Table of Contents
What Is Network Architecture?
Network architecture is the logical and structural layout of a network. In addition to hardware and physical connections, software, wireless networks and protocols, the medium of data transmission also constitutes the network architecture. Network architecture provides a detailed overview of the whole network, which is used to classify network layers. Organizations use network diagrams to create local area networks, wide-area networks and specific tunnels of communications.
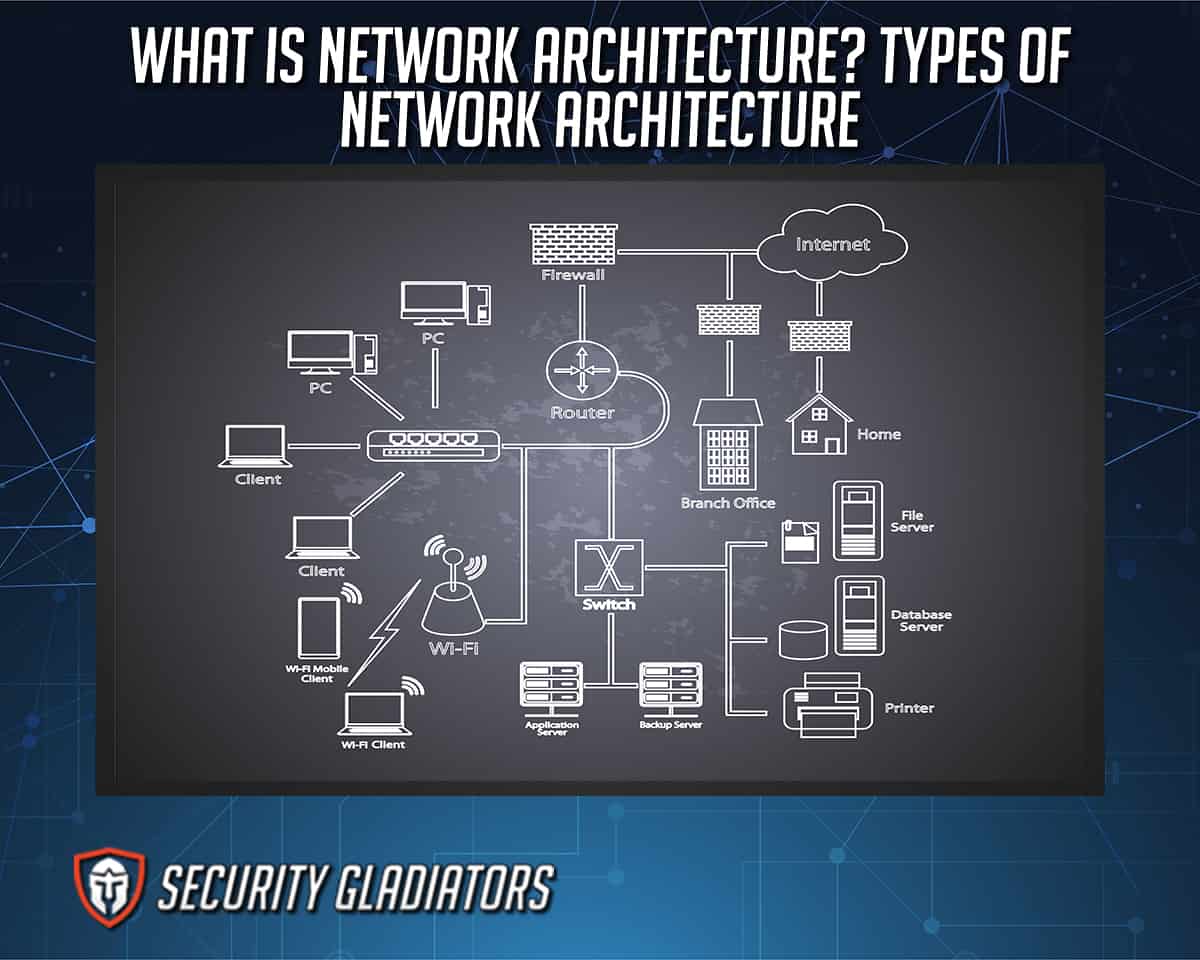
What Is Neural Network Architecture?
Neural network architecture is a type of network design that refers to a network made from individual units, known as neurons. Mimicking the neurons found in a human brain, the neurons can receive input, understand the importance of that input, and then combine multiple inputs into one output value. Activation functions make the output a non-linear combination of all input values.
Note:
A neural network has several rows of neurons, and several neurons in a single row constitute a layer, creating a multi-layer neural network. The first layer is called the input layer, followed by hidden layers and, finally, the last layer is the output layer. Hidden layers are intermediate layers that perform the computations, search for and extract features from the data, and pass on the information to the final output layer.What Is a Network Architecture Diagram?
A Network Architecture Diagram is the visual representation of the network. The layout of the elements that constitute a network is represented with various symbols and lines. Visual representation is the most intuitive way to process information and understand how network elements are connected. This is helpful when organizations are creating new systems or trying to understand where the problem in the network is. The network diagram is created using various software programs, such as SmartDraw, Creately, Intermapper or SolarWinds NTM.
What Is Zero Trust Network Architecture?
Zero Trust Network Architecture is a model of network where every connection to the system has to be verified. The architecture is implemented when the security of the network is ineffective. With numerous users accessing the data from various locations and devices, security breaches are frequent. Zero Trust Network Architecture aims to reduce unauthorized access to the data within the network. Multiple technologies are used to achieve the necessary security, including multi-factor authentication, encryption, IAM (identity and access management), and file system permissions.
What Is Core Network Architecture?
Core Network Architecture is a 5G network architecture that allows devices to be connected over non-3GPP access technologies. The access network can be any network that’s supported by the device, as long as the network offers IP connectivity. EPC (Evolved Packet Core) also exists for 4G, but 5G offers fewer options for supporting devices with non-3GPP access.
The concept of “trusted” and “untrusted” access is present in Core Network Architecture. An example of untrusted networks are private and public Wi-Fi networks, which usually require a password for an outside device to gain access. After the device has connected to the network and the access is granted, an IP address is assigned to the device within the network.
What Are the Components of Modern Network Architectures?
There are three main components of modern network architecture, as listed below.
- Controller-Led: Network controllers are the base of intent-based networking. Their function is to help secure the networks and allow the networks to collaborate.
- Multidomain: When an organization is big and has several networks, each network can communicate to the others through controllers. It consists of a master domain manager, lower domain managers and several agents in each domain. The communication is achieved by lower-placed agents communicating to their domain managers.
- Intent-Based Networking (IBN): This form of network administration uses artificial intelligence, machine learning and network orchestrations to sync and automate the administrative tasks by unifying access, simplifying onboarding new devices and acting as a security tool.
1. Controller-Led

In controller-led networks, controllers are software programs that run as centralized applications. The controller’s role is to centralize the control of all the devices in the network, though the degree and type of control can vary. A controller can edit the data or simply distribute the information without changing anything.
For the controller to communicate to the devices in the network, there must be an interface between the controller and the devices. The types of interfaces are given below.
- Southbound interface (SBI), which includes a protocol and an application programming interface (API).
- Northbound interface, which opens the controller and allows other users to access the data and functions of the device.
2. Multidomain
Multidomain networks have several layers of managers and agents. Every agent reports to the parent domain managers, and every manager reports to the respective higher domain manager. That way, large organizations can have several locations around a city or worldwide without having an uninterrupted multidomain network.
3. Intent-Based Networking (IBN)
Intent-based networking (IBN) uses advanced technological concepts such as artificial intelligence so that the network administrator can set an intent easily without having to code or place input manually. The intent produces the desired outcome.
IBN relies on artificial intelligence and machine learning to perform basic routine tasks, react to system changes and perform additional activities. Automating the tasks offers several benefits, some of which are listed below.
- Faster troubleshooting
- Improved security
- Optimal analytics
- Less manual tasks and consequently, fewer mistakes
- Easy implementation of new organization goals into the network
What Are the Types of Network Architecture?
The two types of network architecture are given below.
- Peer-to-peer architecture
- Client/server architecture

In the client/server network, clients and servers are differentiated. Meanwhile, in the peer-to-peer (P2P) model, the clients and the servers aren’t differentiated. In a network diagram of a peer-to-peer model, every node is both client and server. Peer-to-peer models are used to share various resources, such as power or disk storage.
A well-known example of P2P sharing is file sharing on the internet. Client/server networking is most often used for web services and game hosting. This type of network is also used for private networks inside organizations.
1. Peer-to-Peer Architecture
Peer-to-peer architecture is a type of network layout where each device has the same capabilities and responsibilities.
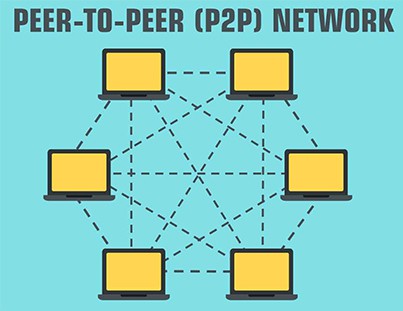
What Is Peer-to-Peer Architecture?
Peer-to-peer architecture focuses on connectivity, and each node has its own data. Every node has equal abilities, capable of requesting and responding to the services. The peer-to-peer architecture is best suited for networks that have less than 10 devices.
What Are the Advantages of Peer-to-Peer Architecture?
The advantages of peer-to-peer architecture are given below.
- Peer-to-peer architecture is less costly than the client/server network model.
- Sharing files is easy and fast, regardless of distance.
- The network is easy to set up, even without professional expertise.
- There’s no need for professionals as each peer has its own settings.
- The failure of one node won’t disrupt the rest of the network.
- Adding new people to the network is easy.
What Are the Disadvantages of Peer-to-Peer Architecture?
The disadvantages of peer-to-peer architecture are given below.
- Peer-to-peer architecture becomes less stable with the increase of peers in the network.
- This model is more susceptible to virus attacks.
- Files and resources are not centralized, which results in less organization.
- Backing up data is hard to achieve due to the lack of a central server.
What Are Examples of a Peer-to-Peer Network?
The examples of peer-to-peer networks and their applications are listed below.

- File sharing over the internet is the most common and best-known application of peer-to-peer networks. That’s how users can download games on online gaming platforms.
- Several Linux operating systems can be distributed through a peer-to-peer network. Ubuntu, Manjaro and Linux Mint can all be downloaded via BitTorrent using peer-to-peer file transfers.
- In Windows 7 and Windows 8 (version 1), you can create a network between a pair of computers, which is a peer-to-peer network that’s ideal for quick file sharing.
2. Client/Server Architecture
Client/server architecture is a type of network layout where some devices serve others and don’t share the same capabilities and responsibilities.
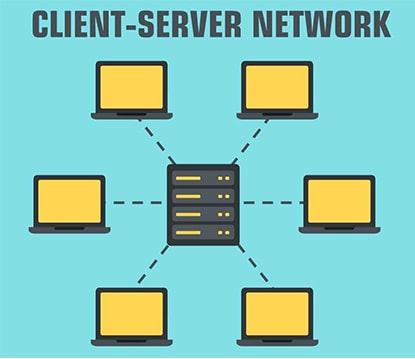
What Is Client/Server Architecture?
Client/server architecture is a model where service requesters are called clients, and service providers are called servers. They don’t have the same capabilities, as servers usually share the resources and clients don’t.
What Are the Advantages of Client/Server Architecture?
The advantages of client/server architecture are listed below.
- All data is centralized, which makes backup uncomplicated.
- Client/server architecture is stable and secure.
- The model can be used for both small and large networks.
- The peripheral devices can be controlled from the central device.
- Data in the server can be accessible from all peripheral devices.
- It’s easy to add both clients and servers without interruptions.
What Are the Disadvantages of Client/Server Architecture?
The disadvantages of client/server architecture are given below.
- Client/server architecture is more costly than peer-to-peer networks.
- For the network to run smoothly, a specialist network operating system is required.
- The disruption of part of the network can cause disruption in the whole network.
- Potential congestion could result in crashes if too many clients request the data from the same server.
What Are Examples of a Client/Server Network?
The examples of a client/server network are given below.
- Bank web servers contain the data about specific customers that users can access when requested.
- If you search for a term in a Google browser, you’re sending the request to the google web server. It responds with data that is then listed in the browser.
Which Network Architecture Is More Secure?
Client/server network architecture is more secure as all data is centralized. In a peer-to-peer network architecture, data is present in all different nodes, and viruses can affect parts of the network or the whole network if one node is infected. Client/server networks are also safer because access to the server is usually granted by the network administrator or after logging onto the network.
Why Does Network Security Require a Network Architecture?
A contemporary network security architecture may assist companies in reducing the attack surface, enhance threat detection and response, and limit cyber threats by protecting all network traffic.
What Is the OSI Model?
The OSI (Open Systems Interconnection) model is a framework whose main function is to describe the functions of a network. The OSI model describes computing functions with a universal set of rules.
What Is 5G Network Architecture?

The types of network architecture are explained in detail above, but what is 5G network architecture? 5G network architecture is the network configuration that includes both the physical construction of the 5G-specific hardware and infrastructure. Moreover, the engineering design that determines how the network transmits data is also included in the network system. The service-based architecture (SBA) has a core that’s aligned with a cloud. This allows the network to control complex network functions and their interconnectedness.

