Organizations may have social media accounts or some online presence, but without a website, it is as if they don’t exist. Websites are the face of a company. With this vital role, website security should be of paramount importance. Having an insecure website is far worse than having no site at all.
Attacks like DoS, DDoS, SQL injections and Cross-Site Scripting can bring your site down in just a few seconds. Not only would your data and reputation get compromised, but you’ll also expose your customers’ valuable information.
This guide will cover the ins and outs of website security. You’ll know why hackers would pick your site, the process, and tools they will use to exploit it, and, most importantly, what you can do when it happens.
 What Is Website Security?
What Is Website Security?
Website security is the set of processes or tools used to protect a website from exploitation and ensure its data is not compromised. Website security is an ongoing process and should never be thought of as a set-it-and-forget-it action.
Website security is a critical element in website management.
As you may know, a website is formed by various elements, including the web-server, database, storage, domains, etc. So, website security should deal with protecting the assets within those elements.
Websites are not typically hosted on home-based servers, which means security would start from your home physical security. Instead, websites are generally served via website hosting providers. These providers will ensure the data center where your website and data are hosted is physically secure and that the server is also behind a firewall or boundary protection device.
So, securing your site becomes a shared responsibility between you and your provider. The provider will secure different levels, but you’ll also need to secure your share through updates, security patches, configurations, customizations and other measures.
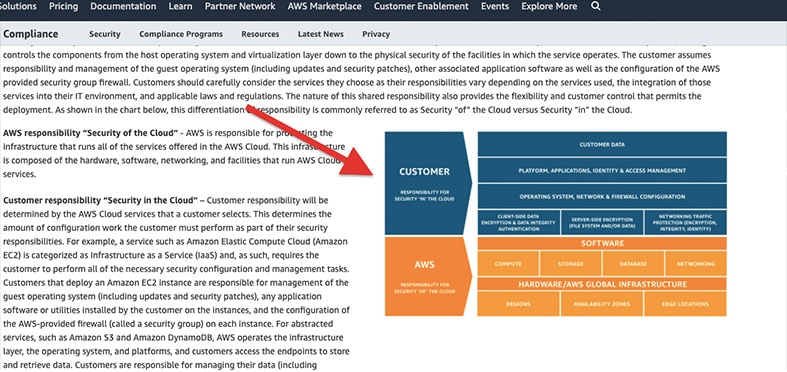
Amazon’s AWS implements a similar kind of shared responsibility model.
Web hosting providers will usually not mention it, but the shared responsibility should be similar to AWS’s model: The customer is responsible for security IN the cloud, while AWS handles the security OF the cloud.
Why Is Web Security Important?
The website owner, managers and developers would take the following road: Make sure the site loads fast, provides a good experience, attracts traffic and pushes visitors in the right direction. With a “nevermind” attitude, they might think that the odds of their site getting hacked are slim to none.
Websites get hacked, and when they do, it can be very expensive for the website owners—not only in terms of data but also in reputation.
Remember: Having an insecure website is far worse than having no site at all. A hacked website compromises your business’s data, as well as the sensitive information belonging to all your subscribers, visitors or customers.
A simple SQL injection attack may compromise a “secured” database with your customer’s credit card information. Imagine all those lawsuits, ridiculous fines and the reputational hit your business will take?
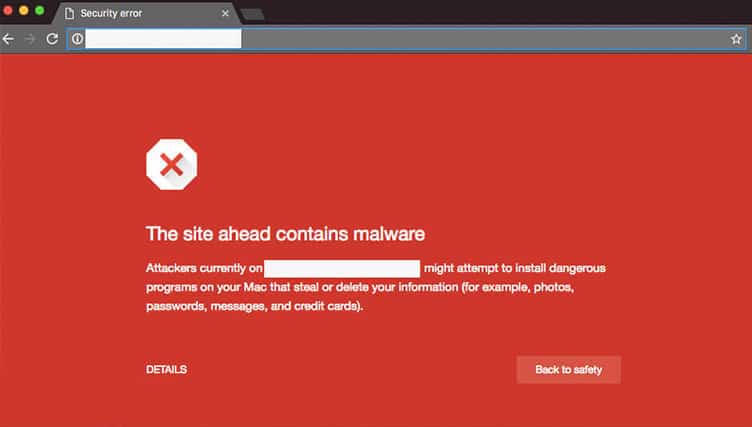
But that’s not all: A site with malware or vulnerabilities can get blacklisted. A blacklisted site could lose up to 99% of its traffic in just a few minutes.
Search engines like Google may even remove sites with malware from its search index. That means anyone looking for you on Google would end up being pushed to your competition in the research results.
Below is a screenshot of how a blacklisted website would look to site visitors:
Website security is also important because hackers could deface your website. Your website will keep your domain but show another homepage.
A defaced website may show what a hacker wants your customers or visitors to see. This can deal a huge blow to your company’s reputation.
Why Do Websites Get Hacked?
Hackers don’t have a win-it-all recipe for exploiting your website security. They’re only looking for vulnerabilities.
Note:
So, any outdated software, weak or default passwords, open ports or misconfigurations will be an entry point to control your website.Hackers exploit websites for several reasons. They are trying to make money by stealing credit card information stored in the website’s databases or exploiting the server’s resources for the purposes of cryptomining or botnet attacks (a DDoS). Hackers may also be after a visitor’s contact information to sell it to unethical third-party marketing agencies for malvertising or spam.
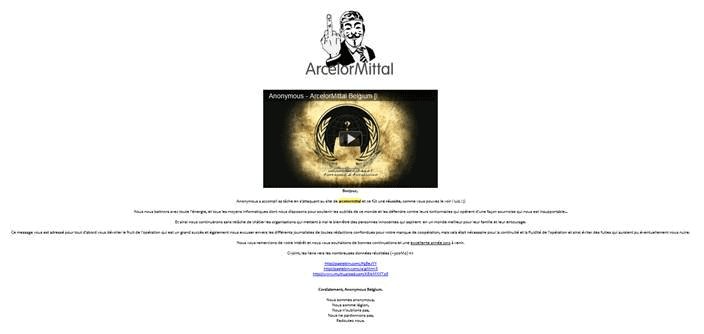
Other hacktivist (hacker + activist) attacks may only want to bring a website down to portray power or alter a site to show a message. Hacktivists are typically politically or socially motivated, aiming to send a statement.
The screenshot above is an example of a hacktivist attack. In 2012, the Anonymous hactivism group took down the website of ArcelorMittal, one of the biggest steel producers in the world. Anonymous Belgium took the site down, changed its homepage, displayed a message and leaked all their information—dealing a major blow to the company’s security and reputation.
How Do Websites Get Hacked?
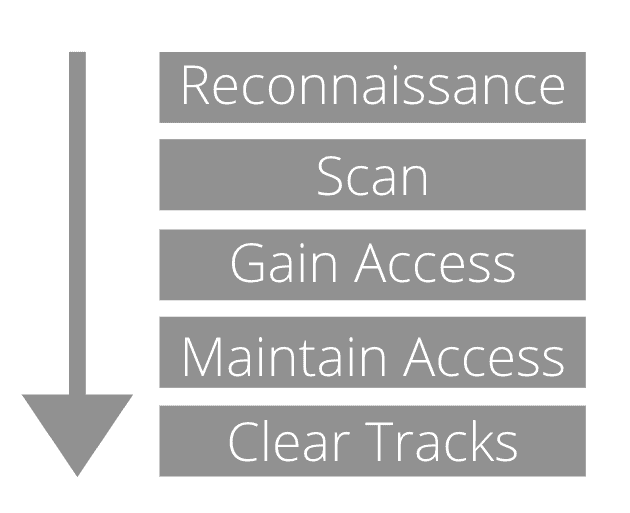
Hackers usually follow the five phases of an attack: Reconnaissance, Scanning, Gaining Access, Maintaining Access, and Clearing Tracks.
Hackers start their attacks in the reconnaissance phase, in which they need to gather as much information as possible unobtrusively. They will use passive scanning, enumeration and foot-printing techniques.
Some questions they’d consider in this phase are: Where are the web servers located? Which DNS are they using? Do they have WordPress? And what plugins are they using?
They might also go to social media and gather intelligence from employees unintentionally leaking confidential information. Hackers might look into publicly available CVs from IT admins, trying to figure out the type of technology they’re working with, looking for OS names, vendors, version numbers and other pieces of information.
Another common way hackers collect intelligence is using something called Google dorking or Google hacking, using the Google Hacking Database. Hackers would use Google’s advanced search terms to find a website’s vulnerabilities.
When hackers get all the intelligence they need, they’ll proceed to the active scanning phase. In this phase, they’ll use scripts or automated tools to scan networks aggressively. Many hackers are likely to start at this phase with random and automatic scans, trying to find easy access to vulnerable sites.
Once the hacker identifies weaknesses, they’ll need to gain access using various methods like SQL injection, brute force attacks and dictionary attacks. Later steps include maintaining access by installing backdoors and clearing tracks to win over the forensics investigation.
What Are the Security Risks of a Website?
In the game of hacking, there are opposing players: The attacker and the victim. We already covered the reasons for attacking and the stages of website attacks. Now we’ll change the focus to the victim—the websites. What are their vulnerabilities or security web risks?The Open Web Application Security Project (or OWASP) is an excellent framework to start with and keep in mind when assessing the vulnerabilities and risks of a website or web app. According to OWASP, the top 10 web application security risks for 2023 are:
- Injection. This type of attack forwards malicious code from an application to another, using system calls with power shell, SQL, LDAP, etc. SQL injections are the most common website attacks in this category. Attackers craft malicious code using SQL statements and input them in a web page search bar or any text input. This attack may be used to retrieve information from a database or even destroy it entirely. SQL injections are relatively easy to perform and can be devastating.
- Broken Authentication. As the name implies, this vulnerability deals with the improper management of sessions and authentication. Attackers may force and break easy passwords, keys or session tokens.
- Sensitive Data Exposure. Hackers are after sensitive high-value data. For example, data from financial or healthcare web applications/pages might need extra protection, like encryption, at-rest or in-transit.
- XML External Entities (XXE). Improperly configured XML processors may automatically assess references of external entities within XML documents. XEEs may be used to steal internal data or even perform DoS attacks.
- Broken Access Control. Broken access control is a type of vulnerability due to improperly configured (or total lack of) restrictions to authenticated users. Lack of granular control or segregated access may grant hackers entry to sensitive data.
- Security Misconfiguration. This is OWASP’s definition of default or incomplete security configurations. Misconfiguration is frequently a cause of unpatched systems. In websites, it could be misconfigured HTTP headers.
- Cross-Site Scripting XSS. This web security flaw allows hackers to run client-side scripts into vulnerable applications, most common, into websites viewed by other users. XSS compromises the interactions between the users and the application.
- Insecure Deserialization. Also known as the “object injection” vulnerability. Object serialization is a web development term that states that an object can be changed into a byte stream, and then back to an object. This flaw enables an attacker to control serialized objects and run malicious code into web applications.
- Using Components with Known Vulnerabilities. Website applications and APIs might be using many third-party components, from libraries to frameworks. When a zero-day exploit is discovered on any of these components, and the site’s developer is unaware of those specific components, hackers will quickly take advantage.
- Insufficient Logging & Monitoring. This is another website and application risk. Websites aren’t usually monitored and logged correctly. Even if the security is solid, hackers may still persevere and attempt different angles and strategies. There is also a lack of incident response.
What Is the Best Website Security?
If a black hat hacker has his eyes fixed on a high-value asset, website security tools will become an obstacle, but they will not stop the hacker.
According to a survey carried out by IT security firm Thycotic, 73% of black hat hackers view traditional firewall and antivirus security as “irrelevant or obsolete.”
So, the best website security is a combination of security best practices (website management processes) and a collaboration of security tools. It starts by identifying the access to your website and the type of “locks” they are using. Are you accessing your site via WordPress? Or FTP, SFTP? Or maybe via a control panel such as cPanel.
This is important:
Whatever method you’re using to access your site, make sure you employ strict granular access control and that passwords are unbreakable and changed regularly.For access, you can refer to the AAA (Authentication, Authorization, and Accounting) model and its protocols to help you control access.
For example, this AAA model can give you an idea of how to do a simple WordPress user assessment.
Also remember, authentication shouldn’t only be what users know (their strong passwords) but also what they have (face ID on their mobile device). So enforcing access with a multi-factor authenticator is a fantastic way to increase website security dramatically.
The second best practice is assessing its vulnerabilities. There’s a high chance that hackers would attack individuals and small businesses, but they also target medium to large companies as well.
Most of the time, hackers would only target whatever/whoever is vulnerable. They use automated tools to scan the web and discover vulnerable websites and apps.
Pro Tip
To reduce the chances of getting discovered by these scans, you should remove useless plugins, third-party apps that you no longer use and, most importantly, keep your systems up-to-date.How Do I Make My Website Secure?
The first step in boosting the security of a website is acknowledging that anyone can be a target of an attack. Hackers can target any kind of business—from enterprises and corporations to large, medium and small businesses. Even if you have a personal blog, you can still be the target of a ransomware or DoS attack.
When thinking about your website security, consider the perspective of the attacker. What would you go after if you were the attacker? What are your high-value assets? Is it the data of your website’s subscribers? Credit card numbers and other financial information? Traffic logs? Or maybe a hacker would want to target your audience?
Website Security Checklist:
The following checklist is not intended to be a comprehensive solution to website security. But it is a good starting point to build up the walls and improve your website security. The checklist contains the most important security measures to consider.
- Encrypt all data. Encrypting sensitive data, at-rest and in-transit, should be one of the top security priorities. Storing encrypted sensitive data may help you comply with strict data protection regulations such as GDPR. For in-transit encryption, switch from HTTP to HTTPS TLS/SSL. Unencrypted sites (without the padlock) will show an “unsafe webpage” message to website visitors. With HTTPS, the website communication between client and web server is protected with an SSL certificate. The “green padlock” ensures that the connection between client and web server is encrypted.
- Enforce Multi-Factor Authentication (MFA). MFA ensures that two or more pieces of evidence are used when authenticating an account. Knowing a password shouldn’t be enough, but also proving proof of the possession of a device (mobile phone) or knowing something else (like an answer to a question). 2FA works anywhere, locally or abroad. MFA goes along pretty well with access level control and a policy for strong passwords.
- Scan your website for malware. Your website’s file system database might be at risk of getting infected with malware. Some services will scan your site and detect malware, malicious code, errors, outdated software and even blacklisting status. Website scanners are useful tools that will scan, discover and help you remove destructive malware.
- Disable unsafe configurations. Remove default, old and unused accounts. Also, disable administrative interfaces, debugging and any unused features. Hackers could use the latter for reconnaissance and access. Using a simple platform without any unneeded components can save you from an unsafe misconfiguration.
- Perform regular automated backups. Backups are the best incident response to any serious attack. A good tool to help you remember is the 3-2-1 rule. Keep at least three backup copies of your data, store two on different storage media, with one of them offsite. Never use the same web server to store your backups; always use remote storage. Even though you’re storing sensitive information offsite, keep all at-rest encrypted. Also, do automatic backups frequently, at least daily. Fortunately, there are fantastic server backup applications that can be automated to get the job done.
- Update all your website’s software. Content Management Systems (CMS), such as WordPress, Shopify, or Joomla, need to be updated regularly, especially when using plugins. Additionally, always be on the lookout for updates to other software programs such as cPanel, FTP clients and HTML editors.
- Use a Web Application Firewall (WAF). A WAF can be either on-premises (hardware to software) or 100% cloud-based. The purpose of a WAF is to monitor and filter out abnormal behavior before it reaches your website. A Web Application Firewall protects your systems and data. They monitor HTTP traffic and detect and mitigate prevalent attacks, such as SQL injections, XSS and insecure deserialization.
- Simple penetration testing. It is highly recommended to perform quick and straightforward penetration tests. From the outside, try accessing your website’s platform with a combination of default usernames and passwords. A fast brute force attack on your public-facing resources may also give you an idea of where you stand. A development sandbox can be useful for testing all new site applications and features in a live, non-public and safe environment. A more comprehensive website vulnerability assessment should be left for the security auditors.
Additional Advanced Controls:
To further improve the security of your website and mitigate common attacks, employ the following advanced security measures:
- Use a Content Delivery Network (CDN). CDNs were created to provide faster delivery of content from different geographically distributed web servers. The very nature of “edge computing” from CDNs will help you protect your websites against attacks like DDoS.
- Make sure all statements are parameterized. Specify parameters in the SQL statements—queries performed by the visitor. Also, make sure that all stored procedures in the database are parameterized.
- Disable External Entities DTDs. Make sure the developer sets the XML parser to reject custom DTD (custom Document Definition). You can also use Static Application Security Tools (SASTs) to discover XXE vulnerabilities automatically.
- Enforce policy controls to prevent access to unauthorized files. Access Control Lists (ACLs) or Security Groups can help you bring some granularity to your website access.
- Perform validation and encoding on the server.“]According to OWASP, a good way to protect from XSS attacks is to ensure that all dynamic content from the datastore is not used to inject JavaScript.
Putting Everything Together
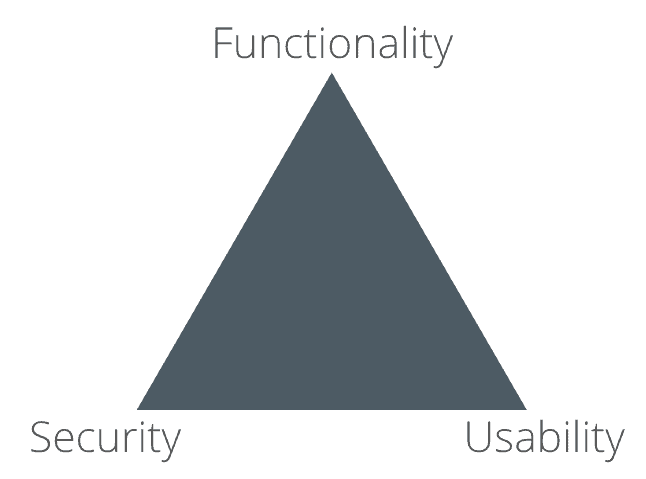
Again: It is better to have no website at all, than to have an insecure website. Of course, you could also take it to an extreme and have the most secured website ever, with the highest protective walls. But in reality, extreme security would only compromise your website’s usability and functionality. Your website visitors/users, subscribers or even other website owners would be quickly turned off by the complexity and lack of functionality.
The Security, Usability and Functionality Triangle (pictured below) is a model used by developers, manufacturers, product designers and web designers to find the perfect balance between these design elements.
Use this model, to employ a proper and clean access control, but never undermine usability. Looking between the interdependencies of these three qualities will help you have a balanced website.
Forgetting about security will probably allow website managers and developers to improve usability and functionality. It will bring more website visitors and it will be easier to use, with more features. But a lack of security will catch your back pretty soon.
How To Make Your Website Secure: Things To Remember
- Never configure security with a set-it-and-forget attitude.
- Hackers are interested in vulnerable and easy-to-hack websites.
- Use the security measures pointed out in the checklist.
- Employ strong access control. Use the AAA model.
- Tools such as WAFs and malware scanners will help you improve security.

 What Is Website Security?
What Is Website Security?