Cybersecurity is adopting technology and measures to protect internet-connected systems such as hardware, software and data against cyberattacks and unauthorized access. The advent of digitization has made everyday tasks easier, including shopping, paying bills, watching movies and a variety of other activities. All of these infiltrations are feasible because of the internet. However, as internet usage has grown, nearly every online user has been vulnerable to attacks and breaches. Cybersecurity is required to keep the internet well-ordered and safe for users. It protects users from cybercriminals, fraudsters, hackers and anybody who wants to financially, mentally or physically harm users or steal data online.
The reliance on the internet has grown in recent years. And without enough caution, hackers are easily able to defraud people of money or other sensitive information. There were 5 billion active internet users globally in January 2022, accounting for 63.2% of the global population. About 86.4% (4.32 billion) of this total used mobile devices to access the internet. Large firms with many employees and affiliates are also at a higher risk of being targeted for holding a large amount of critical data. Furthermore, with so many employees, even a single security failure could threaten the entire firm.
Anyone who is linked to the internet can be trapped if there is no caution. Hacking an internet-connected gadget (laptop, desktop, smart television, smartphone or smartwatch) takes only minutes, which is why cyber security is important.
Online attacks and threats come in many forms. The different types of cybersecurity attacks are detailed below.
- Malware
- Phishing
- Cross-Site Scripting (XSS)
- SQL Injection Attack
- Denial-of-Service (DoS)
- Man-in-the-Middle Attacks
- Ransomware
- URL Interpretation
- Password Attack
- DNS Spoofing
- Brute Force Attack
- Trojan Horses
- Drive-by Attacks
- Eavesdropping Attacks
- Insider Threats
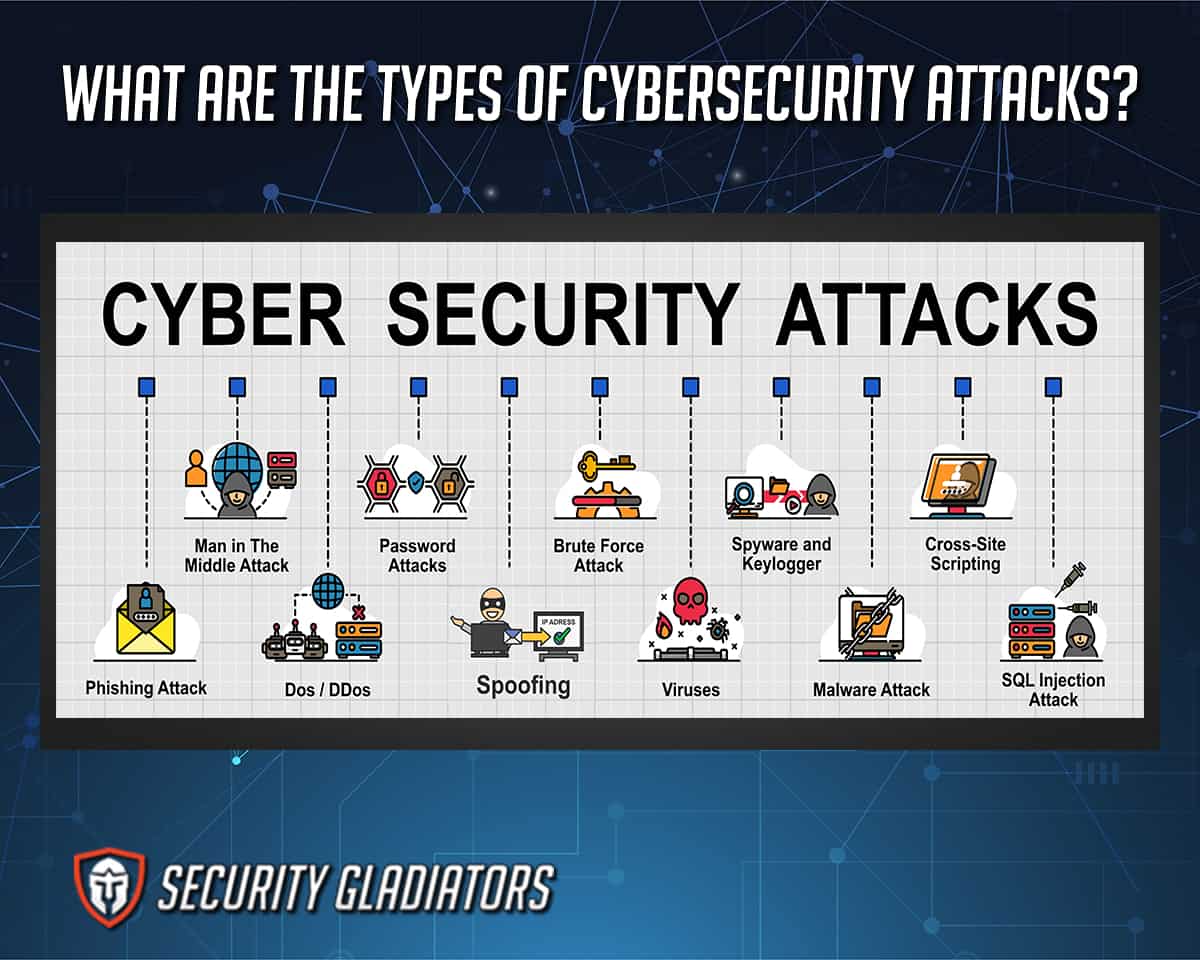
Table of Contents
1. Malware

Malware is software that hackers use to harm or destroy computers or computer systems and gain unlawful network access. Malware (malicious software) comes in various forms, and many hackers will combine different methods to achieve the goals desired. Malware includes ransomware, viruses, spyware, worms, rootkits, adware, trojans, keyloggers, bots and botnets, and other sorts of malicious software.
Malware may be extremely harmful to both organizations and individuals. The effects of malicious software can be seen in the following ways.
- Theft and loss of data
- Slowing down the computer/device
- Restriction of users’ access
- Disruption of normal business operations
- Difficulty in connecting to networks
- System freezing or crashing
- Diverse pop-up ads

Hackers, robbers, fraudsters, private businesses and governments employ sophisticated technologies to create and disseminate malware. Data theft, file damage and financial gain are common motivations for spreading such software. As a result, malware is spread when users click on untrusted links from unknown sources. Malware can potentially infect computers via compromised emails, text messages, Bluetooth connections, infected advertisements and visiting malicious websites. Worms, for example, can move from one infected phone to another without the user’s knowledge.
The severity of malware damage is frequently determined by whether the malware has infected a personal machine or a corporate network. The severity of the harm may also differ depending on the type of virus used and the type of device affected. Users should exercise caution while visiting unknown links or dubious websites. Despite the removal of malware, the damage it causes may be difficult to undo completely.
As malware becomes more sophisticated, consumers can take steps to protect their devices from becoming infected. The following actions are crucial for preventing malware.
- Always be cautious when downloading any file or program.
- Install and activate an ad blocker.
- On the internet, avoid interacting with strangers.
- Use a trusted antivirus to protect all devices.
- Always keep outdated software up to date.
- Scan USB drives and other external devices before use.
- Only download from reliable sources.
- Before installing any software, users should read the terms.
This is important:
Malware victims can report device infringement to the U.S. Federal Trade Commission (FTC) or the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3).There are many approaches to removing malware depending on the type of infection; a few common practices for removing malware from a computer are explained below.

- From a reputable source, download a malware cleanup tool.
- To detect the malware, run an antivirus check.
- Allow the antivirus program to detect and eliminate the infection.
- Restart the computer.
- Use a malware-free backup to restore any damaged files or programs.
2. Phishing

Phishing is a type of cyberattack in which attackers employ trickery to get sensitive information (bank account numbers, login credentials and credit card numbers) or install malware on the victim’s computer, such as ransomware or spyware. Phishing involves using a spoof email as a weapon. The aim is to convince the email recipient that the communication is both helpful and genuine.
Phishing is one of the most significant threats to individuals and organizations because this hacking method masquerades as a reputable source and uses social engineering techniques to convince victims to fall for the attack. Common phishing assaults can have many severe consequences for an individual or company. Phishing harm may involve the following repercussions.
- Loss of data
- Credentials that were compromised
- Infestation of ransomware and malware
- Loss of credibility
- Reputational harm
- Financial consequences
Although email is still the most popular means of phishing, this channel is no longer the only one of its kind. Phishing can also occur via instant messaging, social networking or advertisements such as Google Ads. All of the scams use a link to a website to persuade users to give out login credentials to a specific website or private information such as social security numbers or bank card numbers. The phishing email might be disguised as a routine password reset or information update.

The goal of a phishing website is to appear legitimate. It could be designed to resemble a legitimate website, such as a well-known bank or government portal. The website is usually designed to deceive users into sharing their login credentials or other personal information. Victims will most likely send a link to this malicious website by email or instant chat. Users should, however, research the source of the email or instant message and validate the sender’s identity.
All internet users, whether individuals or big businesses, must take responsibility to avoid phishing. Individual vigilance is required since a faked document typically contains minor errors that suggest a scammer created it. Two instances of these signs are spelling problems and domain name changes. Users should assess the writing style of such an email as well.
Companies and individuals can take many steps to protect themselves from phishing attacks. Some of the precautions that businesses can take to prevent phishing are listed below.
- Two-factor authentication (2FA), which adds an extra layer of verification when visiting critical websites, is the most effective approach for preventing phishing attempts.
- Internet users should regularly change passwords.
- By enforcing certain practices like not clicking on external email links, awareness can help reduce the threat of phishing attempts.
- Use anti-phishing add-ons.
- Organizations should impose stringent password management rules in addition to using 2FA.
- Set up firewalls.
- To detect indicators of an attack, use a data security platform.
This is important:
Victims can report suspicious emails to the Suspicious Email Reporting Service (SERS) in the event of a phishing attempt. The U.K. National Cyber Security Centre (NCSC) will investigate the suspicious email and any websites that link to it. Any other information the victim provides will help NCSC to seek and monitor suspicious activities.When a phishing attempt is suspected, the next step is to take quick action to eliminate the threat. Some useful phishing removal steps are given below.

- To isolate and eliminate the phishing scam, start your computer in Safe Mode.
- Disconnect your device from the internet and any other connected networks.
- Use reputable antivirus software to run a thorough scan of your system. Ignore any pop-ups asking for an internet connection. If malware is detected, follow the software’s instructions for isolating or removing the harmful files.
- Internet users should update their login credentials. Phishing emails are frequently used to acquire personal information such as passwords and bank account information.
- If financial information is at risk, the victim should notify the bank to ensure that any suspicious behavior is properly monitored.
3. Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a client-side code injection attack where a hacker injects malicious scripts into the victim’s web browser to take advantage of the end user’s device. An attacker could exploit a cross-site scripting vulnerability to get around access constraints like the same source policy. An XSS vulnerability that allows an attacker to edit a press release or news item, for example, could impact a company’s stock price or reduce consumer trust.
The most prevalent cross-site scripting attacks are mentioned below.

- Alteration of content, for example, an XSS attack on a pharmaceutical website, might change how pharmaceuticals are prescribed, potentially leading to overdosage and harming patients.
- Sending the user to a different page or website
- Injection of trojan horse programs
- Disclosure of files
- Allowing an attacker to take control of the user’s session and account
- Revealing users’ session cookies
- Impersonation of victims
Note:
Cross-site scripting occurs when data enters an HTTP application from an untrusted source, most commonly a web request. XSS can also arise when data is inserted in dynamic content sent to a web user without verification for malicious elements. Hackers conduct a cross-site scripting attack by inserting a malicious script into user-supplied input. Attackers can also attack by changing a request if the web app is prone to XSS assaults; the user-supplied input processes as code.
Some XSS attacks have no clear target, but the attacker can take advantage of anyone who falls victim to a loophole in the application or site. However, XSS is frequently used in a more direct manner, such as in an email message. A cross-site scripting attack can turn a web application or website into a vector for sending malicious scripts to unsuspecting web browsers. XSS attacks can exploit flaws in VBScript, Flash, ActiveX and JavaScript, among other programming languages. Due to XSS’s deep connection with most browsers, attacks frequently target JavaScript. XSS attacks are both harmful and frequent because of the ability to compromise widely used platforms.
In some instances, preventing cross-site scripting is easy; however, depending on the sophistication of the software, it can be more difficult. The steps to prevent XSS attacks are given below.
- Scan all incoming files.
- Encode outgoing files. Depending on the output context, it may require a combination of HTML, URL, JavaScript and CSS encoding.
- Use headers that are relevant to responses. Use the Content-Type and X-Content-Type-Options headers to ensure that browsers understand HTTP responses as desired. Users can also prevent XSS in HTTP responses that aren’t intended to contain any HTML or JavaScript.
- Follow an appropriate content security policy.
- Make sure all software programs are up-to-date.
- Install a web application firewall.
- Clean up HTML.
4. SQL Injection Attack
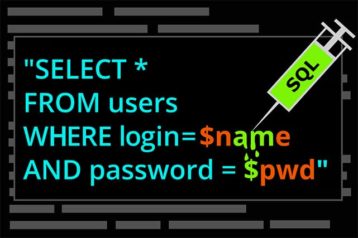
SQL injection (SQLI) is software that hackers employ to exploit data-driven applications. This data could include sensitive company data, user lists or confidential user data. SQL injections are one of the oldest and most dangerous online application attacks. Injections, on the other hand, can result in the following consequences.
- Data theft
- Loss of data (such as user credentials, trade secrets or transaction records)
- Tampered data integrity
- Service interruption
- System breach with a high risk
- Account access that is not authorized
When an online application fails to check values obtained from a web form, cookie or input parameter before forwarding to SQL queries that will run on a database server, SQL injection attacks occur. The danger of a SQL injection attack is usually very serious, and the repercussions can be devastating. SQL injection exploits weaknesses in dynamic SQL statements. A dynamic SQL topic is related to a multivariate function in mathematics, in which the values are fixed, and the results are determined by the values inserted in the independent variables.
Note:
Like a web form, a dynamic SQL statement consists of a specified set of parameters from which an entire statement is developed only when the users fill in actual inputs. Whenever a loophole exists in a dynamic SQL statement, attackers can use complicated scripts to tamper with the pre-existing parameters, leading to misinterpretation of the entire query.Despite the dangers of SQL injections, internet users can still prevent themselves from any form of attack. The steps to prevent injection are listed below.

- Check for input validation. The procedure involves inspection and sanitization to filter out any malicious code.
- Keep software up-to-date.
- Get rid of old databases to reduce entry points.
- Encrypt passwords.
- Clean up data by reducing special characters.
- Implement strict access and designate appropriate privileges.
- Reduce read access to the database.
Furthermore, SQL injection can be removed by rigorously following the methods outlined above. The usage of sophisticated anti-malware programs will also be significant in preventing attacks.
In a SQL attack, victims should contact the police or the appropriate cybercrime agent in the country.
5. Denial-of-Service (DoS)
Denial-of-service (DoS) is a sort of cyberattack where attackers make a network inaccessible to users for a while or indefinitely. Distributed denial-of-service (DDoS) attacks significantly alter computer operations by flooding them with fake traffic from many hacked devices. Customers are prevented from accessing any website that is under DDoS attack.
When a website or application goes down due to a denial-of-service attack, the following things can happen.
- Lost revenue
- Damage to brand and reputation
- Operations and productivity will reduce
- Customer disengagement
DDoS attacks are most commonly caused by a network of remotely controlled, compromised computers or bots. A DoS attack occurs when a hostile actor prevents legitimate users from accessing information systems, devices or network resources. DoS attacks can disrupt email, websites, online accounts (such as banking) and other services that rely on the system or network. DoS attacks are carried out by flooding a targeted host or network with traffic until it becomes unable to reply or crashes, restricting legitimate users’ access.
Note:
A DoS attack may imitate non-harmful availability concerns, such as technical issues with a specific network. A DoS attack can be detected by unusually slow network performance (opening files or visiting websites), the unavailability of a certain website or the inability to access any website. As a result, network traffic monitoring and analysis is the best technique to detect and identify a DoS attack. Users can use a firewall or intrusion detection system to monitor network traffic.To protect devices against DoS attacks, every internet user and company must devise preventative measures. Therefore, users can take the measures below to avoid DoS attacks.

- Make a plan for dealing with denials of service.
- Build a resilient network.
- Follow basic network security procedures.
- Use anti-DDoS technology and software to your advantage.
- Make a backup of your files.
- Keep an eye out for odd behavior.
In the event of a DoS attack, victims should call their local law enforcement department. In many locations, DDoS assaults are considered illegal. Victims contribute crucial information by making a report, which may be useful in various investigations or arrests of the attackers. Victims should also disclose all pertinent information, such as the timing of the incident, any visible changes, the nature of the attack and any procedures used.
The steps to mitigate DoS attacks are listed below.

- Identify the DoS assault as soon as possible.
- Keep an eye on the website’s traffic.
- Make provisions for enough bandwidth.
- For assistance, contact your hosting provider.
- Make contact with a DoS mitigation expert.
- Configure firewalls and routers.
- Use a firewall for web applications.
6. Man-in-the-Middle Attacks
A man-in-the-middle attack (MITM) occurs when an attacker intercepts a user’s conversation with an application to eavesdrop or impersonate any parties participating in the conversation. MITM is harmful because it allows hackers to intercept communications secretly. A MITM attack can interrupt human-to-human communication and machine-to-machine communication, which is critical for a secure internet connection.
The ramifications of a MITM attack can be rather substantial, especially with growing economic globalization and the use of open WiFi. For example, an attacker may observe a user making a financial transaction and alter the destination account number or sent amount. Furthermore, attackers could compel customers to download infected updates that install malware rather than legitimate upgrades on mobile devices.
A MITM attack happens when an outside entity intercepts a communication between two systems. The attackers pose as genuine participants after positioning themselves in the middle of the exchange. Man-in-the-middle attacks can occur in any type of internet communication, including email, social media and web browsing. Hackers can not only listen in on users’ private conversations, but they can also intercept all of the data on their devices.
Companies should take all the necessary precautions to ensure that security policies and systems can properly defend against MITM attacks. Here are a few steps internet users can take to prevent MITM threats:

- Employees should be cautioned against doing any personal work on public networks.
- Make use of an appropriate virtual private network (VPN).
- Use an HTTPS-secured browser.
- Update software to the latest version.
- Partition WiFi networks into groups based on users.
- Utilize two-factor authentication.
- To protect messages and emails, use SSL/TLS.
- Install an intrusion detection system (IDS) to check the network and notify if anything unexpected happens, such as a traffic hijacking attempt.
- Regularly audit and monitor networks.
- Organizations should educate employers about common IT security concerns.
Following these procedures will also assist organizations in removing MITM. However, users should report any suspicious MITM-related attacks to the appropriate law enforcement agency for documentation and investigation.
7. Ransomware
Ransomware is a kind of software that prevents a victim from using the infected computer or files unless a ransom is paid. For several years, different versions of ransomware have been discovered, and they frequently try to extort money from victims by showing an on-screen alarm. Ransomware is malware that can damage or delete computer files, resulting in profit losses for businesses with infected systems.
Some examples of the harms of ransomware are listed below.

- Loss of information
- Loss of productivity
- Profit losses due to downtime
- Cost of replacing faulty equipment and recovering data
- Damage to company’s reputation
- Funding new security protocols
- Possible legal repercussions
- Employee-training costs in the event of an attack
Ransomware is frequently disseminated via phishing emails with malicious attachments or drive-by downloads. Drive-by downloading happens when an unsuspecting person accesses an infected website, and malware is downloaded and installed without the user’s awareness. The attacker encrypts the files on the victim’s computer, adds extensions to the data and holds the files captive until the ransom is paid.
There are various actions organizations may take to prevent ransomware, all of which have varying degrees of efficacy. Some best practices for preventing ransomware attacks are given below.
- Implement spam filtering systems
- Block harmful JavaScript files
- Update anti-ransomware software
- Detect assaults with an intrusion detection system (IDS)
- Block ads
- Configure the firewall
- Regularly perform security checks
- Enforce the use of strong passwords to employees
- Strengthen endpoint security
This is important:
Ransomware victims in the U.S. can report their attacks to the FBI, the Cybersecurity and Infrastructure Security Agency or the Secret Service. To ensure all other agencies are contacted, a victim only needs to report the occurrence once. Similarly, the Internet Crime Complaint Center provides citizens with a secure and accessible way to report suspected internet-facilitated criminal behaviors to the FBI.In a ransomware attack, users can remove the encryption trojan by adhering to the following procedures.

- Disconnect devices from the internet.
- Investigate the situation with appropriate internet security tools.
- Make use of a ransomware decryption program.
- Restore backups.
In the instance of screen-locking ransomware, however, starting the computer in Safe Mode may prevent the screen-locking activity from loading, allowing the victim to utilize antivirus software to attack the malware.
8. URL Interpretation
URL (Uniform Resource Locator) interpretation is a cyberattack in which some parameters of a user’s web page form data are modified without permission. The parameters of a user’s request are manually adjusted by keeping the URL’s syntax but changing its semantic meaning. URL interpretation is primarily used against websites that use CGI scripts. To carry out a URL interpretation attack, a hacker must first guess the URLs used to get administrative access to a site. Hackers can modify the site or acquire access to sensitive information once reaching the desired page.
Note:
To learn how a URL interpretation attack is carried out, consider an email program that allows users to reset their email passwords by answering a security question. The application opens a page where the user can set an alternate email address after answering the security question satisfactorily. The page that receives the request allows users to reset their passwords and contains all of the user’s login credentials.The URL that carries the request to fetch a user’s details and send them to the alternate email identification provided can be altered to fetch the details of another user via URL interpretation. As a result, a URL interpretation attack exposes other users’ information.
It’s also crucial to prevent databases or systems from URL interpretation attacks to avoid exposure to other malware. Therefore, to avoid URL interpretation attacks, internet users should adopt certain authentication measures for any sensitive areas of the respective site. Users can also utilize multi-factor authentication (MFA) or unique and strong encrypted passwords.
9. Password Attack

A password attack occurs when a hacker attempts to steal a user’s password. Passwords are getting less secure due to limits on certain letters and numbers. Password attacks can result in a data breach, which can be disastrous for both the organization and the individual. One of the most common types of corporate and personal data breaches is password attacks.
To begin with, the majority of passwords that hackers have access to come from huge data breaches involving common online services. When popular services such as LinkedIn, Facebook and Adobe have millions of records exposed, the passwords obtained are gathered in enormous databases. There are many password-breaching applications on the market, each with a specific algorithm but all performing the same action in two ways.
Cybercriminals can build permutations using a dictionary of commonly used passwords or deploy a brute force attack to try every possible combination. Criminals can try as many times as possible to break a password list once the list is obtained. The hackers’ purpose is not to crack a single password but to conduct tests against the entire file, knocking out targets. The password-breaking is made possible by today’s graphics hardware. On a desktop computer with a powerful graphics processor, some commercial programs can test trillions of passwords each second.
Users can safeguard against password attacks by following the measures outlined below.

- Reset all the default passwords for all accounts.
- Choose a password that is difficult to guess.
- Use unique passwords for each account.
- Use multi-factor authentication.
- Use biometrics, such as fingerprints or facial recognition.
Victims of password attacks can report the incident to the appropriate authorities. U.S.-based users can easily report the attempted fraud to the Federal Trade Commission. Users in the U.K. can also forward the email to the National Cyber Security Centre’s phishing site.
Pro Tip:
Users can use a password auditor to secure and strengthen passwords against future attacks.10. DNS Spoofing
DNS spoofing (also known as DNS cache poisoning) is a type of cybercrime in which manipulated DNS records are used to redirect online traffic to a malicious site. Users are led to malicious websites due to DNS attacks, resulting in the leakage of sensitive and personal data. DNS spoofing provides many hazards, each of which puts users’ devices and personal information at risk.
The most prevalent consequences of DNS poisoning and spoofing are listed below.

- Data theft
- Malware infection
- Discontinued updates on security
- Censorship
An attacker uses weaknesses in the domain name system to launch a DNS assault. DNS spoofing entails changing the DNS server’s IP addresses with the attacker’s IP. When consumers try to access a specific website after this process, the connection is redirected to the attacker’s faked DNS server, which contains fraudulent web pages.
Users need to avoid DNS spoofing at all costs; some suggestions are given below.

- Use detection tools for DNS spoofing.
- Add extensions to the domain name system’s security.
- Use end-to-end encryption.
- Avoid clicking on suspicious or unrecognized links.
- Scan the PC regularly for malware.
- To get rid of poisoning, clear the DNS cache.
- Employ a virtual private network.
Users should report any violations to the appropriate law enforcement agency. Similarly, DNS spoofing may be permanently avoided by following the guidelines outlined above.
11. Brute Force Attack
A brute force attack is a cryptographic assault that includes guessing all potential password combinations until the correct one is found. The longer the password, the more hackers must evaluate possible combinations. A brute force attack involves guessing login information, encryption keys, or trial and error locating a hidden webpage. Hackers use illegal access because brute force assault involves guessing usernames and passwords.
The user is always the victim of a brute force attack, while hackers benefit. Some of the consequences of a brute force attack are given below.
- Stealing personal information and possessions
- Malware is spread to cause disruptions
- Using victims’ computers to carry out criminal actions
- Tarnishing the reputation of a user or website
Some precautions to avoid a brute force attack are listed below.

- Use strong, unique passwords.
- Limit access to authentication URLs.
- Limit login times/attempts.
- Make use of CAPTCHAs.
- Activate two-factor authentication.
- Keep an eye on the IP address.
When a user is susceptible to a brute force attack, reporting the issue to the country’s cybercrime law enforcement body is important. The incidence of a brute force attack, like any other cyber-attack, should be documented in full to aid the agency’s investigation.
However, to permanently block brute force attacks, users must properly follow the precautionary procedures outlined above. Users should also have dependable software to keep an eye on any strange activities.
12. Trojan Horses
A trojan horse is a type of malware that appears to users as a harmless file but is very dangerous. Hackers employ trojan horses to access users’ systems, and the malware usually comes in the form of an app or software. A trojan horse is a piece of malicious software that infects a computer. Some of the harmful implications of the trojan horse are given below.

- Keylogging
- Data corruption
- Backdoor attacks
- Disposal of documents
- Disclosure of confidential information
- Unauthorized access for hackers
Hackers persuade end-users to install harmful software through social engineering techniques. Banner ads, internet links and pop-up advertisements can lure users into falling victim to the download trap. However, the most common way for trojan horses to propagate is through seemingly harmless emails and attachments. To deliver emails to a large number of recipients, trojan horse developers often use spamming strategies.
A trojan horse can also spread from one compromised computer to another, which is sometimes performed by turning a good computer into a zombie computer without the user’s knowledge. To construct a network of zombie computers, hackers use these zombie systems to continue disseminating more malware. Trojans can also infect mobile devices like smartphones and tablets using mobile malware, in addition to computers and desktops. An attacker could divert traffic on WiFi-connected devices and use the compromised devices to commit cybercrime due to this type of infection.
To mitigate any cyberattack, all internet users and companies should take proper and effective preventive steps. As a result, users can avoid trojan horse infections by following the methods outlined below.

- Don’t install or download software from an untrusted source.
- Avoid opening attachments or running programs provided through email from an unknown sender.
- Keep all software programs up-to-date with the most recent patches.
- Make sure the device has a trojan anti-malware program installed and functioning.
- For each online account, use a distinct and unique password consisting of different numbers, letters and symbols.
- Ignore pop-up advertisements that try to get people to click.
- Make regular backups of files.

Reporting any cyberattack is dependent on location. For instance, when a crime occurs in the U.K., it should be reported to the police. A police force may examine a criminal accusation or submit it to the Police Central e-Crime Unit (PCeU), responsible for investigating the U.K.’s most serious cybercrime events. There’s also Action Fraud, an alternate reporting organization for internet-enabled crime. Since not all computer crimes are investigated, Action Fraud records and forwards crime reports to the National Fraud Intelligence Bureau, determining if the incident warrants further investigation.
In the U.S., victims should contact the local FBI office, the Secret Service or the Internet Offense Complaint Centre to report the crime. Users in Australia should contact the Australian State or Territory Police to report the crime. Although state-by-state investigative policies differ, the Australian Federal Police website guides whether to report to the Australian State or Territory Police.
Once a trojan has infected a device, use an effective anti-malware tool to clear up the compromised device and run a comprehensive system scan. However, users can manually delete a trojan after detection by following the steps given below.
- Stop the system from restoring itself.
- When restarting the device, select “Safe Mode” from the menu.
- Remove all trojan-affected programs.
- Remove all extension application files from the system folder.
- In “Normal Mode,” restart the device.
13. Drive-by Attacks

A drive-by attack (drive-by download) is a cyberattack in which a malicious script forces a program to download on a device without the user’s permission. Malware is frequently propagated through drive-by downloads. Cybercriminals search for unsecured websites and insert a harmful script into one of the page’s HTTP or PHP code. Unlike many other types of cyberattacks, a drive-by attack does not require the user to authorize the attack actively. Drive-by attacks are intended to compromise a user’s device. Some of the consequences of a drive-by attack are given below.
- Hijacking users’ devices to create a botnet, infecting other devices or breaching users’ devices are all possibilities
- Spying on users’ online activities to steal login passwords, financial information or identities
- Inflicting damage on users’ data
Malicious drive-by downloads enter consumers’ devices through two major methods. When a user takes an action that leads to infection, such as clicking a link on a bogus security alert or downloading a trojan, this is the first way a user can relate with a drive-by attack. Another situation is when a user visits a website and becomes infected without receiving any warnings or action. These downloads can be found on any website, including standard sites.
Drive-by attacks take advantage of digital technology’s inherent faults and risky security practices, including exploit kits, zero-day exploits and other security problems. To prevent a drive-by attack, every internet user should take the precautions listed below.

- Regularly update all software programs and applications.
- Install any necessary security software.
- Keep an eye on the firewall.
- Don’t open attachments in emails from an unknown source.
- Educate employees about how to avoid cyberattacks.
- Use a password that is both strong and unique.
- Carefully read and evaluate security pop-ups before clicking.
- Use ad-blocking software.
- Use two-factor authentication.
- Change passwords frequently.
Victims of drive-by attacks should report the event to the appropriate law enforcement body in the user’s country.
Pro Tip:
Using a reliable anti-malware tool, users can eliminate the drive-by assault. Users must select appropriate software to monitor and warn of any unexpected activities.14. Eavesdropping Attacks

Eavesdropping (also known as sniffing or snooping) is a type of cyberattack in which a hacker steals data from computers, servers, mobile devices and Internet of Things (IoT) devices. Eavesdropping is most common in wireless communication and uses unsecured network communications to access data sent or received by the user. For businesses, an eavesdropping attack can result in financial loss, identity theft and privacy violations. Eavesdropping attacks allow attackers to listen to important business facts, chats and trades that threaten users’ privacy.
The purpose of eavesdropping attacks is simple: snooping on unprotected or unencrypted transmissions to collect confidential and valuable data. Unsecured network connections, such as a WiFi hotspot or websites without HTTPS protocol, could intercept the flow of data packets. This data could include users’ browsers, emails, messaging activity and any private corporate information.
Sophisticated attackers use social engineering techniques like phishing to install malware and spyware programs on victims’ networks. Internet users can avoid eavesdropping attacks by following the best practices listed below.

- Encrypt data transmissions and private discussions.
- Confirm that employees are aware of cybersecurity threats.
- Patch and update software.
- Install security and filtering measures.
- Avoid links that are suspicious or untrustworthy.
- Ensure that security teams authenticate inbound network packets.
- Organize the network into categories to limit resource access to only authorized people.
Every eavesdropping attack victim, however, should contact the local police department. Officers from the local law enforcement agency can respond promptly and get more help after assessing the situation.
Pro Tip:
Internet users can prevent eavesdropping attacks by installing anti-malware software that protects against all types of cyber threats, including eavesdropping.15. Insider Threats
An insider threat is a malicious threat that originates from within a company, such as current or former employees, business associates or other employees. When someone close to an organization with allowed access misuses that access to harm essential information or systems, this is referred to as an insider threat. Theft of personal information, fraud and computer system attacks are all possible threats.
Insider threats can be devastating to an economy at large. A few of the effects are listed below.

- Loss or theft of vital data
- Organizational productivity suffers
- Costs associated with incident investigation and system and process remediation are included in the financial impact.
- Fines and lawsuit defense costs linked to complaints from persons and organizations affected by data breaches are legal/regulatory consequences.
- Rejection in the marketplace
- Reputational consequences
Because insider threats are frequently directed at organizations, good planning necessitates teamwork. The most important steps that organizations can take are provided below.

- Sort organizational information into categories based on importance and sensitivity.
- Keep an eye on what users are doing across the entire network.
- Keep business and personal accounts distinct by limiting access rights.
- Keep the entire company informed about insider dangers.
- Automate the response process.
- Create policies that prohibit password-sharing.
- When employees change roles or leave the firm, remove the individuals’ access to resources as soon as possible.
- Regularly look for and delete unused accounts.
- Place restrictions on third-party access.
- For access to sensitive systems and data, use multi-factor authentication.
In the case of insider threats, when a user is not a government employee, military member, or contractor, local law enforcement or the FBI should be contacted.
During the elimination of an insider attack, it’s critical to stick to the prevention measures and educate personnel about the risks and repercussions. Also, including measures in the organization’s security strategy to prevent and detect misuse is one of the best ways to avoid insider risks. Insider misuse investigations should be governed by organizational policy.
What Are the Biggest Cybersecurity Threats in 2022?
The biggest cybersecurity threats in 2022 are detailed below.
- COVID-19 Phishing Emails

During the COVID-19 pandemic, many people were confined to their homes to prevent the infection from spreading. As a result of this effect, remote work processes grew in popularity, increasing the number of internet users. Cybercriminals found this to be an ideal hatching ground.
COVID-related phishing schemes are still one of the biggest cyber security challenges in 2022. Phishing attempts are designed to direct users to websites that include fictitious material regarding the coronavirus. These sites frequently use the user’s system resources to earn cryptocurrencies such as Bitcoin without consent. Following that, internet users become vulnerable to phishing attempts.
- Ransomware

Ransomware encrypts files on computers and demands a ransom in exchange for the files’ originals. The development of cryptocurrencies such as Bitcoin has undoubtedly aided ransomware assaults by making bad actors more anonymous. For example, the Cyrat ransomware was disguised as software to restore corrupted DLL files on the computer, but in reality, parts of the system are encrypted during execution.
- Internet of Things Attacks

Every year, the number of linked devices on the Internet of Things (IoT) increases. Linked IoT devices are projected to reach 75 billion by 2025, a threefold increase from 2019.
Many IoT devices have insufficient or non-existent security features. This covers household items like televisions, stereo systems, lights, autos and home security systems. The attacker can acquire access to these and exploit them to steal sensitive data like passwords and personal information. This is one of the most rapidly spreading cyber security threats.
- Patch Management
Users are exposed to known dangers if they do not keep their systems and applications up-to-date with the latest updates. One of the most prevalent weaknesses exploited by hackers is the use of outdated software versions. This is one of the oldest cyber threats.
- Social Engineering and Cryptocurrency

Cyber security threats persuade people to give out confidential and sensitive data, frequently done through social media platforms. Cybercriminals employ deception and trickery to trick users into providing personal information such as passwords, dates of birth and bank account numbers. Answering what appears to be a harmless social network quiz about a first pet’s name and mother’s name, for example, might provide hackers with the information needed to access internet accounts, including bank accounts.
Social engineering can take the shape of an email, a face-to-face meeting or even a phone conversation to obtain sensitive information. SIM swapping is an assault in which the bad actor obtains access to the victim’s SIM card. The mobile carrier is duped into believing that the perpetrator is the true client due to devious social engineering. If the bad actor is successful, the attacker will possess the SIM card and receive text messages and phone calls. This technique can also be used to get into social media accounts or Bitcoin wallets.
- Insider Threats

In 2021 (according to a Verizon Data Breach Investigation Report), 22% of data breaches were caused by internal attackers. Insider threats are becoming more of a concern as more people work from home. Most cases are caused by ignorance or complacency, which remote employment can encourage. Cybercriminals have pounced on this opportunity, frequently using phishing tactics to target these employees.
The easiest approach to deal with such insider risks is to give all staff thorough security training. Companies should also organize regular refresher seminars to ensure no best practices are forgotten. Remote monitoring software can also assist in detecting and preventing potentially dangerous behavior.
- DDoS Attacks
Distributed denial of service (DDoS) attacks, like other cybersecurity threats, are not new. DDoS is becoming increasingly prevalent, with about 10 million DDoS attacks recorded in 2021. These brute-force approaches have proven excruciatingly effective as more firms have switched to the cloud. Slowing or crashing these networks, especially as more valuable data is stored in the cloud, can be extremely damaging. Furthermore, several small firms are still learning how to secure and manage their cloud-based information properly.

Proactive patch management can help reduce the vulnerabilities that DDoS attacks take advantage of. Network monitoring can aid in detecting and preventing security breaches before too much harm is inflicted.
- Deep Fakes

Deep fakes are a relatively new cybersecurity problem that many experts predict will become more prevalent in 2022. Deep learning algorithms are used to modify photos, videos and audio recordings in a deep fake. Hackers can use these files to create very convincing phishing attacks. Deep fakes have more information to draw from as more video and audio samples of individuals appear online, resulting in more lifelike and believable deep fakes. In one serious incident, fraudsters impersonated an executive’s voice and requested a $243,000 transfer.
Pro Tip:
To combat deep fake attacks, firms should stay wary and double-check all systems. Zero-trust policies can aid in verifying all transactions and procedures. To reduce the potential of deep fakes, caution is advised when placing personal information online.- Mobile Malware

Mobile devices are used for work by more than just remote employees. For some jobs, more professionals are rapidly switching from desktops to laptops or cellular phones.
Mobile malware is a type of malicious software that is specifically designed for use on mobile devices. Mobile malware attacks are anticipated to be one of the most important cybersecurity concerns this year, as more sensitive enterprise data is accessed and stored on mobile platforms.
- Zero-Day Exploits
Zero-day exploits are used to attack systems before being updated. Zero-day exploits are notoriously difficult to combat. Such threats are now more prevalent than ever before. More than 79 zero-days were found in 2021 , which is more than double that of 2020 and far outnumbering any other year. Lately, zero-day attacks have specifically targeted Microsoft Exchange Servers.
How Often Do Cyber Threats Occur?
Cyber threats are everywhere with the growing adoption of internet-connected devices. Some statistics on the occurrence of different cyber threats are given below.

- Human error is responsible for 95% of all cybersecurity breaches.
- In 2022, the global market for information security is expected to reach $170.4 billion.
- In 2019, spear-phishing attacks hit 88% of firms throughout the world.
- 68% of CEOs believe cybersecurity threats are growing.
- Only 5% of businesses’ files are properly safeguarded on average.
- In 2021, data breaches revealed over 22 billion records.
- Financial motivation accounted for 86% of breaches, while espionage accounted for 10%.
- About 45% of the breaches used hacking, while malware was used in 17% and phishing was used in 22%.
- The most common malicious email attachment formats are .doc and .dot, which accounts for 37%, followed by .exe, which accounts for 19.5%.
- Humans and machines use an estimated 300 billion passwords worldwide.
- As of 2021, the average cost of a data breach is $4.24 million.
- It took an average of 280 days from the time a breach was discovered to when users resolved it.
- In 2021, 83% of data breaches contained personal information.
- In 2021, the average number of harmful mobile apps blocked per day was 24,000.
- Malware is delivered by email in 94% of cases.
- A ransomware assault on a business costs $133,000 on average.
- Office files account for over 48% of harmful email attachments.
- Ransomware detections have been more common in nations with larger amounts of internet users, with the United States accounting for 18.2% of all ransomware attacks.
- Around 60% of malicious domains are linked to spam campaigns.
- Approximately 20% of malicious domains are brand new and are used within a week of registration.
Why Do People Launch Cyber Attacks?
Cyber attacks aimed at causing economic harm may have different goals than those aimed at compromising national security. Even if the attacker claims responsibility, a cyber attack’s true purpose and primary goal may be hidden or obscured in many circumstances. Cyber attacks on enterprises are frequently planned and motivated by monetary gain. People can, nevertheless, attack to gain the following information.

- Financial information about the company and customers
- Highly sensitive personal information
- Email addresses of customers or employees, as well as login credentials
- Customer databases
- Lists of clients
- Infrastructure for information technology
- IT support
- Attempting to make a social or political impact
- Espionage
- Psychological activity
- Access to intellectual property like trade secrets
Are Cyber Attacks Preventable?
Yes, cyber attacks can be prevented by learning and employing a variety of appropriate protocols, exploits, tools and resources. Some helpful guidelines users can take to avoid cyber attacks are given below.

- Create policies for cyber security.
- Employers should receive security awareness training.
- Install sufficient firewalls.
- Endpoint detection and response should be installed (EDR).
- Conduct vulnerability analyses.
- Perform regular penetration testing.
- Install spam filters and anti-malware software.
- Implement security events and information management.
- Employ intrusion detection and prevention software (IDS and IPS).
- Develop a data loss prevention (DLP) strategy.
How Can Businesses Prevent Cyber Attacks?
While digitizing a business has its advantages, it also raises the danger of scams and security risks. Businesses avoid data breaches, loss of files and reputational harm by protecting their network from cyber attacks. Businesses can defend themselves against cyber attacks by following the steps outlined below.

- Make securing business data a priority.
- Organizations should educate employees about cyber security.
- Consider getting some sort of cyber insurance.
- Back up business information regularly.
- Protect devices and networks.
- Encrypt sensitive information.
- Change online passwords frequently.
- Keep an eye on the usage of computers and systems.
- Create policies that will guide employees on data protection.
- Keep up with the latest news and trends about emerging cyber threats.
What Tools Do You Need to Prevent Cyber Attacks?
Users can reinforce network security with a variety of open-source and paid products on the market, such as those listed below.

- Wireshark
- Forcepoint
- Paros Proxy
- Nmap
- Nessus Professional
- Nexpose
- TrueCrypt
- Netstumbler
- KeyPass
- Burp Suite
- Tor
- Snort
- Acunetix
- SolarWinds Security Event Manager
- Bitdefender
- Avira
- Mimecast
- Webroot

