Cybersecurity software apps are mobile programs that help to enhance the overall data security of mobile devices, systems, or networks. These apps protect devices against unauthorized access and use of resources, intrusion, and attack. In doing so, user information such as pictures and passwords are protected from leaks and exposure. Businesses and organizations can win the loyalty and trust of customers, handle remote workforce risks, prevent or stop zero-day attacks, reduce downtime and boost productivity.

The 12 Best Cyber Security apps for Android are listed below.
- Norton Mobile Security
- SpamTitan Email Security
- Lookout Security & Antivirus
- Google Play Protect
- Malwarebytes
- DriveStrike
- Acronis Cyber Protect Cloud
- Securden
- ProtonVPN
- LastPass
- Resilio Sync
- GlassWire
Table of Contents
1. Norton Mobile Security
Norton Mobile Security is a cross-platform mobile security platform made for tablets and smartphones. This subscription-based security suite offers a real-time proactive protection program including malware removal and prevention. Norton Security also provides performance tuning tools, email spam filtration, phishing protection, and a personal firewall.
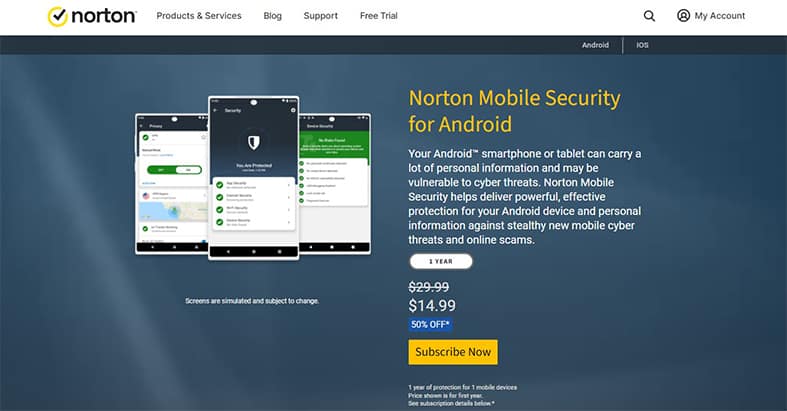
Norton Mobile Security delivers effective and powerful protection for both IOS and Android devices while protecting users’ personal information against online scams, new and emerging cyber threats, and malware. The web protection feature detects malicious and fraudulent websites including MMS, SMS, apps, emails, and social networking sites thus protecting users’ personal information. With Norton, users are alerted when a dangerous network is accessed or when the network is under attack; thus securing users’ financial and personal information. Operating across various devices, Norton safeguards online privacy, protects users from risky apps, helps to recover stolen or lost devices, and restores lost contacts.

Norton Mobile Security achieves a 100% detection rate, ensuring that even the smallest pieces of malware are detected and prevented. Norton also scans all applications prior to them being installed on to the device. This proactive approach ensures only virus-free apps are installed on a user’s device. Norton Security also has an app advisor that helps protect smartphones from threats such as ransomware, malware, privacy leaks, and adware, using top-notch patent-protected scanning technology. The mobile security tool also provides device security, a feature that alerts users to vulnerabilities so that proactive actions can be taken. There’s also a device report card that enables users to see a 30-day analysis of past scanned wireless networks, risky apps, websites, and device vulnerabilities. Furthermore, the tool features SMS security that filters text messages which may contain phishing attacks. For additional security, the security app enables users to develop a virtual safe which can be used to singly lock apps. Norton also offers extensive web security by deploying several features including Safe Search, Web Protection, Wi-fi Security, Link Guard, and Wi-fi privacy. Norton Mobile Security size offers 25GB storage space with the ability to add more space at a prorated price.
The download process is quite straightforward. From an Android or IOS device, head to the Google Play Store or Apple Play Store to download the app. Once downloaded, click on the install button and select “accept” to install the tool. Upon final installation, tap the “open” button, this will lead to the Terms and Conditions page which should be studied carefully and upon satisfaction, continue to the next page by clicking the “continue” button. From the menu icon located at the upper left side of the screen, click on the sign-in option, then provide the email address and password associated with the software. Next, click the sign-in button and follow the instructions displayed on the screen to complete the installation process.

Now that the app has been successfully installed, the next stage involves launching and using the app. To do this, launch the software from the home screen of an Android or IOS device. Open the app and select the preferred purchase option. Proceed to purchase a preferred plan, sign in to the Norton alert displayed on the screen and click on the sign-in/register button to activate the mobile security tool automatically. The security app is now ready to protect the device.
Norton Mobile Security is fast and efficient enough to detect mobile threats of any kind. The security tool is easy to install and is devoid of irrelevant inquiries and complexities. Norton is also available at an affordable price and the interface is intuitive. However, the app sometimes takes a long time to scan apps, websites, and other tools and a free version is not available. Finally, Norton does not offer an anti-theft function anymore.
Norton Mobile Security isn’t free, the tool offers a one-year subscription plan. While this plan previously cost $29.99 per year, at the time of writing there is a sale on the official Norton website, selling this plan for $14.99 per year. This subscription covers one device.
2. SpamTitan Email Security
As the name suggests, SpamTitan Email Security is an advanced email phishing protection program that uses AI and double AV-driven URL detection tools to detect and block malicious threats as well as prevent spear and whaling phishing. The spam filtering solution caters to schools, managed service providers (MSPs), and businesses to help block viruses, malware, spam, ransomware, phishing attacks, and other email threats. This solution can either be deployed in the cloud or on the premises.
SpamTitan protects the user’s device by scanning all inbound and outbound emails in real-time. But beyond scanning messages, the software also scans attachments for the latest viruses; when a threat is detected, the app blocks such messages from being received. Also, SpamTitan can anticipate new and emerging attacks with the tool’s predictive technology, thus enabling the software to prevent a zero-day attack. SpamTitan identifies and prevents viruses through email, email spam, malicious links, malware, phishing attacks, and other email-related malicious threats.

SpamTitan includes robust data leak prevention (DLP) rules to prevent internal loss of data. As stated, with the software’s predictive technology, the app can anticipate new attacks and prevent zero-day attacks. Also, the security tool includes six special Real-Time Blacklists (RBLs) and carries out comprehensive content filtration. Furthermore, SpamTitan provides security against infected attachments by enabling the blocking of malicious attachments while preventing a user’s IP from being blacklisted.
Users can customize policies while the app’s extensive quarantine report enables end-users to have control over personal accounts. The app’s excellent next-generation sandbox security solution protects users’ devices against email attacks. Additionally, the email solution has various deployment options to meet various needs; there’s the SpamTitan Gateway, SpamTitan Cloud, SpamTitan for Service Providers, and SpamTitan for Office365.
While SpamTitan has no specified size, the security solution can cater to all sizes of business including small, medium, and large.

The download process for SpamTitan Email Security is easy, simple, and short. To download the software on a desktop computer, head on to the app’s website and click on the download button to begin the process. Once downloaded, click on the app to commence the setup process. When this is done, the user should be able to see the app and run the program.
SpamTitan has many advantages. To begin with, the mail security solution offers protection to both outbound and inbound emails. The app carries out quick scans to screen and detect malicious threats. Also, SpamTitan has anti-phishing features while preventing malware invasion and spam. Furthermore, the security tool is powerful and easy to manage, provides adequate support, and is reliable.
On the other hand, SpamTitan isn’t the most cost-effective email security solution. Also, the tool has a poor end-user experience and poor integration with outlook. The plugin of the security tool has been criticized for being unstable.

There are various pricing options that users can select from. The cheapest is the 30 days free trial which costs nothing but allows a limited number of users and offers limited services. Then there is the paid option, which provides several choices. The first is the 100 users monthly plan which costs $1.26 per user per month, and a total of $126.50 for 100 users. There’s the 100 users’ yearly plan. This costs the same at $1.26 per user per month with a total of $1518.00 for 100 users per year. There’s also the 100 users 2 years plan; this plan attracts a 5% discount, thus the 2-year plan costs $1.20 per user per month, bringing the total cost for 100 users for two years to $2884.20, saving a total of $151.80. Finally, there is the 100 users 3 years plan. This features a 10% discount, bringing the price per user for a month to $1.14 and for three years to $4098.60. The saving with this plan is $455.40.
Note:
SpamTitan deploys various techniques and procedures to protect businesses and organizations and ensure privacy is not compromised. This is done by blocking malware, spam, ransomware, adware, and links from malicious emails. This email security tool protects email accounts, communication, and content from compromise, unauthorized access, or loss.3. Lookout Security & Antivirus
This is an all-in-one mobile antivirus and security software that protects users’ data, identity, and mobile devices. Deployed on over 200 million devices and with over 155 patents and analysis of more than 100 million apps, the software offers data backup, malware protection, and remote management for tablets and smartphones.
Lookout Security & Antivirus scans files and apps for spyware and viruses, enables users to choose the apps that can access personal information, and protects devices against web-based threats while browsing. The app also reports security breaches, has anti-theft functions with top-tier lockdown options, an excellent privacy adviser, and a decent antivirus tool.
Lookout Security and Antivirus boasts advanced mobile security that protects devices by locating and stopping threats before they can harm the user’s device. This security app also ensures the wi-fi network used is safe and secure as the app alerts users when users join a dangerous wireless network or when the Wi-Fi is under attack. With the app’s privacy advisor, users can keep personal information private because the tool displays which apps can access a user’s contacts, locations, identity data, and messages. Lookout Security and Antivirus ensures safe browsing while the system advisor checks through a user’s device for root detection to ensure the system is functioning seamlessly. All of these features make Lookout Security & Antivirus important security software for millions of users.
The total file size is 15.95 MB on Android and 85.4 MB on IOS. However, the required version of the IOS device is 12.0 or later for iPhone and 12.0 or later for iPad. The minimum required version for Android is version 5.0.

The app is easy to download and use. To install the app, users must visit either the Apple Play Store for IOS devices or the Google Play Store for Android devices. From there, type the app in the search bar and select download or install when prompted. Once downloaded, click on the app to open. Next, the user will be required to create an account. To do this, provide an email address for the username and any password of choice.
Like every security app, Lookout has pros and cons. The user has a solid user interface and works perfectly in the background without impacting or affecting the device’s resources such as memory, power, and network. Besides, Lookout is easy to use and has strong identity-protection options. Also, the app has useful features and yet does not possess overly cumbersome features.
Despite the tool’s many advantages, Lookout’s free version does not offer many features. Also, the software does not offer robust customer support, (there is no chat tech or telephone support for instance). Further, Lookout has poor malware-protection test data.

Lookout Security offers three tiers of subscription plans. There’s the Basic plan which comes at no cost; however, this plan delivers only core features which include predictive security, system advisor, and some Missing Device features. There’s the Premium plan though which costs $2.99 monthly or $29.99 annually. There’s also the Premium Plus plan which goes for $9.99 per month or $99.99 per annum. Both the Premium and Premium Plus versions provide robust features including predictive security, a system and privacy advisor, safe browsing, safe wi-fi, and breach report. The plans also offer Missing Device features including locate, scream, theft alerts, lock & wipe and signal flare. The Premium Plan, however, offers other extra perks such as a Cyber Watch, Social Media Watch, SSN Watch, Lost Wallet Recovery, 24/7 Restoration Assistance, and $1M Identity Theft Insurance.
As well as the security and privacy protection that Lookout Security provides; the software also provides other security and privacy functions. Firstly, the Identity Theft Protection encompasses several features, including breach reports which alert users when there’s a breach and recommend action points to take. The $1M identity theft insurance provided ensures users can recover any financial damages resulting from virtual identity theft. The app also offers a white-glove identity restoration report that ensures users can access ID restoration experts via phone anytime. The app also alerts users whenever there’s a leak. Asides from all these, the app also offers Theft Protection. With this security function, users can pinpoint the exact location of a phone whenever the device is stolen or lost. Also, whenever a phone gets stolen, the owner receives an email with the location of the phone and a picture of the thief attached to the email. There is also a signal flare that alerts users when a phone goes off. Finally, Lookout security also features Lock and Wipe; this feature enables users to erase all personal information if the device is missing or stolen.
4. Google Play Protect
Google Play Protect is a malware detection and protection service incorporated into Android devices that make use of Google Mobile Services. The security app which is arguably one of the most widely deployed security tools keeps systems and devices safe and secure by running safety checks on apps before users can install those apps.

Google Play Protect automatically scans all the Apps on an Android device that are updated and alerts users if there are any threats found. The security tool also scans apps before downloading and allows only the installation of safe apps while preventing the installation of harmful apps. By using proprietary algorithms that are constantly learning and adapting to emerging threats, the security tool is constantly updated to effectively wade off the latest malware. The in-built protection program works in the background, checking and scanning for harmful apps that may leave a user vulnerable.
Google Play Protect offers both on-device and cloud-based security, making the app very important to users who are security conscious. For on-device protection, Google Play Protect deploys several on-device capabilities to keep devices safe. These services combine with cloud-based components that enable Google to bring up updates that constantly improve the functionalities of apps. On the other hand, all Android apps go through intense security tests before featuring in Google Play Store. Google Play Protect goes further to scan more than 100 billion apps available on the Play Store every day to ensure the apps are within standard and do not contain viruses. With this, no matter where an app is downloaded from, users can be assured that the app has been checked and verified by Google Play Protect.
As a result of the app’s inbuilt nature, users are not required to download the app. However, Google Play Protect can be activated and deactivated. To activate the app, open the Google Play Store on an Android device. Click on the user profile icon located at the top right corner of the screen. Click on Play Protect and then click on “Scan apps” to turn on the software. The same is done to deactivate the application. Users can also discover if a device is Play Protect certified, to do this, the user will need to click on “Play Protect Certification”. Furthermore, if a user chooses to download apps from unknown sources, these apps can be sent to Google to verify the safety of the apps. To do this, the user will need to open the Play Store and click on the top right of the profile icon. From there, click on “Play Protect” and on “settings”. Once there, turn on the “improve harmful app detection”. Once an unknown app is downloaded, Play Protect will carry out an analysis and inform the user if the app contains malware.
Google Play Protect is liked for many reasons. The app is built into Android devices; hence users do not need to download the app. The app has minimal system impact, as the software works in the background. Also, Play Protect has solid anti-theft tools and automatically offers solid services without the need to download or activate the app.

On the other hand, Google Play Protect does not have robust features. Besides, the app’s malware protection is not the same standard as many competitors. However, Google Play Protect is completely free as it comes inbuilt in most Android devices. There are no in-app purchases.
Google Play Protect runs an in-depth safety check on any downloaded app. If the downloaded app is seen to be harmful or violates Google’s Software Policy, a notification is sent to the user informing the user of the potential problem before installation is complete. The user can then choose to forego the download or delete the infected file from the device. The security software also carries out periodic device scans to check for malicious apps that may have been previously installed, especially those retrieved from sources other than the Google Play Store.
5. Malwarebytes
Malwarebytes is an American Online security company that specializes in protecting users’ devices from malware. This cross-platform anti-malware software scans, detects, and deletes malware and other viruses. In doing so, Malwarebytes protects computers against viruses, hacks, malware, ransomware, and other new threats, thus enabling a safe and virus-free online experience.
Malware which primarily functions as a scanner, checks and removes adware, spyware, malware, and other rogue software. The software scans apps and files in batches rather than scanning all opened files. This reduces interference and interruption if there is other on-demand software working simultaneously with the app. However, the security tool does not carry out any malicious functions once an app has been downloaded, thus Malwarebytes uses a proactive approach, rather than a reactive one.
Malwarebytes’s importance lies in the app’s ability to offer great online security. The app cleans and clears infected devices and protects vulnerable systems from malware attacks. There are warning tools to alert users if any issue is detected and this is done using a centralized threat reporting system. Also, the app features prevention tools to prevent ransomware attacks from occurring. Besides, Malwarebytes unifies various threats using a centralized management system. In addition, the software has flexible push-install options and carries out quick deployments while also ensuring all networked endpoints are discovered. Furthermore, Malwarebytes deploys asset management to track, deploy and manage endpoints.

To download Malwarebytes, first head to the Google Play Store app and search for the security app. Tap the app to begin the installation process. Click the open option when the installation is complete and then click on “Get started” to proceed. For first-time installation, Malwarebytes requests security permissions from users. Thus, click on “Give Permission” to continue. After that, tap on “allow” to enable Malwarebytes to access folders and files. The app is now enabled.
Malwarebytes has an excellent user interface that’s intuitive and easy to use. Also, Malwarebytes automatically scans apps and devices and also has shield features that provide comfort to users and ensures devices won’t get infected with malware. Besides, Malwarebytes is cloud-based which makes the app reliable. In addition, the app has responsive customer support.
However, Malwarebytes would be better if the app features patch management as this will ensure quick resolution and patching of cyber security issues. The app also isn’t as efficient as most competitors. For instance, Malwarebytes may declare a system as clean but when the same system is scanned with other security apps, some issues and threats may be detected. Moreover, rootkit scanning can become so cumbersome on a device that the device becomes nonfunctional.

While Malwarebytes offers a free plan, the plan is very limited. However, this cyber security app for Android offers various paid plans both for personal and business purposes. In the Personal Plan category, the Premium Plan plus Privacy costs $8.33 per month or $99.99 per annum and protects up to five devices. The app also provides two premium plans. The first plan offers advanced antivirus and anti-malware with safer internet browsing and can protect up to five devices; the plan costs $6.67 per month or $79.99 per annum. The other premium plan also offers the same security features but protects one device for just $3.33 per month or $39.99 per annum.
There are also various Business Plans. To protect between one to nine devices, businesses will have to pay $49.99 per device per annum. Businesses can also subscribe to the 10 to 99 malware endpoint protection; while this plan normally costs $69.99 per annum, the plan now costs $52.49 as there is a 25% off sale currently. For businesses with over 100 users, the plan costs $69.99 per device per year. Finally, for server protection (which features advanced malware remediation and threat prevention for small to medium scale businesses) businesses will need to pay $249.99 per device per annum; however, there is a 25% discount on the plan, thus the plan currently costs $187.49 per device per year. Each paid plan comes with a 60-day money-back guarantee.
Malwarebytes offers great antivirus programs to protect Android devices against hacks, ransomware, viruses, malware, and other emerging cyber threats. With one click, Malwarebytes VPN can be activated. This ensures privacy, online safety, and security as the VPN uses military-grade 256-bit encryption, while also offering DNS leak protection and an automatic kill switch to ensure complete privacy.
6. DriveStrike
DriveStrike is a device and data protection solution for lost, stolen, retired, or missing devices. The cyber security software empowers users to protect devices that are no longer with the user, thereby preventing the compromise of the user’s data. DriveStrike is ideal for professionals, schools, businesses, organizations, and individuals who need to protect devices and data from theft, loss, and compromise.
DriveStrike provides cloud-based device and data protection solutions that help individuals and businesses of all sizes with compliance and data security. The functions of DriveStrike include activity tracking, activity monitoring, archiving & retention, application security, audit management, audit trail, a best practice repository, and policy management. This security tool also carries out incident management, real-time monitoring, compliance management, data management, data security, deployment management, endpoint management, and automated device/user recognition. Other functions include financial data protection, geolocations, and risk management amongst others. From individual accounts to Fortune 500 firms in the legal, healthcare, eCommerce, government, financial services, and entertainment, DriveStrike prevents data breaches to enhance compliance, confidentiality and give a competitive advantage.
The device and data protection solution is important for many reasons. For starters, DriveStrike cleans and sanitizes the main drive, but beyond that, the software also wipes all secondary linked drives, thereby preventing data breaches from compromised devices. Also, with DriveStrike, devices can be locked remotely on request. DriveStrike can lock users out, reboot a device, initiate a firmware lock, and reset device passwords, all to prevent unauthorized access to sensitive data on missing or stolen devices. The app goes beyond IP lookup, leveraging all geo-location assets including triangulation of wireless networks to locate lost or stolen devices. DriveStrike also constantly requests location updates to monitor the historical location of devices. This security tool also integrates BitLocker for Windows and assists with VeraCrypt deployment. While native encryption isn’t yet enabled, the feature is being worked on.

The installation of the app is quite easy and the device is compatible with all major devices including Linux, Windows, macOS, IOS, and Android devices. There are two ways to install DriveStrike on Android. The first method involves Android (Enterprise) Installation. Here, a user will be required to start with a factory reset device. Follow the prompts to set up the device and ensure the device is connected to a wireless network when given the option. Next, input “afw#drivestrike” when asked to sign in to a google account and click the “next” button. Confirm the installation and continue with the prompts that appear. A DriveStrike registration notification will be sent, click the notification and register the device to the app’s account. DriveStrike has now been installed in Enterprise mode.
For Android (BYOD) installation, users will have to head to the installation page on the app’s account. From there, send an email to the end-user of the device to be added. The end-user then downloads the installer and will have to follow the prompts to install the app and register the device to the owner’s account. When required to select a profile setup, the owner is required to choose “Shared Management”. DriveStrike has now been installed in BYOD mode.

DriveStrike is easy to use and has great customer support; the app is also easy to implement on many devices. DriveStrike is so lightweight, users won’t notice the presence of the app; DriveStrike works seamlessly in the background without bloating the device or impacting the system’s power, internet, and other resources. On the downside, DriveStrike has a cumbersome and confusing installation process.
Users can test all the features of the app using the free 30 days trial. However, further use beyond that requires payment. There are various plans which mainly differ depending on the number of devices covered. To protect between 1 and 20 devices costs $2.00 per device monthly and $20.00 per device annually. For devices numbering 21 to 100, a monthly subscription fee of $1.50 per device is required to be paid while the annual fee for a device is pegged at $15.00.To protect from 101 to 500 devices, a monthly subscription fee of $1.35 and an annual fee of $13.50 per device are required. Lastly, to protect more than 501 devices, a fee of $1.25 monthly per device and $12.50 annually per device is charged.
Since encryption is an important tool for data safety, security, and privacy, DriveStrike uses encryption protocols to secure users’ data. With DriveStrike, users can enable BitLocker encryption; users can also escrow and manage keys or create new keys. A forced reboot can also be initiated to secure devices. These are done remotely for fast and efficient fleet management as well as privacy and security of users’ data.
7. Acronis Cyber Protect Cloud
Acronis Cyber Protect Cloud is a cyber security program that allows service providers to deliver cyber protection in a secure, efficient, and effective way. The software merges backup and next-generation AI-based antiviruses, endpoint management solutions, and antimalware solutions in one package. The tool also integrates cybersecurity, data protection, and endpoint management into one solution for centralized administration and tracking. Simply put, Acronis enables clients’ backup and recovery photos, contacts, videos, and calendars from mobile devices.
Acronis integrates seamlessly with PSA and RMM systems. The software app helps to discover malware and other threats present in an Android device by scanning full-disk backups at a central location—with these users can create a clean backup free of malware. The software also carries out automation and integration to reduce complexity, increase productivity and reduce operating costs.
This cyber security software provides active protection from new cyber threats; Acronis uses an anti-ransomware technology with AI-based static anti-malware analysis to prevent zero-day attacks. There is the CyberFit Score, which accesses some security metrics, identifies gaps, and then recommends a solution to improve a client’s security. Also, the tool enables clients to scan devices to identify vulnerabilities and update all apps and operating systems to avoid exploitation by cybercriminals. Acronis also has a monitoring and reporting system that helps simplify operations while also giving technicians the insight needed to find solutions. With the app’s ability to enable customization of dashboard widgets, users can quickly identify and fix identified issues.
Furthermore, Acronis Cyber Protect Cloud has a centralized protection plan and group management system that allows for easy grouping of multiple workloads and application of security configurations across several endpoints simultaneously. With the app’s secure file sync and share feature, users can easily and safely develop, edit and share content using personal devices. Moreover, Acronis provides other advanced security including threat tracking and smart alerts, a forensic backup, data protection map and compliance reporting, patch management, and so on. All of these make Acronis an important software app for privacy-savvy users.

Acronis has an unusual download and installation process. To start with, the app only supports Android 6.0 and higher. Also, before the app can be installed, the Backup Console will first need to be installed. To this, head on to the app’s URL in the browser of any Android device. Next, log in to the backup console and thereafter add the device that needs backup by clicking on the Android option when prompted. This will open the Google Play Store; click on install to install the app. Acronis is now installed and ready to use. To configure the Acronis Cyber Protect Cloud, open the app and click the “next” option. In the login field, input the client’s username used in the Backup Console; tap “login” to continue and tap “next”. Enter the same password used to set up the Backup Console and then click on “log in”. This will lead to the setup page. Here, click on “set up” and then indicate the data to save. To back up data, click on “backup”. Grant access authorization when prompted. The app has now been set up and is ready to back up any data.
The benefits of Acronis Cyber Protect Cloud are numerous. The software integrates storage, backup, and data protection solutions for small and medium businesses. The security tool also features a forensic backup option. In addition, Acronis is designed for remote workers and features powerful and functional ransomware protection. On the other hand, Acronis only offers mobile apps for advanced tiers. Cloud storage is also not integrated but rather offered as a separate product. The app also isn’t the easiest to use.

Acronis Cyber Protect offers various plans that clients can choose from. The cheapest is the Acronis Cyber Protect Essentials plan, which costs $59.00. There is also the Acronis Cyber Protect Standard that costs 79.00 and the Acronis Cyber Protect Advanced that costs $119.00.
Acronis Cyber Protect Cloud provides top-tier cyber security and privacy protection. This is done by addressing new and emerging cyber threats using an improved detection rate, smart protection plans, and deploying additional protection for forensics, backups, and recovery. With the app’s global threat tracking and smart alerts, and forensic backups, user data are never compromised.
8. Securden
Securden is one of the best cybersecurity apps for Android devices. The app is an endpoint protection program created to enable businesses of all sizes to have control over applications, have privileged access, and control remote endpoints. The software also enables administrators to use the password vault to manage, store, and share-secured keys and certificates.
With claims to be one of the leading providers of privileged access solutions, the software uniquely combines the principles of least privilege enforcement, continuous risk assessment, and zero-trust architecture to prevent malware propagation, cyberattacks, and in-house exploitation. Securden provides password management solutions for privileged accounts. The software also carries out other functions including cybersecurity, identity management, endpoint protection, and privileged access management.

Securden is important to businesses for many reasons. Firstly, with the software installed, users can store all passwords, logins, documents, keys, and other identities in a central vault. The software also allows for the organization and classification of this information for easy access. Securden also enables users to discover privileged accounts on Linux, Windows, and Mac devices along with apps and databases. Also, users can define ownership for an account and share passwords with team members while being in control of the account. The software also has established controls on persons that can access certain passwords. Provision and de-provision access can be done seamlessly.
Securden grants access to users without disclosing record sessions or passwords, features advanced authentication, including directory integration, secure service accounts, application passwords, and SSH keys, tracks activity, ensures compliance, and promotes visibility. In addition, Securden has enterprise-ready abilities, has simple features for easy use, and can combat identity theft.
The download process is easy. Just go to the Google Play Store and enter the app name. Click on the install button to begin downloading. However, the next process is quite cumbersome. Users will need to input Securden login details and follow the prompts to install and use the app.
Like most password managers, Securden ensures easy access to all passwords, logins, and usernames. Users can also easily switch between accounts and share passwords without actually sharing passwords. Also, Securden is feature-filled, enabling the app to fight identity theft, manage credentials easily, track password activities and changes across the company. The software has a simple and convenient user interface and credentials can be auto-filled.On the downside, Securden has a complex download process and is more suited for businesses than individuals.

Securden offers various price plans to meet the needs of users. The software is available in three editions. The Starter edition is the lowest costing plan and is free for five users. There’s the Securden Teams edition, the Enterprise edition, and the Enterprise PAM edition. While each edition comes with a fantastic 14-day free trial, Securden does not make public the prices of the plans; users will have to contact the software to get a quote. However, each plan comes with a 30-day money-back guarantee. Users can cancel at any time and get a prorated refund. Also, special discounts apply to non-profit organizations as well as educational and government agencies.
Securden locks access keys, passwords, files, and other sensitive information in a central vault which is then protected by the software. The app deploys security and privacy functions including multi-factor authentication and actionable security reports. The software also helps in establishing a centralized password repository and enforcing two-step verification for enhanced security and privacy.
9. ProtonVPN
ProtonVPN is a virtual private network service provider that places much emphasis on online privacy and the security of user data. The service is a product of Proton Technologies AG, a Swiss company and the operator of Proton Mail. This security software offers a bunch of advanced tools for privacy that are usually found in more expensive tools.
Just like other VPN services, ProtonVPN offers the user cybersecurity. Intending to make online privacy accessible to all, ProtonVPN offers users a secure internet connection and an advanced security technology that is easy to use and freely available. With ProtonVPN, users can be sure of being safe from online security risks and being monitored by internet service providers (ISPs).
Proton VPN is packed with a host of features that have increased the relevance of the software among its users. Among these is that the software has a free version with unlimited data usage and does not compromise the security of users. This security software is also ad-free and very easy to use with a simplified interface, allowing users to enjoy cyber security with little or no stress.
With over 500 servers located in 54 different countries, ProtonVPN also offers a diverse geographical distribution of servers. In addition to this, ProtonVPN also allows the user up to 5 VPN connections and allows fast and secure P2P sharing among users. However, paid versions of the app contain more features than the free version.

The ProtonVPN desktop app has a download size of 20MB on the Android operating system. However, this size may vary across various operating systems and devices. Regardless, the app takes up a small amount of space on the device storage.
The ProtonVPN app is very easy to download. The app can be downloaded from multiple app stores such as the Google Play Store, App Store, Microsoft Store, and more. Users can also download the app from the official website of ProtonVPN. Once the app has been downloaded, installation can easily be done on the device by following the detailed instructions.
There are a few reasons why users should opt for ProtonVPN as their preferred online security app. The app arguably has one of the best free subscription plans, boasting some flexible and low-cost plans. Also, with numerous advanced privacy tools, users can enjoy great features and maximum online security at relatively low costs. In addition to these, the app is also very easy to use and has fast VPN speeds. With a server network speed of up to 10Gbps, VPN speeds can be improved by over 400%, giving users a very fast user experience.

One notable downside of the app, however, is that the app does not possess any public audit of infrastructure. Also, ProtonVPN cannot be said to be the cheapest VPN service provider out there. Although, the host of features possessed by the online security service makes the software worth the price.
ProtonVPN has a free plan and a mix of other paid plans that the user can choose from. These paid plans come at different prices and offer different services and features for the user to choose from. The first plan is the Basic plan, which goes for $4 per month and is billed at $48 per annum, thereby enabling users to save $12 when they subscribe to the yearly plan. There is also the ProtonVPN Plus plan which costs $8 per month and $96 per year. The annual plan enables users to save up to $24. Finally, there’s the Visionary plan which costs $24 per month and $288 per year; the annual plan helps save $72. ProtonVPN offers a 30-day money-back guarantee for users.
Note:
ProtonVPN also offers users an encrypted internet connection. Besides, with the use of encrypted tunnels, ProtonVPN ensures that the user’s connection is not being spied on or eavesdropped on. This feature also allows users to access sites that have been blocked in the user’s country.Like most VPNs, ProtonVPN deploys the best encryption to ensure the security and safety of users’ online activities. This includes an automatic kill switch, DNS protection, and AES-256-bit military-grade encryption. ProtonVPN has a privacy statement that says that a user’s activity or IP addresses are not logged by the software company. The company makes money solely through subscription and does not sell user information, user profiling, or engage in any form of advertisement, which may become a security risk for the user.
10. LastPass
LastPass is an online password manager that allows users to save passwords and have secure access to their computers and mobile devices. The company was initially acquired by LogMeln Inc in 2015 but was later made into a separate company in December 2021. With LastPass, users can easily keep critical information safe and secure, to be accessed anytime and anywhere, giving users complete control of online life and activities.
LastPass allows users to save passwords, addresses, credit cards, etc. in a secure place. The information can then be retrieved automatically by the software whenever the information is needed by the user. This makes the filling of forms online and other such activities easier as data can be auto-filled. In addition to this, LastPass also provides online security for users, allowing the users to access online accounts securely. This is achieved by generating secure passwords to replace weak passwords, alerting users to potentially risky or harmful data, having a robust multi-factor authentication system for user accounts, and more.
LastPass generates strong passwords for users when signing up for a new account or changing an already existing password, providing users with a very reliable password that uses all four sets of characters (lower case letters, numbers, upper case letters, and symbols). Also, this password manager prompts users to save user login credentials when logging into secure websites. However, the user has the option to decline this option. The password manager also possesses an “emergency access” tool that allows users to give a trusted contact access to the user’s vault. Another feature of the software is a 1GB storage (for free users) and up to 10GB (for paid subscriptions) for storing user information in an encrypted format. Other features include multi-factor authentication, security challenging, a sharing center, and so on.

LastPass has a download size of 17MB and is compatible with Windows and Mac operating systems. The app is also compatible with Android and iPhone operating systems. Download size also varies with app version and source of download. This app can be downloaded from the Google Play Store. Just input the app and click on the install button to download. Next, go to settings and then to autofill. Put on the switch for the autofill login information settings. Click on “next” to bring up the device’s accessibility menu. Click on “LastPass” and then toggle on the app setting. LastPass is now enabled and ready for use.
One of the strengths of LastPass that make the app a good choice for users is a free version that stands out and offers a wide range of features. The app also offers affordable paid plans with unique premium features. The app also possesses a strong security framework and a two-factor authentication system that secures user accounts and keeps attackers away.
Some of the downsides of the app include a slow customer support response and an expensive premium version. Also, importing a database from the app is often difficult.
This software possesses a free plan and various paid plans for users. Paid plans vary from individual and family plans to paid plans for businesses. For the Single Users and Families category, the Premium plan is billed $3 monthly, while the Families plan costs $4 per month — each offers a 30-day free trial. For the Business Plan category, there’s the Teams plan which costs $4 per month while the Business Plan costs $6 per month. Both feature a 14-day free trial.
Like most online security services, LastPass works with an end-to-end encryption system. This means that all user information is always encrypted, right from the user’s device to the final destination. Also, LastPass protects users’ information from middlemen attacks by using TLS encryption in the transfer of data between the user and the software’s servers. LastPass ensures maximum privacy for users by utilizing the AES-256 encryption protocol. The password manager also employs PBKDF2, which turns the user’s master password into a key that unlocks the app’s encryption system.
11. Resilio Sync
Resilio Sync (BitTorrent Sync) is an app for file transfer and synchronization. The app is a product of Resilio Inc. Resilio Sync uses a modified version of the BitTorrent protocol to sync files between devices and is available for Windows, Mac, Linux, Android, iOS, Windows Phone, Amazon Kindle Fire, and BSD.
The app is used primarily for the automatic synchronization of files between users and devices. In addition to this, Resilio sync also provides a secure means of file transfer between users. With an end-to-end encryption security method, users and enterprises can synchronize files on various devices securely.
This app also allows users to access files and other data on several devices, anytime, anywhere. Another important feature of the app is that users are allowed to download only files that are needed into devices without having to download the whole folder. Also, files and folders are automatically synced across all devices once added to a single device.

Resilio also provides a fast and secure means of file sharing, taking the shortest path between devices in file transfer. Resilio also offers users an unlimited size boundary in the size of files that can be shared or synced. Other features of this app include camera backup, one-time send, and access permission management. The software, which is one of the best security apps for Android, can be used on any device, to control sensitive data, and do many other things.
Various versions of the app come in various sizes. For example, the Android version of the app has a download size of 24.4MB, while the windows version obtained from the Microsoft app has a download size of 11.99MB. Also, there are various versions of the app compatible with Windows 10 64-bit and 32-bit.
The app can be downloaded from the official site of the company. Alternatively, visit the Google Play Store, input the app and click on the install button. Once installed, register by inputting username and password and proceeding to synchronize files.

Resilio Sync is a fast, secure, and easy to use means of file transfer and synchronization. Files and folders can also be accessed on multiple devices using ResilioSync. Another strong point of this app is that the app is very reliable and allows the transfer of large files between devices, with no size restrictions. On the downside, there’s usually a lag time between when the file is dropped in a folder. Also, the app has a poor pricing structure.
ResilioSync does not have a free version. However, a free trial period exists for the various paid plans available for the software. There are three paid plans available to users, which are: basic, plus, and a premium version which is further divided into Home, Family, and Business plans. The Sync Family protects up to 5 family members; users will have to pay a one-time subscription fee of $99.99. The Sync Business plan on the other hand costs $30 per month while the Sync Home costs $59,99 for a one-time purchase and protects just one individual.
Resilio has a privacy statement that is built on the commitment of the company to respect the privacy rights of all who make use of the company’s services. As a result of this commitment, the company has established a policy statement on privacy.
12. Glasswire
Glasswire is a visual network management system that allows users to keep track of user’s network usage. Glasswire analyzes past and present activities of user’s networks and provides a visual graphical representation of this analysis. The results of this analysis, however, require a certain degree of technical knowledge for interpretation. This app gives the user more control over privacy and security, allowing the user to improve internet connection quality and protect the system from malware.
Glasswire allows users to see what is going on in the user’s network and allows any suspicious activity to be quickly detected by the user for immediate action. The app provides a monitoring system for users to keep track of online activities and detect any form of anomaly. Glasswire allows users to switch between various firewalls available for different locations.
This firewall control feature allows users to block programs or networks without affecting those that have been allowed interaction with the PC. This is achieved by an interaction of Glasswire with the pre-existing Windows firewall. Another feature of Glasswire is the alerts that are sent to the user in the case of any suspicious activity such as new/unknown devices added to the user’s network, device removal from a user’s network, or connection of a user’s app to a harmful host.
Glasswire provides a beautiful graphical representation of the user’s network activity, which attracts the user to look at and be informed of network activities. There are a host of other glamorous features boasted by this app that provides users with maximum security.

The Glasswire firewall has a download size of 55.8MB and is compatible with the Windows operating system. The app is also supported on Android devices.
Glasswire can be downloaded from the official website of the software. The app can also be downloaded from various app stores and third-party sites. To download Glasswire, begin by visiting the official website of the software and thereafter click the download button to download the app. Once downloaded, double-click on the app to begin the installation process. After this, click on “next” and follow the prompts to install the software.
Glasswire software has an easy-to-use interface which makes the platform easy for users to navigate the app. This software has numerous channels such as email, community forum, Android help, and so on, through which users can get customer support, resolving issues easily for the user. Users are notified of any suspicious activity in the users’ networks.

The app also has an incognito mode that the user can switch on when accessing a site the user does not want the app to log. The app allows users to block all network connectivity while the user is away. Furthermore, the app is very user-friendly and allows for easy control of Windows firewalls. One major downside of this software is the fact that users require a degree of technicality, which the average user does not possess, to interpret the graphical representation of network activities. Further, the app does not possess an auto-update feature and is expensive.
Glasswire has a 7-day free trial period for users to try out all premium features. Users can continue with the free version of the app at the end of the 7-day free trial. However, this free package can be used only on one PC and does not possess the essential security features that can be found in higher-paid plans. That said, the paid packages for the software are Basic which goes for $29, Pro which costs $50, and Glasswire elite which costs $75. These paid packages have different capacities of users allowed and features contained in them.
The Glasswire company values the privacy of users, and as such, the software does not send any personal information to the software’s servers. Users can also request that certain data be deleted or request for available information by contacting Glasswire.
How Important is Cybersecurity in Android devices?

Cybersecurity is of utmost importance on all mobile devices, including Android devices. Android devices, like most other mobile devices, are a delicate piece of technology that not only require physical protection but cyber security protection as well.
According to experts, Android devices are more susceptible to security flaws and are more targeted by hackers than other devices. This is because the operating system of Android caters to lots of mobile devices and because of its global popularity, Android devices are more at risk of viruses, malware, adware, and other malicious attacks.
Android devices are also susceptible to many vulnerabilities including binary protection, insufficient transport layer protection, insufficient authentication and authorization, improper certificate validation (cryptography), brute force attacks, insufficient session expiration, and information leakage.
Owing to all these vulnerabilities and since most users store sensitive information on Android devices, maintaining the security of the stored data becomes a necessity to avoid damage, theft, or leaks. By securing Android phones, all categories of data are protected from damage and theft. These data include personally identifiable information (PII), sensitive data, personal information such as photos, phone numbers, videos, and so on.

Others include protected health information (PHI), intellectual property, industry, and governmental information systems, and more. Also, securing mobiles phones protects users against malvertising, guards against constant mobile patching services, and prevents mobile devices from being vulnerable to malware. Mobile security also automatically deletes and removes sensitive information when a phone is lost or stolen.
What Information and Data Do You Need to Secure on Android devices?
The most sensitive information and data need to be kept safe and secure on Android devices. This information includes passwords, private information such as home address, social security numbers, and bank account numbers. Other data to protect include health information, PINs, and credit card numbers.
What are the common Cyber Attacks on Android Devices?

Android devices are faced with a lot of cyber-attacks. Ransomware is one of the most common types of cyberattacks on Android devices. According to a report by VirusTotal on “Ransomware in a Global Context”, more than 130 various strains of ransomware have been detected since 2020.
Another common attack is Malware. Currently, there are more than 1 billion malware programs, this is significantly higher than the 3.2 million malware recorded by G DATA in 2018 and a further rise from the 2.3 million malware recorded in the year before. According to experts, in every minute, at least four companies are hit by a malware attack.
Other common cyber attacks include Denial-of-Service (DoS), DDoS, and phishing attacks, as well as SQL injection attacks. According to recent research, nearly 30,000 DoS attacks occur daily, while in the first quarter of 2021, up to 5.4 million DDoS attacks were recorded, representing an 11% increase compared with the same period in 2020. According to the FBI, phishing was the most common cybercrime recorded in 2020, with up to 241,324 incidents recorded in 2020 compared with the 114,702 incidents recorded in 2019. A new report shows that SQL injection accounts for approximately two-thirds (65.2%) of all web-based application attacks.
What Kind of Cybersecurity Apps Do You Need for Android?
There are many cybersecurity apps, with each having unique functionalities and capabilities. Some of the cybersecurity apps needed include:

- Antivirus: An antivirus is a software designed to scan, detect and destroy mobile antiviruses. While there are lots of antivirus apps available for download either free or paid, the best antivirus apps for Android will protect an Android device from the latest virus, spyware, malware, unsafe applications and settings, and other malicious threats.
- Password security apps: To enhance the security on Android devices, password security apps are also needed. These password security apps can store all the passwords of a client safely. The app also enables users to use unique and strong passwords for all vital accounts. These apps mostly use strong encryption including AES-256-bit encryption to protect users from the activities of cybercriminals.
- Security camera apps: No doubt, security cameras help to secure the home, office, properties, and loved ones. However, users can go a step further in downloading a security camera app on their Android device. This offers 24/7 monitoring and real-time updates, along with access to several features including motion detection and activity alerts.
- VPN: Virtual Private Network (VPN) enables users to create a secure network over the web. VPNs provide cyber safety, privacy, security, and anonymity. With a VPN, a user can access region-blocked sites, browse anonymously, torrent large files and use public wireless networks.
How can Cybersecurity Apps Help You Protect Your Android Device?
Cybersecurity apps are invaluable to Android devices. The best apps protect data and networks from unauthorized access, improve data security and business continuity, and boost the confidence of stakeholders in a company’s data security arrangement. Cybersecurity apps also prevent data breaches, cyber-attacks, and identity theft. Other functions and effects of cybersecurity apps include:

- Protecting personal data: Cybersecurity apps protect the privacy and integrity of data both in transit and during storage. Cybersecurity apps ensure personal data of users are not leaked or exposed and in the case of loss or theft, have measures that can be taken to prevent the personal information of users from being exposed.
- Preventing crashes: Often, device crashes as a result of malware or virus infestation. However, this can be prevented with a cybersecurity app. Cybersecurity apps guard against all types of malicious threats including viruses, malware, spyware, trojan attacks, and so on, thus preventing phone crashes.
- Preventing financial loss: Cybercriminals and hackers are always lurking around looking for vulnerable devices to attack. And when successful, these criminals can, amongst other things, steal a user’s money. This can be prevented with a cybersecurity app. Apps such as password managers and VPNs can prevent hackers from gaining access to a user’s device.

