Encryption has long been a method of safeguarding sensitive data. Cryptography refers to the science of encrypting and decrypting data. Encryption is the process of converting data to a secret code that obscures the data’s true meaning. Unencrypted information is also referred to as plaintext in computers, while encrypted data is called ciphertext.
Encryption algorithms, or ciphers, are the mathematical formulas used to encode and decode messages. A cipher’s algorithm must include a variable to be effective. The variable, referred to as a key, is what distinguishes the output of a cipher. When an unauthorized entity intercepts an encrypted message, the intruder must guess the cipher used to encrypt the message and the keys that were used as variables.

The time and complexity associated with decoding this information contribute to encryption’s value as a security technology. Encryption software has become essential to protecting data and folders. Hacking attempts and privacy breaches have made it easier than ever for total strangers to gain access to a computer’s most personal information. Even more importantly for businesses, encryption software prevents the disclosure of sensitive or confidential documents, the release of which could result in financial losses and hefty fines.
Regardless of core features, encryption programs protect individual pieces of data or a full disk from falling into the wrong hands or being stolen from a device. The software is also utilized to transmit sensitive information that requires a high level of security to be protected. In the current computer age, the utilization of an encryption program has become increasingly essential. Listed below is an in-depth comparison of several encryption software programs.
Table of Contents
1. Folder Lock

Folder Lock, a data encryption service provided by NewSoftwares for individuals, is a good solution for encrypting mobile devices. This solution enables users to secure any device that stores sensitive data. Users can protect personal files, images, movies, contacts, wallet cards, notes and audio recordings stored on a handset using this program.
Folder Lock also gives a user access to the encryption software and decoy passwords, hacker deterrents, the ability to monitor unauthorized login attempts, back up all passwords, and the ability to be informed of future brute-force attacks. All of this and more is covered in greater detail in our Folder Lock review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | No |
| Secure Deletion: | Yes |
| Deployment: | Software – perpetual license |
| Price: | $39.95 for Windows |
| Compatibility: | Windows, Android and iOS |
2. Advanced Encryption Package
Advanced Encryption Package supports both symmetric and asymmetric encryption, offers a choice of 17 different algorithms and has a valuable set of built-in utilities. The desktop interface is intuitive and straightforward to use, with no significant problems, and the user manual is excellent.
Advanced Encryption Package may be a suitable fit for those seeking a simple file encryption tool. Further discussion of this tool and its features can be found in our Advanced Encryption Package review.
| Encrypt: | Files, folders and text |
| Full Disk Encryption: | No |
| Secure Deletion: | Yes |
| Deployment: | Software – perpetual license |
| Price: | $49.95 for a single license Bulk license packages are available |
| Compatibility: | Windows, Android and iOS |
3. Microsoft BitLocker

Microsoft BitLocker delivers cloud-based services and solutions for businesses that efficiently secure data stored on a network. The software includes built-in encryption for data at rest and data in transit and authenticates users and endpoints using the Microsoft Public Key Infrastructure.
Microsoft BitLocker encrypts data using Transport Layer Security/Secure Sockets Layer (TLS/SSL), Internet Protocol Security (IPsec), AES, Azure Storage Service Encryption and Transparent Data Encryption. More details can be found in our Microsoft BitLocker review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | Yes |
| Secure Deletion: | Yes |
| Deployment: | Software – perpetual license |
| Price: | Free with Windows 10 |
| Compatibility: | Windows |
4. AxCrypt

AxCrypt is designed for individuals and small teams and is a solid and powerful product that provides all the tools to secure files. Files are encrypted with 128-bit or 256-bit AES, which should deter most intruders.
Files saved on Google Drive and Dropbox are automatically protected, meaning files not on a machine are also covered. AxCrypt supports cloud storage capabilities and over a dozen languages. Finally, there is passport management and a powerful app for managing all data. AxCrypt also has a free, although limited, encryption software version. More information can be found in our AxCrypt review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | No |
| Secure Deletion: | Yes |
| Deployment: | Software – perpetual license |
| Price: | $9.92/month (subscription) |
| Compatibility: | Windows (2008, 7, 8 and 10, 32- and 64-), macOS, Android 4.0.3 or later and iOS 8.0 or later |
5. CertainSafe
CertainSafe is a perfect alternative for people who need to protect extremely sensitive personal or corporate data. The CertainSafe Digital Safety Deposit Box allows access to files through any browser, on any platform. The MicroEncryption technology ensures that even if a team of burglars successfully releases an entire server, only fragments of data, not entire files, will be accessed. More details about this software can be found in our CertainSafe review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | No |
| Secure Deletion: | No |
| Deployment: | Cloud |
| Price: | $12/month (subscription) |
| Compatibility: | Windows (2008, 7, 8 and 10, 32- and 64-), macOS, Android 4.0.3 or later and iOS 8.0 or later |
6. CryptoExpert

CryptoExpert is one of the best encryption programs available for Windows desktop software security. Providing secure vaults for all personal data and ensuring that it is safeguarded against all possible breaches, CryptoExpert delivers highly sought-after, on-the-fly protection. The system supports backups of various file types, including certificates, Word, Excel, PowerPoint documents, multimedia files and email databases.
CryptoExpert can protect any size vault and encrypt data using the Blowfish, Cast, 3DES and AES-256 algorithms. Further discussion of the features of this software can be found in our CryptoExpert review.
| Encrypt: | Files, folders and text. |
| Full Disk Encryption: | Yes |
| Secure Deletion: | No |
| Deployment: | SaS |
| Price: | $59.95 for a lifetime license |
| Compatibility: | Windows 7, 8 and 10 (32- and 64-bit). |
7. VeraCrypt
VeraCrypt encryption software is a free encryption program that features an intuitive, interactive user interface. On current CPUs, encryption is hardware-accelerated and automated. All data is transparent and available in real-time. The software embeds an encrypted virtual disk into a file and mounts it as an actual disk. VeraCrypt Encryption’s privacy rules are meant to secure users and data to the fullest extent possible. More details about this software can be found in our VeraCrypt review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | No |
| Secure Deletion: | No |
| Deployment: | Open source freeware utility download |
| Price: | Free |
| Compatibility: | Windows, macOS and Linux |
8. CryptoForge

CryptoForge data encryption software is equipped with four robust encryption algorithms: 448-bit Blowfish, 256-bit AES (Rijndael), 168-bit Triple DES and 256-bit Gost. The software has strong compression to further bolster cryptographic security.
The command-line interface enables rapid integration into automated processes and scripts and enables the ability to run operations in interactive or non-interactive server modes. The visual tool enables users to create command-line parameters without having to understand the syntax.
Other unique features include multiple encryptions, filename encryption, compression level control and a ciphers’ speed meter. Further discussion of these details can be found in our CryptoForge review.
| Encrypt: | Files, folders and text |
| Full Disk Encryption: | No |
| Secure Deletion: | Yes |
| Deployment: | Open source freeware utility download |
| Price: | Free |
| Compatibility: | Windows |
9. Boxcryptor
For firms relying heavily on cloud storage rather than on-premises storage, Boxcryptor is an excellent option. Boxcryptor provides end-to-end encryption for 30 different cloud services using a combination of AES and RSA. Google Drive, Microsoft and Dropbox are just a few of the prominent providers.
The company describes itself as a “zero-knowledge provider” which means the encryption process is automated across numerous services and devices. No encryption expertise is required to implement and run Boxcryptor. For further discussion of this software, check out our Boxcryptor review.
| Encrypt: | Files, folders and text |
| Full Disk Encryption: | No |
| Secure Deletion: | Yes |
| Deployment: | Software – perpetual license |
| Price: | $96 per year |
| Compatibility: | macOS and Windows |
10. Secure IT 2000
Secure IT 2000 has an intuitive user interface that is simple to use, with shortcuts to My Documents and the Desktop. The software encrypts and decrypts data in 64-bit chunks using the Blowfish 448 encryption method. This technique generates a key that is between 32 and 448 bits in length.
Secure IT 2000 also includes a built-in file compressor. However, the installation CD or floppy can only be used once and can be a disadvantage if the system crashes in the future. More details about this software can be found in our Secure IT 2000 review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | No |
| Secure Deletion: | Yes |
| Deployment: | Software – perpetual license |
| Price: | $29.95 for Windows |
| Compatibility: | Windows |
11. NordLocker
NordLocker is a relatively new encryption technology developed by NordVPN, a cybersecurity juggernaut. The software provides an option for both 256-bit AES encryption, which is enough to secure most data, and 4096-bit encryption. Users also appreciate the intuitive user interface of NordLocker. Individual files can be added or removed from NordLocker with a simple drag-and-drop operation. This ease of operation allows IT personnel to focus on other initiatives. Further discussion of this software can be found in our NordLocker review.
| Encrypt: | Files, folders and text |
| Full Disk Encryption: | No |
| Secure Deletion: | No |
| Deployment: | SaaS |
| Price: | $3.99 to 7.99 per month |
| Compatibility: | macOS and Windows |
12. Steganos Safe
Steganos Safe concentrates exclusively on encrypting storage containers; secure encrypted file storage or “safes” for confidential data. The software is straightforward to use and includes several novel features for ensuring privacy and secrecy. Steganos Safe is more user-friendly than significant competitors and is one of the most affordable premium encryption tools. Further discussion of this software can be found in our Steganos Safe review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | Yes |
| Secure Deletion: | Yes |
| Deployment: | Software |
| Price: | $34.95 for five PCs (One year) |
| Compatibility: | Windows |
13. Cypherix Cryptainer PE
Cypherix Cryptainer PE is designed to safeguard files within its encrypted volume. However, the secure deletion tool leaves unencrypted originals behind. The issue is that performing this function does not justify the product’s price, even for a one-time fee. For more details about this software, check out our Cypherix Cryptainer PE review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | Yes |
| Secure Deletion: | No |
| Deployment: | Software – perpetual license |
| Price: | $45 |
| Compatibility: | Windows |
14. Cypherix SecureIT
Cypherix SecureIT is a fantastic choice for those in need of a powerful file encryption utility. Secure IT and its file encryption services are reasonably priced, have an intuitive yet powerful user interface and are supported by a slew of fantastic features. Additionally, the program includes one of the most straightforward user instructions, ensuring that even the most unskilled users should have no difficulty using the product. The downside is a lack of filename encryption and advanced features, as well as a dated interface. More details about this software can be found in our Cypherix SecureIT review.
| Encrypt: | Files and folders |
| Full Disk Encryption: | Yes |
| Secure Deletion: | Yes |
| Deployment: | Software – perpetual license |
| Price: | $29.95 for Windows |
| Compatibility: | Windows (32- and 64-bit) |

Overall, the simplest and easiest to use encryption tool is AxCrypt. AxCrypt Premium has a sleek, modern appearance and is almost unnoticeable when active. After a user signs out, the files in Secured Folders are automatically encrypted. Furthermore, AxCrypt is one of the few programs that support public-key cryptography.
For a more thorough software, Folder Lock is a good option. Folder Lock can encrypt files or lock them to prevent unauthorized access. Additionally, this software provides encrypted lockers for safe storage. File shredding, free space shredding, secure online backup and self-decrypting files are among Folder Lock’s numerous other capabilities.
Do I Need Encryption Software?

Data encryption is used to safeguard the secrecy of digital data as it is stored on computer systems and delivered across the internet or other computer networks. The obsolete data encryption standard (DES) has been phased out in favor of new encryption algorithms, vital for information technology systems and communications security.
Modern encryption keys adhere to the Advanced Encryption Standard (AES), which scrambles data using key lengths of 128-bit and 256-bit, which are exceptionally lengthy strings of digits. In rare instances, key lengths of up to 4096 bits are employed. In simple encryption definition, when a file is encrypted, the data sent is unreadable until the same device or another device decrypts it with the key.
This is important:
Data should always be encrypted, both in transit and at rest. The terms “data in transit” and “data at rest” refer to data sent between endpoints and data stored in a database, respectively. If consumer data is exposed, the safeguard provided by encryption can differentiate between a catastrophic breach of personally identifiable information (PII) and the disclosure of unreadable ciphertext. Without adequate security measures, including encryption, firms run the risk of being fined for violating data privacy regulations, such as the EU’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).Encryption is crucial for securing data exposed due to other security software failing on the front lines. Critical to preventing data breaches and ensuring compliance with data privacy requirements, encryption safeguards against cyberattacks, making encryption software a vital component of an organization’s cybersecurity strategy. As governments implement new legislation and data breaches grow more prevalent, encryption is needed to mitigate risks, build trust and remain compliant. Encryption can save firms a significant non-compliance penalty and help maintain the trust earned from customers.
What Types of Data Should Be Protected by Encryption Software?
Encryption is necessary for data protection and is recommended for two kinds of data: personally identifiable information and confidential commercial intellectual property.Personally Identifiable Information (PII)
PII refers to information or data that can be used to uniquely identify an individual. Hackers may use this information to steal a victim’s identity and commit more severe crimes like applying for credit cards and loans in the victim’s name.
Email management and encryption are critical components of a data loss prevention system. Secure, encrypted email is the sole solution for regulatory compliance, a distributed workforce, bring your device (BYOD) and project outsourcing. Staff phones, tablets and laptops contain PII, and those devices and their associated storage should be completely encrypted. When a thief encounters difficulties obtaining backdoor exploits, the hacker frequently resists utilizing employee credentials and passwords to enter the front door.
The list below are examples of PII.
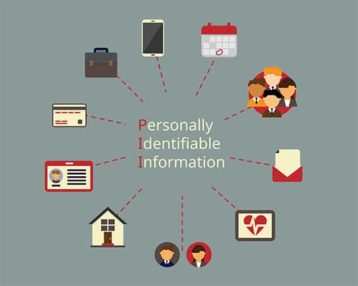
- Name: full name, alias, maiden name, mother’s maiden name, etc.
- Personal identification numbers: credit card number, driver’s license number, financial account number, passport number, patient identification number, Social Security number (SSN), taxpayer identification number, etc.
- Personal characteristics: fingerprints, handwriting, photographic images (particularly of face or other identifying characteristics), etc.
- Personal address information: street address or email address.
- Personal telephone numbers.
- Biometric data: retina scans, voice signatures or facial geometry.
- Information identifying personally owned property: VIN or title number.
- Asset information: Internet Protocol (IP) or Media Access Control (MAC) addresses that consistently link to a particular person.
Confidential Business and Intellectual Property

Businesses generate a treasure trove of valuable information. Today, digital thieves break into company databases because these locations are where the most valuable data is stored. Imagine the customer data that employees access each day or the information on plans for a new product and upcoming marketing strategies. Competitors could benefit from knowing this information or simply from getting a list of clients.
Enumerated below are the types of data that should be prioritized by businesses when encrypting.
Customer Information: Special data protection regulations apply to businesses in the banking and healthcare industries. These regulations govern the protection of consumer information. Even companies outside those industries need to take customer information seriously because the company’s reputation is usually at stake.
Financial Reports: The majority of businesses keep financial statements close at hand. It is essential to identify a location to consolidate the reports and then encrypt them. Access should be restricted and should only be provided to those who need it.

Product Release Documents: Employees sometimes carry vital information about product release schedules for months or even years. Thieves target business travelers and their computers for the information they hold.
Research and Development Data: Companies that invest heavily in research and development safeguard the information through encryption. Although data is frequently distributed internally, encrypting the data will still be a valuable layer of protection.
Images
Certain images can fall under both categories of PII and confidential business and intellectual property, making encryption important for these types of files. Images are encrypted for numerous reasons, including identifying an image source, safeguarding copyright information, discouraging piracy and preventing unauthorized views. Encrypting images provides additional security if a hacker gains access to a drive or a device is lost or stolen.
What Are the Advantages of Using Encryption Software?

Encryption software assists businesses in meeting regulatory compliance and putting data security models into operation. In particular, encryption technology can aid businesses in achieving portions of the CIA triad, which stands for confidentiality, integrity and availability of data, and is a widely used security model to protect information. Below are further details about each portion of the CIA triad.
Businesses must have confidence that the data has not been tampered with, mainly while the data is in transit. Along with maintaining data security, encryption also helps ensure that information is not being deleted or manipulated by unauthorized parties while being transferred.
Numerous data privacy and data protection rules expressly state that encrypted data is adequately safe and not subject to regulatory oversight or less strict regulatory oversight. Encryption is especially beneficial when working with datasets including PII, protected health information (PHI) and payment card industry (PCI) data.
What Industries Should Use Encryption Software?

Safeguarding data using encryption software is beneficial for all businesses. Those handling PII and other sensitive data should consider using encryption software as part of their overall information security practices. Several companies in a vast range of industries should also consider encrypting data. Listed below are sectors where encryption is a must-have due to requirements to encrypt data to adhere to legal obligations and industry norms.
Pharmaceutical Industry: Pharmaceutical businesses are accountable for safeguarding massive amounts of sensitive, confidential data to adhere to data protection regulations and demanding regulatory health standards. Data management is thereby critical in the highly regulated pharmaceutical industry. With research and development costs in the millions, it is vital to protect research and personal data, including the time of product launch.
Healthcare Industry: Medical data has been growing exponentially, which led the Health Insurance Portability and Accountability Act (HIPAA) to enact the Security Rule. The U.S. Department of Health and Human Services (HHS) states that the HIPAA Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for protecting specific health information. Additionally, the Security Rule sets a national framework for protecting sensitive health information stored or transmitted electronically.

Financial Institutions: The finance sector, especially banks, face numerous obstacles and the necessity to obtain encryption in various formats to ensure the security of cards, pins and transactions. Furthermore, the Federal Financial Institutions Examination Council (FFIEC) requires financial institutions to use encryption to reduce the risk of sensitive information being disclosed or altered during storage and transit.
Other Industries: The Gramm-Leach-Bliley Act (GLBA) requires that institutions conducting business in the U.S. adopt acceptable security and confidentiality measures for consumer Non-public Personal Information (NPI). In addition, retailers must comply with the Fair Credit Practices Act (FCPA) and other consumer protection legislation. In the academe, under the Family Education Rights and Privacy Act (FERPA), institutions of higher learning are required to take safeguards to secure student records.
What Companies Use Encryption Software?
Encryption has become critical to many firms’ cyber security strategies. Businesses that employ robust encryption tend to be those that value customers’ privacy and security. Companies seek to protect data and privacy and adhere to stricter compliance rules, such as Europe’s GDPR and California’s Consumer Privacy Act.
The Electronic Frontier Foundation (EFF) is continuously seeking firms that protect consumers’ data. Firms that store user data frivolously are also named and shamed. The EFF gauges companies through these five best practices for encryption.

- Encryption of data center links implies that companies encrypt data as it travels between data centers, a known vulnerability.
- The usage of HTTPS ensures that all communications between a user and a website are encrypted.
- A web server’s security strategy requiring continuous HTTPS communication with users is HSTS.
- Forward secrecy which is a cryptographic quality or ideal that ensures that one compromised key does not compromise subsequent transmissions.
- STARTTLS is an email extension that converts plain-text emails to encrypted emails, regardless of the email client used.
Note:
Currently, eight companies—Dropbox, Facebook, Google, Microsoft, Sonic.net, SpiderOak, Twitter and Yahoo—use the five encryption best practices. These companies encrypt consumer data across the board. These companies encrypt data center links, provide HTTPS, HSTS, forward secrecy and STARTTLS.Still contemplating the encryption features for their data center, LinkedIn received four checks. Tumblr has three checks, while FourSquare and WordPress both received two checks. Apple scored one point for iCloud HTTPS support, and Amazon scored one point for STARTTLS. According to the EFF, firms that received zero checks included AT&T, Comcast and Verizon because they do not encrypt traffic.

