Bots account for more than half of all web traffic and the majority of bots are harmful. However, distinguishing between a human and a robot can be challenging. According to one survey, approximately 9% and 15% of regular Twitter accounts are bots. In addition, Facebook data revealed that 6.5 billion fake accounts were deactivated in 2019. Instagram may have as many as 95 million bot accounts.
Bots on the internet are typically used to automate the execution of routine tasks and have the potential to be both beneficial and detrimental. For example, bots are used by search engines to crawl the web and catalog information from websites. Bots are also used for trading sites to immediately find the best deals (check out our guide on cryptocurrency trading robot). Some websites and services use bots to deliver critical information such as weather, news, sports, and exchange rates.
Bots may be both helpful and destructive as they prowl the internet. Because of this potential, cybercriminals have created dangerous bot programs that silently install themselves on unprotected or susceptible computers to perform whatever operations they command. These malicious processes could be distributing spam or taking part in a distributed denial of service (DDoS) attack that pulls entire websites down.
Table of Contents
What are the Definitions of Bots and Botnets?

A bot is a web-based abbreviation for a robot. The term bot is not new though; it was first used in the 1520s to describe a “parasitic worm or maggot.” In Australia and New Zealand, it also denotes worthlessness and trouble. The term “robot”, however, is a brand-new word in the English language. Karel apek created it (1880-1938), a talented Czech dramatist, novelist, and journalist who introduced it in his 1920s blockbuster play R.U.R., (Rossum’s Universal Robots).
What is Bot Creation?
When a computer has been infected, an attacker can easily do the following:

- Read and write system data.
- Gather user’s personal information.
- Transfer files and other data.
- Track the user’s activities.
- Look for security breaches in other devices.
- Install and run applications.
Bots and botnets are designed to expand, organize, and quicken the capabilities of a hacker to carry out more significant attacks. Bots can carry out automated tasks on the internet because many of them are repetitive and programmed. However, the creation of a bot can be done using the following simple steps.
Preparation and exposure are the first steps. This involves the hackers looking for susceptible elements of a website or application. Hackers make sure that the victim isn’t aware that they’ve been infected with malware. Malware, on the other hand, will be delivered via emails and other online avenues.
The user is then infected with botnet software after performing an action that compromises their device. Many of these tactics entail persuading individuals to download a particular Trojan infection through social engineering. Sometimes hackers may use a drive-by download when visiting an infected site. Cybercriminals eventually compromise the security of multiple users’ systems, regardless of the manner of delivery.
The final phase is to mobilize infected devices to launch an attack. Cybercriminals group infected computers into botnets that they can control from afar. Hackers can use this to infect millions of PCs at once. As a result of the infection’s success, hackers have become the zombie network’s distributor.
How are Botnets Controlled?
The command-and-control (C&C) server is used to control botnets. This is where all botnet instructions are stored, as well as where each zombie computer receives orders. Control can be centralized or decentralized, depending on the situation.
The ability to get updated instructions from the bot herder is a crucial feature of a botnet. The attacker’s ability to connect with each bot in the network allows easy switching of attack vectors, changing the targeted IP address, stopping an attack, and doing other specific activities.
What is the History of Bots and Botnets?
Bots have a long history that may be traced from the dawn of time to the present day. Due to a combination of factors, including the botnet’s fast-paced, global, and highly confidential structure, piecing together a chronological and linear history of a botnet is difficult.
EarthLink acknowledged and exposed the first botnet in 2001 during a lawsuit with famous spammer Khan C. Smith. The botnet was built for mass spam, and it was responsible for almost 25% of all spam at the time. Internet Relay Chat (IRC) first appeared in 1988. Jyrki Alakuijala’s Puppe, Greg Lindahl’s Game Manager, and Bill Wisner’s Bartender were among the first bot deployed on IRC. IRC bots offered programmed services to users and stayed in channels to prevent the server from closing down due to inactivity.
Bots and botnets have become more sophisticated over time. The following lists summarize the evolution of bots and botnets.

- Jarkko “WiZ” Oikarinen of the University of Oulu, Finland, invented IRC in 1988.
- In 1989, Greg Lindahl created GM (GAMbit), the first bot in which GM engages IRC users in a game of “Hunt the Wumpus.”
- Pretty Park was discovered in 1999. The first worm to use an IRC server to control itself remotely.
- SubSeven was a bot/trojan that first appeared in 1999. A control device IRC was used to provide Trojan control.
- In the year 2000, a GT Bot based on mIRC was constructed. It responds to IRC server events by running scripts. Raw TCP and UDP Socket connections are supported.
- SDBot was created in 2002. It was written in C++, and the source code is available to the hacker community in a single binary.
- AgoBot, Gaobot, was created in 2002. The modular bot introduced modular design. They are available in three modules.
- In 2003, a SpyBot was released featuring keylogging, data mining for email addresses, URL lists, and other features.
- RBot was first released in 2003, and it is still the most popular bot today. It spreads through the use of easily adjustable passwords and packaging software.
- PolyBot, a variant of AgoBot, was created in 2004. It possesses polymorphism, which means it alters the appearance of its code with each infection.
- MYTOB bot was invented in 2005. Bot IRC C&C for my Doom mass emailing worm.
How are Bots and Botnets Used?

Bots are used for both good and evil purposes on the internet. Because of the growing number of online apps, various Internet bots can help with running programs such as instant messenger and online gaming, and data analysis and gathering.
Bots are also utilized for media delivery and live streaming across a variety of browsers. Hackers also use bots to carry out destructive internet operations and compromise PC security by installing malicious programs.
Note:
Bots and botnets carry out large-scale operations. Because most botnets have a minimum space, they don’t bog down systems or consume many system resources. It might be challenging to identify when a criminal uses a system for the wrong reasons. Botnets can also conceal themselves to carry out large-scale strikes without being detected.Bots and botnets infect open-source and unprotected devices. For example, Mirai was a botnet identified in 2016 that primarily targets IoT (Internet of Things) devices such as cameras and internet routers. Systems infected with Mirai malware turned into bots that scoured the internet for IoT devices. Mirai would next try to enter and infect such devices using popular default usernames and passwords given by device manufacturers.
Infected devices would function normally, even if utilized in large-scale distributed denial-of-service (DDoS) attacks.
What is a DDoS Botnet?
A DDoS attack employs a network of connected devices, which is frequently carried out by botnets or, on rare occasions, by individuals who have organized specific actions.
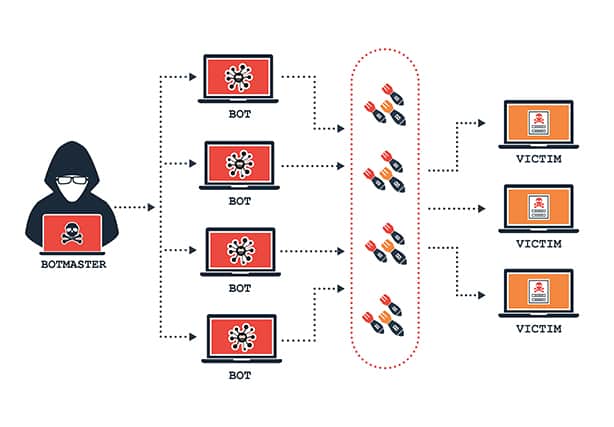
Botnet assaults are the most powerful DDoS attacks yet recorded. While some malware, such as ransomware, directly influences the device’s owner, DDoS botnet malware has varying degrees of visibility. Some malware is meant to take complete control of a device, while others run quietly in the background, waiting for orders from the attacker or “bot herder.” (Originator of a botnet)
A DDoS (Distributed Denial of Service) attack is harmful to prevent users from accessing a server or network resource. It is accomplished by saturating a service, causing it to be temporarily suspended or disrupted.

DDoS attacks are prevalent, and one of the main reasons for this is that many organizations lack adequate DDoS security. DDoS attacks have been progressively growing in frequency in the last few years, with a 10% rise in Q4 2020 compared to Q4 2019. Given the decrease from the previous quarter, this may appear to be a success at first glance. However, in Q2 of 2020, when the coronavirus pandemic led to a huge increase in online remote working, there was a large and sustained increase in DDoS attacks.
The availability of DDoS is another element that influences the frequency of DDoS attacks. A DDoS attack, for example, may be obtained for as cheaply as $5 per hour. Furthermore, DDoS attacks have been seen to become more effective even when their price falls. DDoS attacks are both efficient and economical.
Why do Cybercriminals Use Botnet Attacks?
Cybercriminals use botnet assaults to accomplish a variety of tasks. However, cybercriminals deploy botnet attacks for these reasons.

- To gain access to financial and personal data
- To overwhelm reputable web services
- Extortion of funds from victims
- To profit from zombie and botnet networks by selling access to other criminals
- Scams involving cryptocurrency
- Exploiting backdoors created by viruses and worms
- To keep track of users’ keystrokes
What are the Types of Bots and Botnets?

These are the types of bots and botnets that cybercriminals can utilize to carry out various assaults.
- Phishing
- Spambots
- Bricking
- Cryptojacking
- Snooping
- Distributed Denial-of-service (DDoS) attack
- Brute force attack
What are the Examples of Bots and Botnets?
These are some real-world examples of bots and botnets that demonstrate how common cybercrime has become over time.

- Earthlink Spam in 2000: Khan K. Smith’s spammer was the first botnet to garner widespread attention in 2000. In just over a year, the botnet delivered 1.25 million phishing scam emails disguised as messages from reputable websites. Smith intended to steal private information such as credit card details or install viruses on victims’ computers that would allow him to access data remotely. EarthLink eventually sued Smith for $25 million for using their network for his spam campaign, which netted him at least $3 million.
- Cutwail in 2007: Cutwail, a spam outfit, contributed 46.5 percent of the world’s spam volume in 2009, sending 51 million emails a minute. Attempts to shut down Cutwail have proven frustratingly futile because it comprises about 1.5 million infected PCs. However, the botnet is still alive and available for rent today, despite an attempt to shut it down by the FBI, Europol, and other law enforcement organizations in 2014.
- Grum 2008: Grum was a large-scale spam botnet that was often utilized in pharmaceutical spamming. It could transmit 39.9 billion messages per day in 2009, accounting for 18% of global spam. Grum command and control centers were uncovered in sites worldwide, from the Netherlands to Panama, as a result of the massive outpouring. Grum’s operation was successfully shut down in 2012.
- Kraken 2008: Kraken was one of the first botnets to use evasion techniques to avoid detection by anti-malware software, even when updated automatically. It isn’t easy to analyze how massive the Kraken botnet was, but its scope is apparent. Kraken is thought to have infected 10% of Fortune 500 organizations, with 495,000 bots capable of sending up to 600,000 emails every day. Although Kraken is no longer active, its leftovers have been detected by security systems in the past and could reappear at any time.
- Mirai in 2016: Mirai is a well-known botnet since it was the first to infect Internet-of-Things (IoT) devices. Surprisingly, the botnet was built by college students searching for a competitive advantage in Minecraft.On the east coast of the United States, the Mirai botnet was responsible for a massive distributed denial of service (DDoS) attack that rendered most of the internet inoperable. The worm infected about 600,000 machines at its peak.
What are the Statistics about Bots and Botnets?
These are the statistics related to bots and botnets.

- Bad bot traffic now accounts for over a quarter of all internet traffic, up 6.2% from the previous year.
- In 2017, attacks were attempted on organizations’ clients in 111 countries; in 2018, assaults were attempted on clients of organizations in 101 countries.
- The top five industries with the most harmful bot traffic are Telecom & ISPs (45.7%), Computing & IT (41.1%), Sports (33.7%), News (33%), and Business Services (29.7%).
- Mobile Chrome attachment to malicious bots has increased by 12.9 percent. In 2020, mobile browsers like Safari, Chrome, and others accounted for 28.1 percent of all malicious bot requests.
- Bad bots are frequently from the same country as the country they are attempting to infiltrate.
- Advanced Persistent Bots, or APBs, composed 57.1% of malicious bot traffic in 2020.
- The Mariposa botnet, which first appeared in 2008, was responsible for hijacking around 12.7 million computers worldwide.
Which Devices Can Bots and Botnets Infect?
Bots and botnets predominantly infect mobile devices and IoT devices. However, the following are some of the devices that bots and botnets can infect.

Mobile bots behave similarly to computer bots. If a mobile antivirus does not secure an iPhone, it can become infected with bot malware, adding to a botnet. IKee.B, for example, is a botnet that scans iPhone IP addresses.
A group of hacked closed-circuit television cameras could be utilized as a botnet channel, resulting in DDoS infection. Consider the situation of Mirai, which caused internet access to be disrupted in huge parts of the country, causing issues for several popular platforms such as Twitter and Amazon.
Cybercriminals can use an infected router to target businesses, resulting in botnets shutting down the company’s website. In addition, a hacked router can lead to poor performance for home users. If additional assaults are made from that device, the IP address may be blacklisted, potentially implicating individuals in criminal activities and hindering internet access.
Mobile botnets use unsecured exploits to give hackers root access to the compromised mobile device, allowing them to send email and text messages, make phone calls, see contacts and images, and more. For instance, the Blackberry-targeted ZeuS variation (Zitmo).
The goal of a botnet assault on Symbian is to obtain access to the mobile user device’s resources and content and transfer control to the botnet. SymbOS/Yxes, a distinct Symbian trojan, was discovered in 2009.
Hackers can take control of computers in a botnet from afar, depending on their goals. These computers, often known as a “zombie army,” can be used by the botnet owner to send spam emails, shut down websites, or make cash by creating fraudulent internet traffic or advertising paid botnet removal software downloads.
How Bots Influenced Social Media

Bots have had a significant impact on social media in a variety of ways. A social bot, sometimes known as a troll bot, is an agent that talks autonomously on social media to influence opinions. Bots for social media are prevalent and versatile to a variety of social media platforms, as well as a variety of settings and topics of interest.
Bots are thought to account for up to 15% of all online accounts. Bots behave as if they are human. They create posts, upload photographs, and material, share other people’s postings, etc. They frequently take content from other accounts to appear legitimate. Their purpose, however, is to establish a goal.
Someone trying to boost a stock, for example, might establish 1,000 bots that imitate investors and analysts. These bots can have a favorable impact on a company’s stock in identical ways to real investors.
1. Bots in Instagram

Instagram bots make managing people’s Instagram profiles easier. Bots can like posts, comment on them, respond to polls, send direct messages, and follow new accounts.
They may also respond swiftly to build their audience, and they can use algorithms and data to introduce people to new followers. Though some bots combine with a human-driven team to increase engagement, others are entirely powered by AI.
People’s Instagram presence can grow rapidly with the use of Instagram bots. Similarly, using bots on Instagram might harm a user’s account because it violates Instagram’s service rules. Instagram did in fact take steps to combat bot-generated spam in 2017 and 2019.
2. Bots in Facebook
A Facebook bot is to create and manage a fictitious Facebook account. By using computer software that interacts with users automatically, Facebook bots allow website visitors to access various services. This has significant ramifications for businesses and their profitability.
Facebook bot accounts can be used to inflate or diminish a person or movement’s popularity, distorting users’ perceptions of actual public opinion. Bots, for example, played a significant role in spreading falsehoods on social media before the 2016 US election. In many parts of the world, cybercriminals have been exploiting fake accounts to promote fear and societal division, and in some cases, to encourage violence against organizations or people.
3. Bots in Linkedin

On LinkedIn, a bot is a profile that a computer program has created. Fake LinkedIn profiles can contain hundreds of contacts and a small number of Skill Endorsements. They frequently join various groups and follow a few different firms and influencers.
The use of a bot can result in a user’s account being permanently suspended or canceled. It’s also against LinkedIn’s terms of service. LinkedIn has a funnel of defenses to detect and take down fraudulent accounts at numerous stages to construct robust countermeasures against various forms of attacks.
4. Bots in Twitter
A Twitter bot uses the Twitter API to control a Twitter account. Bots account for a large portion of Twitter’s 271 million users, and they are among the most valuable members of the Twitter platform.
Bots can be used to broadcast helpful information, automatically generate entertaining or original material, and also reply to users via direct message when used effectively. On the other hand, people employ Twitter bots to get around API rate constraints, violate user privacy, and spam. According to studies, questionable bot accounts on Twitter were responsible for roughly 20% of election-related activity.
5. Bots in TikTok
A TikTok Bot is computer software that automates TikTok actions to increase followers and engagement. The TikTok bot is primarily a marketing tool that facilitates and accelerates engagement. The user automates the tool according to particular target audience guidelines and custom filters, which it then uses to scale the activity of liking, commenting, and following other accounts’ posts and profiles. According to a recent study, bots may readily access TikTok accounts, undoubtedly propagating misleading information.
Are Bots and Botnets Illegal?
Making a botnet of computers that one has authority to control isn’t against the law. For example, software engineers or researchers might be interested in experimenting with botnet labs. Installing malware on another person’s computer without their permission is, nevertheless, considered a criminal offense.
What Are the Laws Regarding Bots and Botnets?

Botnets have become a more popular technique for criminals to make money illegally. Law enforcement agents are increasingly discovering that botnet developers and operators utilize botnets for their unlawful reasons and sell or rent access to infected machines to other criminals. Criminals who buy botnet access use infected computers to steal personal information, spam, and launch DDoS attacks on computers.
Because it is illegal to hack into computers without authorization, current criminal law bans the development of botnets. It also makes it unlawful to employ botnets to commit additional crimes. However, it is unclear if the law prohibits the selling or rental of botnets.
For instance, undercover officers uncovered a criminal seeking to sell a botnet containing thousands of victim machines. As a result, authorities “purchased” the botnet from the criminal and informed them that their machines had been infected. However, because there was no evidence that the seller had built the botnet, the operation did not result in a prosecutable offense in the United States. The seller was free to continue his activities. While trafficking in botnets is sometimes punishable under other provisions of the Computer Fraud and Abuse Act, this difficulty has resulted in the inability to prosecute persons who sell access to thousands of infected computers and will continue to do so in the future.
How to Protect Yourself from Bots and Botnets
Bots and botnets can be good and bad, but it is vital to have significant preventive measures against them. These are the ways to protect yourself from bots and botnets.

- Limit the number of failed login attempts.
- Install the most recent version of the operating system.
- Scan all downloads before launching them.
- Do not click on any links that appear untoward.
- Install an antivirus program that is both effective and high-quality.
- When it comes to email attachments, be especially cautious.
- Use complex and lengthy passwords.
- Avoid using devices with poor security.
- Enable popup blockers.
What to Do If You Become a Bots and Botnets Victim
If you notice traces of bots or botnets on your system, follow these steps to restore it.
- Making a criminal complaint.
- Patches and updates should be applied to all system apps as soon as possible.
- Update Anti-virus and anti-malware software regularly.
- Scan your device manually.
- Restore your system to factory settings.
- Reinstall files and applications from a backup or the cloud if possible.
- Get your data from the cloud after you’ve reset the device to factory settings.
How to Remove Bots and Botnets?
These are the ways to remove bots and botnets from your system.
- Run Microsoft Defender: Microsoft Defender is a fantastic antivirus program included with Windows 10. Follow the steps below to use the Defender.
- Choose “Settings” from the Start menu in the bottom left corner of your computer, and a page with nine options will appear.
- You can save time by typing defender into the search box. Alternatively, go to Update and Security. The second menu on the list is Window Defender. Make sure you have the most recent window update before using the Defender.
- Select “Windows Defender” from the drop-down menu. Verify that real-time protection is enabled.
- Open Defender and check that the top-right button is green and says “PC status: Protected.” If you get a red signal, though, you must press the big red button to activate the defense.
- The next step is to double-check all malware updates and update definitions. Now, select “Full” from the scan options and scan. A complete scan can take up to an hour. If there is a threat, the Defender will alert you after it is concluded.
- You can also look through the history section to see which threats have already been quarantined.
- If you see any threats, you can remove them entirely, and the Defender will immediately remove any malware that is present.
With these checks with Microsoft defender, your computer is protected from bots and botnets and any other kind of malware.
Another option to keep the PC protected is by following the steps listed below.
- Isolate the infected PC from the rest of your network and the internet.
- Check all other computers on your LAN because malware can spread across a network.
- Scan all network-attached storage and USB disks you’ve already linked to the infected machine.
- If the problem persists, consider utilizing a malware removal tool. If it still persists, consider utilizing a botnet removal program.
What are the Bots and Botnets Removal Tools?
It is essential to know how to eradicate the risks with the appropriate tools. These are the tools that can be used to clean a device of bots and botnets:

- Avast – What is Avast?
- Malicious Software Removal Tool
- Avira BotFrei
- Trend Micro RUBotted
- BotHunter
- Kaspersky DE-Cleaner
- Norton Power Eraser
- Bot Revolt
- Quick Heal Bot Removal Tool
- Phrozensoft Mirage Anti-Bot
What are the Other Threats?
Various risks can disrupt a company’s network and cause it to shut down. These are some of the multiple threats described below, in addition to DDoS and other types of social engineering attacks.


