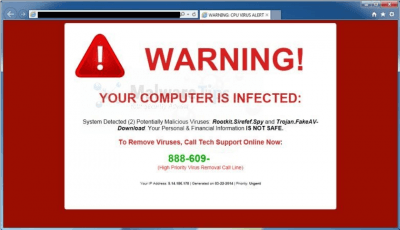
This is the fourth and the final part of this four-part series where we try to teach you how to stay safe from fake antivirus programs.
Most of the tips are self-explanatory and rather simple really but it never hurts to read something you already understand to better prepare yourself against cyber criminals and hackers who scour the online world looking for easy targets.
If you missed the first part of this series of posts then go here. The first part of the post will set your foundations for staying safe from hackers and other cyber criminals who try to bombard you with fake antivirus software in order to gain access to your computer and compromise your privacy and other sensitive data.
For the second part go here. This is where you’ll learn more about the ways cyber criminals along with hackers, try to trick you into installing their fake antivirus programs on your computer.
For the third part go here. This part details some of the advanced methods, cyber criminals along with hackers use to gain access to administrative rights on your computer in order to install junkware on your computer which slows it down and ultimately renders it completely useless.
By now, assuming you have gone through the previous three parts of this series of posts, you should be able to recognize when a cyber criminal is trying to install a fake antivirus program on your computer without your knowledge or permission.
We’ve already discussed the possible signs that make themselves prominent when your computer machine has been infected by a fake antivirus program (that in turn fills up your computer with malware and other forms of spyware).
But just to continue on that point, remember that there is no one single way to identify if a fake antivirus program has been installed on your computer.
You’ll have to look at a lot of things simultaneously to understand if your computer has been hacked remotely.
Generally speaking, you should look out for any funny looking toolbars within your internet browsers, which you don’t remember installing.
There are also other types of junkware that fake antivirus programs will try to install on your computer while you’re busy working on something else.
Sometimes, fake antivirus programs are advanced enough to even direct the behavior of your internet browser and direct it, without your input, to a pre-determined website of a scammer or a hacker.
Hackers along with other cybercriminals use a variety of techniques to con people into buying fake antivirus programs and then try to double up on that by furthering installing spyware along with malware without letting the purchaser of the fake antivirus program know anything.
Modern cyber criminals and hackers have also learned the techniques to come up with cool looking advertisements that are very enticing to click at and believe in. So be wary at all times.
Readers should also know that a fake antivirus program can hurt your computer machine in a variety of ways. Sometimes, the fake antivirus programs would do no harm to your computer other than to install more malware on it to make it slower and slower.
Sometimes, fake antivirus programs take users to fake websites that look like legitimate websites and then try to dupe the user into buying more of their useless software applications.
But that’s not the only form of advertising that hackers along with other cyber criminals use to con internet users. There are a lot of ways in which users can be conned into buying a fake antivirus program through different forms of advertisements.
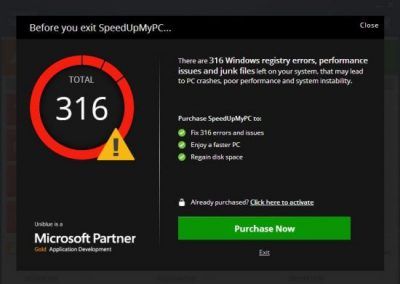
As mentioned earlier as well, when you suspect your computer machine being infected with a fake antivirus program, there isn’t one final sign that indicates such possibility. You must always look for multiple telltale signs.
One of the ways, cyber criminals along with hackers try to fool internet users into buying and then installing fake antivirus programs on their computer machine is through the use of, what is called, inline advertising.
Table of Contents
Now, What Is This Inline Advertising?
It is just another tool for cyber criminals along with hackers to scam people into buying their fake antivirus programs.
Think of it this way: every website that exists on the internet has words on it. Genuine ones along with fake ones, each and every website has some form of content on it in order to either benefit the visitors or to scam them.
When your computer machine or internet browser gets infected with inline advertising, words on those same genuine websites will appear to be underlined for no particular reason.
Moreover, not only will words be underlined, but they will also link to all sorts of disgusting stuff that lie in the darkest dungeons of the internet.
In short, some of these links can land you in some pretty undesirable places. Sometimes, these links will take you, without your permission of course, to gambling websites. Other times, you might be redirected to a porn site.
You might have already figured out, what else can cyber criminals and hackers do if they get their hands on your computer machine or internet browser with the help of a fake antivirus program.
Fundamentally, cyber criminals along with hackers want one thing from you and that is money. Whatever method gets them money, they will use it. And because you made the mistake of installing their fake antivirus program, they get to have their way with you. For a while that is.
Now we come to the juicy stuff. That is, ways you can minimize the threat of cyber criminals and hackers installing a fake antivirus program on your computer machine or any other device that is connected to the internet either through landline or Wifi.
How To Stop Cybercriminals and Hackers Forcing You To Install A Fake Antivirus Program On Your Machine
Thanks to the hard working engineers at cyber security firms and other legitimate antivirus programs, there are many ways in which you can protect yourself against fake antivirus programs.
Well, in truth, you can’t be totally safe from hackers and cyber criminals. But you can drastically reduce the risk of unknowingly installing fake antivirus programs on your system if you just follow some rules.
Let’s have a look at them one by one.
- Always install a firewall. If you have a new computer then the first thing you should do is to install a firewall or just enable the default one if you’re on Windows. Otherwise, go to the internet and download one from a trustable source.
Microsoft already does the job for you as it ships free firewall software with its copies of Windows operating system.
However, if you have a Windows operating system that is older than Windows XP, then you probably don’t have a default firewall. In that case, the only option for you is to download a third-party trusted software and then protect yourself with that.Just because someone says your computer is infected, doesn’t mean it is. - Stop clicking on pop-ups altogether. In other words, never click on random pop-ups just because they look nice and harmless.
There are no exceptions to this rule. You should always stay away from pop-ups and run an antivirus scan when you see on your screen. - If you happen to use the Windows operating system as your primary operating system then have the default security settings at either medium or high.
- Most of the modern users spend the majority of their time on their computer accessing the internet via an internet browser and hence you should pay attention to your browser as well.
If your browser is warning you about a particular website then don’t try to access it again and again using some tricks. Always take the safe route and go to another website for the information that you’re seeking. Google Chrome and Firefox are two of the best browsers available in the market and we recommend that you use either of the two if you want a secure environment in which to surf the internet. - Do not download pirated software. To put it another way: don’t be a pirate. Don’t be evil. Apart from the moral consequences, it is just not nice to download stuff that developers have spent years developing for free.
Now, we’ll grant you that free software always looks and sounds better than a paid one but remember that free products are uploaded by people. And if they are uploaded by people, then those people are going to want something in return.
And since most torrent sites don’t have a legitimate payment system, most of the uploaders inject their files with malware and other forms of software.
People who upload copyrighted content on torrent sites and on other file sharing websites, do want to make money and hence they try to do that by compromising the security of your computer machine.
Sometimes, these uploaders get a hold of your private information when you visit their file sharing website and then sell that data to advertising companies and even to crooks. - Make it a habit of reading at least two reviews before you buy or install any antivirus software application because believe us, there are a lot of fake antivirus programs out there on the internet that pose like the real ones.
Go for well-reviewed and legitimate antivirus program and download them from well-known sources.
We have already warned you about how cyber criminals along with hackers use all sort of methods to package their junkware to look like the real thing when all they are really selling you is junk or probably something even worse. - Do not open email attachments just because you have received a new email. There is a general rule for opening email attachments, which is: only open email attachments from senders who are trusted.
If you don’t know a sender, then don’t open the email attachment. If you can’t verify that the email sent to your by your contact is indeed from the genuine contact, then don’t open the accompanying email attachment.
Remember that cyber criminals along with hackers can inject viruses into your computer through email attachments as well.
The best route to follow here is to have an antivirus program handy at all times and scan the email attachments with that specific antivirus program before you open them.
All your incoming emails should be scanned with a legitimate antivirus program.
Conclusion
Your education on protecting yourself against fake antivirus programs is complete. Remember that each day more people connect to the internet than the day before. In other words, the population of people who connect to the internet on a daily basis in increasing at a rapid pace.
And that gives a lot opportunity to cyber criminals and hackers to destroy unwary internet users with their fake antivirus programs.
Therefore, more people need to become aware of the ever increasing threat of fake antivirus programs on the web.
This fact has also helped people who make genuine cyber security software in order to protect users who only want to gain something beneficial from their travels on the internet.
The security product industry has seen a significant uptick in recent times. More and more people are signing up for free and paid antivirus services along with VPN service and anti-spyware services.
And while all of that is good, the problem with an every increasing number of people on the internet and the increase in the number of cyber security software is that, it pushes hackers and other cyber criminals to come up with even newer ways of hacking into computer machines and injecting them with fake antivirus programs.
One thing is for sure, cybercriminals will not stop evolving and they will try to take advantage of any opportunity to catch one of these unwary internet users off guard.
Offering fake security software applications, such as fake antivirus programs, is their way of taking advantage of the weak and also to make money.
Here is a valuable list of fake antivirus programs.
Congratulations for making this far. This is the end of the series. There are a total of four parts so if you have missed any one of them or just want to read them again, then go here for the first part, go here for the second part and go here for the third one.
What do you think about fake antivirus programs and legitimate antivirus programs? Can you tell the difference without making much of an effort or have you too fallen victim to one of those fake antivirus program schemes?
Do let us know your thoughts, experiences, and comments by using the comments section below.
If you think this super guide helped you in understanding how cyber criminals along with hackers try to take advantage of internet users who don’t prepare themselves, then subscribe to securitygladiators.com for more guides just like this one.