Table of Contents
Summary
Users who want to live in a truly anonymous online world should know that the Tor network provides them with everything they need to realize that desire.
In many ways, using the Tor network to access the internet is like using a VPN service to protect one’s privacy and security online.
Of course, VPN services and the Tor network have some core differences in terms of the technologies that they use to protect online users.
But the fact remains that both of them are very practical in the way they go about protecting users.
For more details head over to the full review below.
Tor Full Review
What is Tor?
Before we define what exactly is Tor, the first thing readers need to know is that Tor provides users from all over the world with an extremely high level of anonymity and security.
Such a high level of security and anonymity come at a cost.
That cost is the lack of day-to-day user-friendliness of the internet.
Now, let’s compare Tor with a VPN service to differentiate the two and enable users to understand how a Tor network is not the same as using a VPN service.
With a VPN service, users do get to enjoy a lot of security and privacy.
But no one in their right mind should consider any VPN service as truly anonymous.
Why?
Because regardless of how good a VPN service is at its job, the user still has to trust the VPN service to not misuse his/her information.
After all, the VPN service always knows the user’s real IP address.
Since a VPN service doesn’t provide as much security and anonymity, it makes up for it by offering a much convenient and seamless day-to-day online experience.
Because of such a situation, most feel that a VPN service (when compared to the Tor network) is the more flexible and general-purpose online privacy tool.
What about Tor then?
Why would someone want to use Tor?
In contrast to a VPN service, Tor is not a general purpose tool.
It can just be a toy for some and absolutely vital for others.
Our research shows that only a tiny subset of all online consumers would genuinely require the services that a Tor network offers.
And what does the Tor network offer?
It offers the maximum amount of anonymity that is possible via existing online tools.
The other great thing about Tor is that it is free.
But apart from being free, it can also perform as a very effective anti-censorship online tool.
That is the reason why a lot of repressive governments around the world have started to take strict measures against the Tor network by blocking any type of access to the highly anonymous network.
Of course, it is another matter that they haven’t been able to achieve the kind of success that they hoped for.
Who Funds Tor?
Now, we have already mentioned the fact that Tor is open source.
It is also free.
That doesn’t mean it does not need any money.
In fact, there are many forums and platforms where it has provided users the facility of donating money to the Tor network.
Some may consider it a rather unfortunate and peculiar twist of fate, the United States Naval Research Laboratory funded and developed the Tor Project back in the 90s.
Why did it do that?
It did that in order to help out people who, at the time, lived under oppressive regimes.
The Tor network allowed them to easily bypass all the censorship measures that hindered their right to exercise free (and fair) speech.
It is also true that in that respect, the United States government still continues to fund the project in substantial ways.
But the curious part about the whole situation doesn’t end there.
It turns out, the United States government has also spent and still routinely spends a sizeable amount of resources, time and money in trying its best to compromise the very secure and anonymous Tor network.
Now don’t let this bizarre set of circumstances lead you away from the fact that Tor is still completely and comprehensively independent and also open source.
In fact, we don’t think there is a service out there whose source code has gone through so many regular and thorough audits.
Of course, all the audits in the world are sometimes not enough for a certain class of people.
And Tor is particularly sensitive to any kind of criticism.
To satisfy such sections of the community, Tor has started to make substantial efforts in order to not only widen its sources of funding but also increase the overall amount of funding.
Users who want to see the complete list of Tor sponsors should go ahead and click here.
How does Tor work?
Originally, the term Tor came into existence as an acronym.
Acronym of what?
It represented the acronym of The Onion Router.
Some believe it refers to the method using which it layers its data encryption implementation.
Let’s list out some of the ways Tor protects users and how does it actually do it.
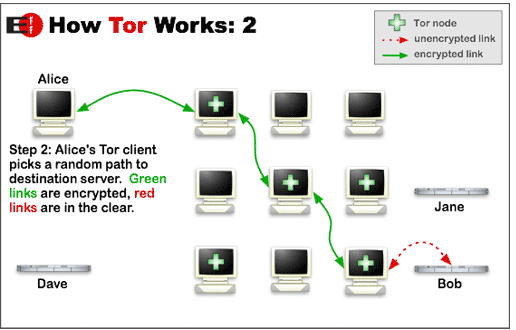
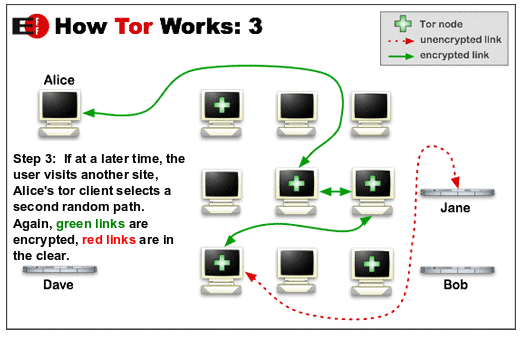
- When a user is utilizing Tor, his/her internet connection is actually routed directly through 3 or more random nodes.
What are nodes?
Nodes are servers that volunteers all across the globe run. - Needless to say, these nodes could have any country on earth as their location.
- With a Tor network, the user’s data has no choice but to go through a multiple number of encryption procedures.
In other words, the Tor network re-encrypts user data a multiple number of times.
More precisely, the user’s data goes through the encryption process each and every time it passes through a given node. - A given individual node only has the awareness of that IP address that is in front of it.
The only other IP address a given individual node knows of is the IP address of the node that is behind the current node. - All of that ensures that within the Tor network there is not a single given point at which any single entity knows the entire given path between the user’s computer machine and the actual website that the user is trying to form a connection with.
With that said, it is also true that sometimes malicious entities get a hold of these nodes and the user’s data may pass through these nodes.
The best thing about using the Tor network nowadays is that the user is free to trust no one.
Originally, researchers designed the Tor network so that not a single entity would have the option of discovering the user’s true identity.
In simpler terms, if the user connects to a very secure website via the Tor network, no one has the ability to have a look at that and spy on the user’s data.
The Tor network relies on the efficiency of relay circuits to perform its duties.
Moreover, the structure of the network is such that, after every 10 minutes (more or less) a random relay circuit gets reset.
This ensures that the user is safe and his/her actions don’t leave a trail behind.
In other words, when the Tor relay circuits are performing well, no one can trace and link a certain action of a given user to the same user’s earlier online actions.
As mentioned before as well, a volunteer runs each given node in a given Tor network.
For the end user that means the more the number of volunteers that are present on the network, the more is the chance that the entire Tor network is safe and secure.
Now, it stands to reason that the chain of nodes in the Tor network would end somewhere.
In this context, the very last node that is present in a given chain of nodes is called the exit node.
This is the node that actually connects the user’s message to the wider world of the internet.
By default, the data passing through the Tor network enters and leaves the Tor network via the exit doe in an encrypted state.
In other words, an operator on the exit node can actually see the data.
Does that cause a problem?
Maybe.
We’ll discuss the security implications of having an exit node in a Tor network in a later section of this review.
What readers need to really understand is that, volunteers who are running exit nodes are actually providing a great service to the overall Tor community.
Moreover, they are not just providing people with a service but are striking meaningful and significant blows to those who want to suppress internet freedom and have oppressive censorship policies.
The other great thing about the Tor network and running an exit node is that, it is fairly easy to set up.
With that said, it is also true that the person running the exit node has the opportunity to take a look at other Tor user’s online activity.
Moreover, if the exit node operator is involving himself/herself in a highly illegal online activity, then that activity would appear to directly originate from the exit node operator’s IP address.
You don’t need us to tell you that would lead to problems.
What we mean to say is that using the Tor network comes with a very particular set of risks.
To learn more about these risks and how to minimize them, click here.
Anti-censorship and Tor
The Tor network is a special network because it randomly re-routes the user’s connection in order to make sure that it outputs via an exit node that is located far away from the user’s original location.
The only that the Tor network has to make sure is to make sure that the exit node is located in a country where there are no or little censorship measures.
This is fairly easy for the Tor network to do because most of the exit nodes come from “free” countries.
As long as the Tor network can ensure that, the user has the option of experiencing the internet without any censorship.
One of the core design features of the Tor network is its ability to evade any and all censorship.
Users have to keep in mind when they evade the highest levels of censorships measures they also get rid of less effective censorship measures like work and school firewalls.
Of course, governments and other organizations aren’t really stupid.
If they are really serious about blocking something on the internet then they have ways of doing that.
The most favorite of their measures is to simply block access to the official Tor network.
Yes.
They can do that.
We’ll talk more about what users can do to combat that in a bit.
Some Issues
The Tor network is slow
As mentioned before, security is the key design feature behind Tor.
However, that comes at a huge cost of reduced speed.
That may not be a problem for everyone.
But for people who want to use Tor to stream video content, a loss in speed is pretty devastating.
When users are taking advantage of the anonymity that the Tor network provides them, they are actually giving a green light to the Tor network to pass their data through more than three randomly chosen nodes.
As mentioned before, these nodes can exist in any part of the world.
Moreover, the Tor network resets these nodes after every ten or so minutes.
Every time data passes through a node, the node re-encrypts the data.
This, as some may imagine, requires quite a bit of processing power on part of the node.
As a consequence of that, the Tor network becomes slow.
We’ll talk more about the Tor network and speed in a later section of this review.
Users who have enough luck to subscribe to a really fast internet connection (broadband internet, in other words), may not actually notice any slowdown while using Tor at first.
But as soon as they start to move away from surfing the online world and try to engage in activities such as streaming HD video content and torrent downloads, they will feel the buffering issues.
Slowness in a given Tor network is an impossibly difficult problem to solve.
The other problem is that a lot of the countries where users would benefit the most from services such as the Tor network, tend to NOT have a speedy internet infrastructure.
That further slows down the Tor network.
Should you use Tor to download torrents? Or for P2P?
No.
Why?
Because the Tor network is already slow.
Trying to torrent on such a network will be even slower.
However, there are more reasons for refraining from downloading torrents via the Tor network.
One is the social nature of the Tor network.
If a user tries to download torrents via the Tor network it doesn’t just slow down the connection speed for that user.
It slows down the Tor network for everybody.
That may not sound like a big deal to a lot of Tor users but consider this:
Somewhere in the world, someone is trying to use the Tor network to get some important information across the border.
If the network does not work fast enough, that someone might go to jail or die.
Yes.
We are talking about reporters who cover human rights violations across the globe.
Then there is the fact that people in less developed parts of the region already have a basic internet connection.
If they use Tor on top of it, it makes things even slower.
And when a first world user torrents over the same network, it makes life hell for users in the developing world on the same Tor network.
The other thing that users should keep in mind that when they download copyrighted material from the internet via the Tor network, the exit node operator (a volunteer) may have to deal with authorities tracing his/her IP address and asking him/her questions.
Because of these reasons, many consider torrenting over the Tor network as a bad behavior.
We’ll have to be honest here and say that this point also applies to users who try to stream video content via the Tor network.
Blocked Tor exit nodes
As mentioned earlier as well, the complete list of Tor relays (or nodes) which are public is listed here.
For those wondering why does the Tor project list the IP addresses of exit nodes, click here.
One of the “benefits” of publicly sharing Tor exit nodes is that it makes it relatively easy for various streaming services and websites to block each and every user who comes via the Tor network.
Of course, generally speaking, that isn’t such a big problem for the majority of online users.
It is only a problem for those who try to bypass geo-restrictions and access services they are not supposed to.
Such services are guaranteed to have blocked Tor exit nodes, so don’t even try.
Even services such as CloudFlare have recently started to take a prominently aggressive approach towards handling online Tor users.
That is significant.
Why?
Because a big chunk of all the websites in the world is actually using CloudFlare hosting services.
For Tor users, this means that they will have to go through some more CAPTCHA challenges and perhaps even lack of access.
Websites and streaming services may employ other security measures to keep Tor users at bay as well.
Tor censorship
Some restrictive countries that make use of reasonably advanced censorship tools and geo-restriction systems like Iran and China usually make comprehensive attempts to block any and all access of their citizens to the official Tor network.
One of the techniques that they make use of a lot of times is the DPI or Deep Packet Inspection.
Using this technique they are able to identify various types of user Tor traffic.
In a lot of the cases that we have come across, users can usually counter techniques such as Deep Packet Inspection by making use of obfsproxy, which is a PT tool (PT stands for pluggable transport).
This tool does a terrific job of wrapping up data and making it more secure.
More specifically, it wraps up data with a special obfuscation layer.
In turn, it makes it look like the user’s hidden traffic is actually normal traffic.
Without the use of an obfsproxy, an observer would be able to see that the user has Tor traffic and that may make the observer suspicious.
Privacy and Security
No one needs more convincing that the Tor network is a very secure system precisely because it makes use of a very complex and strong encryption system.
Let’s make a list of key and simplified points that make Tor such a secure network.
In terms of the cipher used, the Tor network makes use of AES-128 technology.
For data authentication, it makes use of HMAC SHA 256-bit.
As for the handshake technology, Tor uses the Curve25519 ECDH.
The Tor network does offer perfect forward secrecy.
For control authentication, it makes use of SHA 256-bit.
At its core however, the Tor network employs the pretty good TLS 1.2 cryptographic protocol.
About six or seven months ago, Tor finally addressed some of the most serious security concerns that its critics raised over the network’s use of 1024-bit RSA handshake technology by simply taking the initiative to implement a highly secure Curve25519 DH, an elliptic curve exchange.
Of course, that doesn’t really take care of some of the older Tor nodes that may not move to the new implementation and may stick to the old RSA 1024-bit handshake.
With that said, readers should note that even with that fault, the Tor network still utilizes Perfect Forward Secrecy which enables the Tor network to generate new keys for each given new exchange.
This may sound trivial.
But our research shows it is vital in seriously hampering any and all adversary’s attempts to first compromise and then damage communications.
With Perfect Forward Secrecy a hacker would have to come up with a way to crack each new key that generates each and every time Tor forms a new connection.
The Tor network protects the user’s data with the help of AES 128-bit.
It is true that the majority of the security industry has moved on to the later and more secure AES 256-bit.
But AES-128 is still very secure.
And no one has been able to crack it.
If we are talking about facts then the AES 128-bit, when compared to AES 256-bit, has a much more robust key schedule.
Readers should also remember the fact that the Tor network encrypts and re-encrypts the user’s traffic data a multiple number of times.
This provides the user the opportunity to benefit from several layers of protection.
That certain section of our readers who likes to read detailed stuff about the encryption that the Tor network uses and all the relevant analysis, should go ahead and click on this link to read a paper that Tor published a while back.
There is also this paper (which we think is an excellent piece of writing) that comes to you via some independent analysts.
Readers who are not familiar with all the encryption terms that we have used here so far should definitely search for each term using their favorite search engine.
Tor vulnerabilities
Perhaps Bruce Schneier said the truth when we mentioned that as long as Tor acted as a magnet for all of the internet’s “interesting” traffic, Tor would also act as a magnet for all those who have the desire to eavesdrop on that interesting traffic.
By the look of things, almost all organizations and individuals from President Putin to the NSA and many other white hat hackers, want to have a piece of the action.
They have shown great determination to try and compromise the official Tor network.
It doesn’t take a genius to figure out that they also want to de-anonymize any and all Tor users.
To be fair to them, government agencies have seen some form of success in doing that.
However, the prevalent opinion among the majority of the security experts is the same:
Tor is still fundamentally safe and secure.
In fact, online users are more likely to get themselves into trouble on their own by their careless behavior or incorrect use of the Tor network than the Tor network itself.
In short, the Tor network has no major flaw in its design.
Of course, achieving complete anonymity is anything but a difficult process.
Moreover, no one can guarantee that the Tor network will provide that each and every time the user connects to the internet through it.
On the other hand, Tor is a system that is built on security and safety.
It has proven time and time again that it has great resilience when it comes to offering protection against even the most well-funded and sophisticated attacks.
A while ago Edward Snowden released some documents in which the NSA actually admitted that they encountered major problems in the agency’s attempts to successfully decrypt online messages that users sent to their contacts via Zoho, an email service provider that makes heavy use of encryption for its user messages.
The NSA also encountered a ton of problems in launching its monitoring programs to target Tor users.
What readers need to understand here is that Tor is not perfect.
However, neither is anything else.
As far as the real world is concerned, there is nothing that gets even close to Tor when we’re talking about protecting the user’s online anonymity.
And you can only beat the competition that you have.
Tor has done that.
No one can say for certain what type of abilities the likes of the NSA have gained recently.
But we have researched and found out the two most common and most misunderstood online threats to users of the Tor network around the world.
Malicious Tor exit nodes
We have already mentioned the fact that all internet traffic first enters a Tor node and then leaves a given Tor exit node with no encryption.
What that means for Tor users is that anyone who is running that exit or entry node can monitor the traffic.
The problem here is that there are no rules and regulations regarding who can become a volunteer to operate a Tor exit node.
No one needs any convincing why that can cause major online security issues.
Now, we want readers to bear some important points about the Tor network in mind before proceeding.
These are as follows,
- The Tor network makes use of a random chain of nodes through which the user’s data goes through.
Moreover, the user’s data goes through the user’s machine and the Tor exit node.
The operator or the owner of a given Tor exit node does not have the ability to directly have any knowledge about who the user is. - With that said, it is true that the Tor user may inadvertently give away his/her real identity either indirectly or directly via his/her communications and/or online behavior.
- Additionally, malicious Tor exit nodes can snoop on the user’s data.
They can also launch those pesky MiTMs, or Man in The Middle cyber attacks.
Most of the time, these attacks take the user to a dummy page instead of the user’s requested webpage.
Now, the feel-good points that readers need to keep in mind are,
- As long as the Tor user has connected to a given website with a secure and safe SSL encryption certificate (in other words, HTTPS:// websites instead of HTTP://), the user’s data and identity stay safe.
No malicious Tor exit node on earth can intercept any data if the Tor user sticks to this simple tip. - Following from the previous tip, Tor users are also pretty much immune to cyber attacks such as Man in the Middle.
Some of our more discerning readers may have noticed that the internet is filling up with more and more SSL secured services and websites.
In other words, they are becoming the norm.
Why?
Because everyone wants to live in peace and security.
But we should also thank the Let’s Encrypt online campaign from EFF.
As mentioned just now, if the user can make sure that he/she doesn’t connect to a website that isn’t HTTPS, his/her data is safe.
However, if the user ignores this tip and connects to websites which don’t use encryption, they need to be extra careful about the type of information that they divulge to that site.
Our general recommendation is for users to not give sensitive information away even on websites that do have HTTPS.
Recent research has shown that about 2.5 percent of exit nodes on the Tor network are actually malicious exit nodes.
In other words, 97.5 percent of all exit nodes are perfectly fine and no malicious actor is operating them.
Now, the figures as with the “good” exit nodes.
But some has suspected the NSA or operating and running several spoiled onion nodes, as they are called.
The rest of the 2.5 percent of bad Tor exit nodes appear to belong to pretty thieves and criminals.
Timing attack in end-to-end systems
About five years ago, a student at Harvard made the big mistake of making bomb threats to his entire campus.
Why did he do it?
Well, he wanted to get himself out of giving the final exam that month.
Amusing, but ill-advised.
Law enforcement authorities caught him even though he had the brains to make the threat by first connecting to the Tor network.
How did the law enforcement agencies authorities get to him?
Well, the Harvard student made the classic mistake of connecting to the Harvard campus WiFi before connecting to Tor.
So, in essence, all that security agents at Harvard had to do was to simply double check all of their logs in order to find out which of Harvard students had connected to the internet via Tor at the time when those bomb threats surfaced.
After that, law enforcement agents had to question everyone who had used Tor at that time.
There is a good chance that Kim (the Harvard student) was actually the only Harvard student who had connected to the internet at that time of the day.
Now, the reason why we have told you this story is to identify which technique the law enforcement agents used to get to that Harvard student.
The de-anonymization technique that security officials used is generally known as E2E timing attack (E2E here stands for End-to-End).
If it helps anyone’s nerves, this is one vulnerability that is pretty well known in the Tor community.
Readers should note here that the only reason why law enforcement agencies had the chance of catching Kim in the first place was because Kim made a critical mistake of first connecting to the campus’ WiFi network and then connecting to the Tor network.
This isn’t something we think the average Tor user would do under normal circumstances.
Out in the open internet, any adversary would actually have to have control over a really high percentage of existing Tor nodes on the entire Tor network.
Only then can the adversary have any chance of launching a successful end-to-end online timing attack.
But why would the adversary need a high number of nodes?
Why can’t the adversary just control a few nodes and launch the attack?
Well, the adversary would have to fulfill the requirement of controlling a ridiculous number of nodes because a greater number of nodes would actually give the adversary a higher chance of correlating the precise timing of a given activity at a particular given Tor exit node with the target Tor user’s initial Tor network connection.
Even with that, the adversary would have to deal with another problem.
The high number of online Tor users at any given time.
For the adversary to have any success at this task, he/she would need a lot of resources, extensive knowledge and a prolonged session of statistical analysis to make the aforementioned correlation.
Now, readers may think that this task seems like an (effectively) impossible one.
But that’s not the right way to look at it.
No one can guarantee if some organization has the resources and the skills to pull this off.
What users need to keep in mind is that, organizations like Mossad, GCHQ, NSA and some mafias to tend to have an unlimited amount of resources to work with.
These organizations and groups also have a global reach in the truest sense of the world.
Hence, we can’t really put a limit on the things they can achieve and are capable of doing.
Theoretically speaking, if there existed such an adversary and he/she had the mental fortitude, resources and the skills to tackle huge problems, then he/she could actually utilize the E2E timing attack technique in order to de-anonymize a targeted Tor user.
Some hidden services with Tor
As alluded to before, researchers designed the Tor network in order to allow users to have an open access to the internet.
That’s its primary purpose.
Generally speaking, people love to spend time in an online world that is anonymous and uncensored.
Readers should have this clarity in their heads right now that even though some give the Tor network a lot of love, one can’t just ignore the Tor exit node.
This is the node that the user has to make use of in order to connect to the Tor network which in turn will connect to the wider world of the internet.
It is a weakness.
And a major one.
It brings the watertight safety reputation of the whole system into question.
There is nothing stopping malicious entities from controlling and monitoring Tor exit nodes for a multiple number of reasons.
Moreover, the Tor exit node is the one glaring security hole for any hackers who want to launch a time-based attack on a given Tor user or even the entire Tor network.
Something needs to be done to take the focus off the Tor exit node.
Well, guess what?
Tor has responded to this problem.
How?
By developing its very own Hidden Services protocol.
What do these hidden services do?
They enable websites which are tor-only (addresses that end with .onion at the end) and other services to actually exist within the official Tor network in their entirety.
As a result of that, Tor users don’t have any need to access their favorite websites via bad exit nodes.
It might be obvious to some, but with .onion websites, Tor users can skip all the potentially malicious Tor exit nodes from the beginning.
What these Tor hidden services also do is to enable the Tor network to act as an access point to the Dark Web.
The Tor network represents the most popular platform for accessing the Dark web by a country mile, at least in terms of the number of online users.
From a traditional standpoint, the dark web has gained a lot of notoriety for hosting,
- Gangsters
- Drug dealers
- Terrorists
- Pedophiles
- Other players who sell things and materials that the majority of right-minded online internet users would never have anything to do with.
Of course, that is changing.
With people like Edward Snowden doing their work properly, the awareness among people about pervasive government surveillance has definitely increased.
Moreover, other information regarding even more draconian measures to enforce copyright laws has fueled a really huge surge of interest from the public.
This has led to a certain section of online consumers to look for the off-grid internet.
Consequently, many more legitimate companies and organizations have now started to run various .onion (or Tor Hidden Services) websites.
In fact, now users can even access sites such as Facebook via its .onion address.
The address for Facebook onion version is https://facebookcorewwwi.onion/.
Of course, you can’t access it via a normal mainstream web browser.
To access sites via the .onion address, the user first has to connect to the Tor network.
There is little doubt that connecting to websites via the Tor network and Tor Hidden Services is a lot safer than just accessing the regular version of one’s favorite websites.
In short, there is only one way for users who want to access .onion websites on the dark web (Tor Hidden Services).
And that is via the Tor network.
VPN or Tor?
There is no definite answer to that question.
In terms of the general purpose of a given software application, a VPN is pretty similar to the Tor network.
Both work towards providing and then maintaining privacy and security to the user.
In fact, both Tor and VPNs help users to evade all sorts of censorship measures as well.
Similar to a VPN service, users can utilize the Tor network to spoof their geo-location.
That is easily achieved in fact.
All that the user has to do is to continually re-connect to a different Tor exit node until the Tor network re-connects to a Tor exit node that is located in his/her desired country.
This is more easy to do when the user wants to connect to a Tor exit node that is based in the United States of America.
It is a bit harder to pull off when one wants the Tor exit node to be present in a country or a region with less internet connectivity.
With that said, we would also like to mention that the underlying technology isn’t the only thing that is dissimilar between a VPN service and the Tor network.
Even the scenarios in which users take advantage of what both these services offer are reasonably different.
Let’s take a look at the advantages of using each service.
Advantages of Tor
- Offers access to the very secure .onion websites via Tor Hidden Services.
- Free
- The network is distributed which means hackers would find it impossible to shut it down or even attack it an effective manner.
- Users don’t need to trust anyone or anything.
- Very good at anonymizing users.
Disadvantages of Tor
- Users have the option of spoofing their location at a finger’s press.
However, Tor is very inefficient and fiddly when it comes to changing the location of the user.
Additionally, the Tor network is pretty slow.
Hence, users who are trying to bypass geo-restrictions just so they can stream content from various online media services are sure to be disappointed.
Tor isn’t a feasible option for that. - Tor is also not the best option for activities such as P2P file sharing either.
Of course, no one can stop the user from making use of BitTorrent clients over a Tor connection.
And to be honest, a lot of people do it.
But, that doesn’t change the fact that the Tor network is very slow.
Moreover, it is also considered bad behavior when a user slows down the whole of the Tor network just so that he/she can download a movie.
Remember, all Tor users suffer when one Tor user makes use of a BitTorrent client on the Tor network.
Again, someone may be trying to access the open internet for a very important or even critical reason.
In other words, someone’s life maybe on the line while a Tor user enjoys his/her next fix of a TV series episode. - Because the Tor network has to bounce around the user’s data directly through many number of Tor nodes, it becomes very slow.
Sometimes, these Tor nodes may have a location that is very far away from the user’s location.
If that happens, the Tor network becomes even slower.
It might come to a point where using Tor is more painful and living without an internet connection is more enjoyable.
Advantages of using a VPN service
- VPN services are fast.
Much faster than the average speed that the Tor network can provide to the user.
In the real world, VPN users will generally see no noticeable slowdown as far as their internet connection speed is concerned.
Naturally, all VPN services slow down a given internet connection.
But they do it to such a less extent, that the negative effect is almost negligible. - VPN services are great for users who want to spoof their location.
It is true that all good VPN service providers offer users plenty of VPN servers to change their location to any country that they want.
And because VPN connections have great speed, the service is ideal for users who only want to change their location because they want to stream content from a streaming site that uses geo-restrictions on its content. - The perfect solution for P2P file-sharing.
There are many VPN service providers who prohibit users from engaging in P2P file-sharing.
But since a lot of online consumers make use of these services, many have started to target users with this feature in mind.
Disadvantages of using a VPN service
- There is no question.
The biggest problem with using a VPN service is that the VPN service provider has all the opportunity in the world to see the user’s identity and his/her activities.
In fact, there are many countries in the world that make it mandatory upon VPN services to keep a record on their users.
Such VPN services are free to hand over all of their data to law enforcement authorities and even copyright lawyers.
The police can also raid VPN servers.
That is another VPN vulnerability.
Law enforcement agencies, like the police, sometimes raid VPN servers because they have an interest in the information that these VPN servers contain.
Hence it becomes vital for the user to sign up for that VPN service which does not keep any type of logs.
Users should make sure that the VPN has placed itself in a position where it can deliver on all its promises.
Of course, no one can guarantee if the VPN service provider will keep its word.
In the end, it is the user who has to trust the VPN service to actually keep its word and protect their data. - VPN services don’t come for free.
Even though, one can sign up for a good VPN service for as low as $3 month, it is still something.
On the other hand, users always have the option of buying VPN subscriptions in bulk and enjoying further discounts.
How to use VPN and Tor Together
Yes.
It is entirely possible for a user to use both VPN and Tor together in order to protect himself/herself in a more meaningful way.
A combination of VPN and Tor can bring many added security benefits.
This is a topic that needs an entire discussion.
We’ll come up with a guide on the best VPNs for Tor in the very near future.
For now, just know that not all VPN services support Tor.
Therefore, the user first has to know if the VPN in question provides the necessary configurations for proper working with Tor.
Tor website
The official Tor website called the Tor Project facilitates users with installation guides, FAQ sections, and extensive manuals.
There is even a Wiki page with further links to a ton of information contained in unofficial documents.
However, there are always times when a given Tor user may actually get stuck really bad.
For such users, the Tor network provides support via Twitter, IRC, and email.
As far as the presentation of the website goes, it is pretty well done.
But we have to give proper consideration to the fact that the volume of information and resources on the site would be enough to intimidate anyone.
We’re glad that the Tor Project has tried its best to make the information easy to access and sensibly organized.
How to Sign up for Tor?
There is no signup process for using the official Tor network.
The Tor network has a very specific design.
It provides users with the maximum anonymity that is possible with current technology.
The Tor Browser
This is the big one really.
The most secure and simplest method (also the most recommended way) is to use the Tor Browser to access the official Tor network.
Yes.
The old official Tor Bundle is gone.
It has been replaced with the Tor browser.
What is the Tor browser?
It is essentially Firefox.
More accurately, a special version of Firefox.
A version that is open source.
The Tor browser has the ability to route all of the user’s internet connection via the official Tor network.
This browser is also hardened to provide users with enhanced online security.
Let’s list out some of the key features that have become ingrained in the Tor browser because of this “hardening”.
- The Tor browser always makes use of the Private Browsing mode.
That means, it doesn’t allow any cached web content or cookies.
It doesn’t store any browsing history, nor search history or passwords. - The Tor browser makes use of Disconnect.me as its default search engine.
- It is able to block all other web browser plugins like QuickTime, RealPlayer, and Flash.
- This browser makes use of NoScript and HTTPS Everywhere plugins.
That also means users will have to get used to all scripts disabled on all websites because of the Tor browser default settings.
To all our readers, we suggest that they just leave the default Tor browser settings alone.
It is highly recommended for users to not try and install extra privacy add-ons.
Why?
Because all of these add-ons and settings only help to make the user’s browser more unique.
Hence, it becomes slightly more vulnerable to techniques such as web browser fingerprinting.
As the time of writing this review, the Tor browser had full support for platforms such as,
- Linux
- Mac OS X
- Windows
Users can make their way to the official Tor website in order to download the Tor Browser.
Again, we would like to mention here that the Tor Project offers users a hardened version of its Tor Browser for the Linux platform as well.
As mentioned before, the hardened version comes with slightly more security features.
The Tor browser gets to work on the user’s privacy even before the user installs it.
In other words, when the user downloads this browser, it doesn’t just install itself on the user’s computer machine.
Instead of doing that, it simply manages to run from its official executable file.
That’s for the Windows platform.
What Windows users should also know is that when they start the official Tor Browser, the browser will first try to establish a secure Tor circuit.
Users who are on relatively modern machines, this should not take more than a few seconds.
We would gladly show you a screenshot of the thing but we don’t have the reflexes of a 23-year-old Ronaldo.
User Interface and some tips
This is a good time to mention that under normal use, users will find it hard to differentiate between the regular version of Firefox browser and the Tor browser.
Both are identical.
However, users should have the awareness that when they use the Tor Browser, they are almost guaranteeing themselves to break a lot of websites.
One other recommendation from our side, and the Tor Project’s, is that users should try and run the Tor browser in the browser’s Windowed mode.
This will further help users to defeat techniques such as web browser fingerprinting.
Spying agencies and others can use web browser fingerprinting to detect the actual size of the user’s full-screen mode resolution.
Again, we would like to mention that the Tor network creates a new and totally random Tor circuit after the passing of each time block of 10 minutes.
Of course, users are free to do a bit of manual work and change it to manually force the Tor network to create a brand new and random circuit at any given time on the clock.
Under normal circumstances, users don’t have the option of choosing where the Tor network should locate its Tor exit node.
To further harden the web browser, users can always go to the Privacy and Security settings.
Compatibility
Users who want to take advantage of what the Tor browse has to offer on their Android devices should go with the official
This app enables users to actually route all of their Android device’s connections via the official Tor network.
There is also
This app came out of its beta phase just recently.
It requires the user to install Orbot for it to work properly.
What is Orfox?
Orfox works pretty much like the Tor Browser on a desktop machine.
In other words, Orfox is based on the Tor Browser.
Both of these applications are open-source applications.
Additionally, the Tor Project supports both of these apps officially.
For iOS users, there is the
The Onion Browser is also open source but has come about as a result of an independent development process.
Another option is Tails.
What is Tails?
It is a hardened, and hence highly secure, Linux version.
Yes.
Tails is an operating system.
It comes pre-installed with systems that enable the user to route all of his/her device’s internet connections directly through the official Tor network.
The Tails operating system gained a significant amount of notoriety when Edward Snowden revealed it as his tool of preference.
There are some other software as well as hardware security products available as well.
All of these claim that they provide the user with an increased amount of anonymity and security.
They do it by connecting to the official Tor network.
However, users should exercise caution here because a lot of these security products don’t have the tried and test security features that the Tor Browser offers.
Speed
Now, before we even start this section we would like to let the reader know that ours and any other performance tests and reports are strictly provisional.
Why?
Because it isn’t easy to test Tor with the same conditions all the time.
You see, whenever the user connects to the wider world of the internet via Tor, the Tor network has to pass the user’s data through, at a minimum, three random Tor nodes.
These nodes could run on a wide array of servers with different computing powers.
Moreover, these nodes can have any location in the world.
What we want to clarify here is that, our results and probably everyone else’s have inherent randomness.
With that said, it is also true that we believe these do provide readers with a useful and straightforward indication of how a Tor network would hit the performance of the user’s internet connection.
Most of the time, testers try to test a given security product with a 50 Mbps connection.
But everyone is entitled to test the Tor network on any internet connection they like.
Generally speaking, a broadband connection is a must.
The way testers usually review the Tor network for its speed is by first refreshing the current Tor circuit (which is actually just a randomly selected Tor node) after each and every test.
Most security products including the Tor Browser perform the best when they provide their services via a US or UK based server.
Our research shows that user should expect a pretty hard hit to their download speeds when using Tor.
The Tor network will also decrease upload speed but since most users don’t care about that we won’t talk more about it.
What about DNS leak protection?
There is DNS leak protection.
What about WebRTC IP leak?
There is protection for that as well.
Conclusion
Pros
- Free
- Extremely secure
- Excellent set of anti-censorship tools
- Offers completely anonymous access to the internet
Cons
- Users can’t use this service for torrent or P2P downloads
- No one can guarantee that this or any other service provides complete anonymity.
- For day-to-day use, Tor is painfully slow
Bottom Line
Users who want an extremely high level of security and anonymity while they use the internet will find Tor as a really fantastic tool.
In fact, a lot of experts believe that it is the user’s only genuine option.
Keeping the context in mind, there is no doubt that tools such as the Tor network are heaven-sent for whistleblowers, dissidents and other professionals around the world who have this critical need of absolute online anonymity.
The Tor network can also act as a great anti-censorship tool for which users don’t have to pay a dime.
However, if a government agency or streaming service makes attempts to block the Tor network, then its ability to function as an anti-censorship tool is greatly reduced.
As mentioned throughout the review, Tor is just too slow for day-to-day use.
Moreover, it breaks a lot of the most popular sites on the planet.
Its geo-spoofing location feature is severely limited.
And it is ill-suited for users who want to torrent.
As a general-purpose online privacy tool, our vote still goes to VPNs.
Our research shows that IPVanish is a pretty good one.
So if you want to sign up for it right now from the official website, then
Of course, for true anonymity, users should stick with Tor.
In the end, we would like to reiterate that, no service can ever guarantee any user full and 100 percent online anonymity.
It all depends on the adversary.
If one is well-funded and technically skilled, then with a considerable amount of effort, resources and time, any user can be hacked.
From a practical point of view, there is no tool that provides close to the level of anonymity and online privacy as the Tor network.



IMO tor is definitely one of the best things that happened to the internet. I use NordVPN’s onion over vpn and I must say – not bad, not bad at all, Nord. I’ve only used it for a couple of months so I’ll see if it stays cool in the future, but so far, nothing to complain about.
Thanks for the comment Steph,
Yes definitely.
NordVPN is quickly establishing itself as the go-to source for US Netflix and Tor.
We hope it continues to move forward.