During the late 1970s, the OSI model was designed to facilitate the rise of multiple computer networking systems competing for application in the world’s significant national networking endeavors. The goal of developing networking standards is to identify widely accepted methods of setting up networks and connecting the two. The OSI Reference Model was an early attempt to bring all the different hardware and software vendors together to agree on a framework for developing diverse networking technologies. The model became a working product of the Open Systems Interconnection group in the 1980s.
Distributed denial of service (DDoS) attacks can occur on the different OSI layers. DDoS refers to a method in which cybercriminals prevent a network from operating or communicating regularly by flooding the network with malicious traffic that originates from multiple distributed sources. Multiple bots, known as zombies, are employed in this type of attack to send massive amounts of traffic to the victim server. The site’s usual traffic, also known as legitimate packets, is halted as a result. DDoS is a simple, effective and powerful attack method fueled by vulnerable devices and bad digital habits.
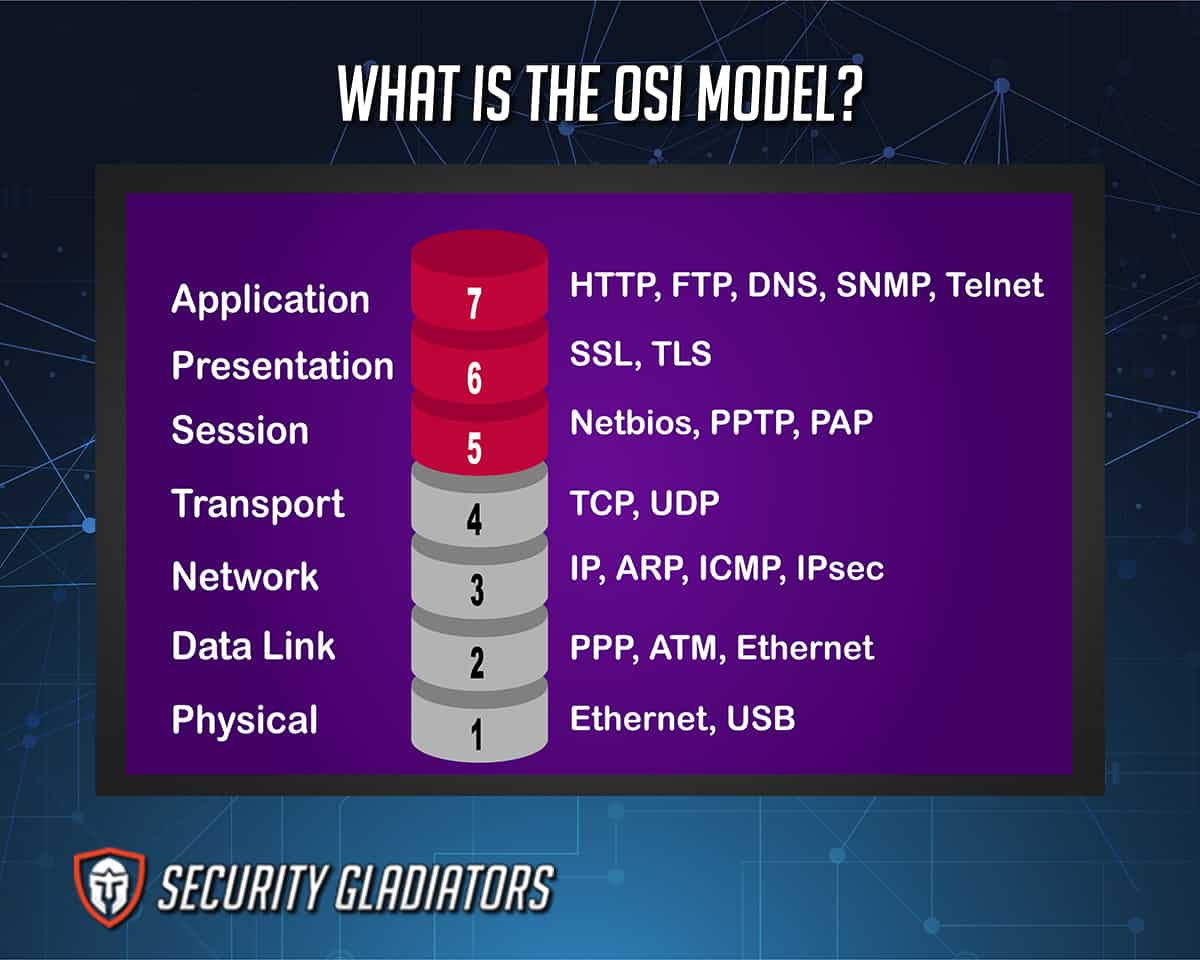
In the OSI reference model, the communications between computing systems are divided into seven abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation and Application.
Each layer performs specialized responsibilities to support the layers above while providing services to the layers below. The three lowest layers are concerned with directing traffic through the network to an end system. The top four layers are used in the final system to complete the process.
Table of Contents
1. Physical Layer

The OSI model’s physical layer specifies connection and interface specifications and medium requirements. The layer takes charge of transmitting data packets through the network media. Electrical, mechanical, functional and procedural standards are provided for transporting a bitstream via a computer network. Passive hubs, couplers, cables and repeaters are all examples of physical layer devices.
2. Data Link Layer

The OSI model’s Layer 2 allows a device to connect to the network and to send and receive messages while providing a physical address so that a device’s data may be delivered over the network.
3. Network Layer

Layer 3, the OSI model’s network layer, is also known as logical addresses. This layer provides an end-to-end logical addressing mechanism allowing a data packet to be routed over several Layer 2 networks (Ethernet, Token Ring, Frame Relay, etc.).
In bigger systems, there are frequently intermediate nodes between any two end systems. The network layer provides the link that allows the layers above to deliver packets regardless of whether the end system is on the local LAN or several hops distant. Routers and gateways are network layer devices.
4. Transport Layer

The Transport Layer facilitates the transparent data movement between end-users while offering dependable data transfer services to the layers above. The same layer uses flow control, segmentation and desegmentation, and error control, ensuring the reliability of a specific link. The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) belong to Layer 4 protocols.
Attacks at Layers 3 and 4 are typically categorized as infrastructure layer attacks. These attacks are often high-volume and try to overburden the network or application servers. However, infrastructure layer attacks have distinct signatures, making detection of such attacks easier.
5. Session Layer

This layer manages computer-to-computer dialogues (connections). The layer creates, manages and closes connections between local and remote applications. Layer 5 supports full-duplex, half-duplex and simplex operation and check-pointing, adjournment, termination and restart processes.
Layer 5, the session layer, provides various functions, including recording the number of bytes recognized by each end of the session from the other end of the session. This layer is responsible for seamlessly closing sessions, as well as session check-pointing and recovery. In application contexts that leverage remote procedure calls, the session layer is frequently built explicitly. This session layer enables device-based apps to start, manage and end a network-based dialogue.
6. Presentation Layer

Layer 6, the presentation layer, takes charge of how an application formats data before sending data out onto the network. The presentation layer essentially enables an application to read (or comprehend) the message. The layer builds context between application-layer items, in which higher-layer entities may utilize distinct syntax and semantics if the presentation service provides mapping in between.
Note:
Because different computer architectures use different data representations, this type of service is required. In contrast to the fifth level, which provides transparent data transfer, the presentation layer handles all data presentation and transport concerns, including compression, encryption and translation.7. Application Layer

Layer 7, the application layer, serves as an interface for the end-user running a network-connected device. This layer is what the user sees when loading an application (such as a web browser or email). In other words, the application layer is the data that the user sees while using these apps.
Attacks at Layers 6 and 7 are frequently classified as application-layer attacks. These attacks are less prevalent but are also more complex. These attacks are often less in scale than other layer attacks, but tend to focus on certain expensive sections of the program, rendered unavailable to real users.
What Are the Advantages of OSI Layers?

The rise of the internet’s popularity and the corresponding TCP/IP protocols collided with the OSI suite. In a nutshell, TCP/IP triumphed. Some OSI protocols were established, but as the internet grew these OSI protocols were surpassed by TCP/IP.
On the other hand, the OSI model found a home as a tool for understanding the operation of the OSI protocols and networking in general. The model was frequently utilized as an instructional tool.
The advantages of OSI Layers are:
- Clearly distinguishes between services, interfaces and protocols. As a result, unlike proprietary systems, devices or equipment from different vendors can coexist on the same network.
- Encourage networking hardware makers to build networking products that can connect via a network.
- Troubleshooting is simplified since each layer defines a collection of data transfer functions and can detect and resolve issues quickly by looking in a layer.
- New ones can easily replace hidden protocols and updates can be made efficiently.
- The model accommodates both connection-oriented and connectionless services.
How Do OSI Layers Help Protect Against DDoS Attacks?

In the OSI model approach, security is addressed at each layer of the model. IT managers must understand that safeguarding applications and networks entails more than just authentication, encryption and OS hardening. At each layer, there are security vulnerabilities and preventative security measures that may be implemented to ensure security. Importantly, as the OSI model progresses, the ability of IT administrators to minimize risk diminishes.
DDoS attacks are most commonly found at the Network (Layer 3), Transport (Layer 4), Presentation (Layer 6) and Application (Layer 7) Layers. An application targeted by a DDoS attack leads to a server overload, while attacks exploiting vulnerabilities in the transport layer (Layer 4) may cause an overflow of the connection table and server inaccessibility. An overflow of data center and client communication circuits leads to a loss of legitimate traffic and unavailability of the service. Congestion on switching equipment caused by fake frames leads to loss of legitimate traffic. Classification of DDoS attacks can be based on the layer of the OSI model that is targeted.
Understanding DDoS attacks is one thing, but one is better armed with the knowledge of which OSI layers DDoS attacks occur and how these layers protect against these attacks.

