Each type of DDoS attack differs in magnitude unit, attack focus and the layers attacked. For example, the magnitude unit for a volume-based attack is bits per second (Bps). For a protocol attack, the unit is packets per second (Pps). For an application layer attack, the measure is in requests per second (Rps).
When comparing volume-based and protocol-based attacks, volume-based attacks focus on an attack site’s bandwidth, while protocol attacks focus on the existing server resources. The other two attacks also consume more resources to accomplish an assault than application-layer attacks.

A volume-based attack has the advantage of utilizing a considerable number of resources to achieve the goal of saturating a server. A protocol attack can cause server failures by exploiting weaknesses in the layers 3 and 4 protocol stacks. Finally, an application-layer attack is a low-level, slow-moving attack that takes down a website, an internet application or a software program.
The types of DDoS attacks are listed below.
- Volume-based attacks
- Protocol attacks
- Application layer attacks
Table of Contents
The Main Types of DDoS Attacks
These are the main types of DDoS attacks.

- Volume-Based attack: This is the most popular of the three types of DDoS attacks.
- The volume of incoming traffic determines the efficiency of a volume-based attack.
- The goal of a volume-based attack is to saturate the website’s bandwidth. This attack also has an impact on CPU utilization.
- Bits per second are used to quantify the bandwidth-based attack.
- Amplification is one of the strategies for transmitting a vast amount of data to a specific website.
- Protocol attack: The attack targets exhausting server resources rather than bandwidth, making protocol attacks distinct from volume-based.
- Protocol-based attacks focus on the protocols involved in transmitting information from one point to another over the internet.
- The attack’s magnitude is measured in packets per second (Pps).
- Protocol attacks are designed to inflict service disruption.
- A protocol-based DDoS assault exhausts server resources and any other network gear in the course of operation.
- Disruptive attacks attempt to take advantage of the protocol stack by sending more packets or bandwidth than a server can manage.
- Also, protocol attacks affect intermediate communication systems, including firewall programs and load balancers, which act as a link between the server and the website.

- Application layer attack: DDoS attacks on the application layer do not target network bandwidth. Rather, these attacks focus on the application layer 7 of the OSI model hosting the service that end-users are browsing.
- Application layer attacks are developed to take over a website or an application.
- The application layer is also known as a layer 7 DDoS attack.
- These attacks are considered slow-rate yet harmful.
- Layer 7 attacks employ limited resources and target application weaknesses by imitating legitimate user activity.
- The slow-rate cyberattacks are aimed at the layer that produces webpages on the domain controller and delivers them in response to HTTP.
1. Volume-Based Attacks
Volume-based attacks include UDP floods, ICMP floods and other spoofed-packet floods. DDoS assaults that are volumetric use different strategies to generate vast amounts of traffic to completely overload bandwidth. The attack causes a line of traffic that prevents genuine traffic from flowing into or out of the targeted website.
2. Protocol Attacks
Protocol attacks include SYN floods, ping of death, smurf DDoS and fragmented packet attacks. Protocol attacks exploit the use of defects in the protocol stack’s layer 3 and layer 4 to leave the target audience unreachable. Protocol assaults, also known as state-exhaustion attacks, disrupt service by consuming too many servers and network equipment resources.
3. Application Layer Attacks
Application layer attacks include the following examples.

- Low-and-slow attacks
- HTTP-encrypted floods
- GET/POST floods
- Attacks targeting DNS services and Apache
- OpenBSD or Windows vulnerabilities
Layer 7 attacks, also known as application-layer attacks, take advantage of deficiencies in the application layer 7 by forming connections and launching process and transaction requests that consume available resources, such as disk space and accessible RAM.
Note:
Application layer assaults can be difficult to protect against because these attacks can distinguish between destructive and genuine traffic.The Sub-Types of DDoS Attacks
1. UDP Flood
A User Datagram Protocol (UDP) flood is a volume-based attack where a hacker sends IP packets, including UDP packets, to random ports on the host.
The host looks for applications connected with these data sets to address the problem, but if none are discovered, the host returns a “Destination Unreachable” packet to the sender. As a result, the system grows saturated and hence inaccessible to good traffic due to being battered by the flood.
UDP flood is free and easy to use, which is why this sub-type of DDoS attack is widely accepted. However, the success rate of UDP is roughly 98.5%.
2. ICMP (Ping) Flood

ICMP flood, also known as ping flood, is a popular DoS technique in which an intruder overwhelms a victim’s computer with ICMP echo requests, also known as pings, to bring the target down.
The attack is executed when the hacker sends packets as quickly as feasible without waiting for responses. Since the target’s servers will frequently try responding with ICMP echo reply packets, the ping flood attack causes a sizable system delay by using both the outgoing and incoming bandwidth.
There is an exclamation mark that signifies the success of the router and the remote host. On a local network, expect close to a 100% success rate. However, the usefulness of the information may decrease as the data travels around the internet. ICMP essentially drains all available bandwidth until it runs out.
3. SYN Flood
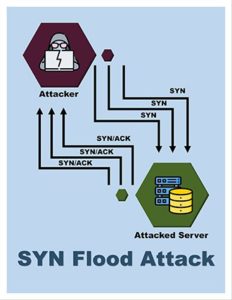
A SYN flood is a DDoS attack that uses all available server resources to render a server unavailable to genuine traffic. The attacker can overflow all open ports on a targeted server machine by continuously sending initial connection request (SYN) packets, causing the targeted device to reply to genuine traffic slowly or not at all.
SYN is a common DDoS attack. Over 80% of DDoS attacks employ the SYN flooding technique, which can cause all of the harm associated with DDoS attacks.
SYN is used to create and establish a connection. This attack also aids in synchronizing sequence numbers between devices.
4. Ping of Death

A ping flood is a basic DDoS assault in which the hacker bombards the victim with ICMP echo request (ping) packets. Ping of death works best when using ping’s flood option, which transmits ICMP packets as quickly as possible without waiting for responses.
Because the attackers can easily fake identities, ping of death attacks are highly successful. Furthermore, a ping of death intruder would need to know the target machine’s IP address.
5. NTP Amplification
NTP amplification is a sort of DDoS assault in which the attacker uses publicly accessible Network Time Protocol (NTP) servers to flood UDP traffic to the target.
NTP amplification attacks were relatively uncommon until 2013 when a significant uptick occurred. In December and January, NTP amplification affected many popular online gaming sites, including EA.com, Battle.net, and League of Legends, with garbage traffic rates reaching 100 Gbit/s.
Note:
The query-to-response ratio of an NTP amplification attack can range from 20:1 or 200:1 or higher. The value of the query-response depicts that an attacker who receives some available NTP servers can quickly launch a high-bandwidth and high-volume cyberattack.Hackers mainly use DDoS attacks against a variety of large and medium-sized organizations. While usually only threatening websites, NTP attacks often use DDoS attacks to extort and inflict direct harm to businesses and mask any penetration attempts. Therefore, a DDoS attack is always a significant problem that’s exceedingly difficult to resolve, irrespective of the hackers’ goals.
6. HTTP Flood

An HTTP flood attack is a volumetric DDoS attack that attempts to flood a server with HTTP requests. HTTP GET and HTTP POST are the two types of HTTP attacks. POST requests are used to access dynamically created resources, while GET requests obtain conventional, static information such as graphics. The primary goal of an HTTP flood DDoS assault is to produce malicious traffic resembling a human.
The popularity of the internet has contributed to the common usage of HTTP. HTTP is the protocol that underpins browser-based internet requests and is often used to load websites or convey form data across the internet. HTTP floods are successful for targeting a website’s resource-intensive components.
HTTP flood assaults are among the most sophisticated non-vulnerability threats that web servers currently face. Unfortunately, it’s difficult for network security features to distinguish between genuine HTTP traffic and malicious HTTP traffic, which can lead to many errors if not properly handled.
What Do Zero-Day DDoS Attacks Mean?

A zero-day attack is a type of cyberattack that uses newly discovered software security flaws that are unbeknownst to the software developer but known to the hacker. There may be long periods of time between a malicious actor discovering a vulnerability to a new patch being released and installed to address the flaw. During this time, the vulnerability will be actively used to restrict resources and steal data.
Since no protections are in place, zero-day attacks have a high chance of succeeding, making them a serious security danger. However, DDoS attack mitigation can help prevent zero-day attacks, such as vulnerability scanning, patch management and zero-day initiative programs. For more on this topic, refer to our DDoS attack mitigation and definition guide.
Hackers have discovered that zero-day and DDoS attacks are closely linked and that this is crucial to server attacks. For example, to launch a successful DDoS assault, the hacker must quickly assemble a botnet, preferably utilizing servers that have not previously been exposed. The zero-day vulnerability approaches are an excellent option for this.
As a result, hackers worldwide are using this strategy. The attackers must gain access to a server running software with a zero-day vulnerability to accomplish their goal. The server can then be utilized to carry out such attacks. This also eliminates the requirement for a massive number of bots.

