Table of Contents
Pros
- Extremely fast scan times
- Manages to score top marks in various malware-blocking security tests
- Reasonably decent scores in various malware removal security tests
- Very tiny in terms of the size of the program and the installer
Cons
- Bonus features such as the anti-phishing protection feature aren’t as effective as the malware-blocking feature
- Some security features/tools may not be for the average user.
Bottom Line
If you are talking about tiny pieces of software application then they don’t come any smaller than Webroot SecureAnywhere Antivirus.
We don’t know of an antivirus product that is smaller in size than Webroot SecureAnywhere Antivirus.
But that tinyness doesn’t mean it doesn’t offer good security.
It does.
In fact, Webroot SecureAnywhere Antivirus has managed to score almost perfect scores in various kinds of malware-blocking security tests.
Webroot SecureAnywhere Antivirus also does a reasonable job of scanning systems infected with malware and then cleaning it up.
Along with Norton Antivirus, Webroot SecureAnywhere Antivirus is amongst the best antivirus security product that one can buy at the moment.
Webroot SecureAnywhere Antivirus Full Review
Nowadays you will not find many antivirus products, or companies behind them, that follow yearly updates or even version updates.
Most of them have dropped this age-old idea.
What do they do instead?
They slipstream all the new features.
They also keep themselves busy in continually honing the tools of their security products.
If we are talking about visible changes then Webroot SecureAnywhere Antivirus hasn’t had many in the last couple of years.
So why does it top so many best antivirus tool charts?
It is because, when we compare Webroot SecureAnywhere Antivirus with the rest of the competition, it still manages to match if not beat their performance scores.
And that is what matters right?
No one wants to have a beautiful looking antivirus product only to find out that it can’t block zero-day malware attacks.
Price
Just like some other elite antivirus products such as Kaspersky and Bitdefender, Webroot SecureAnywhere Antivirus only charges its users $40 per year (update: it is now $30 per year).
That is, a 12 month subscription period in which the user has to pay the company $40.
Pretty simple.
If the user wants to purchase three licenses with the same subscription then Webroot only charges $10 more.
However, Kaspersky and Bitdefender both charge $20 more for the same privilege.
As far as Norton Antivirus goes, it doesn’t any kind of multi-license subscription plan.
Instead, users have to feel content with just one license per subscription package.
Norton costs users $49.99.
There is also McAfee AntiVirus Plus.
It is one of the most, if not the most, expensive antivirus security product on the market.
Users who want to purchase a McAfee AntiVirus Plus subscription have to shell out $59.99 per year.
On the face of it, yes McAfee Antivirus Plus is very expensive.
But look a bit deeper and you will find that just one McAfee subscription gets users an unlimited number of licenses.
In other words, with just one McAfee subscription package, the user has the opportunity to protect all his/her devices.
With Webroot SecureAnywhere Antivirus, users can utilize their licenses in order to install the company’s antivirus protection on both Macs and PCs.
There is not much difference between the two in terms of security.
Although we would like to mention here again that the Mac version of Webroot SecureAnywhere Antivirus hasn’t changed that much since the past many months.
We’ll come up with a separate view of the Mac version of Webroot SecureAnywhere Antivirus at a later date.
Installation
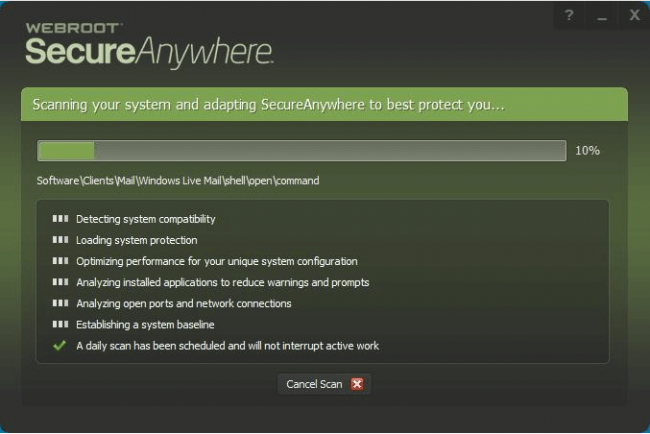
Since Webroot is so tiny both in its size and system presence, it barely takes any time to install.
We haven’t seen many antivirus products that have come close to the actual installation time of Webroot.
With that said, it is also true that the Webroot installer doesn’t just install an antivirus product.
It performs a complete list of other security-related tasks.
Moreover, it also shows the user that list and then checks each task off the list as soon as it finishes that task.
What are these tasks?
As mentioned just now there are many.
One of them is to for Webroot to analyze the currently installed user applications on the system in order to reduce the number of prompts and warnings.
The installer also establishes a security baseline for the system.
It also optimizes the product’s performance for the user’s system configuration which is, in most cases, unique.
The official Webroot installer also runs a complete antivirus system scan.
Now, even though the installer performs all these tasks, it still manages to finish off the installation process in a short amount of time.
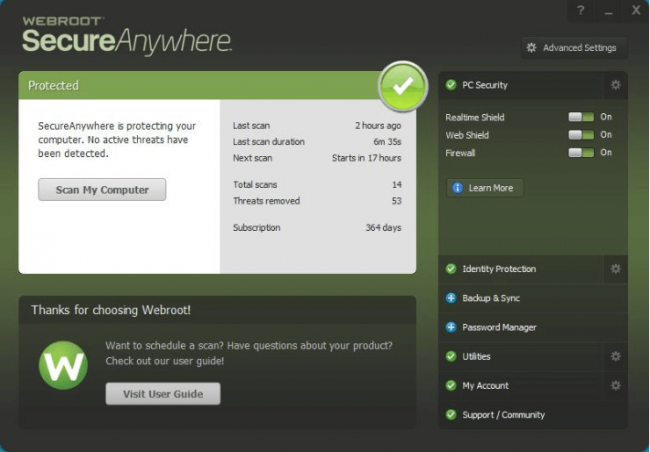
User Interface
The overall theme remains the same:
You have a lot of green and a bit of white.
The main window is predominantly green-toned.
However, now the main menu comes with a lighter panel as well.
This panel (with the light color) shows users some statistics about all the recent scans that the product has performed in order to clean the system off malware.
There is also a button in there.
Users can press the button in order to give orders to Webroot to immediately launch a full system scan.
Of course, there is no need for the user to ever use that button.
Why?
Because Webroot on its own performs a full system scan, on schedule, every single day.
And it starts scanning the user’s system for security related problems from the installation phase.
There is one other panel which is quite sizeable and appropriately offers the user a link.
Users can click on the link in order to view the full User Guide to the product at hand.
The panel which is located in the right-hand side of the screen enables users to easily access all the other features of Webroot SecureAnywhere Antivirus.
And as mentioned before, Webroot comes with a significant security feature collection.
What About Lab Results?
There is where Webroot loses some marks.
The problem with Webroot SecureAnywhere Antivirus is that, it has a decent detection system.
But that malware detection system is a lot different from what most other antivirus competitors offer.
Most antivirus products make use of a signature database.
Webroot doesn’t.
That alone makes it atypical.
Webroot mostly detects viruses and malware on a given user’s computer system with behavior patterns and other metadata.
This security product also comes with the feature where it calculates a rather straightforward number hash for all user files.
After that, it moves ahead and checks the numeric hash from the company’s online database.
It does that to know if the database already has identified the given file as a good or bad file.
When Webroot has finished with that test, it only concerns itself with the unknowns.
So if a user launches an unknown program and the system does that on its own, Webroot SecureAnywhere Antivirus moves in, monitors the program very closely and then notes its behavior.
Not only that, it also keeps a journal of all the actions that the unknown program takes.
Actions which Webroot identifies as irreversible are suppressed.
What are these actions?
Well, actions which are not reversible include, sending some quantity of data to any unknown remote server.
Moreover, Webroot SecureAnywhere Antivirus also transmits various details about the given unknown program and its behavior to the company’s servers for further analysis.
In a case where the server can’t automatically identify whether the program is good or not, it kicks in the analysis algorithm.
This algorithm then transfers the program into the hands of a human who is a malware expert.
The human expert then takes a deeper dive to really find out if the program is a security threat or not.
So what happens if Webroot analysis finds out that the file or the program is a malicious one?
As you would expect, it informs the local Webroot antivirus product.
The antivirus product then moves quickly to kill the unknown program and/or process.
After that, the app automatically rolls back all the actions that the unknown program took prior to its demise.
As mentioned at the top as well, in terms of size, there isn’t an antivirus product that even comes close to Webroot SecureAnywhere Antivirus.
We’re specifically talking about the local program here.
Why is that?
Because Webroot has transferred most of its antivirus intelligence straight to the cloud.
So what happens if the user is offline and then introduces a new unknown file to his/her computer system?
Well, in that case, it is possible for Webroot’s local heuristic system to score a detection.
And it may also identify the unknown program or the file as a type of malware.
If it can’t do that then Webroot SecureAnywhere Antivirus simply treats the program as a potentially bad program.
In other words, an unknown program.
It starts the whole process again where it keeps tabs on the behavior of the program.
Once the user has connected to the internet again and the system has regained internet access, the Webroot local application checks with the company’s cloud servers in order to make further decisions regarding the new unknown file app.
If the Webroot cloud system finds out that the new file or program is a known bad or good program then it moves to treat the unknown program like it deserves to be treated.
However, if Webroot cloud and Webroot local app can’t figure out the unknown program with certainty then it keeps on monitoring the program until one has managed to reach a verdict on the program’s fate.
As some could probably tell, such a style of detection method isn’t really a good fit when it comes to various standard antivirus security tests.
There are many standard antivirus security tests that make use of static samples.
And these, in particular, don’t suit Webroot’s style of malware detection.
Researchers who test different antivirus products launch malware samples just to check if it works.
But even during those early tests, they expect the antivirus product to detect malware samples as quickly as possible.
Most of the time, the antivirus product has to detect malware samples immediately and without any delay.
That method is completely at odds with the way Webroot SecureAnywhere Antivirus works.
Consequently, the company tends to stay away from any participation in such tests.
That means, Webroot doesn’t have much in the way of independent lab tests results.
Looking at the product’s history, we have come to know that Webroot SecureAnywhere Antivirus managed to pass some very difficult tests that MRG-Effitas carried out.
If you ask these questions to Webroot representatives they would tell you that the company will try to appear and participate in the coming tests from the same lab very soon.
What About Malware Protection?
As far as a general malware protection goes, Webroot manages to secure excellent scores.
The problem with no independent lab results is that there is no way to comprehensively test a given antivirus product.
No one has the resources to do that.
So, the next best option is to carry out various hands-on malware tests.
And these become very important in the overall score if an antivirus product doesn’t participate in independent lab tests.
So how does one get the ball to start rolling?
Well, as always, one has to download a sample malware collection from various resources on the internet.
Then, one should extract those files to a particular folder on the test system’s desktop.
It is also a good idea to include some lesser known and old legitimate files within the malware sample collection folder.
One must do that in order to make sure that the antivirus product has the sense to not delete everything if it detects that a certain folder contains some malware.
Some bad antivirus products do that.
If they detect one malware sample in a folder, they mark the folder as dangerous and move to delete everything within the folder.
Good antivirus products have the ability to differentiate on a file basis rather than folder basis.
Our research shows that when Webroot goes through such testing, it manages to detect and then eliminate around 50 percent of all malware samples.
Remember that this is the initial stage still.
At this stage, Webroot’s performance basically indicates that it managed to eliminate all samples whose basic numeric fingerprint or numeric hash had already been stored in the company’s cloud database.
After the first round, one has to initiate the next round with another set of malware samples.
This time, one has to modify some of the malware samples by hand.
What do we mean by “modification” here?
We mean that, in the second round of malware sample testing, the modified samples would have a different name from the first’s rounds malware samples.
They would also have an altered size.
One can easily to that by appending additional zeroes right at the end.
It is also a good idea to just reach out and modify some of the non-executable bytes in all second round malware samples.
So basically, now Webroot has to handle the same set of malware samples but with tweaked settings.
While carrying out such a test, one has to make sure to have enough information stored somewhere so that one can easily find which tweaked file corresponds to which original malware file that Webroot managed to whack out of the park at sight.
Our research shows that Webroot SecureAnywhere Antivirus missed around 25 percent of all malware samples in the second round.
Without going into too many details we would like to mention here that is completely normal.
Such hands-on malware tests are only there to check how flexible a given antivirus product’s signature-based malware detection system really is.
Other elite antivirus products such as Trend Micro sometimes manage to miss a good 45 percent of all modified malware samples/files.
Kaspersky, which is the best of the best, can miss up to 45 percent as well.
With Webroot though, we did notice some rather weird.
Comparing the modified malware sample files which corresponded to the earlier malware samples that Webroot did not successfully eliminate at first sight, our research showed that it managed to wipe out almost 50 percent of the modified version.
How did it do that?
If you put forward this question to a Webroot representative, the representative would tell you that the manually modified malware sample file managed to NOT appear in the company’s database.
And since Webroot had never seen these files before, it found that these samples were absent from the database.
Moreover, Webroot SecureAnywhere Antivirus considered the absence of such malware samples as suspicious.
Such circumstances suggested to the antivirus product the possibility of a malware that was polymorphic.
According to Webroot, such a possibility could have triggered the antivirus product’s additional level of malware scrutiny.
The next sensible step is to individually launch all the surviving malware samples.
Our research shows that as soon as Webroot detected a malware sample, it wanted the user to allow it to run a system scan.
And perhaps that is totally understandable as far as real-world malware detection scenario is concerned.
In order to save some time, it is a good idea to stop Webroot from doing that until and unless it has gone through all the remaining malware samples.
Our research shows that Webroot caught all remaining malware samples either at launch or within a very short amount of time.
We have also come to know from similar research that Webroot has the ability to differentiate between a folder that has some malware samples and a folder that only has malware samples.
In other words, it can detect if a malware-ridden folder contains legitimate and harmless files.
Time For A Full Scan
This one is very important.
Our research shows that after the initial malware sample testing if users do allow Webroot to run a full system scan then it can take up to 15 minutes.
After 15 minutes have passed it will report the system as clean.
As it turns out, Webroot takes the safe route and runs an additional intensive system scan in order to make sure that no malware is left on the system.
Webroot managed to finish the second system scan in about eight minutes.
The next method to text an antivirus product without relying on independent lab tests is to make use some hand-coded analysis tool which can help to verify that Webroot indeed wiped the whole system without leaving any traces of malware.
Our research shows that in this test Webroot managed to detect a whopping 100 percent of malware samples.
That means 10 out of 10 for Webroot when it comes to malware cleanup.
By the way, another one of our favorite Symantec Norton AntiVirus Basic also managed to score a 100 percent detection rate.
In order to compare the scan speed of an antivirus product with the competitors, one has to run a full system an on a system that is completely clean.
Our research shows that Webroot can finish such a scan on a clean system in order eight minutes.
Even though it may look short, we would like to point out here that Webroot has managed to complete system scans in even less time before.
However, if we are talking about the industry average, Webroot is way ahead of everyone else.
We don’t know of a single current antivirus product that can match Webroot’s speed of system scan.
And yes, we are aware that Malwarebytes 3.0 Premium has the ability to finish a complete system scan inside 3 minutes.
But the problem is Malwarebytes’ system scan isn’t really a full system scan.
It is a quick scan actually.
The industry average, as far as genuine full system scans go, is around 45 minutes.
Antivirus testers usually find it hard to gather, then select and then analyze newer malware sample collection to use with their tests.
Such malware samples do have use at least till the tester wants to through another malware testing process.
So no one should find it surprising that Webroot performed better after some time had passed because its databases already had the numeric hashes of the malware samples used the first time around.
On the other hand, the malicious URL blocking security test is a different test.
It is different in the sense that it usually makes use of nothing but the latest malware files.
One can access these files from MRG-Effitas that provides testers with a reliable and regular feed.
Generally speaking, the malware samples in these collections are never older than 24 hours.
This is great.
The way to test an antivirus product for malicious URL blocking is to first access the list of malicious URLs.
Then launch each malicious URL.
After that, discard the malicious URL that gives a random error notification or simply does not launch at all.
If a malware URL does not actually point towards a malware file that is executable then too that malicious URL must be discarded.
The tester should only look at those malicious URLs that work.
Then, the tester has to note down whether the given antivirus product blocks user’s browser access to the given malicious URL page.
If the page is dangerous, the antivirus product must block it.
A good antivirus product would eliminate the malware-ridden download while the user is downloading it.
Some antivirus products eliminate the download after the user has finished downloading the malware-ridden file.
A few antivirus products do nothing.
The tester has to note down what the antivirus product under testing does with each malicious URL.
Once the tester has managed to gather valid results for 100 malicious URLs, then it is time to move forward.
Our research shows that users should expect the Webroot online web protection tool to kick in and start working 16 percent of the times.
In other words, it will keep the browser and the user away from visiting those malicious and dangerous URLs only 16 percent of the times.
When it does block access it states that the user could expose himself/herself to danger if he/she visits the given page.
Webroot’s real-time antivirus component managed to eliminate around 72 percent of these malicious URLs.
That took Webroot’s total score to around 88 percent prevention.
The last version of Webroot managed to block around 84 percent.
So Webroot has improved.
Of course, there are lots of other antivirus products that have managed to score higher scores.
There is the Norton AntiVirus that always manages to top the list of malicious URL blocking percentages with 98 percent.
Another good antivirus product for malicious URL blocking is Trend Micro AntiVirus Plus Security which can climb to as high as 97 percent protection.
What About Ransomware?
We have already mentioned Webroot’s system of keeping a journal with regards to an unknown program and then launching the rollback feature to reverse its actions on the user’s system.
What we want to say now is that these same features can also double up as ransomware protection features.
How?
By simply rolling back the effects that are associated with an encryption ransomware.
With that said, Webroot gives out a warning to users that its ransomware protection comes with certain limitations.
Thes limitations involved drive space.
In other words, the available drive space could impact Webroot’s ability to roll back encrypting software’s actions.
Honestly speaking, the majority of all ransomware attacks would have a hard time to try and get past all of Webroots other protection layers.
If it does, then it would indeed be a very special ransomware attack.
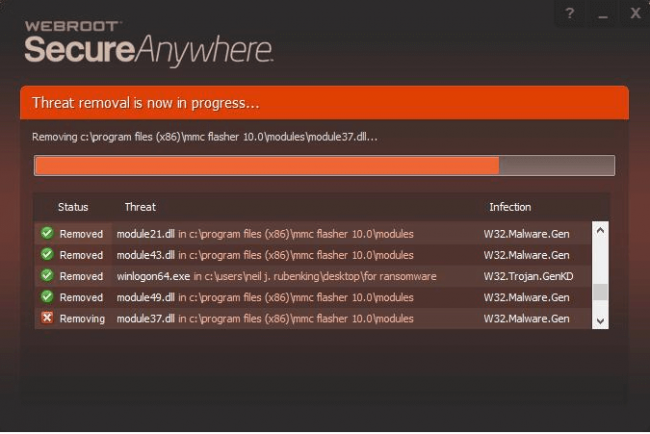
Our research shows that Webroot can completely wipe out each and every ransomware sample.
It can recognize malware samples via the same method it recognizes unknown bad programs and applications.
Webroot can also detect a few ransomware samples with the help of the ransomware’s bad behavior after it has launched itself.
But the real question is this:
How does one test Webroot’s ransomware protection feature?
Well, theoretically speaking, it should not present any problems.
All that a tester has to do is to write a completely new encrypting software for carrying out a ransomware attack.
Then test the new ransomware specimen with the antivirus product under evaluation.
Well, as it turns out, practically speaking it isn’t that simple.
One would need to have astronomical programming skills to program such a ransomware.
Even then, it would be very hard because the programmer simply would not know how to write such kind of a ransomware software.
But there is another way.
That way is to simply use a ransomware simulator.
Whenever a ransomware simulator is activated, it gets to work by first going to the user’s Documents folder and then finding all the present text files.
After that, the ransomware simulator moves to encrypt all text files with the help of XOR encryption (which is reversible).
This is the type of program that testers usually make use of in order to test antivirus products such as Webroot SecureAnywhere AntiVirus.
All that one has to do is recompile such a given encrypting software and then change it a bit so as to protect against Webroot recognizing it via its database.
Remember, a sudden and real ransomware attack would not be present in Webroot’s database.
Hence, one has to test Webroot with a ransomware simulator that Webroot’s database has no idea about.
After one has got his/her hands on such simulator, the only thing left to do is to launch the ransomware program.
And just sit back to let it do its thing.
After that, it is just a matter of verifying if the ransomware simulator managed to encrypt all of the user’s Documents folder text files.
Our research shows that when Webroot is put through such a process, it works pretty well.
More specifically, Webroot has an Active Processes list.
One can verify if it has caught the simulator by looking at the risk.
Furthermore, our research shows, Webroot can mark the fake ransomware simulator or encryptor as a Monitored program.
That means Webroot monitored the program and then create a record file of the program’s actions.
The user is free to just mark the monitored program as Blocked.
Moreover, the user is also free to confirm that he/she wants to eliminate the encryptor program immediately without delay.
After that it is just a matter of running a system scan in order to verify results.
Our research shows that Webroot, after the scan, does not run into any problems in correctly returning all the user’s Documents folder text files in their original plaintext format (back from their encrypted status).
This is really nice.
We have also come to know that Webroot SecureAnywhere’s monitoring feature does have the ability to work with all types of malware samples.
Trend Micro comes with a similar security feature that only focuses on problems related to ransomware attacks.
Moreover, Trend Micro’s security feature starts to kick in as soon as it sights a specific kind of ransomware behavior.
Trend Micro backs up all the user’s important files before the malware has a chance to do something nasty to them.
If Trend Micro’s behavioral detection system is able to verify that the unknown program is actually a ransomware attack then it moves to terminate the ransomware attack before the encryptor has an opportunity to cause any kind of damage.
After it has wiped out the ransomware, it moves to restore all of the user files that it backed up earlier.
What About Phishing Protection?
In one line, Webroot SecureAnywhere has good phishing protection.
What are phishing sites anyway?
These are special websites which basically masquerade as popular and trustworthy websites while they are frauds.
Why would anyone do this?
Well, hackers want to fool people into giving up their sensitive credentials.
Phishing websites can look like anything.
Think your favorite,
- Streaming sites
- Banks sites
- PayPal
- Gaming sites
There is not a site in the world that is safe from phishing sites impersonating it.
Once the user has fallen into the trap of providing these sites with their username and/or password, his/her account is for all intents and purposes pwned.
As some of you might expect, these phishing sites aren’t built to last.
They come and go very quickly.
Entities on the internet keep a lookout on them and as soon as their systems have detected a phishing website, they blacklist them.
Since we are living in the real world, there is a small time period between the phishing site’s appearance and the phishing site’s demise.
Hackers behind these phishing sites want to victimize as many visitors to their site as possible.
After that, the perpetrators vanish.
Needless to say, the best of the best anti-phishing tools do more than just rely on these blacklists.
The best anti-phishing tools perform detailed real-time analysis of any given URL in order to detect the latest frauds.
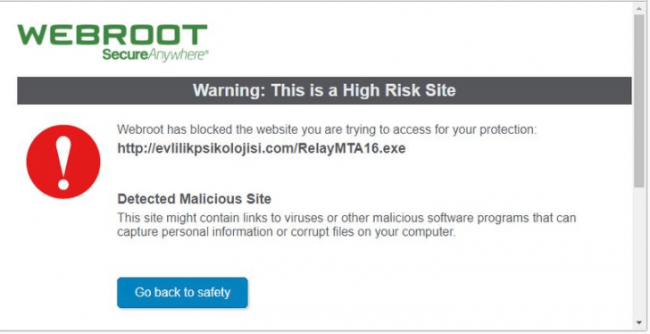
Fortunately, Webroot is an antivirus product that makes use of that real-time analysis technique in order to keep phishing attempts at bay.
Users will come across situations many times that their web browser would start to load a given webpage but then Webroot would interrupt the loading process and show the user a warning message.
The warning message would say something along the lines of Phishing Attack Detected.
Webroot has a blacklist of its own.
Whenever it detects a fraud website, it blocks it and then places the website on its own blacklist.
It also makes use of this blacklist in order to protect other Webroot users who might come across the same phishing site at some other point in time.
That does it for the mechanisms of anti-phishing tools.
But how do you test for it?
Well, a tester has to gather some more URLs that different resources have reported as phishing and/or fraudulent.
While doing that, the tester has to make sure to only include those phishing URLs that have not made it to various blacklists.
A tester also has to make sure that the selected URLs are no more than three hours old.
When all the URLs are in place, the tester has to visit all the URLs turn by turn in a total of five web browsers simultaneously.
Here is the setting.
One web browser has to have the protection of the antivirus product under evaluation.
Another web browser has to have the protection of Norton.
A total of three web browsers should have no protection other than the built-in Internet Explorer, Firefox and Chrome anti-phishing tools.
Our research shows that over 50 percent of all security products score lower than one of these mainstream browsers when it comes to anti-phishing protection.
Moreover, over 20 percent of all security products can’t match any of the three above-mentioned mainstream web browsers.
We haven’t come across many security products that have the ability to beat Norton’s phishing detection rate.
The last time around we researched Webroot, it managed to edge out the phishing detection rate of Norton by a whisker.
In other words, Webroot SecureAnywhere beat Norton by a single percentage point.
What about this time?
Well, Norton came out on top of Webroot by a total of five percentage points.
Even with that defeat, Webroot’s score is at least respectable.
Our research shows that if we limit our review to just recent security products that only Trend Micro and Bitdefender antivirus + have managed to outscore Norton on antiphishing tests.
Bonus Features: Firewall
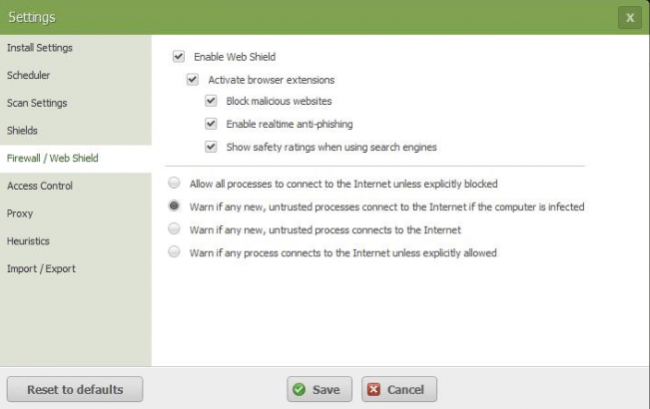
As alluded to at the beginning of this review as well, Webroot SecureAnywhere also comes with a firewall protection feature.
The company offers that even in its standalone antivirus product.
Again, there is a catch.
Webroot’s firewall protection feature doesn’t work the same way as other firewall products do.
In other words, Webroot’s firewall shows no interest in making attempts to make the user’s system ports go into stealth mode.
Webroot firewall understands that these are tasks that are best left to Windows Firewall (the Windows 10 built-in feature).
Of course, users would do well if they double check that they have enabled their Windows Firewall feature.
Webroot Firewall also takes no pains in attempting to fend off exploits which are network-based.
One way to test a firewall feature is to hit the system under testing with around 30 different exploits.
Testers usually use the CORE Impact penetration online tool.
So how did Webroot firewall perform against CORE Impact generated exploits?
Well, it did close to nothing.
Of course, testers usually make sure they test for exploits on a fully patched system.
This way the security exploits can’t do any amount of damage to the test system if the firewall feature under evaluation fails.
Webroot firewall has a simple classification system.
It divides programs into,
- Unknown
- Bad
- Good
Just like in the case of Norton, Webroot Firewall also tends to leave all the good programs alone.
It jumps on the bad programs and eliminates them.
For the unknowns, it keeps the tabs on them.
We have already described the fact that if Webroot identifies an unknown program, it monitors it.
If and when the unknown program attempts to exfiltrate the user’s sensitive/private data, Webroot kicks in to block it and erase its existence.
In the end, the bad unknown program does not find any success in harming the user’s system.
At the point when Webroot Firewall detects that the user’s system has an active infection, it really starts to kick hard.
This results in the app’s main window to change its color from the peaceful green to an intense red.
It is exactly at such point that it starts to clamp down on all network traffic that is generated by unknown applications and programs.
While doing that, it does keep the user from continuing with his/her everyday online activities such as web surfing.
But some users are born glutton for punishment.
Webroot takes care of them.
How?
By providing them with options to tweak Webroot Firewall settings.
Using these advanced options, techie users can force an old-school firewall behavior on Webroot.
In such a mode, the Webroot firewall would pop up a visible warning notification each and every time it detects that an untrusted program has tried to access the internet from the user’s network.
Users who want more stress have the option of going further.
Webroot firewall has an option where it effectively blocks internet access for all applications and programs that it deems untrusted.
If much of above did not make much sense to you then know that there is no way a malware coder would have the skills to disable Webroot firewall protection.
Why are we so sure about that?
Well, because Webroot Firewall manages to NOT expose any kind of settings in the system’s Registry.
Webroot Firewall has to processes and both processes have appropriate protection which renders them invulnerable to termination.
Moreover, even if the user tried, Webroot would not allow the user to disable or stop any of the operating system’s (Windows) services.
More Advanced Features
Webroot SecureAnywhere offers many other tools.
Let’s discuss some of the lesser-known and lesser-used ones.
Of course, we are assuming here that you actually have an interest in poking around to see what is there in the deep pits of hell.
You always have the option of turning around and not look.
If you do, Webroot would continue to protect you.
So no problem in stepping way.
We don’t recommend normal users to use, configure or even use some of the expert features that Webroot offers to its users.
The first of these features is the Identity Protection feature.
As the name of the feature suggests, this feature comes in when there is a need to prevent all the different varieties of normal malware attacks.
This includes some typical ones such as,
- Keylogging
- Web browser process alteration
- Man-in-the-middle attacks
The Identity Protection feature can also apply its abilities to protect specific programs and applications that the user has to choose himself/herself.
By default, Identity Protection protects applications such as Internet Explorer.
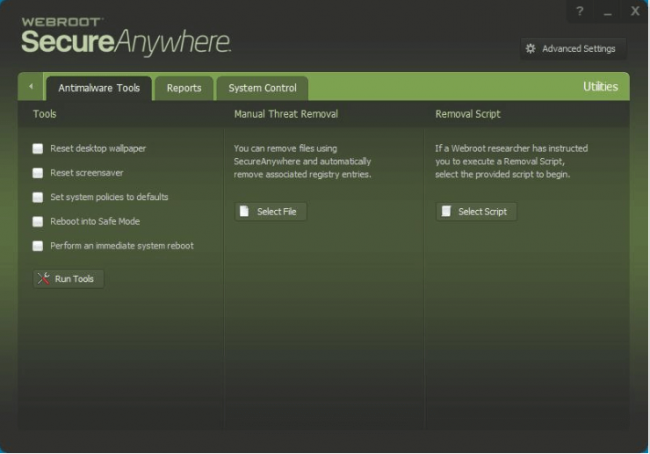
For users who might have ended up in a situation where they want to repair some collateral damage, Webroot SecureAnywhere has a unique set of useful antimalware tools.
These tools can act against malware-modified,
- System policies
- Screensaver
- Wallpaper
Users also have the option of using such tools to quickly reboot their systems directly into Safe Mode.
Moreover, these tools also allow users to perform a kind of instant system reboot.
Users with more tech kills have the option of removing malware problems manually.
In fact, they can also do a bit of work on the associated Registry data.
Webroot technical support team has also created a malware removal script for users who want to go that route either by choice or necessity.
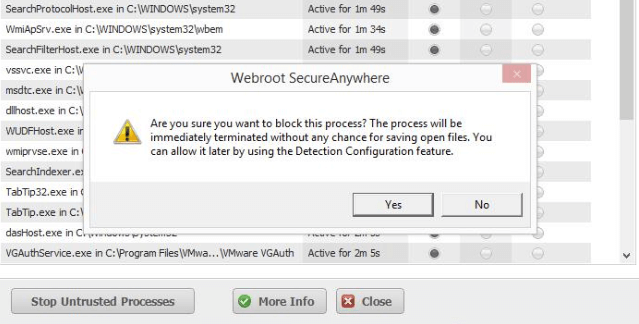
Webroot tools allow users to even view each and every active process that the antivirus product is monitoring at any given time from a list of all active processes.
Users who have an interest in seeing what their antivirus product, Webroot SecureAnywhere, is doing at any given moment can open up the official Reports page.
On this page, they can check Webroot’s current activity.
They can also have a look at the history of all that Webroot has done for them.
Our experience tells us that the majority of Webroot consumers would not have this desire to read or even take a look at all the available threat logs and scan logs.
With that said, there is always a chance that the Webroot tech support may want to have a look at them in order to help out.
Before we forget, Webroot also comes with a tech support which is available for users 24/7.
The company has many call centers based in Australia, Ireland and the United States of America.
Now, we have mentioned some of the expert features.
You know what we haven’t mentioned?
Features which are not expert features but beyond what we call expert features.
One such beyond-expert security feature is SafeStart Sandbox.
This feature is only for those users who have actual antivirus research training.
Such users or more specifically researchers can make use of such features in order to launch any given program that may come across suspect but only under a lot of limitations.
The researcher will have to dig into a lot of details and then specify all these limitations for the suspect program.
Chances are that you are not an antivirus researcher.
In that case, for the sake of your sanity, just stay away.
Is Webroot SecureAnywhere Really The Lightest Antivirus Product In The World?
Many antivirus testers and reviewers have consistently referred to Webroot SecureAnywhere AntiVirus as the lightest and the smallest antivirus security product in the world.
Is it?
And what does it even mean?
Generally speaking, in order to see how big an antivirus program really is, one has to open its installation folder.
This folder usually contains all the files and folders that the security suite or antivirus needs in order to run well.
Remember, this is the place where each and every file and folder that your antivirus product needs is present.
So don’t mess around in here.
In any case, our research shows that if you go to this installation folder for Norton, you will find that the program folder would have close to 140 files and 1260 folders.
It would occupy probably around 700 MB of your hard drive disk space.
Do the same for Bitdefender and you will come to know that its folders and files also reach high numbers but far higher than Norton’s.
Bitdefender has about 201 folders and 4400 files.
However, Bitdefender does not take as much disk space as Norton.
The other thing readers need to understand here is that, Bitdefender and Norton aren’t exactly the biggest in terms of their file size when compared with what is on offer on the market.
So what happens when you check Webroot’s installation folder?
Well, with Webroot users will find a total of ONE file.
This file would have the name: WRSA.exe.
It will weigh somewhere in the region of 1MB.
Is that tiny or what?
If the user takes a deeper look into the Task Manager, he/she would soon find that Webroot SecureAnywhere has a total of two processes.
One of those processes usually runs at the user’s system level.
The other one takes up some of the user machine’s memory space and runs on that.
Norton also has a similar arrangement.
For McAfee, our research shows it has a total of 16 processes which are active ones.
Check for Bitdefender and the user will find that it too has a total of 9 such active processes.
But the thing readers need to understand here is that there are two kinds of processes.
One kind of processes appear in the Task Manager.
The other kind do not.
Not plainly in any case.
What we mean is, many security products and utilities tend to rely on one (and sometimes more) Windows Services.
So you have to count these as well because without them the antivirus product would simply not work.
Checking for such services, our research shows that Norton along with Webroot relies on just one Windows Service.
Kaspersky Anti-Virus relies on three.
On the extreme end, McAfee relied on a total of 13 Windows Services.
In the case of McAfee, all of the services that it relied on were actually running services.
What about Bitdefender?
Well, it had six Windows Services to rely on.
We don’t want to give the reader the wrong impression.
Even if a security product makes use of a large number of Windows services or processes in general, it doesn’t have to mean that the security product is consuming more of the user’s machine resources.
In fact, it is entirely possible that an application may just do with one process but that process is a very resource-hungry one.
In any case, it would bring the user’s system to a rather screeching halt.
Now, remember, that we said that it is entirely possible.
We didn’t say it is probable.
What we mean to say is that no matter how you look at it, there is no denying the fact that Webroot SecureAnywhere is indeed a light antivirus product.
In fact, it is the lightest.
Webroot SecureAnywhere Conclusion
The conclusion is simple enough.
Webroot is a good antivirus product.
But independent antivirus testing labs have little idea about how they should go about testing Webroot as an antivirus product.
In other words, Webroot doesn’t quite jibe with the ways and methods of these independent testing labs.
With that said, Webroot performed really well in various other malware tests.
It proved itself as a huge success when it came to malware protection with near perfect scores.
Webroot SecureAnywhere also managed to score high marks in blocking various types of malicious URLs.
It provided decent protection against phishing sites as well.
Of course, it is hard to test any antivirus product against zero-day ransomware attacks.
And that is the case with Webroot SecureAnywhere as well.
Webroot does have its trusty journal and rollback security system which, according to our research, proved itself very effective against different types of ransomware simulations.
Perhaps Webroot SecureAnywhere is the only anti-virus company that offers so many advanced features not just for average users but also advanced users.
And its packages all of that in a tiny file.
That is the reason why Webroot will continue to be ranked amongst the best antivirus products in the market today.
We should remind users here that Webroot SecureAnywhere isn’t the only player in town.
There is Symantec Norton Antivirus Basic which has consistently aced many types of malware protection hurdles.
Norton is so good that it not only beats all other Antivirus products but also full system security suites.
Especially when it comes to security exploit tests.
Bitdefender Antivirus Plus along with Kaspersky Anti-Virus has made it a habit of scoring perfect scores on all independent lab tests.
Even in the ones they don’t score perfect, they score near-perfect marks.
Both Kaspersky and Bitdefender come with a lot of bonus features as well.
And they aren’t there just for the show.
They are actually useful.
McAfee Antivirus Plus also deserves a mention here.
Even though it is expensive for a single user and even though its scores aren’t as high as Bitdefender’s or Kaspersky’s, it is still an excellent bargain for family protection.
It offers protection for all user devices no matter what their operating system.
McAfee has protection for everything including,
- iOS
- Android
- macOS
- Windows
Each of the four antivirus products that we have mentioned above has its own strengths and weaknesses.
Regardless, all of them are worth a try.