A man-in-the-middle attack happens when cybercriminals intercept communications between two entities. Cybercriminals may do so by eavesdropping on the conversation or altering the traffic as it travels between two participants. After successfully gaining access to the conversation, the cybercriminals then try to steal information or login credentials.
Cybercriminals also use man-in-the-middle (MitM) attacks to corrupt data, spy on participants or disrupt communications. MitM attacks have evolved to interfere with legitimate networks in several ways. Hackers can now use malicious networks to listen to any conversation and intercept any data sent through that network.
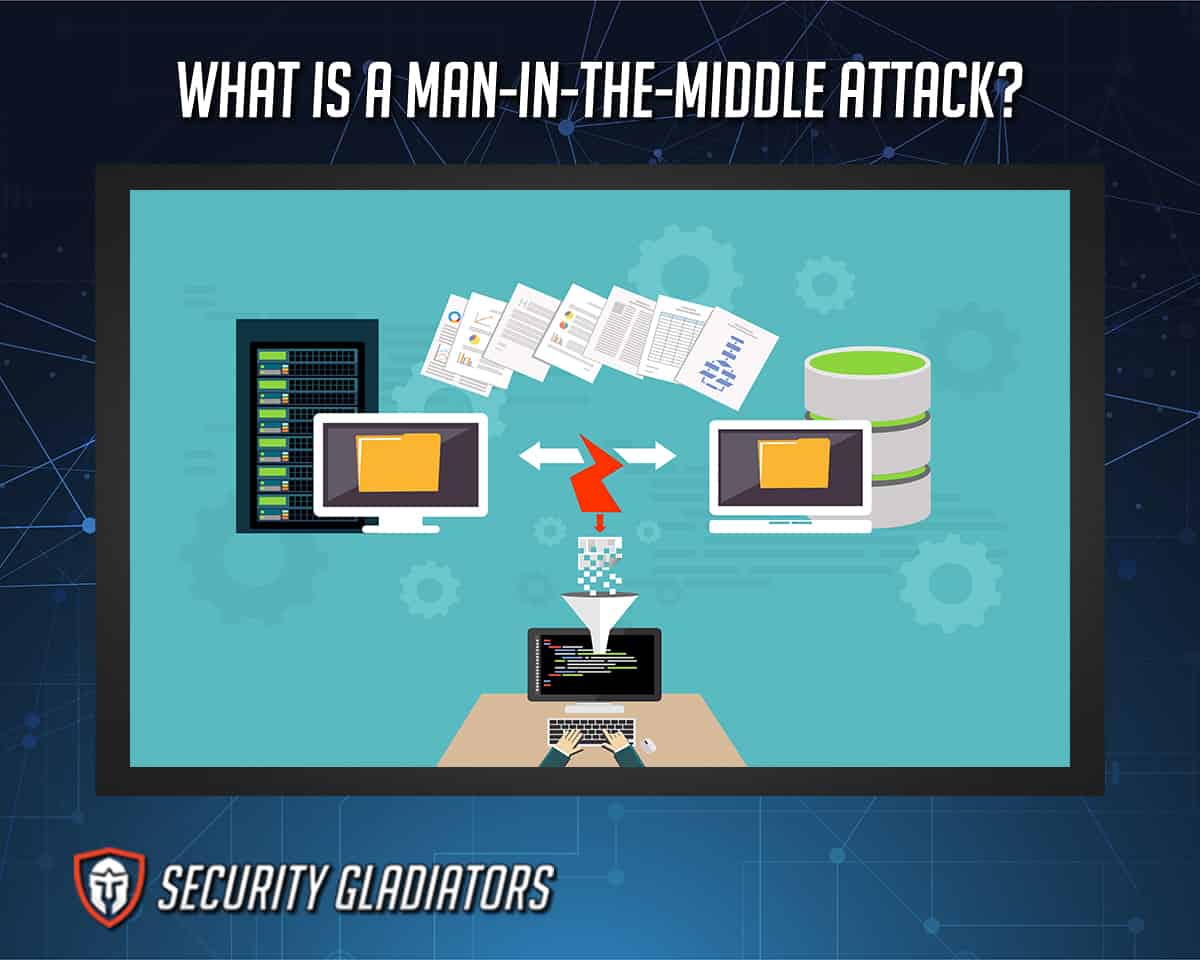
Advances in cybersecurity protocols mean that most older MitM attacks don’t yield a high percentage of success. Cybercriminals now target endpoints with their MitM attacks rather than networks. Exploiting device identities like X.509 digital certificates, cybercriminals can also mask malicious activities as legitimate ones.
Table of Contents
How Do Man-in-the-Middle Attacks Work?

For an effective MitM attack, hackers send email messages that give the impression the sender is someone the target individual can trust. Hackers mostly make it seem like the message is sent from the target’s bank, doctor, lawyer or other trusted entity. Then, cybercriminals ask the target to sign in with their valid login credentials to confirm contact details.
Once the target individual follows a link given in the malicious email message, the link takes the target to the “official” bank website, which is actually a malicious copy of the bank’s legitimate website. Of course, the target does not know this and promptly inputs login credentials while on the fake bank website. The target may log in and complete the task mentioned in the email message.
As soon as the target types the login credentials in the input boxes provided on the malicious bank website (impersonating the legitimate bank website), the target individual actually sends the login credentials back to the hacker’s headquarters operation.
Note:
The most significant effect of a successful MitM attack is the target individual losing login credentials or revealing sensitive information to the hackers, who are free to do whatever is necessary for maximum returns.What Are the Types of Man-in-the-Middle Attacks?
The types of man-in-the-middle attacks are given below.

- IP spoofing
- DNS spoofing
- HTTPS spoofing
- SSL hijacking
- Email hijacking
- WiFi eavesdropping
- Stealing browser cookies
1. IP Spoofing

IP spoofing is when cybercriminals use a device to deceive target networks by impersonating a genuine harmless entity. Hackers create IP packets with an altered source address so the sender’s identity can be hidden, allowing the hackers to masquerade the attack as a genuine computer system.
Historically, cybercriminals have used IP spoofing to launch Distributed-Denial-of-Service (DDoS) attacks on critical infrastructure and individual devices.
Any device communicates with computers on a network by sending and receiving IP data packets, which can be divided into a header and a body. The header contains routing information, such as the source IP address. Under normal circumstances, the source IP address belongs to the entity that has sent the package. With IP Spoofing, hackers can change the source IP address.
Once that happens, the hackers can send IP packages to the victim’s device with a fake return address. The package’s recipient cannot stop the sender as blocking packages from the spoofed source IP address does nothing since the hackers can instantly change the source IP address.

Inevitably, hackers launch DDoS attacks against their targets by using IP spoofing to overload the target device with lots of data/traffic by hiding the source so the receiver of the data can’t take mitigating effects.
Hackers can also use IP spoofing to access target networks and intercept traffic meant for another IP address. Similarly, with few modifications, hackers can launch MitM attacks and botnet attacks as well.
To protect against IP spoofing attacks, the most important action for an organization is training. More specifically, an organization or an individual user may implement a policy to never reply to messages that require changing login credentials by clicking on a link. Instead of doing that, the user or the organization should go to the official website of the sender and then proceed.

Good firewall implementation and strict network monitoring protocols can also be used to track any kind of suspicious activity. IP spoofing helps hackers hide their attacks, but proper network monitoring increases the chances of catching malicious activity. Modern network firewalls can require IP address authentication before proceeding to receive the packets. Firewalls can also use filtering features to stop malicious IP spoofing attempts.
It also helps to use Public Key Infrastructure (PKI) to authenticate devices and users who happen to have a private-public key pair. Finally, packet filtering allows for close examination of IP packets coming from all users and devices. If there is something improper in the header, the network refuses the connection.
2. DNS Spoofing

Cybercriminals use DNS spoofing to alter Domain Name System records and redirect online users to malicious websites masquerading as legitimate websites.
Historically DNS spoofing has referred to activities hackers perform to tamper with DNS name resolution. DNS spoofing is known by many other names, including DNS resolution, DNS hijacking, DNS cache poisoning, two-factor man-in-the-middle and DNS tampering.
DNS spoofing can also be used to launch DDoS attacks, where hackers change a popular domain name’s IP address to the target user’s IP address, so the device gets flooded with internet traffic. Internet service providers (ISPs) use DNS spoofing to censor online content by controlling the DNS server and changing IP addresses to block incoming traffic.

To prevent DNS spoofing attacks, entities should always use HTTPS connections. Monitoring DNS data and behavior patterns of external hosts also help to thwart DNS spoofing attacks. For server providers and website administrators, DNS spoofing detection tools can help, in addition to end-to-end encryption and DNSSEC (Domain Name System Security Extensions).
Pro Tip:
Individual users can use a VPN to protect against DNS spoofing. Using an anti-virus product to scan for malware also helps. As usual, not clicking on malicious links is an easy way to prevent DNS spoofing. Clearing or deleting the DNS cache periodically is also an effective preventative step.3. HTTPS Spoofing

HTTPS spoofing is a form of cyberattack where cybercriminals use a slightly altered but subtle variation of a popular domain name to deceive users into accessing a malicious website while mistakenly thinking the connection is secure (as indicated in the browser’s green padlock icon). HTTPS spoofing is also sometimes known as a homograph attack and is a five step process.
To launch cyberattacks using HTTPS spoofing
- Hackers first have to decide on a target website, which can be any trustworthy and popular website.
- The hackers have to register a domain name similar to the target domain name.
- Register for the associated SSL certificate. Registering for an SSL certificate allows hackers to get the green padlock symbol that web browsers show beside the website link in the URL bar.
- Pick a victim and send the link. Web browsers usually display Punycode hostnames via the URL bar, which helps hackers to trick users into not noticing the slightly changed URL.
- Since the user doesn’t know if the site is malicious, hackers use that advantage to extract login information and intercept traffic.
Essentially, hackers can launch MitM attacks using HTTPS spoofing.

For protection against HTTPS spoofing, security experts advise using a password manager all the time. Password managers usually do not auto-fill on spoofed websites. Upon noticing a suspicious message, users should try to contact the sender with other communication methods, such as a phone call or an in-person meeting. Avoiding clicking on any links without confirming where they land is another useful tip against any type of cyberattack.
Manually typing a URL hidden behind a link in the URL bar of the web browser is another method to stay safe from HTTP spoofing attacks. Instead of going to the target destination by clicking the link, the user is better off using a search engine to find the website of the business and navigate from there to ensure the website is legitimate.
4. SSL Hijacking
SSL hijacking is an attack where cybercriminals can bypass security measures on HTTPS websites via SSL certificates. More concretely, hackers pass fake authentication keys to the application the user is trying to access and the user for the TCP handshake. A secure connection is made with the hacker monitoring from the middle of the connection.

Historically, the technique was sometimes referred to as SSL stripping and SSL downgrading. SSL hijacking essentially downgrades a target user’s HTTPS connection to an HTTP connection. Compared to HTTPS, HTTP is not secure.
Modern web browsers contact web servers via TCP and then redirect to TLS/SSL. This is where hackers can do damage with SSL hijacking. When a user wants to access a bank website to send money, the website is usually HTTPS-secured. In SSL hijacking, cybercriminals sit between the user’s device and the banking website’s servers to intercept communications. Once the user inputs login credentials, that information goes straight to hacker HQ.
Before that, though, hackers connect with the target device, and when the user sends requests to the banking website’s server, the hackers get that request first and then forward it to the banking site’s server. Even though the banking site is SSL protected, the user’s communication line is not secured because of the hacker’s interception. So, instead of responding to the user’s requests, the banking site responds to the hacker’s requests. The hacker receives the information and then forwards it to the user.

Once the HTTPS-secured response comes back, the hacker downgrades the HTTPS URL to an HTTP URL, which allows for data manipulation and eavesdropping—all while the user has no idea that the connection is not secure and a hacker is manipulating the communication lines. Any information the user sends back to the banking website moves in the form of plain text. The hacker can see all the data, including credit card details, banking information and username/password combinations.
Pro Tip:
The best way to prevent SSL hijacking is for websites to enable SSL for all their web pages and reject HTTP connections. Enabling Cert pinning and HSTS HTTP Strict Transport Security also helps. Using secure cookies is another preventative measure that works.5. Email Hijacking

Email hijacking is when cybercriminals break into the target’s email account and access all its information. After that, the hackers keep monitoring the target individual’s communications with other entities. Upon landing on the right communication between the target user and another entity, hackers store that information to use it for even more malicious activities.
Historically, hackers have used email hijacking techniques to target high-value individuals, such as state presidents, politicians, research organizations and entertainment studios. Using email hijacking, hackers can send messages to the target individual’s sensitive contacts, such as banks and medical centers. In the case of a bank, hackers can use email hijacking to approve funds transfers from the target individual’s account to any other specified account.
Using email spoofing, hackers use a known and trustworthy domain to send an email to a target individual who opens the email and clicks a suspicious link, which leads to compromised login credentials. Social engineering is used to send spam to multiple targets. The spam usually offers discounts and other offers that require the users to fill out a form.

The most common email hijacking method is phishing, where hackers send the target an email message with a malicious link that either infects the target’s individual system or takes the user to a compromised website. Once there, the user usually ends up giving up personal details, including financial data. Email hijacking can lead to loss of money, system breakdown and identity theft.
The main way to prevent email hijacking is to use two-factor authentication techniques and a strong password (built with help from a password manager). Using modern passwordless authentication options is also a great way to ward off email hijacking attempts.
6. Wi-Fi Eavesdropping

WiFi eavesdropping is another form of a man-in-the-middle attack where cybercriminals compromise a communication channel between a user and another entity. WiFi eavesdropping involves hackers gaining access to a WiFi network and then using that to listen in on conversations from the users who connect to that network.
Historically, the technique hackers have used most to carry out WiFi eavesdropping attacks is twin networks. Such attacks often happen in places like universities, parks and libraries, where one can easily find a public WiFi network. Past records show that any place that has a WiFi network and lots of traffic is vulnerable to WiFi eavesdropping attacks, such as trains stations, airports and malls. Lately, workspaces have also become a popular spot for hackers to launch WiFi eavesdropping attacks.
Note:
The most common way to launch a WiFi eavesdropping attack is for the hacker to create a malicious WiFi network with a trustworthy name such as that of a popular company, a national store chain or any legitimate company. Creating networks in the name of famous places or restaurants allows hackers to easily dupe unsuspecting users into connecting to the compromised network. The user may think the connection leads to a legitimate WiFi network, and this is what hackers count on.Once the user connects to the malicious WiFi network and starts sending and receiving data packets, hackers start collecting that information. Compromised data can take the form of login credentials, sensitive messages and private health records. Hackers can even use WiFi eavesdropping techniques to take users to malicious versions of legitimate websites like Facebook and Twitter.

The harms of WiFi eavesdropping are generally the same as any other MitM attack. Mainly, they include loss of funds, stolen login credentials and other private information, and identity theft.
To prevent WiFi eavesdropping attacks, users should avoid connecting to public and open WiFi networks. Even when networks have password protection, they must have encryption enabled as well.
Users can also use a VPN to hide IP addresses and internet data from public networks. Studying the network before connecting is another good habit to form against potential WiFi eavesdropping attacks. Users should first look at the name of the network to ensure the name is legitimate. Examples include connecting to the network mentioned on the paper at a cafe or library and not just connecting to a network that appears on one’s device during a WiFi network scan.
7. Stealing Browser Cookies

Hackers can now implement techniques allowing browser cookies to be stolen. Websites store cookies on the user’s devices with confidential data. Hackers gain access to these cookies to steal user data and launch further cyberattacks to cause damage.
Most activities involved in stealing browser cookies are related to cybercriminals gaining access to the user’s network or the user’s device itself. If a web server is not secure enough, hackers can steal browser cookies from there as well.
In such attacks, the user logs into a specific web application, and the web server creates a session in the user’s browser via cookies. Cookies help the remote server remember personal information about the user. If a hacker manages to find the user’s session ID, stealing browser cookies becomes easier. The most common way hackers get session IDs is by making the target click on a malicious link with a compromised session ID or by stealing session cookies. Once hackers have the session ID information, web servers can be tricked into thinking the hacker’s connection is actually that of the target individual.

Once connected, the hacker effectively hijacks the session. After that, hackers are free to carry out activities that the target user is only allowed to do. The most common techniques to steal browser cookies include malware infection for packet sniffing, brute force to find out the session ID, cross-site scripting and session sniffing (carried out via a packet sniffer).
As for the harms of stealing browser cookies, it all depends on the website in question. With stolen browser cookies, hackers can potentially steal company data and online identities, transfer funds (if the browser cookies belong to the user’s banking service) and launch ransomware attacks. If the target is an organization instead of a single user, hackers can compromise entire financial systems, intellectual property data and customer databases.
Pro Tip:
The easiest way to prevent cookie hijacking is to delete cookies regularly. Users should also avoid saving any credit card information on websites that are not trustworthy. Using a password manager can help as well since deleting cookies will require the user to log in to services on each visit.What Is a Passive Man in the Middle Attack?

A successful man in the middle attack has two stages. One is the interception stage, and the second is the decryption stage. A common way to complete the interception stage is to perform a passive attack.
In a passive attack, cybercriminals create free and malicious WiFi hotspots. When the public connects to such WiFi hotspots, cybercriminals can see all the internet traffic that passes through the network.
What Are the Examples of MitM Attacks?

Real-life examples of MitM attacks include a couple from Britain who ended up losing close to $500,000 in 2015 after an email hijacking MitM attack.
Another example is that of Lenovo, a laptop company, that installed adware dubbed Superfish via MiTM SSL hijacking to serve users personalized ads in 2014.
The U.S. National Security Agency found success in listening to TOR connections with the Quantum MiTM system in 2013.
Theoretical examples include a hacker intercepting user data by installing a packet sniffer on a compromised network. Once the user inputs login credentials on a specific website, hackers receive that information and redirect the user to a malicious version of a legitimate website. Then, hackers extract data provided by the user to the malicious website.
Are MitM Attacks Common?
MitM attacks have become very common because the skill level required to carry one out is reasonable enough. Most of the MitM attack vectors take advantage of the vulnerabilities found in WiFi networks. Mobile devices tend to connect to WiFi networks automatically and send passwords to SSID, making it easy for hackers to extract user credentials.
Man-in-the-Middle Attack Prevention and Detection

Generally speaking, man-in-the-middle attack prevention and detection methods involve the user making use of end-point security solutions such as anti-virus products. After that, it is all a matter of keeping everything up-to-date to keep hackers and MitM attacks away.
Taking precautionary measures is the best solution to prevent man-in-the-middle attacks. Those measures mostly boil down to strict authentication and strong encryption. Many cryptographic protocols offer endpoint authentication that can prevent MitM attacks. One of them is SSL.
But SSL is not necessary to gain protection against MitM attacks. Many methods protect against MitM attacks without relying on SSL.
How to Prevent Man-in-the-Middle Attacks?

The best precaution to take against man-in-the-middle attacks is to use authentication based on public-key pairs. An example of such authentication is RSA. These ensure that the entity the user is interacting with is actually the entity it claims to be.
Forcing HTTPS connections is also a good way to prevent man-in-the-middle attacks. HTTPS can block any sniffing attempts on the part of hackers. There are many web browser plugins available that force HTTPS connections. One of them is HTTPS Everywhere for Google Chrome and Mozilla Firefox browsers.
This is important:
Using a VPN service is another way to prevent man-in-the-middle attacks. VPNs protect sensitive information and encrypt user data for secure communication. Changing the default login credentials on the WiFi router is another method to stop hackers from changing DNS servers and directing users to malicious websites unknowingly.
Ensuring WPA/WEP encryption on wireless access points also stops hackers from joining a given network. Hackers sometimes use brute force methods to crack networks, but strong encryption can thwart those attempts. Using tools like proxy servers and SSH is another way to prevent man-in-the-middle attacks.
After a man-in-the-middle attack, there is little the user can do except to change login credentials if possible and block banking transactions by calling the bank and refusing access to healthcare records.
Note:
Implementing two-factor authentication, enabling TLS/SSL standards for email communication, not using public networks and awareness education should be the standard operating procedures after a man-in-the-middle attack.How to Detect Man-in-the-Middle Attacks?

To detect man-in-the-middle attacks, web browser plugins such as Perspective and Cert Patrol can help users identify a legitimate CA from a fake one. Upon connecting to an SSH server, if the server asks for a new fingerprint despite the fact that the user has connected to the server previously, that is a sign something foul is at play.
HTTPS connections allow browsers to detect man-in-the-middle attacks automatically without any effort from the user. Modern browsers also warn the user whenever there is a suspicion of a man-in-the-middle attack.
Pro Tip:
A good anti-virus product can also detect any type of malware that cybercriminals may try to install on the user’s system. If accessing a website gives the warning of an expired certificate, it is standard practice to assume there is a man-in-the-middle attack waiting to happen.
Specialized man-in-the-middle attack solutions can track all the web traffic that goes into and out of the system at both the protocol and port layers. Once such tools identify malicious activity, they can alert the user of a possible man-in-the-middle attack.
If the web browser shows unusual web addresses or regularly disconnects from websites, that is another way to detect man-in-the-middle attacks.
How to Report Man-in-the-Middle Attacks?

To report man-in-the-middle attacks, the user can contact the network administrator to notify of any malicious activities. Showing network connections from suspicious locations and unknown users can help while reporting man-in-the-middle attacks to both network administrators and senior personnel in the IT department.
Taking screenshots of the suspicious address in the browser bar and sending them to the security team is another way to report possible man-in-the-middle attacks.
Apart from that, making a note of WiFi networks with strange names or no passwords and sending that information to concerned personnel is another great way to report potential man-in-the-middle attacks.
What Causes Man-in-the-Middle Attacks?
- Replying to email messages from unknown sources can cause man-in-the-middle attacks.
- MitM attacks are also caused when the user clicks on malicious links via email messages or chat services.
- Another cause of man-in-the-middle attacks is free unprotected WiFi networks.
- A vulnerable router is another cause of man-in-the-middle attacks.
- The lack of HTTPS connections with websites and services is another cause of man-in-the-middle attacks.
- Expired certificates are another factor that assists man-in-the-middle attacks.
- Stolen SSL/TLS keys are another cause of MitM attacks, as is the client’s inability to validate a certificate.
- Malware on the user’s system is another reason for the man-in-the-middle attacks.
- Self-signed certificates are one factor that helps attackers carry out man-in-the-middle attacks.
- Forged or untrusted certificate authorities also cause man-in-the-middle attacks.
Does the Usage of a VPN Prevent Man-in-the-Middle Attacks?
Yes, the usage of a VPN can prevent man-in-the-middle attacks. VPNs can encrypt user data so that even if hackers monitor user traffic, they can’t make any sense of the data packets since they’re encrypted. VPNs also change the user’s location by changing the user’s IP address. This also stops internet service providers and hackers from performing man-in-the-middle attacks since they can’t know which two endpoints to sit between.
How Common Are Man-in-the-Middle Attacks?

Man-in-the-middle attacks are very common in today’s ultra-connected world because it has become financially lucrative for hackers to launch man-in-the-middle attacks. The skill level required to launch MitM attacks has also lowered due to advances in automation and app development tools. Additionally, more people and organizations are digitizing tasks, which gives rise to more opportunities to perform man-in-the-middle attacks.
This is important:
It is very important for online users, website owners and companies to know how to prevent man-in-the-middle attacks because the steps involved in preventing them are easy to follow and implement. Protection against man-in-the-middle attacks is very straightforward and economical. With so many services available to protect against man-in-the-middle attacks and training required to keep safe, it is easier than ever to stay protected against MitM threats.Can HTTPS Prevent Man-in-the-Middle Attacks?
Yes, HTTPS can prevent man-in-the-middle attacks. HTTPS is essentially HTTP over TLS/SSL. The HTTPS protocol is mostly used to secure sensitive communications with the help of encryption, among other security tools. In the case of man-in-the-middle attacks, HTTPS can make it harder for cybercriminals to eavesdrop on conversations. That is because of the presence of an SSL certificate, which is also hard for cybercriminals to get for uncontrolled domain names.
Can TLS Prevent Man-in-the-Middle Attacks?

Yes, TLS can prevent man-in-the-middle attacks. TLS/SSL standards encrypt internet traffic passing through an HTTP connection. In effect, TLS/SSL provides protection against HTTP interception.
TLS/SSL also protects web-based man-in-the-middle attacks. In addition to that, the TLS SSL encryption protects communications between a server and a client, which further prevents eavesdropping attempts.
Can Man-in-the-Middle Attacks Happen Through a Phone?

Yes, a man-in-the-middle attack can happen through a phone. For a man-in-the-middle attack to happen, a cybercriminal has to intercept communications between two parties/systems. The device used for communication is not the most important factor for a hacker.
The vast majority of man-in-the-middle attacks take place via email messages, social media interactions, malicious links, compromised websites and instant messaging. The type of device matters little in this regard.

