
As mentioned before, currently, encryption is the most important tool to protect data that users all over the world send, receive and also store. Encryption can be used for all types of data including text messages, lots, patents, banking information, medical records, and browser history. There are many different types of encryptions. The two most popular types of encryptions are symmetric and asymmetric encryptions. Both have a specific set of advantages and disadvantages which makes each one suitable for different types of tasks.
Table of Contents
What is Encryption?
Encryption is a tool (currently the best available tool) to secure data. Encrypting and decrypting data is almost a foolproof way to keep sensitive information out of the hands of bad actors. The term encryption should not be confused with another related term cryptography. Cryptography refers to the study of methods that help to conceal messages and generate secret codes. On the other hand, encryption is simply a tool that scrambles data and makes that data unreadable for anyone without the decryption key.
Encryption is currently the most effective method to transform information into a secret code. As mentioned before, without encryption, the data is generally considered to be in plaintext. When the data is encrypted, the term used is ciphertext. Encryption algorithms are essentially the critical formulas that take messages and encode/decode those messages. Algorithms come with variables such as keys. Both form a part of a given cipher. The variable is generally called a key. The key is used to generate a unique output once a cipher starts working. Any entity without proper authorization has to guess the kind of cipher used to encrypt data. That is, assuming the same entity can first find a way to intercept data in transit or in storage. The same entity will also have to know the keys used as variables. Encryption is a powerful tool to protect data integrity precisely because guessing the right cipher and then the keys is highly resource intensive and unlikely to lead to a successful outcome.
How does Encryption Work?
The encryption process is simple. First, the sender of a given message has to pick a cipher that can scramble the message. This is usually considered the start of the encryption process. Additionally, the sender also has to pick the variable that will be used as a key to create a unique secret code to encode the message. As mentioned before, the two most popular ciphers are asymmetric and symmetric. Once the cipher has transformed the message from plain text to cipher text, that’s when the digital data becomes safe and secure. Encryption helps protect data both in storage (on computer systems) and during transmission (through any given network including the internet).
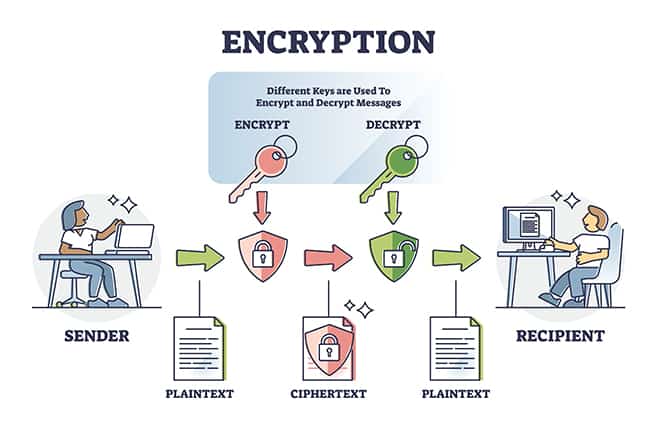
Once a message is sent to the recipient and the message is received, upon access, the message has to transform to the original state. The process of transforming the data to the original form is called decryption. Both the recipient and the sender have an encryption key. This encryption key is always kept secret. The key represents algorithms that can scramble and unscramble messages depending on the need of the user.
Why is Encryption Important?
Encryption is important for many reasons but the most important reason is that encryption keeps data safe from hackers and government agencies trying to spy on company products or user messages. Encryption is also more important to certain types of organizations and kinds of individuals. For example, a purely IT-related company can benefit from encryption a lot more than a construction company. Similarly, individuals who carry out the majority of the task can benefit from encryption the most.
Generally though, encryption is important because the tool helps make any message’s content confidential which is the end aim of any cybersecurity professional and/or product. Confidentiality is a big deal for certain types of online users such as journalists reporting from war zones and whistleblowers. Encryption is also important for proper authentication. With the help of encryption, any given message’s origin can be verified.
Encryption is also important to hold the sender of a given message responsible. Because of the way encryption works, if the sender shoots an encrypted message, there is no way to deny carrying out that action at a later date. Finally, encryption is important to keep the integrity of data in check. Encryption makes sure that any message’s contents remain untouched and unchanged.
Encryption is the only reliable way to reduce any data’s vulnerability to a potential cyberattack. Privacy and security tools such as encryption become even more important when physical access to a given data server is probable. Websites that do not encrypt stored data can easily leak sensitive information once hacked.
What are The Different Types of Encryption?
There are many different types of encryption but the two most common ones in use today are asymmetric and symmetric encryption. Some cybersecurity experts differentiate types of encryption according to use cases as well. By use type, the types of encryption include FDE, end-to-end encryption, network-level encryption, column-level encryption, and field-level encryption.
The different types of encryptions are given below:
What is Symmetric Encryption?
Symmetric encryption is the type where the key used for both the encryption and decryption process is the same. Because of the fact that the key does not change, extra care needs to be taken while transferring the secret key to both the recipient and the sender of a given message.
In symmetric encryption, the sender first composes a message/data in plaintext. The key is used to encrypt the data to generate the ciphertext. The ciphertext, which is gibberish to anyone without the key, is then sent to the receiver of the message. Moreover, the receiver also receives the same key that was used to encrypt the message/data at the beginning. Once the key is used to decrypt the message/data, the receiver can view/analyze the message/data in plaintext and thus protect the data/message in transit.
Note:
Symmetric encryption is currently considered the simplest type of encryption since there is only a single key that both encrypts and decrypts information. The secret key used for encryption and decryption can be anything from a random set of letters, to a word or even a number. Currently, the most popular examples of symmetric encryption include RC6, RC5, DES, RC4, and AES in addition to Blowfish. The symmetric encryption key is different from the actual algorithm used which could be AES 128-bit, and/or AES 256-bit.What is Public-Key Encryption? (Asymmetric)
Public key encryption is also known as asymmetric encryption. Asymmetric encryption is a slightly newer method to protect information when compared to symmetric encryption. Asymmetric encryption uses two keys for both the encryption and decryption process, one for each. Just as before, the secret keys used for encryption/decryption and/or changing plain text to ciphertext have to be exchanged over the internet. Because there are multiple keys, asymmetric encryption is more resilient against malicious attacks. Asymmetric keys are sometimes considered more secure because of the requirement of two related keys instead of a single one. Thus boosting the overall security of any information exchange. In Asymmetric encryption, there exists a public key. The public key is available to any online user looking to send a message to a target receiver. There are no charges to use the public key. In addition to the public key, there is also the private key. The private key is always kept hidden from everyone else apart from the receiver of the message.
Using asymmetric encryption, the message first has to be encrypted using the public key made available by the receiver of the message via various online platforms or some other way. Then once the message is received, the receiver has to use the secret key to complete the decryption process and consume the information/message. Similarly, from another perspective, the sender has to use the private key to encrypt a given message. Then the receiver has to use the available public key to decrypt the message.
Note:
There is little need to keep the public key private or even secure. The readily available nature of the public key enables users to pass the public key over the internet to encrypt messages. Generally, asymmetric encryption offers more protection of information, especially during transmission. Some of the most widely available asymmetric key algorithms include PKCS, Elliptic curve techniques, DSA, RSA, and ElGamal.What is Better? Symmetric Or Asymmetric Encryption?
Generally, Asymmetric encryption is considered better for the average online user. However, depending on the use cases, both asymmetric encryption and symmetric encryption can offer unique benefits. Asymmetric encryption is definitely better for digital signing. The presence of a private and public key for encryption and decryption means that the signer of a given document can be ascertained easily. The same is the case during cryptocurrency transactions. Asymmetric keys are also considered better because there is no concept of losing the public key since a different key is used for the decryption process which only the owner has. However, the fact that there are two different keys used to complete a given transaction, asymmetric encryption is also slower.
Symmetric encryption is faster and hence used in situations where speed is important. Such situations include banking. Banks not only have to keep information extremely secure but also access the stored data quickly. That means, banks have to decrypt information quickly. Since asymmetric encryption only uses one secret key, the time required to decrypt and encrypt information is less. Symmetric key encryption is also much simpler to implement for any organization. However, the loss of the encryption key means the security of encrypted data is at risk. With asymmetric encryption, such a problem does not exist as a separate private key is required to decrypt the information and view contents.
What are The Advantages of Encryption?
There are many advantages of encryption depending on how an organization and/or individual operates in the online world. In terms of security, the main advantage of encryption is protected against data breaches. Encryption protects data not only while in transit but also in storage. Encryption not only keeps organizations safe but also employees when a slip-up happens. An employee might get mugged and end up losing company devices. Encryption can make sure the data on the stolen device remains secure. Encryption also reduces risk in any type of online transaction including banking, medical records checking, online shopping, and communicating sensitive material.
Encryption also enhances privacy to a great degree. Depending on the implementation, encryption may require any access to be verified before accessing data. Thus encryption ensures that only the authorized recipients and/or data wonders can decipher sensitive material over a network. Via encryption, users and companies can guard against aggressive advertising attempts, many types of cyberattacks including man-in-the-middle attack attempts and spying on the part of internet service providers in addition to government agencies. Of course, users have to make sure only the best encryption software is used for protecting online communications via any channel.
Another less talked about benefit of encryption is data integrity. Many types of cyberattacks manipulate data when data is in transit. With encryption, bad actors cannot change a given file’s content or size or even the type of file. Encryption also guards against unauthorized deletion and/or copying of encrypted files. Sometimes, developers verify data present on a given website via encryption. Web browsers and the server hosting the website have to exchange information for any interaction to take place. If the information is encrypted, the process of verifying if the website is a real one (instead of a fake malicious copy) becomes much easier.
Finally, encryption can help organizations comply with new rules and regulations such as EFRPA, HIPAA, FCPA, and others where protecting the customer’s personal, medical, and financial information is paramount. Of course, to get the maximum benefits, users and organizations have to use the best encryption software.
What are The Disadvantages of Encryption?
In the vast majority of cases, encryption is beneficial for all parties involved. However, encryption also has limitations.
The most obvious disadvantage of encryption is the loss of decryption keys. If the data is encrypted and the decryption keys somehow get lost, then there is no way to access the encrypted data. For all practical purposes, the data is destroyed. That may not be a problem in certain situations where everything happens behind the scenes with apps on auto-mode. The other problem is the more encryption an organization uses, the more the number of secret keys to take care of. Some organizations make use of multiple keys for more security in case a given secret key gets lost which only adds to the overall complexity of any system. Organizations also have to spend more resources keeping track of all the secret keys and hackers away.
In some instances, encryption is only as strong as the passcode used for encryption. For example, iPhone devices do offer encryption services. But the user has to provide a passcode to set up encryption. Hence, the strength of the encryption depends on the strength of the passcode. Human passcodes and passwords are notoriously easy to crack which further reduces the effectiveness of encryption in places where a passcode can undo encryption for sensitive information.
A more technical disadvantage of encryption is restricted access. By design, encryption is supposed to restrict access to critical data. Organizations and individuals who do not plan well ahead before using encryption can end up encrypting too much information that may not be useful. That can make accessing routine data difficult even for administrators. As a result, an organization may be weaker than before when responding to emergency situations where accessing and reviewing data quickly is critical. As mentioned before, misplaced encryption keys or passwords can further slow down access to data.
Note:
To combat problems such as lost encryption keys, companies can implement elaborate backup systems. But creating and maintaining backup systems can give rise to new problems.What are The Different Types of Encryption Algorithms?
Every encryption method comes with a different logic that commands operations behind the scenes when scrambling data. Most of the encryption methods today make use of complex mathematical functions to scramble data. In the end, the encrypted data is, for all practical purposes, uncrackable (though that could change with the advent of commercial quantum computers in the very near future). In total, there may be over a hundred encryption algorithms in use.
The most common types of encryption algorithms in use are given below:
Data Encryption Standard (DES)
The DES encryption algorithm belongs to the symmetric class encryption methods. Data Encryption Standard is considered one of the earliest symmetric encryption algorithms developed by IBM. IBM wanted to protect intellectual property rights. To protect government data, unclassified records, and sensitive information, IBM developed DES, a standard that was adopted in 1977 by the government. At the core, the DES encryption algorithm makes use of a 56-bit encryption key. Horst Feistel is usually credited with the design of the Feistel Structure. The Feistel structure is what the DES encryption key is based on.
Note:
To convert plaintext co ciphertext, the DES encryption algorithm uses 64-bit blocks and applies encryption to each one. DES is almost extinct now as security researchers were able to find many problems with the encryption algorithm.Triple DES (3DES)
The triple DES encryption algorithm essentially means a triple data encryption algorithm. The Triple DES algorithm is an upgrade to the older DES algorithm. As mentioned before, the DES algorithm had certain vulnerabilities. The primary way triple DES overcame DES vulnerabilities was to apply the same DES algorithm to data thrice. Each block got encrypted thrice which improved security. The finance industry along with technology companies, standards, and payment services started to use the triple DES algorithm very quickly. The Triple DES encryption method was also employed in cryptographic protocols including OpenVPN, IPSec, SSH and TLS. But just as before, security researchers were able to find vulnerabilities within the triple DES algorithm as well. As a result, NIST and other industries including TLS 1.3 standard deprecated the 3DES algorithm.
Elliptical Curve Cryptography (ECC)
The Elliptical Curve Cryptography started to develop in the 1980s with help from two mathematicians Victor S Miller and Neal Koblitz. Both proposed using elliptic curves in the field of cryptography to secure data. The ECC algorithm really started taking shape (and finally got implemented) in 2004. As the name suggests, the ECC employed elliptic curves that represented points satisfying an equation. The ECC is a strong encryption algorithm for the simple reason that it allows for easy computation in one direction but almost impossibly hard in the reverse direction. A point that exists on a curve is symbolized by a number. The number gets multiplied by a different number. And the result of the multiplication gives a new number or a point on a curve. Since there is no easy way to know which point on the curve the new number belongs to, the ECC became one of the strongest encryption algorithms. Currently, the only problem with the ECC encryption algorithm is the lack of support from SSL and TLS. The ECC uses short encryption keys which means less computing power and network load. Such qualities should enable faster adoption in the coming future.
Advanced Encryption Standard (AES)

The AES or Advanced Encryption Standard protocol is considered one of the strongest encryption algorithms available today. Security organizations along with governments and big businesses use the AES algorithm for secure communication channels. Moreover, almost all elite VPNs exclusively use the AES encryption standard to protect user data packets. The AES encryption algorithm uses symmetric secret keys. That means, any receiver close to receiving any information needs to have the secret key in order to decrypt the message and read the contents of the message. Each encryption method makes use of a different technique to encrypt data. The AES standard uses single blocks for data encryption. Some algorithms encrypt individual data bits which can be a resource-heavy task. The size of the block that is used by AES is generally written in front of the term AES. Currently, the three most popular block sizes are AES 128, AES 192, and AES 256 (which means that each encrypted block is 256 bits). Of course, each AES encryption type uses different block sizes as well as the number of rounds used for complete encryption. AES 256-bit uses the most rounds with 14.
Diffle Hellman Exchange
Generally, the Diffie Hellman Exchange is considered the first popular encryption method to generate and exchange secret keys and make communications over insecure channels secure. Technically though, the Diffie Hellman Exchange doesn’t allow for key exchange. Instead, the keys must be jointly derived. The Diffie Hellman Exchange encryption algorithm was developed by Martin Hellman and Whitfield Diffle. Explaining Diffie Hellman Exchange is the easiest with the help of an example. For any secure communication, the sender and receiver have to agree on a prime number p that is large enough (in Diffie Hellman Exchange). The two parties also have to agree on a generator g which has to be less than the prime number p. The sender then has to use a secret integer A which acts as the private key of the sender. After that, the public key is generated. Both the sender and receiver have to generate public and private keys. Both have to exchange the generated keys according to another formula that enables all users to have a symmetric secret key for the purposes of encryption.
Quantum Key Distribution (QKD)
Currency encryption algorithms aren’t very good against quantum computers. Quantum cryptography offers a new type of encryption where two parties can share a secret key without anyone else intercepting communications. QKD requires the sender and receiver to use a total of four non-orthogonal quantum states. These quantum states are chosen from two bases. Then, a sequence consisting of various random states is sent to the sender via a quantum channel. From the two bases, one is used for sending information over the quantum channel randomly. On the public channel, both the sender and receiver can compare the bases used. Then coincident bases can be identified and the error rate calculated. If the error rate increases beyond a certain threshold, that is usually a sign that information was changed. The non-cloning theorem governs the entire process. Currently, other encryption methods such as AES are used in conjunction with QKD for optimal results.
Rivest-Shamir-Adleman (RSA)
Rivest Shamir Adleman is another widely used and very secure asymmetric encryption algorithm. As the name suggests, the algorithm was invented by Ron Rivest, Leonard Adleman, and Adi Shami in 1977. The RSA algorithm relies on the prime factorization method where two large prime numbers are randomly chosen and multiplied to create another prime number that is even larger. Without any reliable way to know the new prime number, RSA encryption is almost unbreakable. The key length used to generate prime numbers has to be large as well. Currently, even the fastest computers need thousands of years to crack even the weakest versions of the RSA algorithm.
What is Decryption? Why Is it Needed?
Decryption is the process that transforms encrypted data from an unreadable form back to plaintext where the contents are readable again thus undoing the encryption. The receiver of encrypted information needs to have the correct decryption tools and secret keys to decrypt encrypted information.
Decryption is needed to convert encrypted data back to a form where encrypted information can be useful. Decryption is also needed to complete the process of improving data privacy. Along with encryption, decryption secures sensitive information such as usernames and passwords along with confidential data. Decryption is also needed to ensure that information was not changed during transit or storage. Other reasons why decryption is needed include IP protection, keeping data safe from hackers who spy via network communications, and knowing that there is a way to access encrypted information (that no one else can access) at a moment’s notice.
How To Manage Encryption Keys Safely and Securely?
The most common ways to manage encryption keys safely and securely include not hard-coding keys in the software to guard against possible unauthorized recovery, limiting encryption keys to a specific and single purpose only, investing in a comprehensive key management system, using white-box cryptography for more key protection, and opting for hardware-based security modules for key protection where possible.
What is the history of Encryption?
The history of encryption starts with hand-coded encryption in the early part of 800 BC right up to the 1500s. Modern encryption is done by algorithm machines. Such machines store all the information that needs protection and offer tools to manage communications safely. The defining moment of modern encryption probably came in 1945 via a series of research papers written by Claude Shannon. Shannon described perfect security that attacks could not break even with great resources. Computer technology gave way to further development in the field of cryptography. With advances in computing devices, algorithms, and better mathematical equations, modern encryption algorithms such as symmetric and asymmetric were born for encrypting and decrypting data.

