DDoS (distributed denial-of-service) is a DoS cyberattack in which several hacked systems target a single system to render the target system inaccessible to users. DDoS attack tools are commonly used to transfer small quantities of data over several connections to keep access points on a targeted server open for as long as possible. These tools consume the provider’s resources until there is no ability to support more connections.

According to a 2017 study, the average cost of a DDoS attack for a small to medium-sized organization is roughly $120,000. And a big corporation could end up paying more than $2 million for an attack. However, these rates were marginally lower in 2020, with SMBs spending roughly $100,000 and big companies spending $1.6 million. In Europe, a typical malware attack costs $300, whereas a targeted DDoS attack costs as little as $10 per hour or $60 for 24 hours. DDoS attacks grew beyond 278% in the first quarter of 2021 compared to the first quarter of 2019 and more than 542% in 2020.
These are the 10 best DDoS attack tools.
DDoS attack tools are available as free tools and premium DDoS attack tools.
The top selected DDoS attack tools are listed below.
- Fastest DDoS Attack Tool: SolarWinds Security Event Manager (SEM)
- Cheapest DDoS Attack Tools: All the following DDoS attack tools are available as free downloads:
- HULK
- Torshammer
- Slowloris
- XOIC
- DDOSIM
- RUDY
- PyLoris
- Low Orbit Ion Cannon (LOIC)
- GoldenEye
Table of Contents
1. SolarWinds Security Event Manager (SEM)

SolarWinds Inc. is a United States-based software company that helps companies manage their networks. Donald Yonce, a former Walmart executive, and his brother, David Yonce, co-founded the company in Tulsa, Oklahoma, in 1999. TraceRoute and Ping Sweep, SolarWinds’ first products, were published in March 1998. In November 2001, the firm released its first web-based network performance monitoring program.
As of December 2020, SolarWinds had around 300,000 customers, including Fortune 500 corporations and some federal agencies. SolarWinds split its management service provider operations from the principal firm in July 2021.
This is important:
SolarWinds Security Event Manager is a virtual security information and event management (SIEM) software program that improves the efficiency of controlling, regulating and tracking security practices and protections on an organization’s network.SolarWinds is the first on this list because the program is the fastest DDoS attack tool out of all the others mentioned. SolarWinds offers automatic mechanisms for generating notifications, restricting IP addresses and shutting down accounts. Checkboxes can be used to configure the options in the device.
SolarWinds encrypts and compresses the logs and events before storing them in an unalterable read-only mode.
2. HULK

HULK (HTTP Unbearable Load King) is a web server-based DoS attack tool that was made for research. Invented by security developer Barry Shtieman, HULK could drive a Microsoft IIS 7 virtual server test system using a single host in less than a minute.
HULK is a denial-of-service program that generates distinct and encrypted traffic volumes to attack web servers. The traffic generated by HULK avoids buffering engines and goes straight to the server’s immediate resource pool.
Shteiman has included a variety of capabilities in HULK to mislead the target web server as thoroughly as possible, including the ability to mask the actual user agent and complicate the originator for each request.
With a unique ability to disguise users, HULK is regarded as one of the best DDoS tools on this list.
HTTP can avoid the cache engine, resulting in unique and encrypted traffic. However, the tool also causes a significant amount of load on the website.
3. Torshammer

Phiral.net created Torshammer, a slow-rate HTTP POST (Layer 7) DoS tool. This tool made its initial public appearance in early 2011.
Torshammer launches a DoS assault by employing a traditional slow POST attack, in which HTML POST fields are sent at a slow rate inside the same session between 1,000 and 30,000 seconds.
Like the RUDY (R-U-Dead-Yet) tool, the slow POST attack causes web server application units to wait for the end of endless posts before processing. This depletes the web server’s resources, resulting in a denial-of-service situation for any valid traffic.
Running the tool through the Tor network has the extra benefit of concealing your identity.
4. Slowloris

Robert “RSnake” Hansen created Slowloris, which was first published on June 17, 2009. Slowlorises, a tribe of monkeys known for slow mobility, inspired the program’s name.
Slowloris, which is 36kb in size, has demonstrated effectiveness against various prominent web server software, including Apache 1. x and 2. x.
Because the attack is carried out at a sluggish rate, traffic can be easily identified as irregular and blocked. Also, by creating and maintaining multiple simultaneous HTTP connections between the hacker and the victim, Slowloris allows an attacker to overwhelm a targeted server.
PyLoris, a protocol-agnostic Python implementation supporting Tor and SOCKS proxies, has a similar efficiency with Slowloris.
5. XOIC
The XOIC application is named after the ion cannon, a fictitious weapon featured in numerous science fiction books, video games, and, most notably, the Command & Conquer series. The creator of XOIC is unknown at this time, but the developers claim the program is more powerful than LOIC. XOIC is a free-to-use software program that simplifies the process of launching a DoS attack against any server once it has access to an IP address, a protocol and a target port.
The unique feature that brought XOIC to this list is the program’s three different attack modes. The first, known as test mode, is the most basic of the three. The second mode is a standard DoS attack. The final mode is a DoS assault, which uses a TCP, HTTP, UDP and ICMP message.
XOIC, like LOIC, has a user-friendly interface, so even a novice can use the tool to launch DoS/DDoS assaults against websites or servers.
6. DDOSIM

Michael Calce, a 15-year-old teenager who went by the online handle “Mafiaboy,” perpetrated one of the earliest DDoS assaults in 2000. DDoS Simulator (DDOSIM) is a tool that replicates a real DDoS attack and can attack both the website and the network. Random IP addresses, SMTP DDoS, and application layer DDoS layer are among DDOSIM’s most notable characteristics.
DDOSIM supports Linux platforms, so the tool can attack with both legitimate and illegitimate requests.
Note:
DDOSIM attacks the server by spawning a large number of Zombie hosts. Also, with the server, these hosts establish a complete TCP connection. DDOSIM initiates an interaction with the listening application once the connection is established (e.g., HTTP server). Thus, DDoS can attack the application layer.7. RUDY
Raviv Raz designed the RUDY DDoS attack. The DDoS tool was named after the album “Are You Dead Yet?” by Children of Bodom.
RUDY attacks are sometimes known as “low and slow” assaults because they aim to open a small degree of connectivity to the targeted server or website over a long period while keeping the sessions active for as long as possible.
Also, RUDY contains a console menu that users can interact with. For the POST-based DDoS assault, users can choose the forms from the URL. RUDY works by identifying the form fields for data submission and then slowly injecting the extended content length data into this form.
The RUDY tool, just like Slowloris, launches an attack by submitting a long-form field using the POST method.
8. PyLoris

In 2009, software developer Motama described the invention of PyLoris as a result of inspiration from a hack a day about Slowloris. PyLoris is an application programming interfaces tool for assessing a server’s susceptibility to DoS attacks caused by connection exhaustion.
PyLoris is compatible with SOCKS proxies and SSL connections and HTTP, FTP, SMTP, IMAP and Telnet as destination protocols. Tkinter GUI, Scripting API, Anonymity, TOR Proxying and SOCKS Proxying are all features of PyLoris.
Note:
Unlike conventional DoS assaults, PyLoris targets a service rather than the hardware. Thus, artificial limits placed on the program are the fundamental source of trouble in a PyLoris attack, not hardware shortcomings.9. Low Orbit Ion Cannon (LOIC)

LOIC (Low Orbit Ion Cannon) was created by Praetox Technologies and was first released on December 13, 2014. The program was eventually placed into the public domain and is now available on a variety of open-source platforms. LOIC had been employed in some high-profile DDoS operations before this time, including Project Chanology in 2008 and Operation Payback in 2010.
LOIC made this list because the tool is a free, easy-to-use and common solution for dealing with DDoS attacks.
10. GoldenEye

GoldenEye is a Python-based DDoS tool that’s only used for security purposes. The program’s developer remains unknown. By sending out random GET and POST requests, GoldenEye generates mixed traffic.
The GoldenEye utility includes a set of basic classes and extensions that can be utilized on a whim. For example, this HTTP test program allows a single machine to knock down another system’s web server using authentic HTTP traffic.
GoldenEye’s one-of-a-kind characteristic earned the program a spot among this list of the best DDoS attack tools: GoldenEye doesn’t require much traffic to exhaust the server’s connections.
What Are the Reasons for DDoS Attacks?

Websites and online services are the targets of distributed denial-of-service attacks. Hackers attempt to overwhelm target websites with traffic that exceeds the server’s or network’s capacity. The DDoS attack purpose, however, is to make the website or service unusable.
Revenge can be one of the motivations for DDoS attacks. Revenge could affect organizations, individuals and governments and is a common cause of DDoS attacks. Attackers utilize vengeance to attack their enemy, not simply to comment.
Politics can also be a significant reason for DDoS attacks because the internet is now the new trend of communication and means to show power. As a result, government websites may be targets of DDoS attacks. While individual hackers could have targeted the sites, many people believe governments and political parties frequently use the DDoS tactic to attack one another.

Also, competition among hackers can lead to DDoS attacks. The mindset is that if a competitor’s website is unavailable, all visitors will be directed to the attacker’s website. Furthermore, the brand image of the targeted competition is degraded, resulting in positive associations with the new company.
DDoS attacks are now available in the market at a token, and attacks can be accomplished for a relatively modest price, even if an entrepreneur is not proficient in hacking.
Note:
DDoS attacks are profitable for malicious hackers experienced in the technique of crippling servers, and this can be the most strong incentive to hacking. Money can be demanded in exchange or settlement after a website has been overtaken.Why Should Someone Use DDoS for Testing His Own Server?
To test the server’s capacity and security, one can use DDoS for the following reasons.
- It relieves businesses of the costly burden of fixing or addressing a hacked website.
- The organization’s reputation is safeguarded because a single customer attack could jeopardize a company’s reputation over the years.
- A DDoS protection system would aid in customer retention by ensuring clients have the most outstanding experience possible while interacting with the company’s website.
- Any portion of a website or network component can be stress-tested using the platform. This also helps for server load test processes.
What Is the Most Common Type of DDoS Attack for DDoS Tools?
Examples of the most common DDoS attacks for DDoS tools are listed below.

1. The first type of DDoS attack for DDoS tools is the volume-based attack.
The size of a volume-based attack is measured in bits per second (Bps). This type of attack aims to overload the capacity of the targeted site. Some examples of volume-based attacks are:
- ICMP
The ICMP flood attack consumes both outbound and incoming capacity. The attack bombards the target with ICMP Echo Request (ping) packets, sending them as quickly as possible without delay.
- UDP flood
The purpose of a UDP attack is to saturate various ports on a host system, causing the host to check for the app listening at a specific port repeatedly and respond with an ICMP “Destination Unreachable” signal if none is detected. This attack depletes the host website’s resources and can make the site inaccessible.
2. The second type of DDoS is application layer attack.
Application layer attacks are composed of potentially valid and harmless requests to crash the website. The size of these attacks is measured in Requests per second (Rps). Some of the examples of application layer attack DDoS types are:
- Low and Slow attack
A low and slow DDoS attack uses a small flow of prolonged traffic to target the server. Low and slow assaults, unlike more classic brute-force attacks, consume relatively minimal connection speeds and are difficult to resist because they drive traffic that’s difficult to separate from regular traffic.
3. The third type of DDoS attack is protocol attack.
Protocol attacks use server resources or intermediate telecommunications networks, such as firewalls and load balancers, to perform. The measurement of protocol attack is in packets per second (Pps).
DDoS types include the following.
Ping of Death

In a Ping of Death (POD) attack, the attacker sends repeated faulty or destructive pings to a computer. In this scenario, the recipient receives an IP packet bigger than 65,535 bytes when reassembled due to malicious fragment content alteration. This can cause genuine packages to be denied service due to overflowing memory buffers allocated for the packet.
SYN Flood
The requester sends numerous SYN requests in an SYN flood situation but either ignores the host’s SYN-ACK response or sends the SYN queries from a fake IP address. In either case, the host system continues to wait for acknowledgement of each request, tying up resources until no new connections can be created, leading to service denial.
NTP Amplification
The perpetrator of NTP amplification assaults uses publicly accessible Network Time Protocol (NTP) servers to flood a target computer with UDP traffic. Because the query-to-response ratio ranges between 1:20 and 1:200 or more, the attack is classified as an amplification assault.
HTTP Flood
The attacker uses seemingly valid HTTP GET or POST requests to attack a web server or application in an HTTP flood DDoS attack. HTTP floods don’t employ spoofing, faulty packets or reflection methods and thus consume less bandwidth to bring down the targeted site or server than other types of assaults.
Slowloris
Slowloris is a highly targeted attack that allows one web server to take down another web server while leaving other activities and connections on the target network unaffected. Slowloris accomplishes this by maintaining as many connections to the target web server as feasible. As a result, the Slowloris attack causes the maximum concurrent connection pool to overflow, preventing legitimate customers from connecting.
Do DDoS Tools Use Proxy?
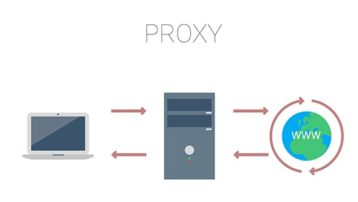
Yes, DDoS tools use proxy, and the essence of using a proxy is to combat and reduce the effect of DDoS. Reverse proxy and caching are two distinct technologies that coexist, particularly in DDoS attacks.
The reverse proxy works as an effective DDoS layer because the proxy is positioned between the attacker and the targeted server. When network attacks are intended at the server, they almost always encounter a brick wall when reaching the reverse proxy.
Multiple requests to a single resource will result in only one request to the server during a DDoS attack, and the server will be unaffected by the attack. When catching and proxy technologies are combined, they effectively stop practically all network attacks, application attacks on static pages, and, to a lesser extent, other types of attacks. This technology combination is regarded as one of the most effective DDoS defense strategies.

