The first step in phishing detection is to understand what a phishing email is. A phishing email is defined as an email sent to a recipient with the intent of forcing the recipient to complete a certain activity. The attacker may employ social engineering tactics to make emails appear legitimate, including a request to open an attachment, click on a link or submit other sensitive information such as login credentials. The main ways to detect phishing emails mainly rely on the individual to be diligent in making sure the email is legitimate and not from a fraudulent source, this can be done by performing a number of manual checks for authenticity and the use of some software can also be beneficial.
Phishing emails are now being meticulously researched and manufactured to target specific receivers. Given the quantity and severity of data breaches in recent years, phishers have a plethora of material to draw on when polishing writing skills, making phishing emails even more difficult to identify symptoms of a phishing email and distinguish reality from fiction.
The tips and methods to detect and avoid phishing email attacks are given below.
Table of Contents
1. Be Careful While Answering Public Domain Emails

Cybercriminals frequently target businesses and individuals using emails that appear to be from a genuine bank, government agency or organization. The sender of these emails instructs recipients to click on a link that leads to a page to validate personal information, account information and other types of data. Except for a few smaller businesses, most organizations will have a private email domain and company-associated accounts.
Using public email accounts for correspondence may seem like a risk-free method to do transactions, but this introduces more vulnerabilities. A hacker may successfully intercept messages if one transmits sensitive or confidential information over a public email account. The victim could even discover that communication contains a virus or malware.
Hackers continue to target public email networks because the degree of protection does not correspond to private business email accounts. Spammers frequently utilize public domains for sender addresses; the domain reputation for these domains is typically low. Public email services that spammers and cybercriminals use are generally free.

When a person gets an email, one of the first things to look at is whether the email extension is from gmail.com, outlook.com, yahoo.com or some other official email domain. The sender’s name may be faked in public domain emails. The sender looks familiar, such as a coworker or a company representative, but the email address is different. The “spear phishing” strategy comprises a fictitious firm name (impersonation) and critical facts about the target. A representative finds the name, position and other customization in sales and incorporates such details in a pitch email. Consider the public address to be a temporary address. Spammers are likely to quickly obtain a public address, particularly if regularly used on the internet.
Tips:
Companies and legitimate businesses usually house a private domain to communicate with customers and employees. Hover the cursor over the “from” address to confirm the email address and then cross-check the website the official email address and domain used.2. Avoid Misspelled Domain Names and Emails

Attackers impersonating brands is one of the most prevalent types of phishing. This phishing attack is generally accomplished by using an email address linked to a domain that’s substantially similar to the target company’s domain. Domain names may provide another hint that indicates phishing schemes. The issue is that a domain name may be purchased from a registrar by anybody. And, while each domain name must be unique, there are several techniques to generate addresses that are indistinguishable from the one being faked.
Anyone can receive a message from what appears to be an official corporate account. In many cases, the phisher cannot spoof a legitimate address and rely on readers’ failure to check. Rather than being transmitted from an official source, the sender’s address is frequently reported as a string of characters. Criminal hackers need only one person to make a mistake to be successful. An example would be instead of using @mediahosts.com, the address would be written as rnediahosts.com with “r” and “n” together, looking like the letter “m.” Other addresses would add an extra character or symbol to fool the receivers, such as @paypall.com, @pay-pal.com or @netfl1x.com.
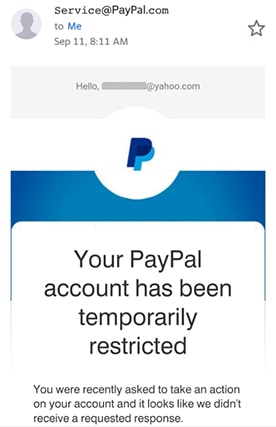
As a result, every email address must be scanned and checked before interacting with the contents.
Tips:
Take note of the spelling of the sender address and email subject line, which may contain small details to fool the receiver into clicking the malicious link or attachment.3. Detect the Poorly Written Emails
One of the best ways to detect phishing attacks is to check for poor spelling and grammar in the email content. The goal of phishing is to appear genuine enough that individuals would click on the link and provide account information. A genuine organization’s email should be nicely worded. Although no particular word is misspelled, the statement contains several grammatical mistakes that a normal speaker usually would not commit.
Missing words within a string of sentences may be spotted. For example, “Someone may have accessed account” or “we have detected something unusual to use an application.” That is not to imply that each email containing a typo is a fraud. Everyone makes mistakes now and then, especially when people are in a rush. However, spelling and grammar errors tend to be telltale signs of phishing attempts.
Tips:
Look for inconsistencies in grammar and small spelling mistakes. Companies usually run through emails and check content before pressing the send button.4. Check the Links’ Target within the Email

All phishing emails include a payload. This payload will be either an infected attachment or a link to a fake website. These payloads are designed to collect sensitive information such as login passwords, credit card data, phone numbers and account numbers. Most phishing emails contain URLs that lead to a page where one must input financial or personal information or ask for a login and password. To avoid falling for such scams, one must learn to verify where links lead before clicking.
That page is carefully constructed to look like another trustworthy website to earn visitors’ confidence. As a result, one should never enter sensitive information via the links given in the emails. Make sure to type the URL again to avoid any phishing scam. A malicious link can be identified if the destination address does not match the context of the remainder of the email. Scammers may conceal URLs by utilizing hyperlinks that appear to lead to a legitimate website. Hover the cursor over any questionable links to see the link’s address. Illegitimate links frequently comprise a sequence of digits or strange site addresses.
Tips:
On a computer, hover the cursor over the link, and the destination address displays in a tiny bar down the bottom of the browser. Hold down on the link on a mobile device, and a pop-up window with the link will display.5. Do Not Download Every Attachment

Downloading files from suspicious emails or websites is not advisable. Corporate emails containing attachments should always prompt the recipient to be cautious, especially if the extension is unknown or is often linked with malware. Some malicious files come in file formats such as .zip, .exe and .scr.
Web browsers include settings to restrict access to dangerous websites, and when one attempts to access a bad site, an alert message appears. Ignore such warnings and refrain from visiting that website or accessing that file. Be wary of harmful files; a phishing attempt may arrive as an attached file. Check if these files are expected or if the source is trustworthy. Security experts recommend never opening an attachment unless certain that the communication is from a genuine source. Even still, keep an eye out for anything odd in the attachment.
Tips:
Run a virus or malware scanner on files before downloading attachments.6. Do Not Fall for the Urgency Messages
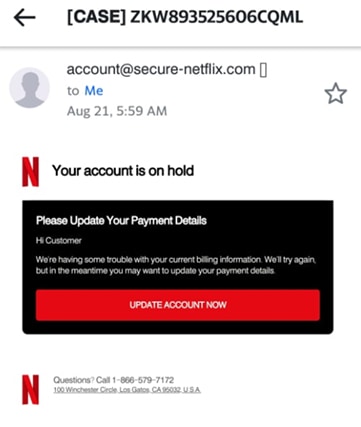
An urgent warning tries to frighten people into reacting without considering the consequences. The most efficient phishing email subject lines use psychological cues to get recipients to click, and people generally don’t like missing out on important and attention-catching messages. Attackers frequently feed on fear and urgency.
That is why so many scams demand that recipients respond quickly to avoid being too late to recover from. Once the bait has been laid and the victim falls for the scam immediately, whatever link or attachment has been accessed could have already infected the device.
Tips:
Avoid bland or generic welcomes and salutations, such as “Dear Customer” or “Hello your.email@company.com.” Legitimate companies will utilize the given name or surname of the recipient.7. Educate the Employees

Phishing is undoubtedly one of the most serious issues that businesses face. No two attacks are alike. However, training staff on security awareness builds a fast-growing workforce to recognize fraudulent emails and respond following cybersecurity best practices. Employees have credentials and general information that are crucial to a security breach at the firm, and phishing is one way an adversary acquires this protected information.
Phishing attacks are becoming more sophisticated on a regular basis. Employees should make a habit of forwarding phishing emails to the relevant security unit and alerting colleagues to the hazard so that one does not fall for the bait. The IT team or human resources can share mock phishing scenarios to allow employees to know possible situations. Only by reiterating scam-avoidance guidance will the staff acquire healthy habits and recognize fraudulent emails as second nature.
Tips:
Many tech security companies offer workshops and awareness training that tackle different types of cybersecurity threats or make use of legitimate online courses about phishing that colleagues and peers can share.8. Use Logic for the Extremely Good Messages
When everything checks out with the contents of the email—the grammar is correct, the email address appears legitimate—one must be able to go deeper if something seems off with the email being sent. Some phishers and cybercriminals have upped methods and approaches to getting private and personal information. Cybercriminals use phishing email samples to mimic well-known companies. Other telltale signs to check in the email are given below.

- “Clickbait” titles on social media, advertising or publications are attention-grabbing and can lead to fraud.
- Attackers can mix fake links with real links in spoof emails, such as the legitimate privacy and terms of service for the site being impersonated or an unsubscribe link that may appear secure. URLs can be sneaky, so hover the mouse over the link to discover what the actual website URL is.
- Generic greetings are not the common practices of legitimate companies but rather would use the real or full name of the customer. Greetings like “Dear Customer” or “Hello subscriber/member!” are some of the ways phishing emails could start.
- Poor quality logos that are unclear or smaller than usual may indicate that one may be reading a phishing email. In phishing emails, phishers frequently clip and paste the logos of government organizations, banks and credit card companies.
- Emails requesting login credentials, financial information or other sensitive data from an unexpected or unfamiliar source should always be regarded with care.
Tips:
If one has any doubts about a website, do not sign in. The safest option is to close and reopen the browser, then enter the URL into the browser’s URL bar.9. Regularly Check Your Accounts

Monitor personal and private accounts and look at the settings. Multi-factor verification has been one feature that secures email and work accounts. Some accounts provide additional protection by needing two or more credentials to log in. Creating a separate private and personal email address can increase the security of information and sensitive data.
Open email accounts only with providers that offer spam screening. Select an antivirus and internet security package that incorporates powerful anti-spam capabilities. Installing and using good internet security software on personal computers and devices is one of the simplest methods to protect users from being victims of phishing operations. Internet security software is essential for each user since the program offers many levels of protection in affordable and easy-to-use packages.
10. Call the Authorities If You Have Doubts
Inform the authorities immediately if there are emails or websites that may be faulty or malicious. The local police and the government keep track of the many scams and cyberattacks citizens experience. The report may prevent others from falling victim to a scam or phishing email. The reports are used by government authorities to track scam tendencies and trends. Based on the reports, victims may potentially initiate legal action against a firm or sector. However, most organizations do not follow up after the report and are unable to recoup lost funds.
11. Protect Your Personal Information
Email spam filters may block many phishing emails. On the other hand, scammers are always attempting to outwit spam filters, so adding extra levels of security is always a good idea.

Besides having virus protection software on personal devices, using a password manager to handle online credentials is critical. The need to use distinct passwords is critical for each website. If a data breach happens, hostile attackers will attempt to use the leaked credentials throughout the internet.
What Should You Do If You Receive a Phishing Email?

Suppose any aspect of the email is suspicious and falls under any of the common characteristics of a phishing email. In such a case, the first thing to do is not to panic and touch or click anything within the email to go any further. Responding or interacting with the email may compromise the device’s security and data. Just because one gets a phishing email does not indicate the machine is infected with a virus or malware.
Whether an email is received from a stranger or a known service/firm, verify with the company to determine if the communication is genuine. Do not respond to the email. If it appears to be from someone known, create a new email message, text or call the person and ask whether they meant to send an email with said attachments or links. Again, do not click any links in the email.
If one gets a phishing email at a work address, recall the company policies that are in place regarding this. According to IT security standards, an employee may be required to forward a phishing email to a specified address, fill out an online report, file a complaint or trash it. If one is unsure about the company’s policies, contact the IT security staff or the email service to provide them with details.
How to Report a Phishing Attack?

Reporting possible phishing attacks and opening suspicious emails allows security staff to protect the network promptly, reducing the chance of a threat spreading to other sections of the network and minimizing interruption. Determine which workers detect genuine phishing emails so that action may be prioritized when several complaints of a phishing assault are received.
While all jurisdictions have prohibitions against fraudulently obtaining someone else’s personal information, not all states have laws that explicitly handle phishing. One must still contact the nearest local police station to inform the authorities of the experience to lead the victim to the respective agency or department.
On an international scale, a person who suspects to have been victimized by a cybercriminal or wants to file on behalf of someone suspected to have been a victim may contact the Internet Crime Complaint Centre (IC3), a website that provides users with a standardized reporting method and interfaces for suspected cybercrime. One may also contact econsumer.gov, which would help authorities spot trends and combat fraud.
The complaint should provide and track the following information.
- Victim’s name, address, telephone and email
- Financial transaction details: account information, transaction date and amount, recipient of the money
- Subject/suspect: Name, address, email, telephone, IP address, website
- Specific details on how the target was victimized
- Email header(s)
- Any other relevant information believed to be necessary to support the complaint
What to Do If You Have Responded to a Phishing Email?

Before realizing that one might have responded to a phishing email, one may have responded to phishing or may have sent it. Time is of the essence, so do take the appropriate steps to minimize and prevent any consequences.
First, one must change the account passwords right away. Verify new passwords against established email password rules to ensure password complexity requirements are met. As a result, it’s critical to change passwords for the suspected compromised account and any additional user accounts linked with it. A situation could be possible that one may use the same password for different accounts and websites; therefore, changing and setting different passwords would be best.
Next, don’t forget to record and report the incident. Take screenshots and any related evidence that could be submitted to the authorities or respective departments. This way, the report would warn other unsuspected victims or users to be wary of circulating phishing attacks. Responding to phishing emails may result in the compromise of email accounts, illegal access to the organization’s networks and systems and the introduction of malware into the phishing victim’s computer and network. As a result, time is critical to launching a preliminary inquiry into the phishing event as soon as the report has been filed via the IT service desk. This inquiry aims to collect important information regarding phishing emails and analyze the impact of the attack.
Lastly, implement security and safeguard strategies to be less vulnerable to future attacks. Installing the right and effective programs to combat phishing attacks must also complement the user being well-informed on the phishing attack routes. Organizations must perform extensive user security education and training to promote cybersecurity awareness and best practices.
Should You Use an Anti-phishing Program?
Yes. Although email platforms have security features and personal or work devices have basic antivirus programs installed, the best way to secure files and sensitive data is to install an anti-phishing program to lessen vulnerabilities and be more confident to handle emails and transactions. One must not confuse an antivirus program with an anti-phishing program, as these software tools serve different purposes. However, choosing the best anti-phishing program for your home or company is now as vital as any antivirus solution.
The best anti-phishing programs must be able to identify malicious files that include macros and ZIP files. A reporting feature to identify possible phishing attacks and malicious URL detection that can be auto-blocked are some other criteria that must be considered when finding an effective anti-phishing tool.
How to Define a Phishing Attack?

In a phishing attack, a hacker sends a “spoofed” message to mislead a victim into sharing important information or installing harmful software, such as ransomware, on the victim’s infrastructure. A common definition of phishing is that this attack method is a type of social engineering.
Phishing convinces people to do anything that grants fraudsters access to personal devices, accounts or personal information. Hackers may infect the device with malware or steal credit card information more easily if posing as a person or organization that is trusted.
What Are the Types of Phishing Attacks That Aren’t Emails?

Other phishing channels would be phone calls, instant messages, social media posts or pop-ups.
Scammers mimic corporations through Voice over Internet Protocol (VoIP) technology. This approach also utilizes other types of phishing, such as utilizing personal information about targets and impersonating corporate employees.
Many Facebook users have received messages in Messenger accounts from other familiar users. LinkedIn has been the target of internet scams and phishing assaults for several years, owing to the quantity of information provided about corporate personnel. Malicious actors mine that data for possible targets for business emails and personal accounts.
While browsing the web, false or fraudulent messages may “pop up,” notifying the user of cautions, offers or recognized websites. There are some inconsistencies, so look for spelling mistakes and unusual color schemes, and keep in mind that certain pop-ups might change the browser’s orientation.

