In this guide, we’ll take a look at the computer networking term “localhost,” which is essentially a local computer address.
What is localhost, and what does it have to do with the IP address 127.0.01, if anything? Learn more about what it means and how it works:
Table of Contents
What Is localhost?

Every website in the world has a domain name (like www.google.com). Every website also has an associated IP (Internet Protocol) address. You can connect to any given website via either its domain name (for example, www.cnn.com) or its related Internet Protocol address.
But typically, internet users don’t use IP addresses to access websites. They use domain names because they are easier to type and remember, whereas IP addresses contain a string of numbers.
And this is where the IP address 127.0.0.1 comes into play. Whenever you use this address for a connection, it will lead to the machine you are currently working on. Most of the time, that will be your own computer.
This is important:
Now you’re in a better position to understand localhost: Localhost is nothing but your computer, and that localhost has 127.0.0.1 as its default IP address. It doesn’t really matter which computer you’re using—if you try to connect to the default IP address, you will always connect to the computer you used to type that IP.More specifically, you should think of localhost as a server that your own computer uses for networking purposes. When your computer wants to ping or call to itself, it uses the localhost. But localhost is a bit more than just a virtual server. It is also a top-level domain name.
Web developers usually use .localhost for development testing and documentation purposes. This is also where the concept of loopback address comes into the equation. The loopback address is simply the Internet Protocol address that localhost resolves to, which, for the purposes of this post, is 127.0.0.1.
You can also use a loopback system to modify a hosts file and block malicious websites. Your device creates a host file for every website you visit; it hosts the IP and domain name assigned to the site by the DNS (domain name system). By changing the hosts file, you can effectively block websites that could contain malware and other security threats lurking behind the interface of the site.
What Is My localhost?
Your localhost is your own computer/device, and if you are running a server on it, your localhost IP address is most likely 127.0.0.1. This is also your loopback address.
How Do I Access localhost?

Assuming you have a server running on your computer, you can access localhost by going to a web browser and using the URL bar to type http://127.0.0.1. Alternatively, you can also use the text http://localhost/.
If you aren’t picky about using the 127.0.0.1 localhost, you can use http:192.168.X.X (the X.X part is the local IP address of your server) if you are on a different computer than the one that’s running the server.
On a side note, you can use the hostname -I command on a Linux program to find out your server’s reserved local IP address.
Should I Use 127.0 0.1 or localhost?
You can use either option. But the more accessible one is 127.0.0.1 since using localhost means your computer will have to do an actual DNS search of localhost. Since the number is an IP, your machine can use it directly on your network. It’s also your loopback address.
How Do I Access 127.0.0.1 from Another Computer?
Assuming you are an administrator using a computer running the Windows operating system, here are the steps you need to take for accessing your IP address from another computer:
Step 1: Go to Your Windows Firewall Settings
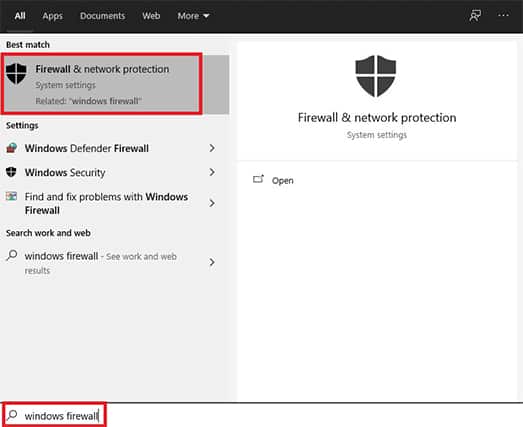
You can easily do that by clicking the Windows icon in the bottom left corner of the screen and typing “Windows Firewall.”
Step 2: Click on Advanced Settings
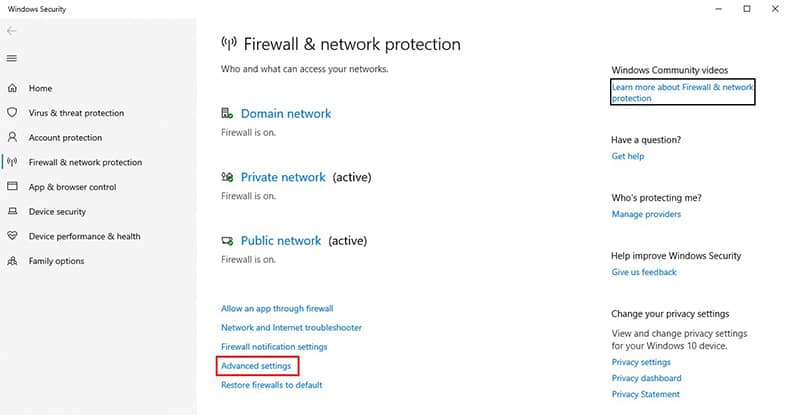
Step 3: Go to Inbound Rules
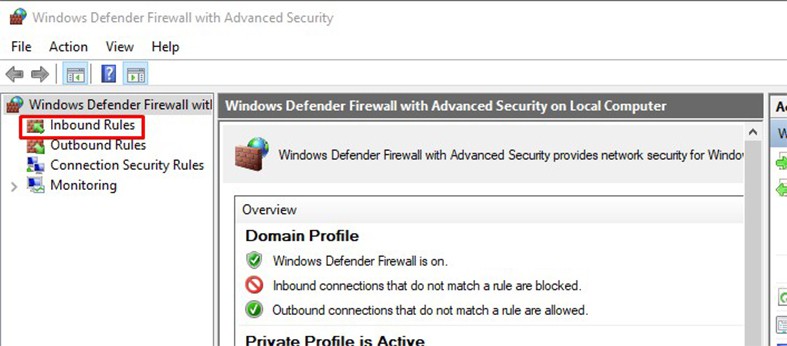
Step 4: Click New Rule
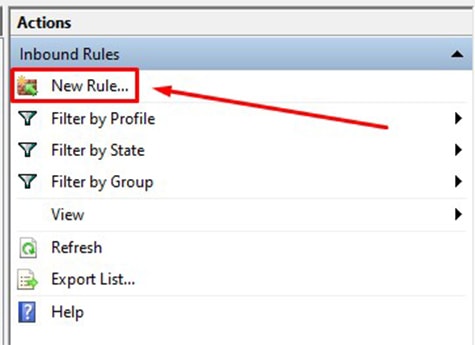
Step 5: Go through the Pop-up Wizard and Select the Port Option
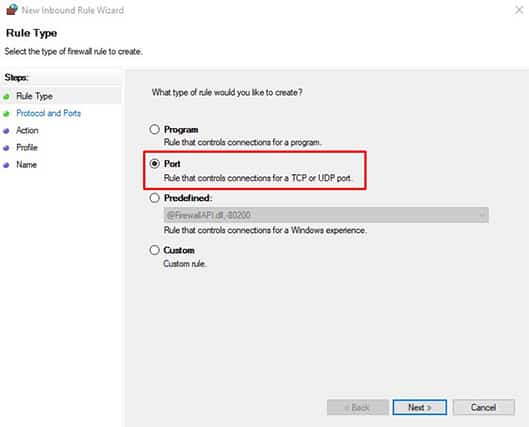
Step 6: Pick the Option That Says ‘Specific Local Ports’
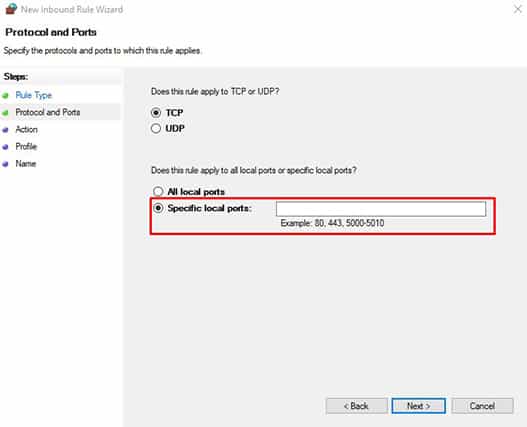
Step 7: Input the Proper Port Number
If you have a web server set up correctly (which you should, otherwise none of this would work), then it should be listening through a port. That web server port number is the one you need to input in the shown field.
To find out the port number the web server is using, look at the address you are using when you open localhost. These addresses can range from 127.0.0.0 to 127.255.255.255. Is it the address 127.0.0.1:8000 or 127.0.0.1:80 or just 127.0.0.1?
In these IP addresses, the part after the “:” is the port number. In the above three cases mentioned, the web server port number is 8000, 80 and 80 (when there is no port number mentioned, it is considered 80), respectively.
Step 8: From the Next Screen, Click on ‘Allow the Connection’
Step 9: Check All Boxes on the Next Screen Under ‘When Does This Rule Apply’
Step 10: Provide a Name
The next screen should have two text boxes. The first one asks you to provide a name for your new rule.
You are free to choose any name you want, but common sense dictates you should go with a name that makes sense to you and the purpose for which you created the rule.
There is also a description box right under the name box. The box clearly mentions it is optional, but again, we suggest that you should give it a description that allows you to fully understand what this rule is for. You won’t always remember why you created the rule, if say, you don’t use it for three or four months consecutively.
Step 11: Click ‘Finish’
After choosing a name for your new rule and providing a description, you should click the button that says “Finish.” That will also save your rule.
So, what’s next? Well, since you wanted to access localhost from another computer, that is what you should do. Before you actually do that, you will need to do a couple of things.
You will have to use a mainstream browser on the other machine and then input the local IP of your current computer into the URL bar of the browser on the other computer. All of this will go smoothly only if the two computers are on the same local network—for example, when you want to show your friend something you have built, but it is only available on your computer, which is on the same network as your friend’s computer (like in a university setting).
Note:
If you don’t know the local IP of the computer you are currently using, open up the terminal window and type the command ipconfig.Conclusion

The main purpose why web servers use localhost is to properly program applications that will eventually use the internet for communication. The development process of any app requires that the software is able to work as planned once it is given internet access, which is why web development and networking professionals use this system in testing software programs.
Localhost is used in many other situations as well—like in loopback testing, for example, where developers use localhost to test unfinished products. Moreover, localhost allows them to avoid the whole network detour part while stimulating a legitimate connection. In other words, they only have to expose their application or product to their own system rather than outside systems.

