Domain Name System (DNS) is the IP Address recording system to help people to navigate a certain IP Address by browsing. A request to a website will cause a response from a server via Domain Name System. Every website has a DNS that helps website visitors to navigate via IP lookup.
Any device or web server that has to connect to the internet must have an IP address. All websites and apps have IP addresses as well. And since humans cannot remember the IP addresses of the websites they have to visit regularly, the Domain Name System (DNS) steps in to look up the IP addresses behind the names of popular websites.
DNS security is all the steps organizations and individuals need to take to protect the DNS protocol from hacking attempts. The inventors of DNS did not develop the system with security in mind, underscoring the need for robust security measures. Cybercriminals can exploit DNS vulnerabilities to disrupt the communications of both individuals and organizations.
DNS has also become important amid the rise in remote work and the digitalization of everyday tasks. This has attracted even more hackers to attempt disrupting DNS to destabilize online interactions, leading to damages.
This security guide will explain important DNS security terms, common DNS problems and threats, and effective prevention strategies.
Table of Contents
What Does DNSSEC Mean?

DNS Security Extension or DNSSEC represents the set of protocols that provide an extra layer of security to the DNS system.
The method used by DNSSEC enhances authentication processes in DNS. DNSSEC uses techniques such as public-key cryptography and digital signatures to achieve more security and accuracy—in terms of landing users on the website requested instead of a different site or a compromised one.
How DNSSEC Works?

DNSSEC takes advantage of public-key cryptography techniques to secure DNS processes. Many cyberattacks start by redirecting unsuspecting users to malicious websites. Once the user inputs login credentials on the fake site, hackers can steal login information, credit card details and other financial data. DNSSEC effectively prevents hackers from doing this and ensures users get to the websites and services that were initially intended.
There are many ways to describe a DNS, but the comparison to a lookup service is arguably the most fitting. DNS services direct users to the websites that users request. DNS zone file data ensures users in any part of the world are able to connect to any website globally. DNSSEC protects these DNS zones via public and private keys. Once a match is made, DNSSEC validates the DNS data authenticity with digital signatures.
DNSSEC also guards against DNS resolvers from landing users on malicious websites. With DNSSEC in place, DNS resolvers only point users to genuine IP addresses behind popular websites.
As mentioned, DNSSEC makes use of public and private keys to protect DNS services from corruption. Each domain name owner has a private key. When a user wants to go to a specific website, the user inputs the URL of the website into the web browser’s URL bar. This is where the user is requesting DNS data from the website, and the website’s domain owner signs the DNS data with the private key.

Then, the recursive DNS server checks registry records for the presence of a public key related to the signature. If the public key and private key combination match is successful, the user receives the DNS data that opens access to the service or a website. If the public and private keys do not match due to the presence of DNSSEC, the DNS data is assumed to be corrupted or forged.
The aim of using public and private cryptographic keys to sign DNS data is to make sure that when users want to go to a website, the browser takes users to the original website and not a compromised version. An authenticated DNS result is more likely to be valid, and this is what DNSSEC ensures.
This is important:
DNSSEC introduces several new types of DNS records so that new protocols don’t have trouble providing extra protection. These include NSEC(3), which stores records for denial-of-existence; DNSKEY, which stores public signing key; DS, which stores hash of the DNSKEY; and RRSIG, which stores cryptographic signatures associated with a record set.What Is DNS?

Domain Name System (DNS) is a system that enables users to connect to the specific websites that users want to visit. To do that, DNS matches the domain name of a given website with the IP address that’s unique to the said website. Think of DNS as a phone book containing the phone numbers of all the websites in the world.
Since a website is stored on a server, which in turn is connected to the internet and has an IP address, each website has a unique IP address. It is the DNS’s job to match the website’s IP address with the domain name of the website (provided by the user via the web browser’s URL bar).
What Is the Difference Between DNSSEC and DNS Security?
The difference between DNSSEC vs. DNS security is that DNSSEC refers to the new protocol ensuring the validity of DNS queries, data and results with the help of cryptographic signatures. DNS security refers to the concept that organizations, companies, users and services can use DNS to secure networks.
How DNS Works?
DNS stores the IP address of all the websites in the world and their matching domain names, which contain alphabet letters instead of a string of numbers (as is the case with IP addresses, which are hard for humans to remember).

Whenever a user inputs a domain name in the URL bar of a web browser, the DNS completes the job of translating the domain name into its matching IP address. Then, the DNS sends that data back to the user’s device, and the user can connect to the desired website and consume content.
Note:
There are many methods to configure and optimize DNS, depending on the needs of the individual or organization. But one method that works for everyone and improves DNS performance is to change the default DNS server that completes the task of doing the lookups. Fortunately, the market offers several free options that individuals and small organizations can use as DNS servers.Changing network settings to use the DNS servers of popular services is a good first optimizing step. Regardless of the operating system, one can make use of the OpenDNS server by changing the IPv4 address to 208.67.222.222 or 208.67.220.220. For IPv6 address, the options are 2620:119:35::35 or 2620:119:53::53.

Google also offers its Google Public DNS service for which the IPv4 address is 8.8.8.8 or 8.8.4.4.
Finally, Cloudflare also offers DNS servers. To use Cloudflare, the IPv4 address should be 1.1.1.1 or 1.0.0.1. The IPv6 address should be 2606:4700:4700:::1111 or 2606:4700:4700::64.
Users and companies should use different DNS servers to see which ones perform better under different situations. DNS performances are affected by the DNS server one uses and the connection type, location, and filter requirements. Optimizing DNS settings may also include using DNS over HTTPS and DNS over TLS for more security.
What Is the Difference Between Public DNS and Private DNS?

What is a public DNS and what is a private DNS? Public DNS refers to the global hierarchical structure of DNS servers, while private DNS refers to the DNS server hierarchy that only exists on a private network.
Private DNS servers usually serve a company or organization. To maintain proper security and privacy, no user from outside the private network should have access to these servers.
Internet service providers offer businesses and individuals access to public DNS servers. Public DNS servers contain records of all domain names pointing to public websites. Any device that has access to the internet can use public DNS servers to reach any website on the internet.
Private DNS primarily serves companies and organizations by maintaining records of all related internet websites. Private DNS servers usually have a firewall guarding against unauthorized access.
Public DNS servers offer services to anyone with a device and internet connection. Private DNS servers mainly serve employees who need access to company resources via internet services and websites but don’t want to do so through IP addresses alone.
Some organizations can use both private and public DNS for better security and service.
Why Is Security Needed in DNS?

Security is needed in DNS to stop hackers from corrupting DNS data and serving users counterfeit results. Proper DNS security guards internet clients against such problems. Security is also needed to validate DNS data by verifying digital signatures.
Without proper security in DNS, there would be no way to ensure that the DNS records users have received have come from a genuine and legitimate source. Without security measures, hackers could easily redirect users coming to a given domain name or even take over the domain name entirely.
This may be insignificant for a small-scale website that ranks movies based on votes, but it is a big deal for a banking website. Companies that serve customers and employees through websites can lose a lot of business if the website goes down or redirects customers and employees to something they aren’t looking for.
Warning:
Without proper security, companies would face serious DNS issues that could damage digital services beyond repair.Is DNS Secure?

DNS is secure provided that the party controlling the DNS server is authentic and legitimate. If a hacker controls a given DNS server and the user selects that DNS server to send back DNS data, there’s a chance the user might be redirected to compromised versions of legitimate sites.
Every year, hackers are able to victimize online users with phishing sites, malware and other types of scams by compromising DNS servers and redirecting users to malicious websites and services. Without advanced encryption and other security protocols, DNS servers are susceptible to cyberattacks that corrupt DNS records and launch man-in-the-middle attacks.
If a DNS server does not have an authentic controller, that’s a significant security risk as well. Google controls Google Public DNS servers, so such DNS servers can offer good speed and security. However, the weakness of this service is that Google may record the user’s internet history for its own objectives.
Note:
DNS servers without proper security are very vulnerable to DNS-related attacks such as DNS spoofing and DNS cache poisoning.Which Are the Safest DNS Servers?
The safest DNS servers are given below.

- Google Public DNS servers are highly secured and take care of user privacy. Google also ensures the inner workings of these public DNS servers are transparent. The only downside is that Google Public DNS servers are more suited to experienced users. Also, in the future, Google may try to use data it collects via its public DNS servers for advertising purposes.
- OpenDNS offers some of the best public DNS servers for free. OpenDNS also provides a Family Shield DNS server plan that families can use to block adult content to keep their children safe online. Additionally, OpenDNS has specialized servers for both small and large companies. Configured properly, OpenDNS can prevent access to inappropriate, offensive and malicious websites. For the extra productive lot, OpenDNS can also get rid of time-sucking sites. However, the problems with OpenDNS servers are obvious, namely that the service stores browsing activities and IP addresses for enhancing user experience and personalization. That can be a significant drawback for privacy-conscious users.
- Cloudflare is commonly viewed as the best public DNS server provider. By some measures, Cloudflare offers the highest levels of performance and privacy controls, along with a vibrant support forum run by a supportive community where beginner and experienced users can get help setting up DNS servers correctly on their system. Cloudflare does not store user data or serve users any type of ads, which is why the service routinely ranks as the fastest public DNS server. For the extra privacy-conscious online users, Cloudflare has even undergone an independent audit by KPMG to prove the service delivers on all its claims. The paid subscription plans can get expensive, though.
- ComodoDNS is very simple to use and configure. All users have to do is change their network adapter settings to use Comodo DNS servers. Comodo DNS offers subscription plans offering extra features such as malware protection, encryption and content filters. The only problem with Comodo DNS is that the free tier is a bit too restrictive and does not have access to many essential features.
- Quad9 is the newest public DNS server provider out of the bunch mentioned here. Quad9 offers great performance, decent speeds and can automatically block domain names that try to infect users with malware. The only problem with Quad9 is the lack of tutorials for the latest versions of macOS and Windows. Some users have mentioned that Quad9 can be inconsistent with its speeds, especially for North American queries.
Why Do We Need Security in DNS?

Security in DNS is needed to add an extra layer of security between the public internet and the end-user. Proper security in DNS can block dangerous websites and establish content filters to keep harmful content away from the online community. DNS security also reduces malicious cyberattacks and many other online risks.
Without security in DNS, the process of filtering content to keep phishing attempts in check would be very difficult. If users can’t get to phishing links due to content filtering, that would automatically decrease the number of successful phishing and malware attacks.
A robust security system in DNS would also eliminate the need for organizations and users to install additional software to filter content and malicious sites effectively. Some clients want to simultaneously stay protected from malicious attacks and reduce the number of unwanted advertisements. A well-configured content filtering mechanism can block advertisements from directing clients to malicious websites and collecting user data.
Note:
Another reason why security in DNS is needed is its ability to reduce the chances of a successful botnet attack. The number and types of smart devices have increased manifold in recent years, and hence protection against botnet attacks has become paramount. Security in DNS can take note of obvious botnet servers and prevent user devices from forming a connection with botnet servers.
If internet service providers’ DNS servers do not offer proper security, this also increases the chance of a slow internet experience. Secure DNS services offer high performance and good reliability compared to unsecured ones.
Security is also needed in DNS to stop malicious attacks that take advantage of typos. When a user inputs a wrong URL in the browser’s URL bar, an error page usually appears. But hackers can purchase the incorrectly typed domain names and hack users who accidentally land on such malicious URLs because of a typing error. A properly secured DNS server would automatically detect obvious URL mistakes to stop users from connecting to malicious webpages.
What Are the Common DNS Security Threats
The common DNS security threats are given below.

- Distributed Denial of Service (DDoS) Attacks: A broad category of attacks that aim to overload and clog networks.
- Amplification Attacks: A type of DDoS attack where hackers use public DNS servers to overwhelm the target network or website with DNS traffic.
- DNS Spoofing: A type of cyberattack in which hackers modify DNS records and redirect users to malicious versions of legitimate websites.
- DNS Tunneling: A cyberattack type that exploits the DNS protocol to introduce malicious data stealthily through a company’s defenses.
- DNS Hijacking: This happens when hackers compromise responses to DNS queries so they are not resolved correctly and redirect traffic to malicious websites.
- NXDOMAIN Attack: A type of DDoS attack where attackers flood a DNS server with DNS queries to domain names that do not exist.
- Phantom Domain Attack: Another cyberattack where attackers disrupt communications by forcing the victim’s DNS resolver to resolve phantom domains that do not respond back, hence slowing down the process.
- Random Subdomain Attack: A cyberattack where hackers flood the victim’s DNS server with DNS queries for subdomains that do not exist, leading to the depletion of the victim’s DNS server.
- Domain Lock-up Attack: A type of DDoS attack where hackers set up malicious resolvers and domains that disrupt the handshake process between a client and a server.
- Botnet-based CPE Attack: A type of botnet attack where hackers compromise CPE devices such as modems and cable TV boxes and make these devices part of a botnet to launch attacks against another website or service.
1. Distributed Denial of Service (DDoS) Attacks

Distributed Denial of Service (DDoS) attacks occur when hackers bring down websites and other online services by overloading their networks with high volumes of fake traffic. The extra fake traffic to overload servers can come in many forms, including spam messages, fake data packets or connection requests.
Hackers use the method of overwhelming the target website’s servers or company network with traffic that the server or network can’t handle. Once an overflow happens, the network or server goes down and the target website becomes inaccessible.
Hackers can also use botnets to generate HTTPS floods, where hacked devices send HTTPS or HTTP requests to a web server. The requests can take the form of a GET request or a POST request. Both consume the web server’s resources, which could have been used to respond to legitimate requests.
In the end, the botnet causes the victim’s website to go down. The harm mainly comes in the form of increased downtime and fewer visitors, which translates to lost business.
For prevention, there needs to be a comprehensive monitoring system that keeps track of traffic at all levels and for all IP addresses. Having a plan on how to handle denial of service programs is also very important. Network resources should have their own security protocols. Detecting and blocking DDoS links via router filters and firewalls is another helpful way to prevent DDoS attacks. Re-routing the fake traffic to a nonexistent IP address can also redirect the DDoS attack.
2. Amplification Attacks

Amplification attacks are a type of DDoS attack in which hackers exploit DNS server vulnerabilities to transform small connection requests into huge payloads. Amplification attacks are also a form of reflection attacks, where hackers exploit DNS resolvers to overload a given network or server with amplified traffic. This causes the target infrastructure, including the server itself, to become inoperable.
Hackers make small DNS requests to public DNS servers and spoof the source address (to which the DNS servers will send the response) to the target’s IP address. Once hackers manage to spoof the source IP address from where the DNS request originated (and change it to the victim’s IP address), the DNS server in question sends the response back to the victim’s spoofed IP address instead of the device that sent the request.
Using automated tools, hackers can use thousands of devices to send thousands of requests to multiple DNS resolvers and then have the response (much bigger than the initial request) go to the victim’s device. With a sufficient number of requests, the bandwidth sent towards the victim’s device can be amplified to the extent that the target device clogs.

The harm, again, comes in the form of downtime for a website or service, which leads to loss of business, customers or workflow.
For prevention, since amplification attacks exploit DNS resolvers, these resolvers should be configured properly and only serve devices coming from a trustworthy domain. Internet service providers can also help guard against botnet attacks by stopping traffic sourced from spoofed IP addresses since, for a successful amplification attack, hackers have to modify the source IP address to the victim’s IP address via spoofing. DNS servers can install tools that can scatter a given amplification attack so the extra fake traffic can’t disrupt operations.
3. DNS Spoofing

DNS spoofing is a type of cyberattack that redirects internet traffic away from a genuine server and to a compromised one by exploiting the security vulnerabilities found in DNS servers.
There are multiple methods to carry out DNS spoofing attacks, but exploiting a DNS server is one of the most common techniques. Corrupting a DNS cache also works. Assuming hackers can access the target network, a simple man-in-the-middle attack can also help with DNS spoofing. Fabricating a DNS server on a given network and guessing sequence numbers can also help with DNS spoofing.
Using the DNS cache poisoning method, hackers substitute a local DNS server with a malicious one. Upon sending a request, the user gets connected to the malicious DNS server instead of the original DNS server. As a result, the malicious DNS server redirects the user to a compromised website or service. Sometimes, hackers can also take advantage of the DNS cache and inject false DNS records. Another method to carry out DNS spoofing attacks is to corrupt the IP information and packet ID when the user sends a DNS request to a server or DNS resolver. The target user’s device will accept the corrupted data packet from the DNS resolver because the response ID matches the request ID.
DNS spoofing attacks can lead to censorship and a lack of security updates. DNS spoofing also leads to malware infection and stolen data.
Prevention techniques for website administrators and DNS servers include end-to-end encryption along with advanced detection tools and DNSSEC implementation.
Tools such as Registry Lock can protect DNS records and stop malicious alterations. Tools for monitoring internet traffic and controlling how applications access data can also help.
This is important:
End-users should avoid clicking on malicious links and double-check the website if the task at hand is sensitive. Regularly running scans can also guard against malware. Deleting the DNS cache and using a VPN service can help against DNS spoofing as well.4. DNS Tunneling

DNS tunneling is a form of cyberattack where hackers are able to route DNS requests to compromised DNS servers.
The method used to perform DNS tunneling attacks is to first compromise a user’s device and then download a malicious payload on the device. Then hackers aim to establish a C2 connection with the target device. To achieve that aim, hackers want the user to send DNS queries to the compromised DNS server they have set up. The actual DNS tunneling hides within the data for DNS queries.
The harm of DNS tunneling is that hackers can essentially monitor everything that happens on the device. Hackers can steal data and then sell it on the dark web. Hackers can also use the DNS tunnel to check which websites the user has visited and even carry out other cyberattacks.

To prevent a DNS tunneling attack, a monitoring system should be installed to track suspicious IP addresses and domains, combined with services that keep a record of malicious IP addresses, servers and domains.
Since DNS requests are generally able to pass firewalls easily, proper configuration of the DNS firewall is a must. DNS firewalls should be able to identify suspicious behavior and look out for pathways that exfiltrate data from the target device. Tools should be installed to identify data extraction techniques and destinations that process such data. Another set of tools should be installed to block such destinations.
5. DNS Hijacking

DNS hijacking happens when hackers compromise the target user’s DNS traffic via a malicious DNS server that returns fake IP addresses as responses to the user’s DNS requests for specific domains.
There are many methods of carrying out DNS hijacking, but most take advantage of either malware or a hacker-created malicious DNS server or a legitimate but compromised DNS server.
Using the malware method, hackers can infect the target user’s router. Then, hackers alter the DNS settings so that the router uses the hacker-created DNS server instead of the DNS server picked by the target user’s ISP. Once a user inputs a URL in the web browser’s URL bar, the malicious DNS server would take the user to a malicious version of a trustworthy site. For example, the server could land the user on “gogle.com” instead of “google.com.”
The method of using rogue DNS servers involves hackers setting up DNS servers and then changing specific database entries on those DNS servers. When users query a domain name, the hacker-owned DNS server sends customized IP addresses instead of legitimate ones.
Setting up DNS servers can be too bothersome for some hackers, so hacking legitimate DNS servers helps get around that problem. Once through a DNS server’s defenses, hackers alter specific IP addresses present in the legitimate server’s database. Once users query these genuine DNS servers, the users are directed to hacker-preferred websites instead of the intended ones.
The harms of DNS hijacking include stolen personal and financial information. Hackers can also launch phishing and other malicious attacks via the compromised websites users land on due to DNS hijacking.
For prevention, users should make use of anti-phishing web browser extensions and script blockers. DNS resolvers that can support DNSSEC should implement DNSSEC as soon as possible. But individual users need to access a DNS resolver and have a home network before implementing DNSSEC.

Modern anti-virus and anti-malware products can also protect against DNS hijacking by warning users when landing on a malicious or phishing website. Regularly changing DNS servers is another way to make sure hackers can’t pin down a user’s routine. Cybercriminals usually go after ISP-provided DNS servers a lot more than public DNS servers from providers such as Cloudflare or Google.
Not connecting to public WiFi always helps, as there is usually no encryption present on such connections, and the user can’t know the DNS server working on the available network.
Users who can’t afford to go without a public WiFi network can use a VPN service to guard against DNS hijacking attempts. VPNs hide IP addresses, which are what hackers need to start monitoring traffic and potentially harm users.
6. NXDOMAIN Attacks

In NXDOMAIN attacks, hackers overwhelm a target DNS server with invalid DNS record requests. DNS resolvers suffer the most from NXDOMAIN attacks.
In NXDOMAIN attacks, hackers try to engage authoritative DNS servers and DNS proxy servers with invalid requests. At a big enough scale, such a cyberattack generates NXDOMAIN error responses and the DNS server experiences latency issues. In the end, the sheer amount of invalid requests sent to the target DNS server leads to significant performance issues. The DNS requests themselves point to non-existing domains, which also causes problems like DNS recursion.
The harms of NXDOMAIN attacks are many since the target DNS server cannot serve legitimate requests as all of the DNS server’s hardware and software resources are used up by the invalid DNS requests. The target DNS server spends all its time trying to resolve the invalid DNS requests until the DNS server’s whole cache fills up with NXDOMAIN failure errors.

ISPs also know that once the DNS server can’t find the IP address for the hacker-generated DNS requests, the server will return an error message. So, ISPs manipulate the returned message by directing such requests to other DNS servers that may show users unwanted ads. In other words, ISPs can exploit invalid requests.
To prevent NXDOMAIN attacks, server administrators should allow the server to store cache information for longer when the server receives valid DNS requests. Doing so allows the server to serve genuine DNS requests while hackers attempt to flood the server with fake requests. With the cache information in place, the server has to expend fewer resources to respond to the DNS request.
This is important:
Systems should be put in place to detect servers and domains that act suspiciously or are on some sort of malicious list. Blocking such servers and domains means the server can use resources more effectively.7. Phantom Domain Attack

A phantom domain attack involves hackers creating multiple ghost domain servers or phantom domain servers. When these servers get requests, these servers respond to those DNS requests either too slowly or not at all. After that, hackers try to overwhelm the target DNS resolver with DNS requests to the phantom domains. And since the phantom domain servers are not going to respond in a timely manner, the DNS resolver keeps waiting for a proper response while consuming resources. Over time, the phantom domain attack leads to lower levels of performance. In extreme cases, phantom domain attacks lead to DoS attacks as well. Other harms include system shutdowns and clogged networks.
To prevent phantom domain attacks, server administrators should put a hard limit on the number of recursive requests made successively on a given server. Zone limitations can also guard against phantom domain attacks.
To further prevent phantom domain attacks overwhelming the system, administrators should take note of non-responsive servers and enable the hold-down feature for the DNS server under attack or potential threat. By enabling the hold-down feature, the DNS server can limit the attempts the DNS server makes with unresponsive servers.
To reduce the impact of phantom domain attacks, a greater number of recursive servers can also help as more servers can share the extra requests between them.
8. Random Subdomain Attack

Random subdomain attacks are attacks where hackers flood DNS servers with requests for domains (more specifically, sub-domains of a given legitimate domain) that do not exist.
The method is essentially the same as that of phantom domain attacks, only this time, instead of the domain being slow or non-response, the domain simply does not exist.
Normally, when a user tries to go to a website like google.com, the www.google.com server would respond to an access request since the domain actually exists. However, if a user or a hacker removes the “www” part in “www.google.com” and replaces it with “xyzd” or any other random string, the recursive DNS server will keep on expending resources to find the xyxd string from Google’s authoritative servers in a recursive context.
The end result in such a situation would be the aforementioned NXDOMAIN response error. The target DNS server would keep storing these responses in the negative cache. Hackers could then change the “xyzd” part multiple times so that the authoritative servers respond with a recursive query and keep filling up their negative cache with the NXDOMAIN response error. Random subdomain attacks also consume recursive contexts that eventually cause performance losses on the part of the target DNS server.

Prevention methods include using DNSSEC for server operators and having lots of DNS servers that can distribute the flood of bad requests. A nameserver with lots of reserve resources can handle all types of volume-based attacks, including random subdomain attacks.
Random subdomain attacks can also be prevented by limiting traffic rates from various source and destination IP addresses. Blocking requests based on keywords can also help.
9. Domain Lock-up Attack

In domain lock-up attacks, hackers set up custom domains and DNS resolvers to form TCP connections with genuine DNS resolvers. If a genuine DNS resolver sends a request to these hacker-created resolvers and domain servers, they respond slowly and with junk packets that consume the connection resources of the genuine DNS resolver.
Since the appropriate response is never going to be sent by the hacker-owned DNS resolver, the genuine resolver or server remains engaged, waiting for a response. As mentioned, this bogs down the system and consumes available connections.
The DNS domain lock-up attack is a bit like a TCP SYN flood attack in that both exploit the TCP handshake process to take up reserve connection spots available with the target DNS server.
Usually, a DNS client sends a synchronize or SYN message to a DNS server. The DNS server responds with an ACKNOWLEDGE message, also known as SYN-ACK. Then, the DNS server waits for the DNS client to send the ACK message back. Hackers slow down this process and send ACK messages to the DNS server faster than the DNS server can respond. The hacker-created domains also send random data packets to overload the target DNS resolver. And since the DNS resolver can’t respond with the same speed, it can’t resolve the TCP handshake process.

The main harm of domain lock-up attacks is the lack of connection opportunities for genuine DNS requests from users.
Enabling DNSSEC on a DNS server that supports DNSSEC is a good step to prevent domain lock-up attacks. Keeping all operating systems and software performing any tasks related to the DNS server updated is a must as well. The latest security patches usually address DNS attack problems. Enabling two-factor authentication and generating security codes on the domain account also helps.
Note:
Sometimes, keeping recursive servers completely separate from authoritative servers can prevent hackers from compromising the recursive server. Blocking DNS output and limiting connections is also a good starting point.10. Botnet-based CPE Attack

Botnet-based CPE attacks happen when hackers compromise a CPE device and create a botnet to perform further attacks on target domains and websites.
The main method of launching botnet-based CPE attacks is to compromise a bunch of CPE devices such as routers, modems and cable boxes (via methods such as malware attacks, phishing attacks, Trojan injection or email attacks) and then have them become a part of a network known as the botnet. Hackers then use the botnets to carry out malicious activities.
The main harm of a botnet attack is the loss of uptime, which leads to loss of business. Botnet attacks can also lead to email spamming, cryptocurrency mining, infecting devices with advertisements and popups, stealing information, generating artificial traffic and committing advertisement fraud.
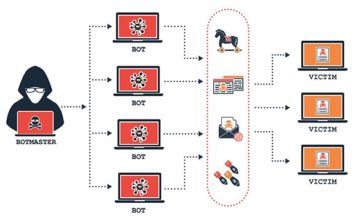
In the context of DNS attacks, though, botnets can perform random subdomain attacks where lots of compromised devices would send DNS queries of a genuine website’s subdomains that do not exist. As a result, the authoritative nameserver of the target domain or website gets bogged down and can’t respond to legitimate DNS requests for the target domain from other DNS clients.
For prevention, typical measures against botnet attacks and DNS attacks usually work. Keeping everything updated, using a VPN and using advanced security options with DNS resolvers can help.
DNS resolvers now support features such as content filters, malicious website blockers and botnet protection. Some DNS resolvers even keep a record of known botnets and spam-generating websites and hence block requests from them.
What Are the Best DNS Protection Methods?
The best DNS protection methods are given below.

- Follow best practices governing how to prevent DNS attacks.
- Enable two-factor authentication to guard against DNS zone compromise.
- Use third-party DNS servers from Cloudflare or Google.
- Secure DNS servers with DDoS mitigation techniques provided by Akamai, Incapsula or Cloudflare.
- Use dedicated DNS services only (preferably an isolated DNS server).
- Filter traffic via a firewall.
- Close unneeded server ports.
- Disable DNS recursion.
- Limit DNS zone transfers to a few IP addresses.
- Obscure BIND version.
- Keep all programs and systems up-to-date, including NSD, PowerDNS, BIND and Microsoft DNS, in addition to the operating system.
- Enable DNSSEC and RRL.
What Is a DNS Firewall?
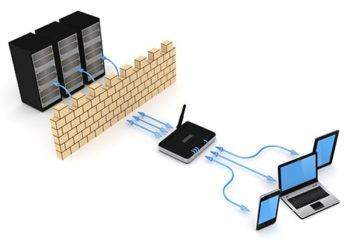
A DNS firewall is a security tool that acts as a protective shield and monitors internet traffic while filtering it to make sure users do not get into contact with malicious websites. DNS firewalls make use of intelligence threat feeds with DNS protocols and work at the application level. This is the best solution to enhance security in end-to-end encryption communications.
DNS firewall is currently the most reliable way to block a given user’s access to dangerous websites and protect users from malicious hackers trying to steal data and use up computing power.
Home users, small organizations, medium organizations and companies need DNS firewall protection because this tool not only protects against hackers but also results in bandwidth savings. DNS firewalls ensure longer uptime and maximum service availability.

As mentioned, DNS firewalls use intelligence threat data for enhanced protection and increased network visibility, inevitably making it easier for security personnel to separate infected devices and manage external threats if a hacker breaks into the network.
DNS firewalls have also become important because they can serve stale content to users and keep the website online in a scenario where DNS servers get knocked out.
More consideration should be given to DNS firewalls because they can hide IP addresses and offer granular control over connections to the website or network in question. All of these benefits make it difficult for hackers to track down potential targets.
What Are the Types of DNS Queries?

A DNS query refers to the information request that a user sends to a DNS server. The user’s device is referred to as a DNS client, and a DNS query is also known as a DNS request.
The types of DNS queries are given below.
- Recursive DNS query refers to the DNS query that can make an attempt to obtain the IP address of the requested domain simply by asking the name server. The name server can complete the translation recursively.
- Non-recursive query refers to a DNS query where the DNS resolver already has an answer to the DNS request and can complete the request quickly.
- Iterative DNS query is when the DNS client can form a connection with the specific DNS server that can complete the DNS lookup.
Are DNS Queries Private?

DNS queries, by default, are not private since these queries and the associated answers do not have any kind of protection. Regular DNS queries also do not have access to encryption technologies that improve privacy and security.
Regardless of which application is trying to resolve a domain name, a software library usually completes the job of converting domain names to IP addresses. That library uses a recursive DNS resolver to get the IP address desired.
Another consideration is that the application cannot control whether or not the DNS resolver uses security and privacy tools. Software libraries can usually implement such measures. But if they don’t, DNS queries are not private.
This is important:
Most users rely on the DNS resolver provided by the internet service provider for convenience and speed. Those benefits can come at the cost of security and privacy since the ISP’s DNS resolver may not implement privacy measures. And if the ISP doesn’t, malicious actors can profile or interfere with the user’s internet activity.Another reason why DNS queries are not private is because of the nature of the DNS. The DNS is unencrypted by default. A malicious actor, internet service provider or another member on a WiFi network can sit between the DNS resolver and the user’s device to eavesdrop on the data packets and even alter responses and DNS requests.
What Is DNS Over TLS?

DNS over TLS is one of the stronger security protocols that uses TLS to secure connections with DNS servers.
DNS over TLS has become very important because simple DNS gives plenty of opportunities to internet service providers, network administrators and hackers to steal information and launch cyberattacks. DNS over TLS, however, closes several attack vectors that have become common in the modern internet age.
With DNS over TLS, internet service providers can’t know which websites a given user is visiting at any given moment. More and more apps, especially on the Android platform, are starting to use DNS over TLS to secure communications and keep DNS data private. Google DNS servers also support DNS over TLS.
What Is DNS Over HTTPS?

DNS over HTTPS is another DNS encryption protocol that takes advantage of the security enhancements provided by HTTPS. Using DNS over HTTPS, DNS servers can complete DNS resolution jobs by using the HTTPS protocol.
DNS over HTTPS encrypts all DNS queries and their responses. But instead of using UDP to send data, DNS over HTTPS uses HTTP/2 protocol.
DNS over HTTPS has also become important as an alternative to DNS over TLS or DoT. DoH or DNS over HTTPS prevents hackers from modifying and forging DNS traffic.

Privacy-conscious users need to know about DNS over HTTPS because internet service providers have every opportunity to watch users’ DNS queries and the associated responses and then record such DNS data to profile users.
Modern browsers have started adopting DNS over HTTPS as well because web browsers have a business interest in protecting users.
DNS over HTTPS changes the way cybersecurity teams conduct everyday operations. Government bodies also have to look at how DNS over HTTPS affects people. Internet service providers know they will have to provide users some level of privacy surrounding their DNS data, and DoH is the simplest way to do it at the moment.
Apart from these, operating system vendors and public interest groups have started to pay more attention to DNS over HTTPS since privacy and security issues are no longer optional subjects of discussion in the digital landscape.

