Table of Contents
What Is CI/CD Pipeline Security?
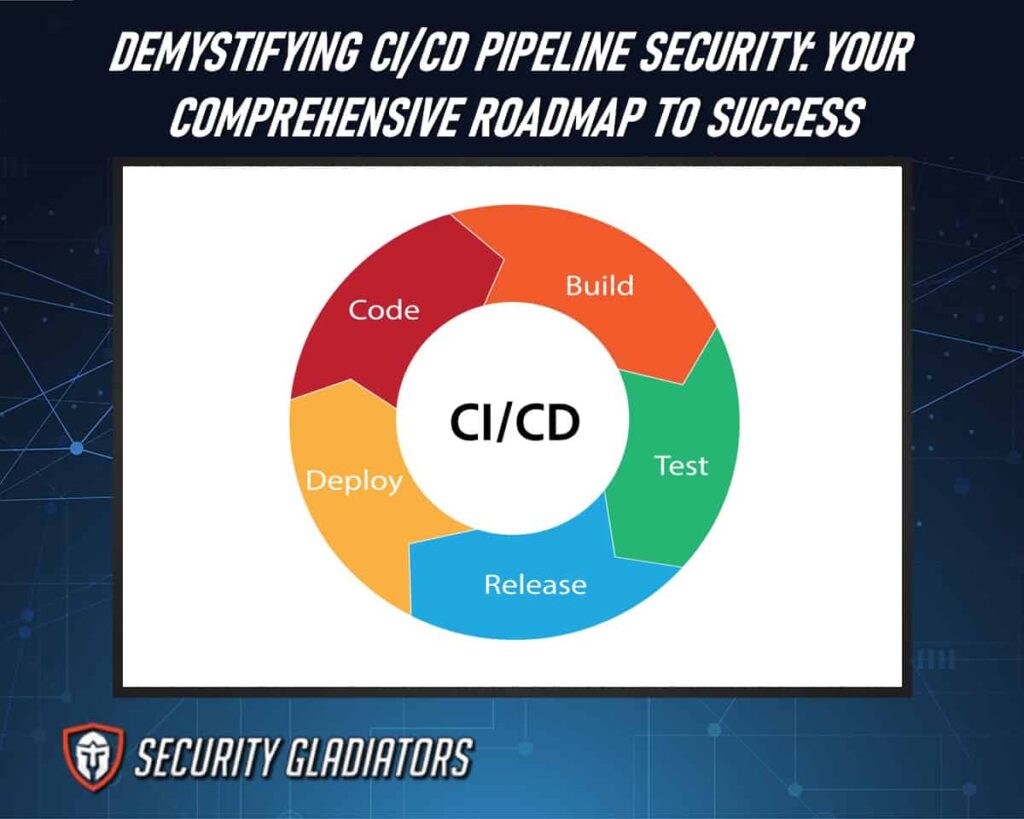
CI/CD pipeline security refers to the implementation of measures and best practices to protect the Continuous Integration and Continuous Deployment (CI/CD) process throughout the software development lifecycle. It involves safeguarding the CI/CD pipelines against potential threats, vulnerabilities, and unauthorized access. Security measures for software security include access control, secure configuration management, code signing, static and dynamic application security testing, secrets management, continuous monitoring, and incident response planning. By addressing security at each stage of the CI/CD pipeline, organizations aim to ensure the integrity, confidentiality, and availability of their software applications, reducing the risk of security breaches and vulnerabilities in the deployed code.
Why Is CI/CD Pipeline Security Important?
CI/CD pipeline security is crucial for several reasons:
Protection Against Supply Chain Attacks
CI/CD pipelines are integral parts of the software supply chain. Securing the pipeline is essential to prevent attackers from injecting malicious code or compromising dependencies. Ensuring the integrity of the source code, dependencies, and build artifacts helps safeguard against potential supply chain attacks.
Prevention of Unauthorized Access
CI/CD pipelines often involve sensitive processes and configurations. Securing the pipeline helps prevent unauthorized access and ensures that only authorized personnel can make changes to the pipeline configuration, code repositories, or deployment environments. This reduces the risk of malicious actors tampering with the pipeline.
Mitigation of Credential Exposure
CI/CD pipelines often require access to various credentials and secrets for integration with external services, deployment to cloud platforms, or interaction with third-party APIs. Securing the pipeline involves managing and safeguarding these credentials to prevent accidental exposure or unauthorized use, reducing the risk of potential security breaches.
Detection and Remediation of Vulnerabilities
CI/CD pipeline security involves integrating automated security checks and tests to detect vulnerabilities in the code, dependencies, or configuration. This proactive approach ensures that vulnerabilities are identified early in the development process, allowing for prompt remediation before code reaches production.
Compliance and Audit Requirements
Many industries and organizations have specific compliance and audit requirements related to software development and deployment. Securing the CI/CD pipeline ensures that the development process aligns with these regulatory standards. It enables organizations to demonstrate a commitment to security and compliance, which is crucial for maintaining trust with customers, partners, and regulatory bodies.
What Are CI/CD Security Risks?
One must acknowledge the inherent security risks associated with the implementation of continuous integration and deployment (CI/CD) processes to effectively safeguard software development operations and mitigate potential vulnerabilities.
Here are the CI/CD Security Risks:
Insecure Coding
Insecure coding practices pose a significant threat to the overall security of software development operations, leaving organizations vulnerable to potential breaches and compromise of sensitive information. Insecure code can introduce vulnerabilities that can be exploited by attackers, leading to unauthorized access, data leaks, and system compromise.
To mitigate this risk, organizations need to implement rigorous security testing throughout the software development process. This includes conducting regular code reviews to identify and address potential security weaknesses, as well as incorporating secure coding guidelines into the development lifecycle. Additionally, access controls should be implemented at various stages of the CI/CD pipeline to ensure that only authorized individuals have access to sensitive code repositories and deployment environments.
Insufficient Access Controls
Insufficient access controls can lead to unauthorized individuals gaining access to sensitive code repositories and deployment environments, potentially compromising the security of software systems. Access control mechanisms play a crucial role in ensuring that only authorized personnel have the necessary privileges to view, modify, or deploy code. Without proper access management practices in place, there is an increased risk of security incidents such as data breaches or malicious code injections.
To mitigate this risk, organizations should implement strong authentication mechanisms, enforce least privilege principles by granting users only the necessary permissions for their roles, regularly review and update access policies, and monitor user activity for any suspicious behavior. Additionally, secure coding practices should be followed to minimize vulnerabilities that could be exploited through unauthorized access.
Security Misconfigurations
Security misconfigurations can leave software systems vulnerable to attacks and compromise their integrity and confidentiality. These misconfigurations can occur at various stages of the CI/CD pipeline, including during the development, testing, deployment, or production environments.
Common examples of security misconfigurations include:
- Leaving default credentials enabled
- Failing to apply patches and updates on time
- Granting excessive privileges to users or services
- Not properly configuring access controls
Vulnerable Third-Party Libraries
Vulnerable third-party libraries pose a significant risk to software systems as they can introduce exploitable vulnerabilities and compromise system integrity and confidentiality. Third-party code is commonly used in modern software development, allowing developers to leverage existing functionality and reduce time-to-market. However, the use of such components introduces potential security risks, as these libraries may contain known vulnerabilities or be susceptible to supply chain attacks. To mitigate this risk, organizations should conduct thorough software composition analysis to identify any vulnerable third-party libraries in their codebase. This analysis involves scanning the dependencies of an application and assessing its security posture.
Supply Chain Attacks
Supply chain attacks have become a significant concern in the realm of software development and deployment, following the discussion on vulnerable third-party libraries. These attacks involve cyber attackers compromising the security of the supply chain to introduce malicious code or components into software products. By targeting trusted vendors or suppliers, adversaries exploit the trust relationship between organizations and their third-party dependencies, thereby infiltrating systems and potentially causing severe security breaches. Supply chain attacks often exploit known vulnerabilities in third-party libraries, as they can serve as an entry point for attackers to gain unauthorized access to sensitive data or compromise system integrity.
How To Secure the CI/CD Pipeline
Here are different ways of securing the CI/CD pipeline:
Access Control and Authentication
Enforce strict access controls to limit who can modify the pipeline configurations and access sensitive information. Implement multi-factor authentication (MFA) and strong password policies to secure access to CI/CD tools.

Source Composition Analysis (SCA)
A robust implementation of Source Composition Analysis (SCA) enables software development teams to gain insights into the origin and quality of third-party components used in their applications, fostering a sense of confidence and trust in the software supply chain. SCA tools play a crucial role in identifying any vulnerabilities or security risks associated with these components, allowing development teams to take proactive measures to secure applications.
By analyzing the composition of software applications, SCA helps identify any outdated or vulnerable components that may pose a risk to the overall security posture of an application. Additionally, SCA provides visibility into licensing issues, ensuring compliance with open-source licenses and minimizing legal risks. Moreover, source composition analysis empowers development teams by enabling them to make informed decisions about which third-party components are safe for use in their applications, reducing the potential for introducing vulnerabilities or malicious code through insecure dependencies.
Source Code Scanning
Source code scanning involves the automated analysis of software source code to identify potential vulnerabilities, coding errors, and security flaws, ensuring the integrity and reliability of the developed application. It is an essential part of the CI/CD pipeline security measures as it helps in detecting any weaknesses or loopholes in the code that can be exploited by attackers. By scanning the source code, security teams can identify any vulnerabilities or security issues early in the development process, allowing them to make necessary code changes and implement appropriate fixes. This not only enhances the overall security posture of the application but also reduces the risks associated with potential attacks. Additionally, source code scanning can be integrated into automated tests within the CI/CD pipeline to ensure continuous monitoring and assessment of code quality and security throughout its lifecycle.
Dynamic Application Security Testing (DAST)
Integrate dynamic testing tools that simulate real-world attack scenarios. DAST tools can identify security vulnerabilities in running applications and provide insights into potential weaknesses that might not be apparent during static analysis.
Static Application Security Testing (SAST)
Integrate SAST tools into the CI/CD pipeline to analyze the source code for security vulnerabilities. This identifies issues early in the development process, allowing developers to address them before deployment.
Incident Response Plan
Develop and document an incident response plan specific to the CI/CD pipeline. Define procedures for handling security incidents, including communication, investigation, remediation, and post-incident analysis.
Continuous Monitoring
Implement continuous monitoring in your CI/CD pipeline to detect anomalies and potential security incidents. Monitor for unauthorized access, changes to pipeline configurations, and unusual behavior in the development and deployment environments.
Common Challenges Faced When Implementing CI/CD Security Measures
Here are some of the challenges encountered when implementing CI/CD security measures:
Integration Complexity
Challenges arise when integrating security tools into the CI/CD pipeline, requiring compatibility and seamless cooperation between various tools and stages.
Speed vs. Security Balance
Striking a balance between the speed of continuous delivery and the thoroughness of security measures can be challenging, as rapid deployments may sometimes compromise in-depth security assessments.
Automated Testing Limitations
Over-reliance on automated testing may lead to false positives or negatives, requiring a careful selection and configuration of security testing tools to ensure accuracy.
Cultural Shift
Cultural resistance and lack of awareness can impede the adoption of security practices within development teams, requiring a shift in mindset towards shared responsibility for security.
Credential Management
Safeguarding and managing credentials and secrets within the CI/CD pipeline poses challenges, as mishandling of sensitive information could lead to security breaches.
Frequently Asked Questions
How Does CI/CD Security Differ From Traditional Application Security?
CI/CD security focuses on securing the entire software development lifecycle by integrating security measures into the continuous integration and continuous deployment processes. Unlike traditional application security, which often involves manual testing and periodic assessments, CI/CD security emphasizes automated and continuous security checks, enabling early detection and remediation of vulnerabilities. The dynamic and automated nature of CI/CD security aligns with the speed and agility of modern software development, ensuring that security is an integral part of the development pipeline.
Are There Any Industry Standards or Best Practices for CI/CD Security?
Industry standards and best practices for CI/CD security exist to ensure the integrity, confidentiality, and availability of software development processes. These include secure coding practices, vulnerability scanning, access controls, encryption, and continuous monitoring.
How Can Organizations Ensure Continuous Monitoring and Detection of Security Vulnerabilities in Their CI/CD Pipeline?
Organizations can ensure continuous monitoring and detection of security vulnerabilities in their CI/CD pipeline by implementing automated security scanning tools, integrating security testing at each stage, conducting regular vulnerability assessments, and employing threat intelligence feeds for real-time detection.

What Are the Potential Consequences of Neglecting CI/CD Security?
Neglecting CI/CD security can lead to serious security threats, including data breaches, unauthorized access, and compromised customer information. It may result in financial losses, reputational damage, legal liabilities, and regulatory non-compliance for organizations.
Conclusion
Securing CI/CD pipelines is not just a matter of implementing tools; it’s a holistic approach that intertwines technology, processes, and people. By integrating security into every stage of the development lifecycle, from code inception to deployment, organizations can fortify their pipelines against evolving threats.

