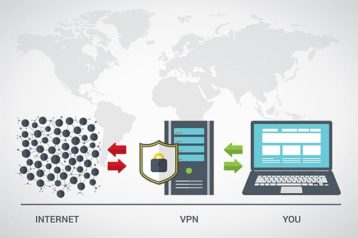
A Virtual Private Network (VPN) is a tool that enables online users to connect to a secure and private network over public internet. Online consumers may not understand what is a VPN but nevertheless use VPN services and various VPN protocols to gain anonymity and data security in the online world. VPN services hide a given user’s IP address and hence make online communications untraceable. VPN services are also useful tools to form encrypted and secure connections which come with the added benefit of enhanced privacy.
There are many types of VPNs available in the market today. The two most common types of VPN are Remote Access VPN and Site to Site VPN. The remote access VPN type is better suited to individual users while the site to site VPN type is better at meeting corporate needs. The average cost for both types of VPN can vary depending on the features included and the requirements of the corporation in question. Generally speaking though, remote access VPNs cost between $2 to $11 per month depending on the length of the subscription period. For Site to Site VPNs, there are lots of payment plans and options. The service offering site-to-site VPNs usually tailors the price according to the setup and requirements of the organization in question. Generally speaking, site-to-site VPNs charge approximately $0.05 per hour.

While talking about VPN services, VPN protocols must also be acknowledged as they essentially represent all the instructions and processes that VPN services use to ensure a stable and secure VPN connection for their customers. Without VPN protocols, VPN services would find it impossible to establish a VPN client-to-server connection and enable encrypted communications. VPN protocols also enable the mix of encryption and transmission protocols which is necessary for identification prior to setting up a VPN connection.
Note:
Just like VPN services, VPN protocols are used to set up different types of VPN connections but mostly come down to a balance between security, reliability, and speed.VPN protocols also come in different shapes and sizes. The most common ones in use today across all platforms are OpenVPN and IKEv2 with AES 256-bit encryption.
Table of Contents
What are the Types of VPNs?

Types of VPN are listed below.
- Remote Access VPN
- Site-to-Site VPN
The remote access VPN can work for both home users and businesses as remote-access VPNs can bypass geo-restrictions and access blocked content. The Site-to-Site VPN is better suited to corporate use as it is better at connecting offices of the same company located in different regions.
1. Remote Access VPN
Remote Access VPN connects online users to remote servers (of the user’s choosing) which may be located in the user’s current country or a different one. Remote Access VPNs have their own VPN network and encryption processes which protect user data and guard the user’s online privacy.
When companies use remote access VPNs, companies enable workers to access company files, printers, and other resources via a private network from a remote location.
Remote Access VPNs are easy to install and use and hence are suited for residential users.
Residential users can use remote-access VPNs to access geo-restricted content and blocked websites while keeping traffic data private and secure.
2. Site to Site VPN
Site to Site VPNs primarily serve corporations that may have offices located in different locations. Site to Site VPN’s main feature is its ability to connect networks belonging to one office in a particular location to another network belonging to an office in another location.
If those offices are of the same company, the site-to-site VPN becomes an Intranet based VPN. If offices belong to different companies, the site-to-site VPN becomes an extranet VPN service. Site-to-site VPNs can establish digital communication lines between networks that can be present on different continents.
The benefit of using the site-to-site VPN is the privacy and security of any communications or activities that may happen between two given networks belonging to the same or different companies. And since site-to-site VPNs require authentication before communication lines can be established, they are perfectly suited to a situation where an employee wants to access sensitive files and other types of content over the internet from a remote office and/or collaborate with another company over the internet.
What are the Types of Virtual Private Network (VPN) Protocols?

VPN protocols are instructions that VPN services use to set up secure and private communications with help from servers and VPN clients. VPN protocols determine how the user’s data moves between the user’s computer and its final destination and what type of encryption protects the data.
Here are the types of virtual private network protocols for both the remote access VPN and site to site VPN types.
- WireGuard
- IPSec
- L2TP
- OpenVPN
- IKEv2
- SSTP
- SSH
- SSL and TLS
WireGuard is the latest VPN protocol of all VPN protocols and is different from other VPN protocols because it is open source and the easiest to set up. PPTP supports a lot of devices and platforms but is not secure enough. IKEv2 differentiates itself by being ultra compatible with mobile devices and is open source. SSTP is considered the standard protocol that offers decent security and is not as easy to detect and block as some of the other protocols.

The OpenVPN protocol is currently the most versatile protocol as it supports a wide variety of online activities, makes use of strong encryption, and is open source.
SSL and TLS work in tandem where the client is the web browser. SSL and TLS restrict application access to enhance security and privacy. The IPSec/L2TP protocol is another VPN protocol call that makes use of a single port to form a VPN connection. The SoftEther protocol is different from other protocols in terms of specificity. It works best for SoftEther VPN which takes advantage of softether SSL version 3. The final protocol is SSH which transfers data through an encrypted tunnel via an SSH client to a remote server while using a local port.
1. Internet Protocol Security (IPSec)
The Internet Protocol Security or IPSec is one of the more established protocols that encrypts the user’s internet data packets and verifies the IP communication session before sending it over the network. Because IPSec encrypts user traffic, this VPN protocol is easily able to hide data packets belonging to the user from various endpoint applications.

IPSec provides all the necessary tools to enable any number of devices to communicate in a secure environment.
The Internet Protocol Security makes use of UDP port 500 for forwarding user traffic uninterrupted by any installed firewalls.
IPSec was published in 1995.
One of the main advantages of using IPSec is the lack of dependency on applications. IPsec is at its core a network layer protocol. Hence, IPSec is not concerned with the application used. It modifies the operating system.
A key disadvantage of using the IPSec protocol is that this VPN protocol not only decreases download speed but also makes connecting to the internet via various clients slower. IPSec also has some compatibility issues with applications that do not support IPSec standards. IPSec makes it difficult to switch networks as well once a connection has been established if there is a firewall present.
2. Layer 2 Tunneling Protocol (L2TP)

The Layer 2 Tunneling Protocol (L2TP) is a standard VPN protocol that passes internet traffic through a private tunnel. Most VPN services offer L2TP with PPTP for more privacy and anonymity. The most common use of the L2TP protocol is that of support. ISPs also use L2TP for some operations.
Since L2TP on its own cannot encrypt data, it uses IPSec for encryption. L2TP/IPSec makes this VPN protocol very strong with a high level of encryption.
Microsoft and Cisco are the two companies that worked together and published L2TP in 1999. At the time, it was considered a successor to the PPTP protocol, and hence, the L2TP protocol takes many of its features from PPTP.
The main advantage of using L2TP/IPSec is security. Once paired with IPSec, the combination can deliver 256-bit encryption keys. L2TP also supports many platforms such as Mac, Linux, and Windows which is fairly uncommon in VPN protocol options. It is also easily configurable on mobile devices as many platforms have native support for L2TP. L2TP completes the data encapsulation process via UDP hence firewalls usually don’t bother it.
The main disadvantage of using the L2TP protocol is eavesdropping since it uses pre-shared keys. A service providing pre-shared keys has access to the said keys and that can result in hackers getting hold of them and launching malware attacks.
L2TP also has limited port support, similarly to PPTP. Any decent NAT firewall can block it if configured correctly. Finally, as it offers such thorough security, L2TP does slow down internet connection slightly more than other VPN protocols.
3. Point–to–Point Tunneling Protocol (PPTP)

The Point-to-Point Tunneling Protocol is a VPN protocol that connects different networks to each other. The PPTP protocol is one of the oldest protocols available and uses a communication rule set that can protect even a company network. It can handle such VPN connections competently. In terms of privacy, it ranks high among various other VPN protocols and hence many applications use PPTP to encrypt data.
The developers of the PPTP protocol took 10 years to fully code PPTP and released it in 1995. PPTP enhances the security features offered by PPP. More specifically, PPTP started offering a tunneling feature. Initially, only the Windows platform supported PPTP but quickly other platforms have also started to offer PPTP.
Modern VPN protocols do offer better encryption but PPTP still has its benefits.
For example, while PPTP is not the most secure of VPN protocols, PPTP does offer great compatibility options. PPTP is fully supported by platforms such as Linux, Mac OS, and Windows. PPTP works with lots of other devices as well.
The second advantage is that it is easy to use. And because PPTP doesn’t require a lot of setup steps, PPTP is very fast on all platforms.
PPTP does also have a number of disadvantages. Firstly, firewalls can block PPTP fairly easily with the right configuration. Since PPTP doesn’t work well with NAT, any router that uses NAT must have an exception for PPTP Passthrough. Modern cybercriminals have learned to exploit PPTP due to its weaker encryption.
4. Secure Sockets Layer (SSL) and Transport Layer Security (TLS)

The Secure Sockets Layer (SSL)/ Transport Layer Security (TLS) is another popular protocol that can encrypt user data that travels through the internet. It makes a vast number of different online communications possible.
TLS is a successor of SSL and both provide security features and encryption which enable commerce to take place in the online world. Unlike some of the lesser-known protocols, SSL and TLS have both received several updates over the years. That has allowed SSL and TLS to remain secure even today.
Then in 1999 TLS was released and quickly saw the community adopting TLS as The Internet Engineering Task Force (IETF) made TLS a standard. IFTF also named the protocol Transport Layer Security (TLS).
Most entities that implement SSL do so in a combination with TLS. TLS is responsible for encrypting online traffic. Users who access websites via HTTPS addresses get protection from TLS. However, many other applications use TLS as well, such as Usenet and email.

The main advantage of SSL TLS is secure web servers which in turn means secure user data. SSL/TLS implementation, if done properly, can show a certain amount of trust as the address bar on most browsers turn green in color. SSL and TLS also enable verification as visitors to a given website can know for sure that the site in question is legitimately the site it claims to be. SSL certificates also guarantee the integrity of data. Finally, SSL/TLS helps with ranking one’s websites better on search engines like Google.
The main disadvantage of using SSL is the price. There are free SSL certificates available but a paid one is considered better as it offers more security. Another disadvantage is the setup process. If SSL is not set up right, visitors to a given site will get a warning message and hence will stay away from that website even if it is legitimate. Web servers using tools such as proxy caching can get into trouble as it is difficult to cache encrypted traffic.
The final disadvantage in using SSL/TLS is the difficulty on mobile. SSL/TLS was developed when web-based applications ruled the online world. As this is no longer the case it can take effort and capital to buy any needed modules or software changes from vendors.
5.Secure Shell (SSH)

Secure Shell (SSH) is another protocol that secures data and makes communications private. SSH also allows for secure execution of commands and file transfer between two machines.
Most of the time, network administrators use SSH to take advantage of the security SH offers. Businesses use SSH to control their websites and log in/log out of their accounts.
Tatu Ylonen, a Finland resident, created Secure Shell in 1995 after it was found that hackers had launched a password sniffing cyberattack in the university Tatu was studying in. SSH mainly focused on security and encryption instead of using plain text for communication.
Then after a few years Bjoern Groenvall, a programmer based in Sweden, made a fork of SSH called OSSH after Tatu Ylonen set up SSH Communications Security Corporation to license and profit from SSH.
Note:
The most important feature of SSH is the extra layer of security SSH adds to any communication in the form of authentication.As such, the primary advantage of using SSH is encryption. SSH encrypts data when data is being transmitted. SSH also authenticates the source and can generate an audit trail. Public key authentication is also available instead of the user having to use an encrypted password. SSH can filter IP addresses for logins via resolved domain and listed keys. SSH can also save time for webmasters who can handle SSH as SSH allows hosting accounts control via remote server control.
The main disadvantage of using SSH is complexity. SSH is complex to administer. Further, because of the authentication process, SSH is also slower. That is especially true where there is no DNS available or IP address at the source that refuses to resolve.
6. OpenVPN

OpenVPN is a protocol that makes use of the most modern virtual private network techniques to secure the two types of VPN connections mentioned before, namely, site-to-site and point-to-point connections. OpenVPN is also a software that has become very popular since the mid 2005s.
OpenVPN was created by James Yonan in 2001. Yonan wanted to bring security in addition to usability to the VPN community which until that point had failed to offer both. In addition to that, Yhan also wanted to explore modern methods of securing online communications and changing a given device’s IP address.
Yonan found some success in using TAP/TUN devices as a suitable model for networking. Yonan also made the OpenVPN protocol open-source and named OpenVPN as such. There are two versions of OpenVPN. The latest version has improved performances on Windows and other platforms.
This is important:
The OpenVPN protocol mainly manages client-server communications. To create a tunnel OpenVPN needs a VPN server and a VPN client. For authentication and encryption, the OpenVPN protocol relies on the OpenSSL library. OpenVPN has the ability to use both TCP and UDP for transmitting data.OpenVPN’s main advantage is security. OpenVPN is the most secure protocol currently available as OpenVPN takes advantage of security layers such as peer authentication, HMAC packet authentication, and pre-shared keys. In addition to that, OpenVPN also covers any and all types of VPN configuration setups. In simpler terms, OpenVPN is highly configurable.

Some of the other advantages include widespread support, support for multiple strong cryptographic algorithms, the fact it is open-source, and lively community support. OpenVPN has support for perfect forward secrecy as well as encryption levels reaching as high as 1024-bit.
The main disadvantage of using OpenVPN is the overheads. With so many privacy and security features on offer, OpenVPN is not a light protocol. It also runs into some proxy problems as it is complex to implement. To set OpenVPN up properly, users need to install third-party applications. And even though OpenVPN offers great configuration options, it is difficult to configure OpenVPN.
7. IKEv2

The Internet Key Exchange Version 2 (IKEv2) is a newer encryption protocol that is used to secure internet data.IKEv2 is a successor to the less popular IKEv1. As is the case with a couple of other protocols, the IKEv2 was developed by Cisco with some help from Microsoft in 2005. At its core, the IKEv2 represents only a tunneling protocol. When combined with a good authentication standard though, it turns into a complete VPN protocol. The IKEv2 secures internet traffic at a more basic level via Security Authentication (SA).
Even though Microsoft and Cisco partnered to develop IKEv2, the protocol does have open source versions. The three most widely used open-source editions of IKEv2 are OpenIKEv2, strongSwan, and Openswan.
Compared to IKEv1, the IKEv2 offers many security and privacy enhancements. For example, the IKEv2 uses fewer messages to create a tunnel between endpoints. The IKEv1 uses anywhere from three to six messages depending on the mode used (the aggressive mode or the main mode respectively), while the IKEv2 uses four. The IKEv2 does many other things better than IKEv1 including offering Asymmetric authentication and MOBIKE support.
The main advantage of using IKEv2 is stability. IKEv2 is a very effective VPN protocol for forming stable connections even when there are some interruptions. More specifically, whenever a user’s connection becomes weak and is about to drop, IKEv2 tries to go through the steps to restore the VPN connection. This way the user does not have to disconnect from the internet to finally connect again and resume work.

Another IKEv2 advantage is mobility. IKEv2 supports MOBIKE which is great at keeping VPN connections away from sudden drops. MOBIKE also comes in handy when the user wants to change networks from Cellular data to WiFi.
IKEv2 also keeps latency rates low because IKEv2 uses UDP port 500. Applications that require low latency can benefit from that.
The main disadvantage of using IKEv2 is that IKEv2 needs to use UDP port 500 to work at its best. An experienced network admin or a firewall can block that port and hence make IKEv2 ineffective.
Another disadvantage of using IKEv2 is that IKEv2 doesn’t work well with some devices and platforms. IKEv2 is great on operating systems such as IOS, macOS, and Windows. But users may run into problems on other platforms.
Note:
IKEv2 is also a closed source protocol which may be a problem for some users..8. Wireguard

WireGuard is a VPN protocol that focuses on security first. WireGuard uses the most advanced and tested cryptography algorithms and protocols to secure user data. WireGuard is also easy to use and set up.
Unlike some of the protocols mentioned on this list, Wireguard was originally native to the Linux platform. Now with help from various developers, WireGuard is easily implementable on platforms such as Android, iOS, BSD, macOS, and Windows.
WireGuard is different from other VPN protocols in the sense that WireGuard does not offer options related to hashing algorithms, key exchanges, and/or encryption. This has harmed the WireGuard adoption rate since sometimes it is deployed insecurely. WireGuard uses cryptographic primitives that the user cannot change and hence result in strong cryptographic option selection.
Although there are a lot of bugs that need to be fixed to make WireGuard adoption widespread, generally it is used with supercomputers along with embedded interfaces. WireGuard can work in many other situations (industrial and residential) as well.

The main advantage of using WireGuard is the performance that does not sacrifice speed. Compared to OpenVPN and IPSec, WireGuard is faster because WireGuard uses the latest cryptography algorithms which give WireGuard a speed boost. WireGuard can also include ChaCHa20, Curve25519,HKDF, SipHash24 and BLAKE2. Other modern optimizations make WireGuard one of the best VPN protocols for devices that don’t have access to a lot of power.
Note:
The number of lines of code that WireGuard needs to implement its security features is also less than other protocols which reduces the chance for errors and makes it easier for security researchers to audit.Another advantage is WireGuard’s cross-platform support. WireGuard also has low configuration requirements. For both encryption and identification, WireGuard uses public keys and hence doesn’t need a complex certification infrastructure. In terms of platforms, WireGuard works well with Windows, OpenBSD, FreeBSD, macOS, and Android.
9. SoftEther

SoftEther is an open-source VPN protocol. SoftEther VPN protocol works best when there is a need to secure communications from a client to a server. For VPN communications, the SoftEther protocol uses SSL 3.0.
SoftEther is fast, secure, and modern. All three of these features help SoftEther to encrypt communication tunnels between client and server so that no one can monitor the information passing through.
SoftEther offers several features which make it one of the best protocols. Some of those features include implementation of Virtual Network Adapter, deep inspection packet log function, RSA certificate authentication, UDP connections, TCP connections, IPv6 support, packet filtering, and support for AES 256-bit encryption.
SoftEther enables users to browse public WiFi networks safely and easily. SoftEther can also bypass geo-restrictions and firewalls.

The main advantage of using SoftEther is remote access to LAN via a module known as SoftEther Bridge. Users who go one step beyond just using the SoftEther protocol by also using the SOftEther server can get rid of Cisco routers and replace them with the SoftEther server application. Softether also supports NAT traversal function and dynamic DNS which means there is no need for a fixed IP or even a static IP address. SoftEther has full support for IPv6 and IPv4. Another advantage is access to high-level encryption implementations such as RSA 4096-bit and AES 256-bit. Traffic protected via SoftEther protocol can go through even the most robust of firewalls.
Pro Tip:
SoftEther is one of the fastest protocols around that enables low latency rates and above-average throughput. Finally, SoftEther is free, open-source, and regularly updated.The disadvantages of SoftEther are that since SoftEther is new, SoftEther does not have the kind of support other protocols have. SoftEther also has some compatibility issues with macOS and users have to install various other SoftEther apps in order to take full advantage of the SoftEther protocol.
What is the Fastest VPN Connection Type?

The fastest VPN connection type is SoftEther. IKEv2 is the fastest VPN connection for mobile devices.
SoftEther is faster than almost all VPN protocols because of its new VPN processing modules. Namely, the VPN processing modules are highly optimized. SoftEther is written in the C language and that also gives it the edge over other protocols. SoftEther is also one of the newest VPN protocols available and SoftEther takes full advantage of it by implementing rules that are tailor-made for high-speed throughput. Other protocols such as PPTP were not made with high-speed communication over the internet. Older protocols were more suited to packet transmission over narrow telephone lines.
The developers behind SoftEther made SoftEther with high performance in mind. SoftEther, when processing a given VPN packet, reduces the number of memory copies needed for each cycle.
SoftEther is faster than other protocols also because SoftEther can resolve Maximum Transmission Unit (MTU) problems most efficiently. Unlike older protocols where VPNs must transmit data packets into tunnels, SoftEther adopts a different approach called the streaming tunneling mechanism.

For mobile, the IKEv2 protocol is the fastest since IKEv2 doesn’t consume as many CPU resources. Of course, there are many other factors why IKEv2 is the fastest but the main reason why IKEv2 is the fastest especially on mobile devices is that it is very efficient at reconnecting a user whenever there is a weak VPN connection.
Users who want the fastest possible speed at the maximum level of protection should look towards OpenVPN UDP as it doesn’t decrease speed by much but continues to maintain a high level of anonymity and protection. The PPTP protocol may be the fastest in situations where security is not as important.
Which Type of VPN is Most Commonly Used Today?
The type of VPN that is most commonly used today is Remote Access VPN. The main advantage of using Remote Access VPN is the ease with which remote access VPN can connect users to a remote server of their choosing in any location they like. Remote Access VPNs allow users to browse cyberspace as they like with no geo-restrictions or hyper-targeted ads. Remote Access VPNs offer other benefits as well such as anonymity, privacy, and online data security.
Remote Access VPNs are preferred to other types of VPNs because Remote Access VPNs connect online users to the public internet via a private network safely and securely. Remote Access VPNs are also preferred because all that users need to do is to install (and subscribe to) a VPN client. The vast majority of online users make use of Remote Access VPN as it is the only VPN specifically designed for personal use.
What VPN Protocol Should You Use?

To answer the question of which VPN protocol you should use, the user needs to understand the given requirements of any situation. Some users may prefer speed over privacy or security while others may prefer security over everything else. Users looking to stream geo-restricted content should go for protocols that offer speed. If a user wants a stable connection that works on any device and under any situation, they should choose a protocol that has the maximum compatibility and an above-average level of security. Some users may be more concerned about who gets to see and monitor data passing through a given VPN tunnel, such users should go with open-source VPN protocols. Another factor in determining the protocol that any given user should use is flexibility and ease of setup. Not all protocols are click and go. Some require the completion of configuration steps while others are easier to install and use. Another factor is the reliability of the connection. When choosing a VPN protocol one should look at whether it focuses on connection stability (so that there is less chance of a VPN connection drop) or security (so that the data is super secure when the VPN is turned on and thus giving less importance to occasional connection loss).
Users should also consider which protocol is the most modern. New protocols are much better suited to high-speed internet connections than older ones which were meant for dial-up connections. The final factor is the device. Some protocols are better for mobile devices while others are better for desktop computers.
What are the Best VPNs?
In this section, the best VPNs will be presented for the general online user irrespective of the platform (for specific uses, the best iOS VPN will differ from the best Android VPN).

