Different security methods are used to ensure secure smartphone experiences, such as secure online gateways, endpoint protection, email security, VPNs, and other security measures. Some smartphones are specifically designed to provide users with the highest level of security possible. As such there are many benefits to using a secure smartphone, namely, the users’ data is protected from unauthorized access and the many threats that can come with this. Furthermore, the need for data privacy and security necessitates using a safe smartphone. A secure smartphone safeguards users from losing crucial data to cybercriminals by wiping the data in the event the device is lost or stolen.

The following are some of the most secure smartphones in 2023.
- Bittium Tough Mobile 2 C
- Purism Librem 5
- Apple iPhone 12 pro Max
- Silent Circle Blackphone 2
- K-iPhone
- Sirin V3
Table of Contents
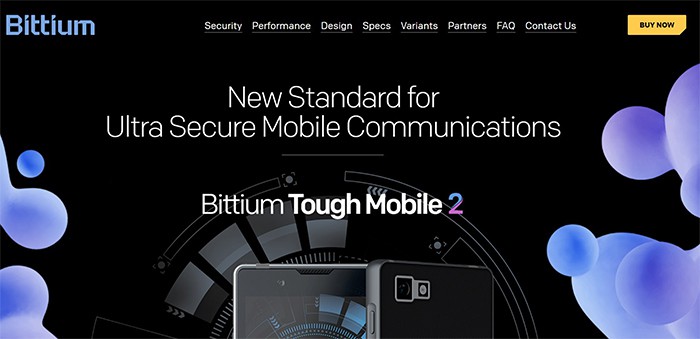
1. Bittium Tough Mobile 2 C
Bittium Tough Mobile 2 C is a secure smartphone developed for secure communications for government officials. The Bittium Tough Mobile 2 C is a telecommunications device ideal for the defense industry and other organizations where security is of utmost importance.
The smartphone has a confidential operating system segregated and hardened for secure use and designed for top-secret, government-level conversations. Other features of Bittium include:
- Multi-layered security
- Trusted design and manufacturing
- Long lifespan
- 12MP autofocus rear-facing camera
- 5MP front-facing cameras
- Ultra-secure communication
- Two separated operating systems
The dual-boot functionality of the Bittium tough mobile 2 C allows two distinct operating systems with full data separation within one device. Users can also effortlessly switch between the two operating systems. In Confidential mode, the operating system is separated and hardened for secure use and is intended for government-level secret communications. The Personal mode of the hardened Android operating system is designed for personal usage, with free access to Google services and other social networking applications. When using adoptable storage mode, all data on the device, including the memory card, is encrypted with AES-256 encryption.
The Bittium Tough Mobile 2 C features a 5.2-inch Full HD “sunlight-readable” touchscreen (that works with gloves and while wet), a Snapdragon 670 SoC, 4GB RAM / 64GB eMMC, MicroSD expansion slot up to 256GB, a 12 MP rear camera, a 5 MP front-facing camera, dual front-facing speakers, dual-band Wi-Fi, Bluetooth 5.0, and NFC, as well as a 12 MP rear camera, water and dust resistance to IP67 standards, as well as shock and drop resistance to MIL-STD-810G standards. Bittium tough mobile 2 C boasts dual-SIM capability, a 3,000 mAh battery, and dedicated privacy, emergency, and push-to-talk buttons.
Users can purchase the Bittium tough secured smartphone through resellers and system integrators. The Bittium tough mobile 2 C costs between €2800 and €3,000, including tax from resellers, and close to €2,500 without tax. Users can also place an order for the smartphone by contacting the Bittium service with all of the information required on the website.
Note:
Bittium secure suite management software and encryption software are included with the Bittium Tough Mobile 2 C smartphone, which allows for remote management of devices and applications and secures IP-based data transfer. The Bittium Tough Mobile 2 C has been certified as Confidential level NCSA-FI, TL III when used with DEC Secure.Bittium tough mobile 2 C is a smartphone with advanced security features. The benefits of using the Bittium smartphone are two-factor authentication, impenetrable hacking protection, tamper-proof secure elements to prevent data theft and hardware manipulation, secure duality in one device, extended availability of security updates, backup accessories, and a longer life span. The main disadvantages are the high cost of the device, complexity of use for non-technical users, and the limited battery capacity of 3000mAh.
The important applications of the Bittium tough mobile 2 C are the always-on VPN, Bittium Secure Suite, and encryption software. However, to use that VPN client to secure data in transit, users need the Bittium Secure Suite software solution for Bittium Tough Mobile 2 C. Also, the smartphone is a fantastic device that is only available to government agencies and other authorized organizations.
The Bittium smart gadget has, however, received some criticism. Some users claim that the Bittium Tough Mobile 2 C is a regular phone with water, shock, and dust resistance that prioritizes security over all other features. Despite the premium specs, the smartphone met the security needs of users who value security over specifications. Another area of contention is the device’s price compared to competing smartphones with similar features.
2. Purism Librem 5
Purism Librem 5 is an open-source smartphone developed for individuals who value privacy and security. The smartphone is powered by free and open-source software, open governance, and transparency rather than Android or iOS. The smartphone also comes pre-installed with PureOS, a GNU/Linux operating system. The term “free software” denotes that the source code is available, and people with sufficient technical knowledge may easily read and comprehend the operating system’s language.
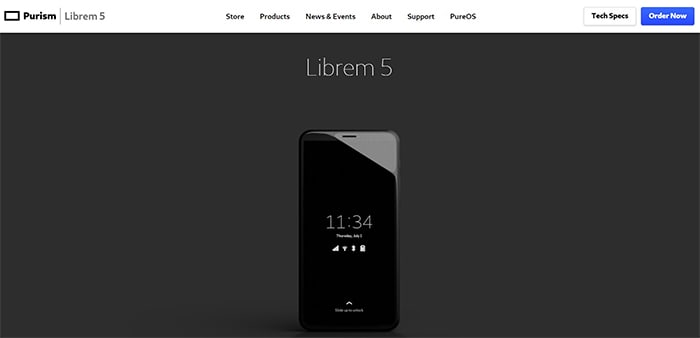
The Purism Librem 5 has unique hardware kill switches that disconnect the WiFi, Bluetooth, cellular signal, microphone, and camera. Some of the other features of the Librem 5 device are a user-replaceable battery, multilayer security protection, decentralized connectivity, user-controlled source code, and the ability to run HTML5 (web) apps. The Librem 5’s Vivante GC7000 Lite GPU has a lot of 3D rendering capabilities while keeping users’ independence with free software drivers. Users will also benefit from lifetime updates, which will extend users’ phone lives.
Purism Librem 5 features include a NXP i.MX 8M Quad-core Cortex A53, 64bit ARM @max 1.5GHz (auxiliary Cortex M4), 3 GB RAM, 32 GB eMMC internal storage, microSD (2TB max), 5.7′′ IPS TFT 7201440, TESEO LIV3 multi-constellation GNSS receiver, front camera of 8 MPixel, rear camera of 13 MPixel w/ LED flash, and “9-axis” by ST.
The price of Purism Librem 5 starts at $1199. The Purism Librem 5 has a high level of security because the smartphone runs on completely auditable open-source code. The Librem 5 is a phone developed on PureOS, a privacy-supporting, open-source, and completely verifiable operating system that is not based on Android or iOS.
The benefits of using the Purism secure smartphone are access to a user-replaceable battery, privacy, a headphone jack, continuous and lifetime upgrades, an open-source operating system, hardware kill switches, and end-to-end encrypted communication. Despite all of the advantages of using the Purism secure smartphone, there are some drawbacks, including high pricing, low battery life, and the device’s large size.
Users often criticize the Purism Librem 5 because the operating system could be improved. According to a TechRadar critic, the Librem 5 caters to privacy and security concerned users with hardware kill switches and carefully developed hardware. Another critic revealed that the smartphone is difficult to recommend, but with future software upgrades and hardware modifications, there could be improvements.
Nevertheless, every software is designed to be updated regularly. However, the Purism Librem 5 will need more frequent updates to compete more effectively in an extremely difficult market.
3. Apple iPhone 12 Pro Max
The Apple iPhone 12 Pro Max is a powerful smartphone with long battery life and an excellent camera for a smartphone. Some of the security-based features of this iPhone version are Face ID, Touch ID, and most importantly, the latest iOS. This iOS is one of the most significant improvements to the phone’s mobile operating system. The iOS 14 operating system is one of the most secure on the market, with more control over the location, camera use, and access settings.
The Apple iPhone 12 pro max iOS 14 prioritizes user data privacy much more than the mainstream competition. However, the smartphone now supports iOS 15, the most recent version of the software. Apple also incorporates encryption for all users’ sensitive data directly into the phone’s hardware.
Aside from the iPhone 12 Pro Max’s security, this smartphone also has a very -powerful A14 Bionic CPU, Apple’s fastest mobile chipset ever. This processor controls the phone, resulting in a smooth, lag-free experience. Some of the other features of the Apple iPhone 12 pro max are an internal memory card with 128GB and 6GB RAM, 256GB and 6GB RAM, or 512GB and 6GB RAM, an accelerometer, gyro, proximity, compass, barometer, Siri natural language commands, Ultra-Wideband (UWB) support, magnetic MagSafe accessories, 5G network compatibility, and IP68 water resistance.
The Apple iPhone 12 Pro Max is available through Apple store locations, and Apple authorized resellers, with prices varying. Although the price of the iPhone 12 pro max varies based on storage capacity, the price starts at $1,099, $1,199, and $1,279 for 128GB RAM, 256GB RAM, and 512GB RAM, respectively. The iPhone 12 Pro Max has a battery capacity of 3687mAh and supports 20W fast charging.
The Apple iPhone 12 pro max security is excellent, with customers’ privacy in mind. The iPhone 12 pro max also has a high level of security built into the hardware and the ability to encrypt all sensitive data. Face ID is a secure and convenient way for users to unlock the iPhone 12 pro max, authenticate payments, and sign in to various third-party apps. Ultimately, “Find my iPhone” assists consumers in locating lost or stolen phones while also preventing someone else from gaining access to users’ data.

The benefits of using the Apple iPhone 12 pro max include an amazing user interface, 5G connectivity, 6 GB of RAM for uninterrupted multitasking, stereo loudspeakers, a great screen, longer battery life, and a strong camera. The disadvantages of using the iPhone 12 Pro max include the high price, large size, and lack of a MicroSD slot for memory expansion.
Some of the major apps pre-installed on the Apple iPhone 12 pro max are iMovie, Pages, Keynote, Numbers, GarageBand, Apple Store, Trailers, iTunes Remote, Safari, Wallet, Siri, Maps, Clock, and Reminders. Some users criticized the iPhone’s price compared to the other iPhone 12 models. The iPhone 12 pro max will appeal to consumers who want long battery life, a sophisticated iOS, and enough storage to watch movies on the go.
4. Silent Circle Blackphone 2
The Blackphone 2 is the second smartphone from Silent Circle, a Swiss firm specializing in encrypted mobile phones. The smartphone offers a completely private experience, including advanced security features, comprehensive permissions control, and encrypted voice, text, and video chat. Silent Phone provides top-of-the-line security and functionality to help secure a company’s data.

The Blackphone 2 features a 5.50-inch touchscreen display with a resolution of 1080×1920 pixels. The Qualcomm Snapdragon, 615 octa-core processor in the Silent Circle Blackphone 2, runs at 1.7GHz with 3GB of RAM. Silent OS 1.1 is installed on the Silent Circle Blackphone 2, powered by a non-removable 3060mAh battery.
The Silent Circle Blackphone 2 includes 32GB of internal storage that users can upgrade up to 128GB through a microSD card. The Silent Circle Blackphone 2 is 165.00 grams and measures 152.40 x 76.40 x 7.90mm in height, breadth, and thickness. Silent Phone 2 also allows for secure team collaboration, including secure conference calls and secure group messaging.
Users and corporate communication security are the focus of this secure smartphone. Silent Phone supports OpenID Connect (OIDC) and Active Directory Federation Services for single sign-on (ADFS). Silent Phone offered an extra layer of security by allowing users to control security with security words. This one-of-a-kind system serves as the “final line of protection” against man-in-the-middle attacks.
The Blackphone 2 has a price range of $700 to $1200. The Blackphone 2 is equivalent to any other Android phone except for the operating system. The smartphone’s Silent OS is a modified version of Android 5.1.1 Lollipop that adds a variety of new security capabilities to the device.

A security umbrella feature, which integrates a variety of granular controls without sacrificing the overall experience, is the key to the Blackphone 2’s success. Concerning users’ data, Silence Circle takes a “zero-knowledge” approach. Despite the security protections, the basic Android Phone and messaging apps are still available on the home screen, allowing users to make unencrypted phone calls or send text messages.
The amazing security offered by the Blackphone 2 is one of its major advantages. However, compared to other smartphones, this device has some drawbacks, such as performance lags. Also, encrypted calling and messaging requires an additional fee. Secondly, the lack of encrypted email and security certifications on the Blackphone 2 could create problems for some enterprises, particularly government agencies, to rely on the smartphone. Blackphone 2 also does not support fast charging and is not waterproof.
Users of this smartphone reported that, despite the 3GB RAM, they still encounter lags while browsing. Blackphone 2 may not compete with some of the leading secure smartphones due to the way the device trades performance for privacy.
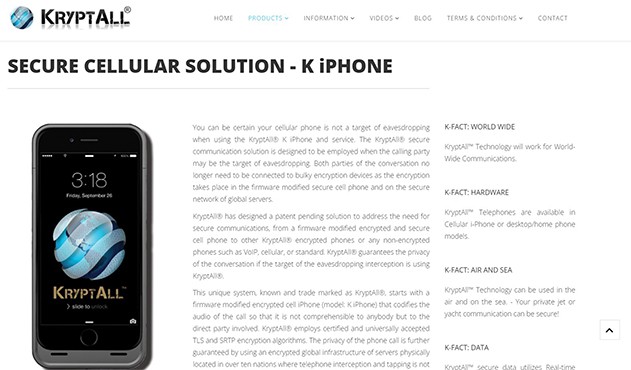
5. K-iPhone
K-iPhone is an unhackable encrypted smartphone. The calls made on this safe smartphone are encrypted and sent over the cellular data network. Users’ internet security and privacy are a top priority for K-iPhone and the KryptAll protects users’ data by codifying the audio of the call. The encryption makes the call unreadable to anyone other than the direct party utilizing approved and generally recognized encryption techniques. The technology also uses a global encrypted server infrastructure that spans over ten countries where intercepting or tapping phone calls is illegal.
Some of the features of the K-iPhone include worldwide network security, complete freedom to call anyone in the world with full encryption, and comprehensive customer support. K-iPhone also employs encryption techniques such as 256-bit AES.
Every KryptAll phone has a unique 6-digit network number that can call other KryptAll phones. Around the world, KryptAll is used by heads of state, Fortune 500 corporations, executives, and privacy advocates. The call quality is as clear as any other call, and there is no delay due to encryption. This secure smartphone provides users with the freedom to customize the display on caller ID.
Users who seek total security will pay any price, according to the KryptAll smartphone service. However, users who want to purchase the K-iPhone can visit the company’s website for further information. Users can find some of the phones on eBay and Amazon. Depending on the model, a secure smartphone from KryptAll might cost anywhere from $5,000 to $10,000.
Note:
K- iPhone’s security differs from that of other secure smartphones. The company regularly distributes phone numbers that are not linked to the International Mobile Equipment Identity to users, making it impossible to trace users’ identities. Calls enter standard phone networks through more than 100 connecting points on five continents for added security. K-iPhone is also a customized and hardened smartphone with 256-bit AES voice/data encryption.The advantages of using the K-iPhone include a patent-pending caller-initiated encryption method and manufacturer privacy assurances. Calls are also made from a modified phone across a very secure worldwide network. Furthermore, users have the flexibility to call anybody, anywhere, on any phone in the world without leaving a trace. However, the K-iPhone is very expensive and can be difficult to use for non-tech savvy users.
Some of the inbuilt applications of the K-iPhone are not revealed, but some of the applications are expected to be security-based. The K-iPhone is one of the most secure smartphones available and connects to the internet via WiFi or 3G, allowing content to be securely encrypted without leaving a trace. There are currently no major complaints about the smartphone.
6. Sirin V3
Sirin V3 is based on Samsung’s latest business-class Galaxy S21 smartphones, including a multi-layered platform incorporated into the hardware and software. The V3 has a Dual-Persona solution, allowing users to flip between two different spaces. There’s a Personal mode that gives users unlimited control and robust baseline security, as well as a Confidential Workspace option that protects user data and professional conversations from malicious actors.
A behavioral-based and machine learning Intrusion Prevention System (IPS) is included in the Sirin V3 multi-layered cyber security suite for proactive cyber defense in real-time. Other features of the Sirin V3 include a resolution of FHD+ 2400 x 1080 pixels, 20:9 aspect ratio, US chipset Snapdragon 888 Global, Exynos 2100 for the global unit, 8GB LPDDR5 RAM, a battery with a capacity of 4000mAh and a charging speed of 25W, 128GB UFS 3.1 storage, triple rear camera (12MP primary with OS, 12MP ultra-wide, 64MP telephoto with OIS), and Samsung Knox, personal mode, and workspace mode security.
The Sirin V3 is quite costly, costing $2650, approximately $800 more than the Samsung Galaxy Z Fold 2 foldable phone. Users can order the smartphone by visiting the company’s official website.
The real-time encryption, device multi-layer security, and high-end privacy are all advantages of using the Sirin V3 smartphone. The main disadvantage is its expensive price.
The Sirin V3 has many useful applications, including a confidential call app, ProtonMail, and the TOR browser. The Sirin V3 is still largely regarded as privacy and security-focused smartphone. There are currently no objections about the smartphone, possibly because the device is a 2-in-1 security solution smartphone based on Samsung premium phones.
What are the Security Features of Secure Smartphones?
With updates and the necessity to resist any cyber threat, smartphones are becoming smarter and more secure. All internet users must use encrypted phones to safeguard data with technological advancements. As a result, certain security features are essential for all secure smartphones.

Facial recognition is a vital security feature used to verify the user’s identity and unlock the device. There should, however, always be a backup option for recovering information from the phone, especially if the software begins to malfunction. Users can activate this functionality by navigating to Settings – Lock Screen & Security – Face recognition on most smartphones, then turn on face recognition. The user must also set up app verification and other features. This facial characteristic looks impenetrable to intruders, but users can reinforce the approach by introducing an additional layer of security.
One of cybersecurity software’s most frequent security features is a kill switch. Most smartphones have a kill switch that allows the entire phone to be wiped in case the phone gets lost and is difficult to be found. Users can navigate the account and remotely reset the device to factory settings, wiping out all personal data. Although nothing can bring the users’ device back, the data is encrypted, so the kill switch is a strong security feature.
Voice detection is another security feature required for the encryption of mobile phones. This voice security feature is useful for individuals who require immediate access to specific confidential information. Users can also use Google Assistant to create a voice match profile, which will only respond to the user’s voice. There’s also an Unlock with Voice Match option, which allows users to unlock the device by merely saying, “Ok, Google.” Voice security can be enabled by navigating to Settings – Lock Screen & Security – Smart Lock. After that, users must verify a backup passcode to choose Voice Match. The user can then choose Access with Voice Match to have the assistant record the user’s real voice.

A security feature used to locate misplaced phones is a message on the lock screen. Certain features, such as the lost phone prompt, allow users to message the person who recovered the phone. Users can locate this function under Settings – Lock screen and security – Lock screen signature on most smartphones. The user can leave a backup phone number or email address activated when the phone is stolen or lost.
What are the Best Security Apps for Secure Smartphones?
The best security apps for secure smartphones are listed below.
- Password generator
- Where’s My Droid
- Anti-theft alarm
- Norton mobile security
- Find my device
- Prey
- McAfee mobile security
- Avast mobile security
What is the Cost of Secure Smartphones?
Depending on the smartphone, safe smartphones can cost anywhere from $700 to $10,000. These secure smartphones are expensive, but the prices are a better investment than using an insecure handset.

