When a virtual private network service provider wants to provide efficient troubleshooting or plan for capacity, they will record the events in the system—or in other words, save log files.
The zero-logs policy is an important aspect to consider when you’re looking for a VPN service.
It is simply a statement saying how a provider does “not” keep your logs.
But in most cases, it states the type of logs they are keeping, for how long and for what purpose.

Table of Contents
Why Do We Need a No-Logs Policy?
Any person or company with access to infrastructure handling your internet traffic can easily install a packet sniffer (or DPI) and inspect your traffic. But who can have access to the infrastructure handling your traffic?
According to this diagram from NordVPN’s website, when using a VPN, four agents are rejected from reading your traffic:
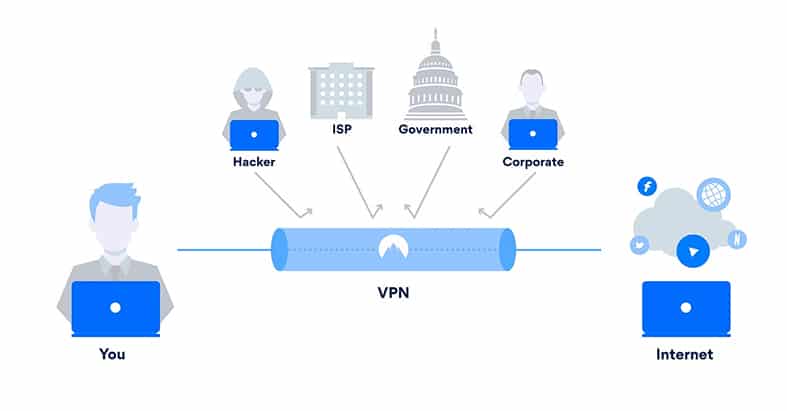
- Hackers? If you are sharing a WiFi Access Point (AP) to access the internet with anyone from coffee shop visitors to your neighbor, they can run a packet sniffer and read some of your traffic.
- ISP? If you feel comfortable and secure at home with the assurance that your internet is only for you, think again. Your internet service provider has access to every single packet in your traffic.
- Government? Governments, especially from the Five Eyes alliance countries, will undoubtedly ask your local ISP for traffic logs (or even redirect traffic through a proxy/firewall, as is the case for China) to monitor and censor “abnormal” traffic.
- Corporate? If you are connected to the internet inside a corporate or university network, your traffic is likely being monitored or limited by a proxy or firewall. Additionally, the admin could be curious enough to install a packet sniffer and read your unencrypted data.
A solution (as you might already know) would be to use a virtual private network. A VPN creates a kind of encrypted tunnel between the VPN client and the server and lets you exit the internet with a completely new identity. Two birds for one-shot: encrypted traffic (gibberish) and a new internet identity (the server’s IP addresses).
Note:
The VPN service provider is the last (and fifth) agent with access to logs of your internet traffic. Yes, the VPN provider has your identity (with data leak protection) fully covered from source to VPN server. However, the server knows your source IP address and has the key to unencrypt your traffic.In other words, the VPN server knows your secrets. How can you ensure it protects your secrets? That’s where the no-logs policy comes in.
What a No-Logs Policy Should Look Like
Before delving deep into NordVPN’s logs, let’s see what type of logs or data a VPN service could keep from you, and what could they do with that?
VPN service providers usually collect usage logs and connection logs. The usage logs contain sensitive information—pretty much everything that defeats the purpose of privacy. They contain your IP address, the amount of data transferred, web services and websites you visit, and other sensitive metadata.On the other hand, the VPN connection logs don’t contain sensitive information. VPN providers use connection logs for troubleshooting or forecasting. These logs may include the amount of data per connection, timestamps, the IP of the VPN server, etc.
But usage logs and connection logs are not the only things to consider. When getting a new VPN, consider the following:
- The country a VPN company operates: Look for VPN services based in countries with flexible data collection and retention laws. The VPN providers in countries that abide by the Five Eyes surveillance agreement have to keep logs to comply with the law. While they aren’t easily giving away your logs to government agencies to protect your privacy, the government has the upper-hand and can request audits or logs, especially when investigating criminal activity.
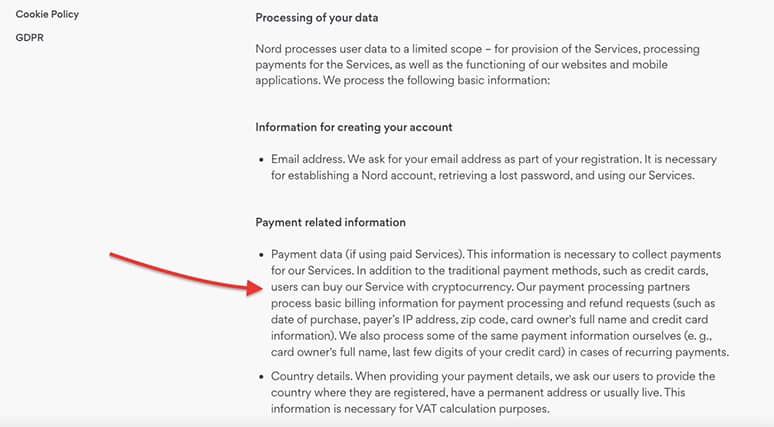
- The kind of personal data they ask for when you subscribe: An email and payment information should be enough to get your hands on a VPN subscription. Never include information like your address, full name or other personally identifiable information.
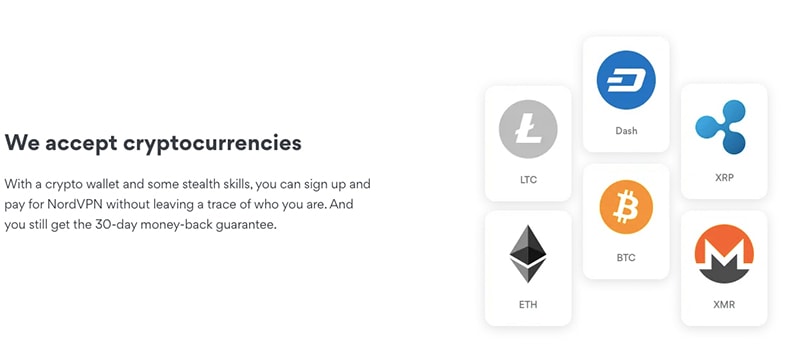
- What are the payment options available?: Your bank account or credit card is very personal. Some VPN providers give the option to pay with cryptocurrency, like Bitcoin, to also keep your payments fully anonymous.
- Is the VPN paid or free?: Paid VPN services keep data for troubleshooting or scaling purposes. A free VPN service would keep your logs to sell them for marketing or intelligence services. Additionally, free VPN services keep bandwidth logs to enforce bandwidth limits. A paid VPN could also keep bandwidth logs during a trial period before your 30-day money-back guarantee is up.
Although they could try, no VPN service provider is immune to data leaks. But what could go wrong? A disgruntled employee in a data center could take the customer’s data and sell it on the dark web, the data center could be running VPN software with unpatched servers and be the target of an attack, or the country’s government could also request logs to the VPN provider.
NordVPN Logs
NordVPN promises to protect your privacy through their “no-log VPN service” policy. But how does this policy work? And what type of logs does NordVPN keep?
NordVPN collects your email address for registration purposes. Obviously, for payment purposes, they collect payment data like credit and debit card numbers and country information. Fortunately, NordVPN supports payments over cryptocurrency to improve your payment anonymity.
You can sign up and pay for NordVPN via cryptocurrency, without leaving any trace of your identity. NordVPN accepts popular cryptocurrencies such as Bitcoin, Dash, Litecoin, XRP, Monero, Ethereum and Ripple. Even NordVPN encourages “stealth skills,” meaning, don’t just throw in your personal data, use your second name, maybe a new email address and other online privacy best-practices.
What Country Does NordVPN Operate In?
NordVPN is headquartered in the Republic of Panama, which is a country with no data retention laws, and far away from the prying eyes of Five Eyes surveillance member countries. That means, no government or third-party agency has the authority to knock on NordVPN’s office and request users’ logs.
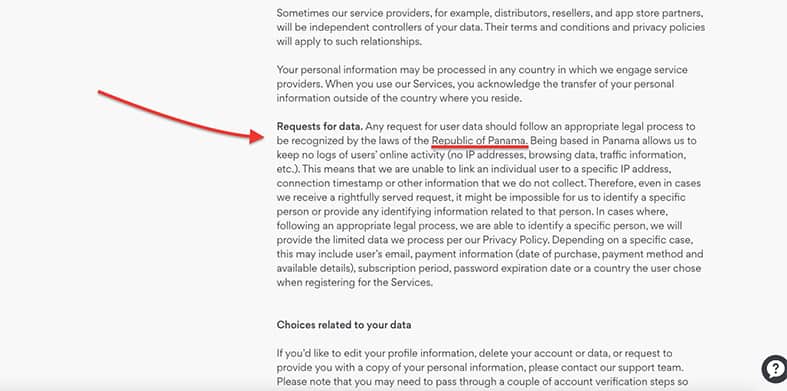
What About Usage and Connection Logs?
According to NordVPN’s privacy policy: “We do not store connection time stamps, used bandwidth, traffic logs, IP addresses, or browsing data.”
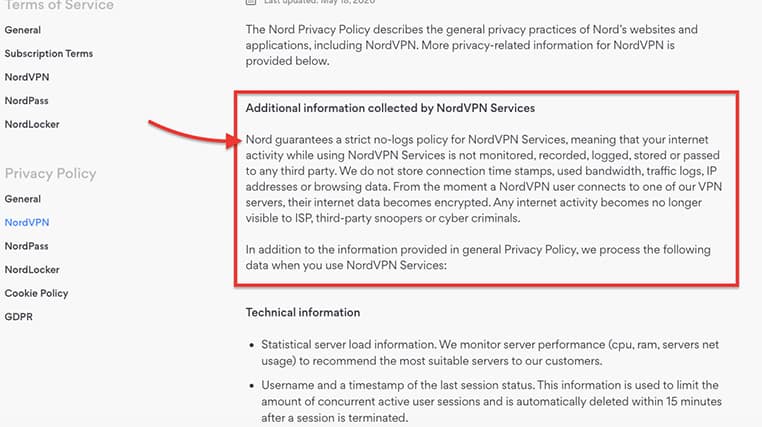
So, what logs do they keep? To monitor the server’s performance and find the most suitable one, NordVPN needs to keep track of certain parameters of the VPN server, including CPU, RAM and network usage. The username and timestamp (the time you connect to the server) are also collected to limit the total amount of concurrent users. NordVPN deletes this information 15 minutes after the session is over.
NordVPN also collects the following information from the client VPN software:
Anonymized app usage statistics include search, open push notifications, content viewed events, etc.
The NordVPN client detects the type of device you are using, including the operating system.
When using your mobile device, NordVPN does record the device’s ID.
No-Logs Policy Audit
NordVPN is one of the only VPN providers to have performed an independent audit on their no-logs policy for two consecutive years. To prove they’re trustworthy, NordVPN hired an independent auditor firm (PricewaterhouseCoopers AG) to perform an exhaustive audit of their logging policy.
Final Words
A no-logs or zero-logs policy is a statement disclosing the way a VPN company treats your logs.
This is important:
For 80% of the collected logs, there is nothing you can do aside from trust what the VPN provider is stating. For the remaining 20%, you can adjust your settings on the VPN client, compartmentalize (create access policies), never post private information, use HTTPS and stay away from illegal activities.When it comes to NordVPN, their no-logs policy is helping its existing and prospective customers to establish trust with the company: First, by putting everything they do with your logs in the policy, and second, by performing those regular private audits. These actions confirm the company’s commitment to keep no logs of users’ personal information.
Conclusion? NordVPN does not collect any personal information that could threaten your identity. The technical information collected from servers and clients is used for troubleshooting and capacity planning.

