoS attacks much more destructive and technologically more advanced. That being said, DDoS attack targets have not helped themselves either.
While hackers moved to find new and more lucrative targets, their targets such as companies and individuals, moved more of their activities online. Moreover, the digital ecosystem saw the rise of IoT devices that had vulnerabilities that were waiting to be exploited. Today, there are more smart devices connected to the internet than regular laptops or desktops. All the while, hackers kept fine-tuning their DDoS attacks. DDoS attacks moved from attacking small businesses and charity organizations to big banks and WiFi routers. Botnets of old contained standard devices but now could count IP cameras, refrigerators and set-top boxes as botnet members.
Note:
The earliest DDoS attacks relied on botnets that consisted of abandoned personal computers and servers only. Now, botnets can count on members such as coffee machines, dishwashers and robot vacuum cleaners.DDoS attacks have not only evolved in terms of how they develop and what devices they leverage for different targets. DDoS attacks have also evolved in terms of how much damage they do to an organization or a target server and the type of damage they inflict. Moving into the future, DDoS attacks are likely to get even more potent and damaging.

Perhaps the earliest cyberattack that could be loosely considered a form of DDoS attack was the Morris Worm. The Morris Worm shocked the world in 1988 when a student, Robert Tappan Morris, wrote a program to approximate the size of the internet at the time. The program jumped from one computer to another computer via the internet and started to copy itself on its own. In the end, the Morris Worm managed to infect over 60,000 devices and brought down ARPANET, and hence entered the domain of DDoS attacks.
In 2012, two entities that can only be described as online gangs engaged in DDoS warfare which resulted in DDoSed websites for both the government and the opposition. Moving back to 2007, another DDoS attack in Russian cities Astrakhan and Adygea took down the internet intermittently. The interruption to internet communications not only irked the citizenry but also government officials and law enforcement agencies who did not have any idea of the perpetrators. The DDoS attack of 2007 in Russia lasted for an entire month and flooded the network with 10 Gbps junk traffic with the help of botnets as well as peer-to-peer file transfer services. The hackers behind the attacks were never identified. However, the DDoS attack of 2007 did make policymakers in Russia and other countries take DDoS attacks seriously.
What Are Important Examples of DDoS Attacks?

The most important examples of DDoS attacks are numerous but the latest of the big DDoS attacks which was launched against Amazon deserves a mention before any other example. While the pandemic had the whole world reeling, hackers launched a massive DDoS attack against Amazon Web Services in February of 2020.
Hackers targeted a specific AWS customer which the company did not identify. Hackers used a Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection attack to accomplish the feat. Hackers increased the traffic towards the target customer’s IP address around 70 times by amplifying methods and exploiting weak CLDAP servers. The attack on Amazon Web Services flooded the network with 2.3 terabytes of data per second and lasted for three days.
Moving back two years to 2018, hackers launched a giant DDoS attack against GitHub. GitHub acts as a code repository for software developers. Hackers flooded the Github network with 1.35 terabits of junk traffic per second. This led to a massive DDoS attack which was the biggest of its time. As a result of the attack, GitHub had to go through intermittent outages. GitHub eventually recovered because the service had signed up for a DDoS protection service.

The Dyn attack in 2016 is perhaps the DDoS attack that has garnered the most media attention. Dyn is one of the biggest DNS service providers in the world. Hackers launched a DDoS attack against Dyn with the help of compromised IoT devices. As mentioned before, hackers usually have to make a botnet of these compromised devices and have to use some sort of malware to infect the IoT devices before launching a DDoS attack. In the Dyn attack, hackers use the Mirai malware to compromise devices, create a botnet and launch the Dyn DDoS attack.
What Is a Yo-Yo Attack?

A Yo-Yo attack is a type of DDoS attack where hackers exploit the features that cloud services provide to attack organizations. The target organizations have usually signed up to use one of the available cloud services. Cloud services provide a reactive auto-scaling feature via load balancer systems. Hackers exploit this by increasing the volume of junk traffic over a period of time.
Yo-Yo attacks have become important because hackers are using Yo-Yo attacks to target more and more websites. If the website owners and network administrators along with cloud service providers do not take the necessary security measures against Yo-Yo attacks, hackers will likely cause more damage more regularly.
The other reason why Yo-Yo Attacks are important is because of the interest hackers have shown in using Yo-Yo Attacks to damage websites and services. Compared to DDoS attacks, Yo-Yo attacks do not cost much to launch and do not require much expertise to execute. Generally speaking, though there are variations, DDoS attacks are volumetric attacks in the sense that DDoS attacks flood the target network with high volumes of traffic. Some DDoS attacks increase the volume of extra traffic suddenly while others increase traffic levels over time. In Yo-Yo attacks though, hackers only send extra junk traffic in bursts.

Hackers also use cycles of low extra traffic and high extra traffic. This makes it difficult for any network to detect if there is a DDoS attack happening. In any case, such cycles, which are where Yo-Yo attacks derive their name, make it easy for hackers to target websites and services.
In terms of harm, Yo-Yo attacks are a bit different from normal DDoS attacks. Yo-Yo attacks not only want to make a target website or service unavailable but also aim to damage the target service in financial terms. Since the target website or service uses cloud services, an increased amount of traffic usually means the target website or service has to pay the cloud service more for the increased resource usage. Cloud services charge based on usage rather than a flat fee for their services. With Yo-Yo attacks, the target website can end up paying a lot of money to its cloud services providers.
Note:
Yo-Yo attacks can be mitigated by hiding traffic scaling statistics. An attacker needs to know how much scaling has taken place to stop the DDoS attack and then eventually turn it on again once the traffic goes to a predetermined average level. If the owner of the website can hide scaling information, this would disrupt any preparations attackers might have made before launching the attack.Another way to mitigate against Yo-Yo DDoS attacks is to not use the default values for downscaling and upscaling when it comes to the cloud service provider’s load balancing mechanism. Doing so also disrupts any plan attackers might have made of when to stop sending extra junk traffic and when to start again. Of course, hackers can always move away from assuming the default values and analyze how the target server responds to some junk traffic to approximate resource consumption levels. If the junk traffic has activated the auto-scaling load balancing feature then the target website or server would respond very quickly to any extra requests. On the other hand, if the target server does not respond quickly enough to the junk traffic then that means the auto-scaling feature either has not been activated or has gone back to a state of being deactivated.
Websites and cloud service providers can work together to come up with a strategy to hide the details regarding the system’s response times. For example, cloud services and websites can build a plan where if there is some malicious traffic then the system can deliberately slow down response times to that particular traffic. The website can continue to serve genuine user requests in a normal manner if that is what the security systems in place have determined.
Using a reverse proxy, a decent web security tool can hide the backend architecture of a website or service. This also helps to hide information regarding response times and other steps that hackers always find useful to make Yo-Yo attacks more potent.
What Are the DDoS Attack Tools?
The list of DDoS attack tools is given below,
- Tor’s Hammer
- XOIC
- LOIC
- HOIC
- SolarWinds Security Event Manager
- Slowloris
- PyLoris
- RUDY
- GoldenEye
What Is the Difference Between a DoS and a DDoS Attack?
The differences between a DoS vs. DDoS attack are given below:
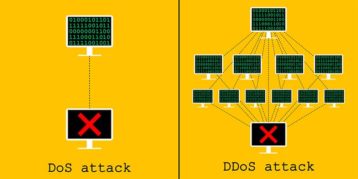
- DoS attacks do not use multiple connections to overwhelm the target network, system or server while DDoS attacks do.
- Since DDoS attacks use multiple compromised devices to send junk traffic towards the target server, it is difficult to know where the DDoS attack is originating and operating from.
- DDoS attacks can overwhelm networks with high junk traffic or requests more easily and at a higher scale than DoS attacks.
- DoS attacks may use a script to target a network or server while DDoS attacks use a botnet to be effective.
- DDoS attacks send malicious data packets from multiple locations and devices while DoS attacks do it from a single device or location.
- DDoS attacks are fast while DoS attacks are slow.
How to Recognize and Prevent Distributed Denial-of-Service Attacks
Even though DDoS attacks are evolving at a rapid pace, not all DDoS attacks are state-of-the-art. Moreover, many network security tools can handle the vast majority of DDoS attacks. Therefore, the first step should be to get the right hardware and network security tools to guard against DDoS attacks. More specifically, network firewalls should be used. Load balancers and web application firewalls can also be used to guard against application-layer DDoS attacks and protocol DDoS attacks.
The market now offers specialized hardware that can guard against common DDOS attacks and keep network resources available for genuine user requests. More hardware resources are always a good way to prevent DDoS attacks from completely breaking the system and shutting down the target network or website for a long period of time.
The other thing organizations and website owners need to pay attention to is the location of the servers. Ideally, servers should be located in multiple data centers. It also helps if the data centers themselves are not on the same network. Making sure there are no singular points of failure or bottlenecks can also help protect against DDoS attacks.
This is important:
Precautions against DDoS attacks are all about architecture resilience. Planning and preparing for DDoS attacks before they happen are the two critical safety measures against DDoS attacks. The planning should be about identifying vulnerabilities in the system or network and then preparing to fix those vulnerabilities before a DDoS attack happens.
The general tips to guard against DDoS attacks include keeping everything on the system updated. Fix all the security issues and bugs and develop a plan to identify such problems as quickly and early as possible.
Anti-malware programs and network monitoring tools always help to detect average traffic levels and then compare them with suspicious traffic levels. The necessary protection measures can then be taken if a discrepancy is noticed. Response teams should be placed not only in the IT department or to assist the network administration department but also the data center that contains all the service’s or website’s resources. Some of the tools that come in handy to take preventive measures against DDoS attacks include SolarWinds Security Event Manager, Imperva and Cloudflare.
What Is the Relation Between Proxy and DDoS Attacks?

First, what is a proxy? A proxy server acts as a bridge between the user of the proxy and the wider internet. Instead of using one’s own device to communicate with different entities on the internet, the user utilizes the proxy server.
When it comes to DDoS attacks though, hackers use proxy servers to make themselves anonymous and then launch DDoS attacks. More specifically, hackers use anonymous proxies to turn a standard denial of service attack, which has a single point of origin, into a distributed denial of service attack. Proxies can enable hackers to use thousands of different IP addresses to become part of a botnet and launch DDoS attacks.
Proxy services also help hackers mask the actual source of the DDoS attack which in turn makes it harder for security tools to detect if the traffic is part of a DDoS attack. Access control lists also become less effective when the hacker uses a proxy to launch DDoS attacks.
With proxy services, blacklisting IP addresses also becomes useless since hackers can change IP addresses at any time. Generally speaking, proxy services help hackers launch DDoS attacks more easily and evade mitigation measures.
What Is the Relation Between OSI Model and DDoS Attacks?

The Open Systems Interconnection (OSI) model is an architecture consisting of different layers stacked one above the other that enable the process of communication between two endpoints. Each layer in the OSI model is dependent on the other layers for the process of communication to take place. In simpler terms, the OSI model offers a standard protocol that different devices can use to communicate over the internet.
The relation between the OSI model and DDoS attacks is that DDoS attacks usually exploit vulnerabilities present in the OSI model layers. Different types of DDoS attacks target different layers in the OSI model. But almost all DDoS attacks have the same purpose which is to either crash a device, network, server, service or program or at least slow it down to a halt. Some DDoS attacks use the OSI model layers to fill up the target network to capacity so that all genuine requests are turned down.

