Password cracking tools can also be used by system administrators to check for easily hackable passwords. Although traditionally perceived to be used exclusively for criminal purposes, using password hacking tools to test or recover lost passwords is a legal practice. The best password cracker apps can handle multiple targets simultaneously, are usable on different platforms, and support multiple protocols.
The 12 best password cracking tools are listed below.
Table of Contents
1. John the Ripper
John the Ripper is a good choice for a password cracking tool, mainly because of its open-source nature and support for different platforms. The open-source nature means that the code is available to the public, so users do not have to worry about the legality of the software and about potential malware of malicious programs that might be deeply integrated into the software.
Since John the Ripper is open source, users may find the need to use encryption technologies supported by the software. In such cases, external extensions made by other users can be downloaded from the Internet and used with John the Ripper.

John the Ripper is usable for passwords on Windows, macOS, and Linux, along with web apps, groupware, database servers, network traffic captures (such as network authentication and WiFi), encrypted private keys, filesystems, archives, and document files. Additionally, John the Ripper jumbo can support hundreds of hash and cipher types.
The software comes in two variations, the standard John the Ripper product, which is free, and John the Ripper Pro for Linux and macOS for commercial uses. Pricing for John the Ripper Pro is set at USD 250 per hour for a minimum of three hours, or USD 9,000 per week. Fixed price quotes are also available for specific projects.
The flexibility of John the Ripper comes with some disadvantages. Users may find that the software takes some time to set up, and some knowledge of using the command line is also necessary to fully maximize the benefits of John the Ripper.

John the Ripper is safe to use as it runs under the same user privileges for every other program by the user. As for privacy, the cracked password is shown or given only to the user; it is up to each user to take steps to prevent unauthorized access by other users.
There are no legal issues that arise directly from the standard use of the software. Legality is highly dependent on the purposes behind the use of a password cracker, so it is the user’s responsibility to ensure that the use of John the Ripper falls within the permissible confines of the law.
2. Hashcat
Touted as the world’s first and only in-kernel rule engine, Hashcat is another password cracking tool that can help recover different passwords, such as those used for WiFi, documents, and other file types. Multiple platforms and operating systems are supported, such as Windows, Linux, and macOS for desktop. There is also mobile support for Android, iOS, and Windows mobile.
The main feature of Hashcat is automatic password recovery. Hashcat is also known to be one of the fastest password cracker apps.
Note:
Hashcat has a variety of password cracking methodologies available, ranging from brute force attacks to hybrid masks using a wordlist. However, Hashcat is limited in the kinds of passwords that can be recovered. Unlike John the Ripper, which can recover passwords for databases and operating systems, Hashcat is mostly limited to documents such as PDF, Word files, and Excel files, in addition to WiFi passwords.Hashcat is available to download for free.
Hashcat does not store any cracked passwords on its servers, ensuring that any passwords deciphered by the user are given to that user alone. For this reason, it is possible to say that Hashcat provides privacy.
In terms of safety, Hashcat does not access or modify the user’s files in any way. The software is limited to deciphering passwords of selected files or the user’s Wi-Fi network in the background, so users do not have to worry about the software tampering with important files and sensitive information.
Using Hashcat is legal, provided that the purposes for its use are legal as well. As a general rule, legal purposes for using password crackers involve recovering one’s passwords or passwords that the user is authorized to recover on someone else’s behalf.
3. Medusa

Medusa is an online password-cracking tool that supports plenty of protocols, including HTTP, SSH, FTP, CVS, AFP, POP3, Telnet, and more. The software works as a login brute-forcer; many credentials using as many protocols as possible are inputted to arrive at the correct password.
According to the software’s website, Medusa’s key features are thread-based parallel testing, flexible user input, and modular design. Parallel testing also allows the software to perform simultaneous brute-force testing. The flexible user input allows the user to configure each item as either single-entry or multiple-entry, and the modular design means that Medusa requires no modifications to extend the supported list of services.

Medusa is a command-line tool that currently supports Linux, SunOS, BSD, and macOS. There is currently no support for Windows. For Kali Linux users, Medusa is already pre-installed. Linux users who do not have Medusa pre-installed can type “sudo apt-get install medusa” on the command line to install Medusa. Users can also type the “medusa” command on the command screen to see the available commands used with the software.
As with other password crackers, Medusa is merely a command tool that cannot read, modify, or otherwise tamper with users’ files. Medusa is safe to use, provided that the user’s hardware can run the program itself.
As for privacy, Medusa does not store any information obtained for or inputted by the user. Any cracked passwords are available only to the user, which may allay some privacy fears.
Medusa is completely legal to use as long as users ensure that the passwords obtained are their own or belong to people who have given authority or consent for password recovery.
4. THC Hydra
THC Hydra has seen many comparisons to Medusa as a password cracker, but there are notable differences between the two software. Like Medusa, THC Hydra is also an online password cracking tool that uses a brute-force password guessing method. One key difference is that THC Hydra can be installed on Windows, macOS, Linux, Free BSD, and Solaris, notably more platforms than Medusa supports. In addition to the brute-force method, THC Hydra can also use dictionary attacks, using external wordlists.

THC Hydra also supports a wide range of protocols, including Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC, and XMPP.THC Hydra’s vast number of supported protocols is what makes the software stand out from the others on the list.
THC Hydra is free and also open-source, with over 25 regular contributors. THC Hydra users looking for additional features not found in the “official” code may find these features in user-made extensions.

To begin using THC Hydra, users can download xHydra, a GUI that makes the software much easier to use. xHydra is also pre-installed on Kali Linux operating systems, but users of other Linux OS’s may install xHydra by using the command “sudo apt-get install hydra-gt”. Like the main software, xHydra may also be downloaded from the Github repository. By typing “hydra -h”, users will be shown the various commands and syntaxes that can be used with THC Hydra.
THC Hydra does not collect or store any recovered passwords on online servers. Such passwords are shown only to the user, and there have been no reports to date of THC Hydra making unauthorized modifications to user’s files.
The mere use of THC Hydra is not illegal. Legality or illegality is largely dependent on the motives and purposes behind each person’s use of the software.
5. WFuzz
WFuzz is another brute-force password-cracking tool, much like Medusa and THC Hydra. Another feature of the program is finding hidden resources like servlets, directories, and scripts. The tool also supports multiple injection types with multiple dictionaries.

While most password cracking tools are used to detect easily-cracked passwords, WFuzz can also find injection vulnerabilities in an application, such as XSS injection, SQL injection, and LDAP injection. WFuzz stands out as more than just a password cracker; the software also allows users to detect vulnerabilities and secure Web applications as a whole.
WFuzz is a free tool that makes this list because of its multi-platform support. The software can be installed on Windows, macOS, and Linux. Since WFuzz uses a command-line interface, users may have to be familiar with commands to maximize the use of WFuzz.
To start using WFuzz, users can type “-h” or “–help” to bring up all available commands that can be used with WFuzz.
Note:
Users concerned about privacy and safety can rely on the open-source nature of WFuzz, which allows the program’s source code to be scrutinized by the public. Fortunately, there have been no reports of privacy breaches or safety concerns from WFuzz users.WFuzz is legal to use, provided that users limit their use of the program to the legal recovery of passwords.
6. Brutus
Brutus can recover passwords and usernames from websites, operating systems, and other applications. True to its name, Brutus utilizes a brute-force dictionary attack to retrieve passwords.

The software supports multiple platforms, including FTP, HTTP, POP3, SMB, Telnet, NetBus, IMAP, and NNTP. There are also multiple brute force modes that users can choose from to tweak the exact methodology by which Brutus cracks passwords.
Brutus also supports multiple connections, allowing for up to 60 simultaneous connections. The user can also tweak the precise brute force modes.
Unlike most password crackers on the list, Brutus does not support any operating system other than Windows desktop. Additionally, Brutus cannot crack passwords for social media and email accounts. The program also cannot hack complex passwords that consist of numbers, letters, and symbols.

Brutus is a free software that does not require command-line knowledge or familiarity from the user. The graphics user interface allows for relatively easier use than more powerful and more technical password crackers that use only command-line interfaces. For this reason, Brutus is recommended for simple projects and users who are unfamiliar with complex interfaces.
The program’s capabilities are limited solely to brute-forcing a given account’s passwords. Since Brutus does not use any external files like wordlists, users will face minimal privacy issues, if any. Additionally, the only safety concerns that users may face are hardware-related, as password crackers can be quite taxing on computers. There are no reported instances of users’ computers being compromised as a result of using Brutus.
As with all password crackers, Brutus can be used legally, provided users limit password recovery to their passwords or passwords of people who have authorized password recovery.
7. RainbowCrack
RainbowCrack is another password cracker tool that uses a rainbow table attack to decipher passwords in hash form. The main technique used is the time-memory trade-off technique which can be accelerated with multiple GPUs. Users can use RainbowCrack to generate rainbow tables to be used in the password cracking process or download preexisting rainbow tables from the Internet.
RainbowCrack also offers rainbow tables for LANMAN, MD5, NTLM, and SHA1 password systems, which is why the program made the list. Alternatively, the user can download paid rainbow tables from RainbowCrack as well.

Using RainbowCrack is easier with a GUI, where the user only needs to click on File and “Add Hashes” to get started. The basic command is “rcrack” for the command-line interface, followed by the drive location and the corresponding hash to crack.
There are no recorded instances of RainbowCrack gaining unauthorized access or causing crashes to computers with capable hardware. RainbowCrack also does not store any passwords on a server that allows access or transmission to other people.
As with the other password crackers on the list, RainbowCrack is also legal to use.
8. L0phtCrack
L0phtCrack is an open-source password cracking tool that can be used to crack Windows passwords. The main techniques that L0phtCrack uses are the dictionary attack and the brute-force attack, which allows the program to generate and guess passwords.
In addition to password-cracking features, L0phtcrack also offers routine password security scans as a network security preventive measure. The user can choose between daily, weekly, or monthly frequency options.
While formerly a paid product, L0phtCrack is now available as a free download and can be used and installed only on Windows devices. Despite being used only on Windows, L0phtCrack can still be used to crack MD5 and DES-encoded password files from Unix or Linux machines. The program’s ability to crack multiple protocols and encoding systems is why L0phtcrack is on this list despite being usable only on Windows.

L0phtcrack is unique in that first-time users are greeted with a simple tutorial when launching the program for the first time. Additionally, L0phtcrack also has management functions like reporting and account disabling, making the software more flexible than conventional password cracking apps.
L0phtcrack also uses a graphical user interface (GUI) as opposed to a command line, making password recovery much easier than manually typing in commands that users will have to look up before using the software.
Note:
After the cracking process, the passwords are displayed on a table in L0phtcrack’s GUI, but the passwords are not uploaded online. Only the user has access to the passwords, allowing for a secure and private password cracking session.L0phtcrack is also legal to use as long as the passwords to be recovered are owned by the user or recovered with the consent of the password owner.
9. OphCrack
OphCrack is a free, open-source password cracker that uses rainbow table attacks to decipher passwords. Specifically, the program cracks LM and NTLM hashes. LM hashes are for Windows XP and earlier operating systems, while NTLM hashes are for Windows Vista and subsequent Windows operating systems. The rainbow attack has been used to decipher an 8-character password in just six seconds, using a rainbow table that contains uppercase and lowercase letters and numbers.
OphCrack comes with free rainbow tables for Windows XP, Windows Vista, and Windows 7. The software can also be used on the Linux and FreeBSD operating systems, but to a limited extent.
To simplify the password-cracking process, OphCrack offers a free live CD that works on Windows-based operating systems.
Since Ophcrack is primarily for recovering Windows OS passwords, most users will be unable to use Ophcrack the same way other password crackers are used. This is where the Live CD comes in, which contains a small operating system that can be run independently.

The live CD should be downloaded on a different computer and transferred to a CD or other bootable drive, which will then be used on the locked computer to recover the OS password.
As an open-source tool, OphCrack’s documentation is made available for the public to read. This preempts any privacy issues, as the public would quickly know if OphCrack has hidden code that allows it to access user files or leak cracked passwords. To date, there are no reported issues regarding OphCrack’s privacy or safety.
OphCrack is also legal and widely used by testers and network administrators to test passwords and spot weak password policies.
10. Aircrack-ng
Aircrack-ng is a good choice for cracking WiFi passwords, allowing users to crack passwords that use either the WEP or the WPA/WPA2 PSK standards. As for the technique, Aircrack-ng uses a dictionary attack with multiple supported algorithms, including PTW and FMS.
Aircrack-ng is free and is available primarily for Linux, but can also be installed on Windows, macOS, FreeBSD, OpenBSD, NetBSD, Solaris, and eComstation 2 operating systems. The software uses a command-line interface, which makes Aircrack-ng more technical, but a free live CD makes the learning process easier for users.

Although limited only to Wi-Fi passwords, Aircrack-ng’s extensive multi-platform support, along with its ability to crack different standards for Wi-Fi passwords, makes the software a notable entry on the list.
Using Aircrack-ng to crack Wi-Fi passwords can be slightly more complicated. To get started using THC Hydra, the software will first have to be started in monitoring mode, and drivers will have to be set up before the wireless client can be unauthenticated, which allows the pre-shared key to be identified.
Aircrack-ng is primarily a network scanner that happens to have password cracking capabilities. There are no reports of Aircrack-ng transmitting recovered or deciphered passwords, although the software has been noted to be able to transmit packets, which can be a security concern for some.
As a network scanner primarily, Aircrack-ng is legal to use. Using Aircrack-ng’s password cracking capabilities, however, should be confined to authorized uses of password recovery.
11. CrackStation
Unlike most entries on the list, CrackStation does not have a standalone program installed on the computer. Rather, CrackStation is a free web-based password cracker that uses the dictionary attack technique to crack hashes, which allows the program to be used on any operating system, even on mobile.
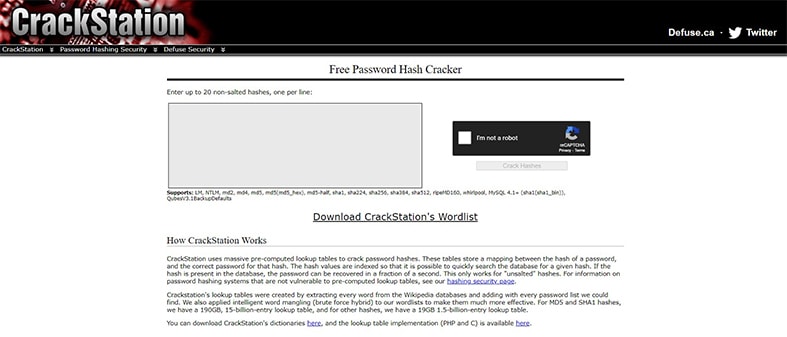
The program supports multiple protocols, such as LM, md2, md4, md5, md5(md5_hex), md5-half, MySQL 4.1+ (sha1(sha1_bin)). NTLM, sha1, sha224, sha256, sha384, sha512, ripeMD160, whirlpool, ), and QubesV3.1BackupDefaults. However, only non-salted hashes without any attached random strings can be used, limiting CrackStation’s password-cracking capabilities.
CrackStation allows up to 20 non-salted hashes to be inputted on the interface. MD5 and SHA1 hashes are referenced with a 190GB lookup table that contains 150 billion entries, while other hashes are referenced with a 19GB table that contains 15 billion entries. The tables were filled by extracting every word from Wikipedia databases and adding passwords from all password lists that the developers could find.CrackStation’s dictionaries can also be downloaded separately.

To use CrackStation, users can place up to 20 non-salted hashes on the website, which is a relatively simpler step than the more complex setups required for other password crackers.
According to CrackStation’s privacy policy, any hashes that users crack are not stored in any way by the website. However, the website states that there is a possibility that connections are being intercepted by government agencies such as the NSA, which may prompt some users to opt for other tools instead.
Despite any possible monitoring, the mere use of CrackStation is legal as long as users do not attempt to crack passwords that they are not authorized to.
12. Password Cracker

Password Cracker is another desktop tool that can uncover hidden passwords. Since most operating systems hide passwords using round dots or asterisks for security, recovering these passwords can be difficult, especially for users who have relied on autosave features to store most passwords.
Password Cracker also supports multiple languages and is available as a free download. However, it can only crack passwords for Windows applications. Additionally, there is no support for password recovery for MS Office password-protected documents since the password encryption for MS Office is not supported by Password Cracker.
Despite the limited capabilities of Password Cracker, the software still makes the list for its relative ease of use, considering that Password Cracker is limited only to Windows applications.

Like other password cracking apps on the list, Password Cracker is also safe to use, with millions of downloads and no reported instances of hash leaks. Password Cracker may be used legally, provided that users limit password cracking to owned passwords.
Password Cracker is one of the simplest password cracking tools to use in the list, although its capabilities are limited. Windows usually hide passwords in asterisks or dots, but pasting the password in Password Cracker’s GUI allows the user to hover over the Test field to see the real password.
Password Cracker is a simple, offline tool so users do not have to worry about any privacy issues or data leaks when using the program.
How does a Password Cracker App Work?

For password cracker apps, the precise methodology differs from app to app. In essence though, password crackers use a reference list, called a “table,” containing commonly known passwords and put these into the system until the correct password is found. They all essentially create variations from a dictionary of known common passwords.
The specific techniques all use a variation of the dictionary method, except the brute-force method, which relies on entering all possible combinations, starting from shorter lengths to longer ones. However, some modes of brute-forcing still make use of a lookup table containing commonly known passwords or previously leaked passwords to speed up the password cracking process.
Is It Possible to Crack Strong Passwords with a Password Cracker?

Yes. In theory, all passwords can be cracked but it is impractical to crack strong passwords as it takes much longer. The main factors that determine the crackability of a password are length, complexity, and uniqueness.
Strong passwords use a combination of uppercase and lowercase letters, numbers, and symbols for security. These kinds of passwords take longer to crack, as they are less likely to be found in wordlists. Strong passwords also cannot be brute-forced in a short amount of time and tend not to be used on any other website or network. While all passwords can be cracked given enough time, sufficiently complex and lengthy passwords will require so much time that cracking is realistically impossible. Certain websites allow users to input their passwords to determine how long the passwords will take to be cracked. For long and complex passwords, the cracking process can take upwards of millions of years, which is virtually impossible for the vast majority of computers.
What Type of Accounts can be cracked with a Password Cracker?
Passwords for different kinds of accounts can be retrieved with a password cracker, and whether the password can be recovered will depend on the exact password cracker used.
- Social media accounts: The growth in social media use has scaled up data privacy risks. Social media users have been advised many times to use different passwords for different accounts to prevent data breaches. There are free-to-download password unlockers, such as an Instagram password cracker. One such decryptor is the John the Ripper password cracker.
- Email accounts: Email account passwords are as vulnerable as social media accounts. A forgotten email account password may be retrieved using a Gmail password cracker or other email password crackers.
- RAR/Zip: A user may suddenly need to retrieve a file from a password-protected archived folder, but the user has forgotten the password. The required file may still be retrieved using either a RAR password cracker or a zip password cracker. Some of these password cracker apps are similar to Hashcat.
- PDF and Microsoft: Files protected by passwords may still be viewed and edited by the user even if the password has been forgotten using a PDF password cracker. Similarly, a decryptor can crack an excel password or even a Windows 10 password.
- Operating systems: Most operating systems like Windows allow users to secure access by requiring the input of a password. For users who have forgotten the password for the OS, such as Windows 10, and are locked from accessing the computer, or users who want to review the security level of passwords, operating system password crackers can help crack Windows 10 passwords.
- Databases: Databases stored on applications like SQL, Oracle, or DbVisualizer are usually secured by passwords to prevent unauthorized access to sensitive information. Database password crackers like John the Ripper can help users recover passwords to regain access.
- WiFi: Networks like WiFi or other closed networks use passwords for security, and WiFi networks are known to be one of the most vulnerable access points to an entire network. To ensure that only authorized people have access, network administrators can use network and WiFi password crackers to monitor password security and recover lost passwords securely.
What Techniques do Password Crackers Use?
Different password crackers use different techniques, but the dictionary, brute-force, and rainbow attack are three of the most commonly used techniques.

- Bruteforce Method: The brute-force method involves inputting all possible combinations of letters, numbers, and symbols with increasing characters until a match is found. The method requires computers with strong computational capabilities. However, with modern technology such as multi-core processors and graphics processing units allowing computers to test billions of passwords per second, shorter and simpler passwords are easily cracked and recovered through a brute-force method.
- Dictionary Method: In the dictionary method, the password cracker uses a list of known or commonly used passwords and inputs the passwords in the system until there is a match.
- Rainbow Table Attack: The rainbow table attack, such as the one used by Ophcrack, is a more sophisticated version of dictionary attacks. The hash form of the password is used and cross-referenced with a data table containing the hash versions of millions of other passwords. The data table contains common passwords and their hashed versions, with some data tables being so extensive as to reach hundreds of gigabytes’ worth of storage.
How Long does It Take to Crack a Password with a Tool?

The speed at which password hacking tools crack a password differs depending on factors such as the complexity and length of the password, the methodology used by the password cracking tool, and the capabilities of the user’s computer, mainly the CPU and GPU.
There is no exact answer that can determine how long a password cracker can decipher a password. The general rule is that simpler and shorter passwords can be deciphered quickly, while longer, unique, and complex passwords take substantially more time to be recovered.
Is It Legal to Use a Password Cracking Tool?

Yes, but the legality of password cracking tools largely depends on the purpose of the user. Password cracking apps, along with the use of such apps, are not illegal per se.
As with any tool, password cracking tools can be both used for legal and illegal purposes. Legal purposes include recovery of the user’s password or data or the recovery of data that the user has been authorized to crack. Private companies that regularly manage sensitive data and information also want to ensure that passwords used on the system are secure to prevent unauthorized access.
However, illegal uses include cracking passwords of users who have not given prior consent or knowledge.
The password crackers presented on the list are legal to download, but the legality of the use depends on a case-to-case basis. Each user is responsible for ensuring that password cracking activities fall within the permissible confines of the law.

