Table of Contents
What Is a Smurf Attack?
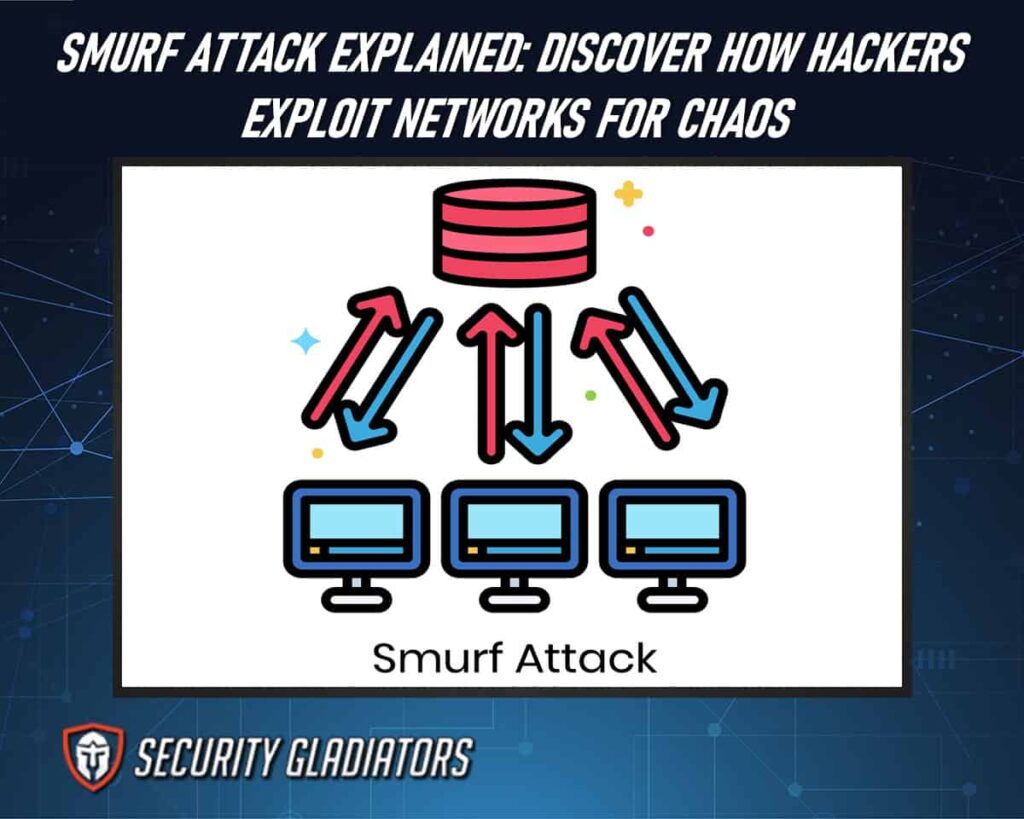
The Smurf attack is a type of distributed denial-of-service (DDoS) attack that exploits the Internet Control Message Protocol (ICMP) to overwhelm a target network with massive amounts of traffic. The attacker sends a large number of ICMP ping message(s) to network routers, using the spoofed source IP address of the victim machine.
The routers respond by sending ICMP echo reply packets back to the victim machine, which floods it with more traffic than it can handle. To execute a Smurf attack, an attacker typically uses specialized software that automates the process and enables them to send a high volume of ICMP echo requests at once. If IP broadcasting is enabled on your network routers, it may permit the transmission of ICMP echo requests to all nodes rather than a specific target.
Example of a Smurf Attack
One notable case example of a Smurf attack occurred in 1997 when a Canadian teenager named Michael Calce, also known as “Mafiaboy,” launched a series of high-profile DDoS attacks. In one instance, he targeted major websites such as Yahoo!, CNN, and Amazon, causing significant disruption to their services. Calce utilized a network of compromised computers, also known as a botnet, to initiate Smurf attacks by sending ICMP echo requests to broadcast addresses, spoofing the source IP addresses to appear as the victim’s IP. This caused a flood of ICMP responses to overwhelm the target sites, resulting in hacking and financial losses for the affected organizations. The incident drew significant attention to the potential impact and consequences of the Smurf attacks, leading to increased awareness and efforts to enhance cybersecurity measures.
Types of Smurf Attacks
There are two main types of Smurf attacks: basic and advanced. Let’s take a closer look at each:
1. Basic Smurf Attack
In a basic Smurf attack, the attacker spoofs the source IP address of the ICMP echo request packets to be the victim’s IP address. The attacker then sends these spoofed packets to a network’s broadcast address or multiple broadcast addresses. Since the packets appear to originate from the victim’s IP address, the network’s hosts respond by sending ICMP echo replies back to the victim, overwhelming its resources. The attack amplifies the traffic by leveraging the broadcast nature of the network.
2. Advanced Smurf Attack
An advanced Smurf attack goes beyond the basic technique by incorporating additional elements to enhance its effectiveness. These enhancements may include the use of multiple attackers, multiple amplifiers, or different attack vectors.
Smurf vs DDoS Attack
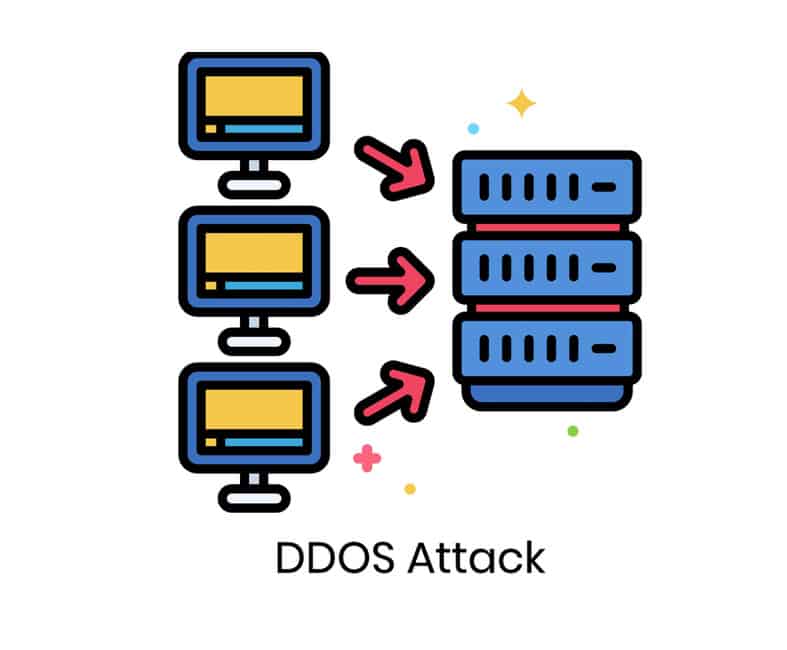
A Smurf attack involves sending ICMP traffic to broadcast addresses on the network, which causes all devices on the network to respond with an ICMP packet. The attacker spoofs the source address of their packets, making it appear as though they originate from the victim’s IP address. As a result, all responses are directed toward the victim’s machine, causing overwhelming traffic that can lead to system failure. In contrast, DDoS attacks involve using multiple compromised machines (known as ‘botnets’) to flood a target server or website with malicious packets. Unlike Smurf attacks, where only one machine is involved in generating traffic, DDoS attacks can generate massive amounts of traffic from different sources simultaneously. This makes them much harder to detect and mitigate than Smurf attacks.
Smurf vs Fraggle Attack
A Smurf attack involves sending ICMP echo requests from a spoofed IP address to multiple network nodes, resulting in an overload of responses that flood the victim’s system. In contrast, a Fraggle attack uses UDP packets instead of ICMP and exploits the vulnerability of open ports on network devices.
What Are the Consequences of a Smurf Attack
The consequences of a Smurf attack can be significant and disruptive. Here are some of the main consequences:
Network Congestion
The Smurf attack floods the target network with a large volume of ICMP packets, consuming the available bandwidth. This leads to network congestion, making it difficult for legitimate traffic to reach its destination. The victim’s network may slow down or even become completely inaccessible to users.

Service Disruption
Due to the excessive amount of traffic generated by a Smurf attack, the target system’s resources, such as processing power, memory, and network infrastructure, can become overwhelmed. This can result in service disruptions, making the system unavailable to legitimate users.
Loss of Productivity
When a network or system is under a Smurf attack, legitimate users or organizations relying on the targeted resources may experience a loss of productivity. They may be unable to access critical services, resulting in downtime, delays, and potential financial losses.
Remediation Costs
Recovering from a Smurf malware attack often requires significant resources and costs. Organizations may need to invest in additional network infrastructure, DDoS mitigation solutions, or security services to prevent future attacks. Incident response teams may need to be deployed to investigate the attack, mitigate its effects, and implement measures to prevent similar attacks in the future.

Legal and Regulatory Consequences
Depending on the jurisdiction and the nature of the attack, there may be legal and regulatory consequences for the perpetrators of Smurf attacks. Participating in or orchestrating DDoS attacks is illegal in many countries and can result in criminal charges, penalties, and potential imprisonment.
Mitigation Methods
Network Configuration and Filtering
One effective method to prevent Smurf attacks is to properly configure network devices and implement traffic filtering. Network administrators can configure routers and firewalls to block incoming ICMP traffic with broadcast addresses or disable ICMP responses altogether. This prevents the amplification effect caused by the attackers exploiting broadcast addresses. Additionally, implementing source address validation techniques, such as Ingress Filtering or Reverse Path Forwarding (RPF), can help detect and drop spoofed packets before they reach the target network.
DDoS Mitigation Solutions
Deploying specialized DDoS mitigation solutions can significantly help in mitigating Smurf attacks. These solutions use various techniques, such as rate limiting, traffic profiling, and anomaly detection, to identify and mitigate malicious traffic patterns associated with Smurf attacks. They can differentiate between legitimate and attack traffic, allowing organizations to divert or filter out malicious traffic while ensuring legitimate traffic reaches its destination. DDoS mitigation solutions can be deployed on-premises or can be outsourced to dedicated DDoS mitigation service providers.
Collaboration and Communication
Collaboration between network administrators, internet service providers (ISPs), and security communities is crucial for effective Smurf attack mitigation. Sharing information about attack patterns, new vulnerabilities, and countermeasures can help in early detection and timely response to Smurf attacks. It is important to establish communication channels with ISPs to coordinate actions during an attack and leverage their filtering capabilities to block malicious traffic upstream. Engaging with security communities and staying up-to-date with the latest security advisories and best practices can provide valuable insights and proactive defense strategies against Smurf attacks.
Frequently Asked Questions
What Is the Origin of the Term “Smurf Attack”?
The term ‘smurf attack’ originated from a technique used by attackers to send Internet Control Message Protocol (ICMP) echo requests to an intermediary network, which then floods the intended victim with large amounts of traffic.
Can a Smurf Attack Target a Single Device or Does It Always Affect an Entire Network?
A Smurf attack can target a single device or an entire network. It floods the target with ICMP packets, overwhelming its resources and causing it to crash or become inaccessible.
How Do Smurf Attacks Differ From Other Types of Network Attacks in Terms of Their Goals and Methods?
Smurf attacks are characterized by their use of ICMP packets to flood a network with requests, causing congestion and disruption. Unlike other types of network attacks that aim to gain unauthorized access or steal data, Smurf attacks seek to disrupt normal operations without targeting specific devices.

Are There Any Legal Consequences for Launching a Smurf Attack?
Launchers of smurf attacks can face legal consequences, as such acts violate laws that prohibit unauthorized access and damage to computer systems. The severity of punishment depends on the extent of damage caused by the attack.
Conclusion
Smurf attacks can cause significant disruption and damage to a targeted network. It is crucial for organizations to be aware of this threat and take proactive steps toward protecting their networks from such an attack. By implementing effective mitigation methods such as filtering out incoming broadcast traffic and monitoring for unusual spikes in ICMP activity, businesses can safeguard themselves against potential cyber threats and maintain their operations with minimal interruption.

