Denial of service (DoS) attacks have become one of the most widespread cybersecurity dangers confronting modern businesses. The simplicity and efficiency with which a DoS attack may be orchestrated make denial of service an attractive method for cybercriminals or hacktivists. A DoS attack aims to render a website unavailable to users by flooding the target URL with more requests than the server can handle. During the attack, regular website traffic will be interrupted – either slowed down or altogether halted. A Distributed Denial of Service (DDoS) attack, on the other hand, is a DoS attack that originates from multiple sources simultaneously. A DDoS attack is launched utilizing thousands, even hundreds of thousands, of unwitting zombie PCs. In either attack, the goal is to blend in as much as possible, making mitigation efforts as inefficient as possible.
Being familiar with the different types of DoS and DDoS attacks that may occur is an essential component of internet security. This article explains these differences, as well as how users can prevent DoS and DDoS attacks.
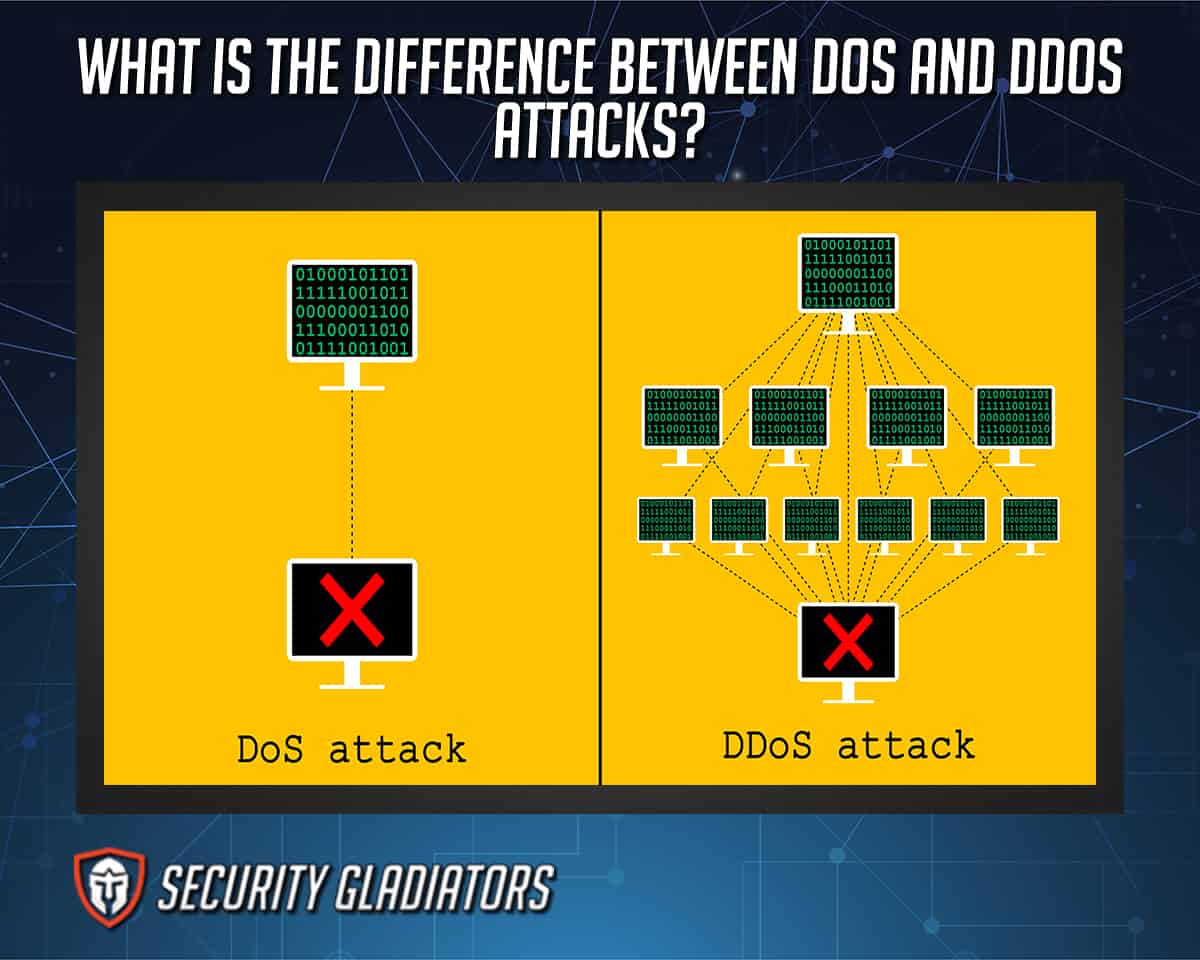
Table of Contents
What is a DoS Attack?

A denial of service (DoS) attack is a cyberattack that floods or overwhelms a server with TCP and UDP packets in an attempt to shut down a computer or network, rendering it unreachable to its intended users. A hacker attempting to disable a computer or other device from serving legitimate users, such as employees, members, or account holders, by interfering with usual operations is an example of a DoS attack. According to the DoS attack definition, a DoS attack is launched from a single computer but disables specific computers or even networks. A script or denial-of-service tools, such as Low-Orbit Ion Cannon and Slowloris, are used to launch a DoS attack.
Crashing exploits flaws in the target system or service, causing the target to crash. These attacks send inputs that exploit flaws in the target system, crashing or severely destabilizing the system to the point where the site cannot be accessed or used. The teardrop attack is a classic example of crashing.
DoS attacks do not often result in theft or loss of sensitive information but can be costly and extremely time-consuming to resolve. Targets are frequently high-profile web servers, such as banks, commerce, media companies, and government and trade organizations.
- The first documented attack similar to DoS happened in February 2020, when a 15-year-old Canadian hacker shut down the www sites of several e-commerce websites such as Amazon to legitimate traffic. Based on FBI reports, the cost of the attack on these sites amounted to about $1.7 billion.
- Reports claim that the internet suffers from distinct DoS attacks at an average rate of 28,700 per day.
- Three percent of websites ending in .org, .net, and .com are victims of daily DoS attacks because they are hosted on targeted IP addresses.
- Based on 2018 cybersecurity attacks statistics, 51% of businesses have experienced DoS attacks.
What is a DDoS Attack?

A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the target’s server or regular network traffic by flooding the infrastructure with internet traffic. According to the DDoS definition, a DDoS attack utilizes networks of internet-connected computers (usually compromised systems) as fake traffic sources to bring systems offline. This means that determining the source of a DDoS attack is difficult, complicating the recovery process. DDoS attacks are among the most prevalent and costly DoS attacks used today, confirmed by the following statistics.
- DDoS attacks are steadily rising, with the last quarter of 2020 registering a 0% increase from 2019.
- The longest reported DDoS attack, which happened during the first quarter of 2021, lasted more than 776 hours.
- DDoS attacks can cost $20,000 to $40,000 per hour.
DDOS attackers must first locate zombie hosts on the Internet, including some with backdoor vulnerabilities, before breaking into the system and installing control programs. In almost nine out of ten instances, the strategies used to launch DDoS assaults have been compromised, allowing the attacker to initiate strikes remotely via slave machines, otherwise referred to as zombies or bots. Computers and other networked resources, such as IoT devices can be exploited.
These bots link together to establish a network of connected devices called a botnet, which the attacker manages through a command-and-control server. The attacker or botmaster can direct an attack by sending remote commands to each bot after a botnet is established. Botnets can consist of only a few bots or hundreds of different bots. When a botnet targets a victim’s server or network, each bot sends requests to the target’s IP address, aiming to overload the server or network resulting in a DoS attack. Differentiating between attack traffic and normal internet traffic is complicated because each bot is a legitimate device.

The proliferation of IoT devices with lax security controls has resulted in a tremendous increase in the number of botnets, for example, the Mirai Botnet has been used in some of the most disruptive DDoS attacks. Attackers can even rent out the botnets to other criminals to fuel major DDoS attacks such as the one against Dyn in 2016, which paralyzed large areas of the internet. Similarly, to execute online attacks against computer systems, the Anonymous hacking group employed a free internet program called Low Orbit Ion Cannon (LOIC). As retaliation for the response against WikiLeaks, the group caused multi-million-pound damages to several companies, including PayPal and the Ministry of Sound.
Note:
DDOS attacks are most commonly directed at major websites, such as internet shopping sites, businesses providing online services, search engines, online casinos, and government institutions. The goal of a DDoS attack is to send many requests to the targeted web resource beyond the website’s capacity to handle multiple requests, thereby preventing the site from working properly.What are the Most Common Forms of DDoS Attacks?
Familiarity with the types of DDoS attack methods allows users to take steps to prevent them from happening on their own devices. Below are the most common DDoS attacks and the methods used.
- Ping of Death
A Ping of Death (POD) involves sending fake packets to ‘ping’ every machine on the target network. POD attacks deliver packets to the network that contain IP packets that exceed the maximum packet length. These unauthorized packets are transmitted in fragments. Access to genuine traffic becomes restricted once the victim’s network resources are depleted by reassembling the packets, bringing the target network to a total halt, and disabling the network altogether.
- UDP Floods
A User datagram Protocol (UDP) flood is an attack in which the victim’s network is flooded with UDP packets. The attack operates by flooding ports on a remote computer, causing the host to constantly search for a listening application. When the host detects the absence of an application, a packet stating that the destination could not be reached will be the response. The network resources are drained, preventing other devices from properly connecting.
- ICMP (Ping) Flood
An Internet Control Message Protocol (ICMP) flood attack, also known as a Ping flood, disrupts a network’s service by sending ICMP Echo requests or ping packets to the device. The attacker rapidly sends these packets without waiting for a response in an attempt to disable the target network via brute force. These attacks are high risk as they waste a lot of bandwidth in both directions, as attacked servers attempt to respond with their own ICMP Echo Reply packets. As a result, the network’s overall speed decreases.
- HTTP Flood
A hypertext Transfer Protocol (HTTP) Flood attack launches an assault on an individual web server or application by utilizing HTTP GET or POST requests. HTTP flood attacks are Layer 7 attacks that do not make use of faulty or faked packets. Attackers use HTTP Floods because they use relatively less bandwidth to disable the victim’s network relative to other attacks.
Zero-day attacks are those that use newly identified vulnerabilities to develop future attacks. Zero-day Attacks is a catch-all term for potential attacks. These attacks can be particularly damaging because the victim cannot anticipate an attack before encountering one.
- SYN Flood
SYN (synchronize) flood attacks send connection requests to a server without completing the transaction. As a result, the network becomes overburdened with connection requests, making access impossible for all users. SYN Flood attacks are another form of DoS attack in which the attacker manipulates the TCP (Transmission Control Protocol) connection sequence to disable the victim’s network. The attacker initiates SYN queries against the victim’s network, which answers with an SYN-ACK (synchronize-acknowledge) response. The sender is then expected to acknowledge, but the attacker fails to do so (or uses a spoofed source IP address to send SYN requests instead). Each unanswered request consumes network resources to the point where no device can connect.
What are the Types of DoS and DDoS Attacks?

Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks can take on various forms and be employed for various purposes. These could cause a firm to suffer a loss of revenue, cripple a competitor, divert attention away from other attacks, or cause difficulty or make a statement. The following are several prevalent forms that DoS and DDoS attacks take.
- Application-Layer Flood
Application Layer Attacks or Layer 7 Attacks are attempts to consume resources by establishing as many processes and transactions as possible. This includes GET/POST floods, low-and-slow attacks, attacks that target Apache, Windows, or OpenBSD vulnerabilities, amongst others.
These attacks do not require many devices to launch and are extremely challenging to identify and address. The objective of these attacks is to deplete the target’s resources and cause a DoS attack.
Application-Layer attacks are directed at the layer that generates and delivers web pages in response to HTTP requests on the server. While a single HTTP request is computationally inexpensive to execute on the client-side, it can be costly to respond to on the target server. The server frequently loads many files and does database queries to build a web page. Layer 7 assaults are notoriously difficult to protect against, as malicious traffic is often difficult to distinguish from genuine communication.
- Volumetric Attack
Volumetric or Volume-Based Attacks are any type of attack in which an attacker consumes a target network’s bandwidth resources and causes congestion between the target and the wider internet. . This includes ICMP floods, UDP floods, and other spoofed-packet floods. Once a network’s bandwidth has been utilized, the network becomes unavailable to legitimate devices and users.
For instance, an attacker might employ a botnet to flood a network with request packets, clogging the bandwidth with internet Control Message Protocol (ICMP) echo requests. As a result, services are slowed or ceased entirely. Volumetric assaults are initiated when an attacker floods network devices with ICMP echo queries until there is no more accessible bandwidth. Magnitude is usually measured in bits per second (Bps).
- Protocol Attack
Protocol attacks, also known as state-exhaustion attacks, disrupt service by consuming excessive server resources or network equipment resources such as firewalls and load balancers. This is achieved by using flaws in the OSI model’s Layers 3 and 4 to render the target unreachable. For instance, the attacker might exploit the TCP connection sequence by issuing requests but failing to get responses or responding with another request from a fake source IP address. Unanswered queries deplete the network’s resources to the point that the site becomes inaccessible. Protocol attacks include fragmented packet attacks, SYN floods, Ping of Death attacks, and many more.
DoS vs. DDoS: What’s the Difference?
The fundamental difference between DoS and DDoS attacks is that DDoS uses many internet connections to disrupt the victim’s computer network, while DoS uses a single connection. DDoS attacks are more difficult to detect because attacks originate from multiple locations, rendering the victim unable to determine the origin. DDoS attacks are also launched via botnets or networks of attacker-controlled computers. By contrast, DoS attacks are frequently initiated by a script or a DoS tool. Another critical distinction is the scale of the attack, as DDoS attacks allow the attacker to flood the entire network with traffic they are disruptive on a much larger scale. Detailed below are other differences between DoS and DDoS attacks.
1. Traffic Volume
DDoS attacks make use of several remote machines called zombies or bots. These remote machines allow a significantly larger amount of traffic to be sent from multiple locations simultaneously, rapidly overwhelming a server in an undetectable manner. DoS has considerably less volume of traffic but is still able to overwhelm an unprotected system.
2. Manner of Execution
DoS attacks are carried out from a single system through a script or DoS tool, while DDoS attacks are coordinated from numerous hosts infected with malware (bots). Botnets controlled by the attacker execute DDoS attacks. A bot-master forms a botnet that controls the network by a command-and-control (C&C) server.
3. Tracing of Source
Tracing the source of a DDOS attack is significantly more challenging than tracing a DoS attack. The botnet makes the task near impossible due to the varying locations of the attack source. DoS attacks are easy to trace as only one system is used.
4. Ease of Detection
Identifying and terminating the connection of a DoS attack is relatively easy. A competent firewall may be enough to mitigate an attack. However, the concealed source of a DDoS attack makes detection and mitigation difficult, if not impossible.
5. Speed of Attack
As DoS attacks originate from a single location they are slower than DDoS attacks which come from numerous sites. The increased DDoS assault speed also makes detection complicated and the resultant damage more severe.
Comparison Table of the DoS and the DDoS
| Denial of services (DoS) | Distributed Denial Of Services (DDoS) | |
|---|---|---|
| The attack is facilitated by | Single System | Multiple Systems (bots are used to attack at the same time) |
| Data packet sent from | Single location | Multiple locations |
| Speed of attack | Comparatively slow | Faster than DoS |
| Volume of traffic | Comparatively less than DDoS | A massive amount of data is sent |
| Level of threat | Low Rarely used to cover a breach attempt | Medium to high. Sometimes used to cause serious damage to networks or systems. |
| Malware | No malware involved | Malware on thousands of infected PCs, known as the botnet |
| Detection | Can be easily detected by identifying the IP address of the attacker | Difficult to detect due to multiple attackers at the same time |
| Victim action | Can stop an attack with proper security | Difficult to prevent |
Is DoS Worse than DDoS?
No, DDoS is more complex and usually worse than DoS attacks, as the former is launched from multiple computers. A DDoS assault uses numerous systems to coordinate denial-of-service against a single target. When one computer attack is compared to one hundred (or more) devices in a botnet attack, it makes logical sense that the overall severity of the attack is increased. DDoS attacks are very difficult to prevent as many attacking systems are randomly distributed to different locations (often worldwide) and the primary attacker is concealed through several compromised systems.How to Improve DoS and DDoS Attack Protection

DoS and DDoS attacks are a constant threat to modern businesses. Thankfully, steps can be taken to both prevent attacks and protect systems that have already been attacked. Before implementing a defense strategy, it should be accepted that not all attacks can be stopped though. The goal of the strategies listed below is to prevent attacks and minimize the damage from successful attacks.
- Network Monitoring
Network monitoring acts as a deterrent and helps companies detect attacks before systems are taken offline. Constant network monitoring is an excellent preventive and preemptive measure intended to help identify normal traffic patterns and help detect and mitigate threats early. Most attackers will test a network with a few packets before launching a full attack. Monitoring network traffic will detect minor signs early, help keep the service online, and avoid unexpected downtime costs.
Action can be taken immediately after noticing unusual data traffic or an unknown IP address by monitoring traffic. An additional precaution would be to filter unwanted traffic by activity profiling and ingress/egress filtering.
- Simulate Attacks
To defend against every attack is virtually impossible, but users can be prepared in the event of an attack. Simulating DDoS attacks is one of the most direct ways to accomplish this. Simulating an attack enables the evaluation of current prevention methods and the development of real-time prevention strategies that can save a lot of money in an actual attack. Running tests to simulate attacks will help assess risk levels, expose network vulnerabilities, and train employees for cybersecurity needs. Testing DoS attacks allows the refinement of an overall strategy.
- Develop a Response and Protection Plan
The crucial first step toward developing a holistic defense strategy is to create an event response plan. A DDoS response strategy, depending on the infrastructure, might become extremely thorough. However, a clear plan can make the difference between a minor inconvenience and a major disaster. Ascertain that the data center is prepared and that all members of staff are aware of their duties.
As part of a protection plan, create checklists, assign roles to response team members in case of an attack and specify response parameters. Security measures must also be put in place; this includes creating customer support procedures, so customers are not left hanging while technical issues are being dealt with.
- Identify critical systems
Security requires a strong focus on secure network architecture. Businesses should provide redundant network resources; in the event of an assault on one server, the remaining servers can handle the increased network traffic. When possible, business servers should be geographically dispersed. Resources that are scattered are more difficult for attackers to target. Knowing critical systems helps in planning for protection.
- Leverage the cloud
Outsourcing DDoS mitigation to cloud-based service providers has several benefits. The cloud likely has significantly more bandwidth and resources than a private network. Although extra bandwidth availability will not stop an attack, the network will handle traffic spikes and lessen the impact. With the rising size of DDoS attacks, depending exclusively on on-premises hardware is a recipe for failure. Second, the nature of cloud applications means dangerous or destructive traffic can be filtered out before reaching the intended destination. Thirdly, software engineers manage cloud-based services whose primary responsibility is to watch the Web for new DDoS strategies.
What are the Best Tools for DoS and DDoS Attack Protection?
Entities have little control over the traffic that enters a website making complete protection against DoS and DDoS attacks impossible. However, listed below are some tools which provide a degree of protection against DoS and DDoS attacks. Included in this list is the best tool against DDoS and DoS attack.

- Akamai Prolexic Routed – DDoS attacks such as UDP floods, SYN floods, HTTP GET, and POST floods are all blocked.
- AWS Shield – Real-time traffic analysis is performed via flow monitoring, packet filtering, and traffic prioritization.
- Cloudflare – Network capacity can withstand some of the largest attacks in existence. This tool manages a broad range of attack types via an IP reputation database.
- Indusface AppTrana – A web application firewall with vulnerability screening, DDoS prevention, and anti-bot detection capabilities. Additionally, this package of edge services includes a content delivery network.
- Link11 – Cloud-based security service is capable of detecting and mitigating assaults. It is simple to set up, utilizes AI and provides a clear view of server behavior via the dashboard.
- Sectigo Web Firewall – Web firewall protects websites and web applications from cyber threats and harmful traffic, such as cybercriminals, malicious bots, DoS, and DDoS attacks, without disrupting the user experience.
- SolarWinds Security Event Manager – A robust program capable of detecting and monitoring a wide variety of network events, including DDoS attacks. Maintains logs of attacker IP addresses and even blocks the attackers.
- Sucuri Web Application Firewall – This WAF inspects and stops all incoming HTTP/HTTPS traffic. Geo-blocking capabilities are enhanced.
- StackPath Web Application Firewall – Detects and blocks threats using behavioral algorithms and has user-configurable DDoS protection thresholds.

