Since there are several types of DNS hijacking methods, each type comes with a distinct set of risks. The two most prominent techniques hackers use to launch DNS hijacking attacks are DNS redirection and DNS spoofing. Fortunately, cybersecurity tools provide protection against specific types of DNS hijacking. Cybersecurity experts also have a simple set of guidelines anyone can follow to present DNS hijacking attacks. Of course, the effectiveness of any DNS hijacking attack depends on the resources available and the expertise of the actors involved. So DNS hijacking can occur for many different reasons to achieve many objectives. There isn’t a single set of malicious actors behind most DNS hijacking attacks.
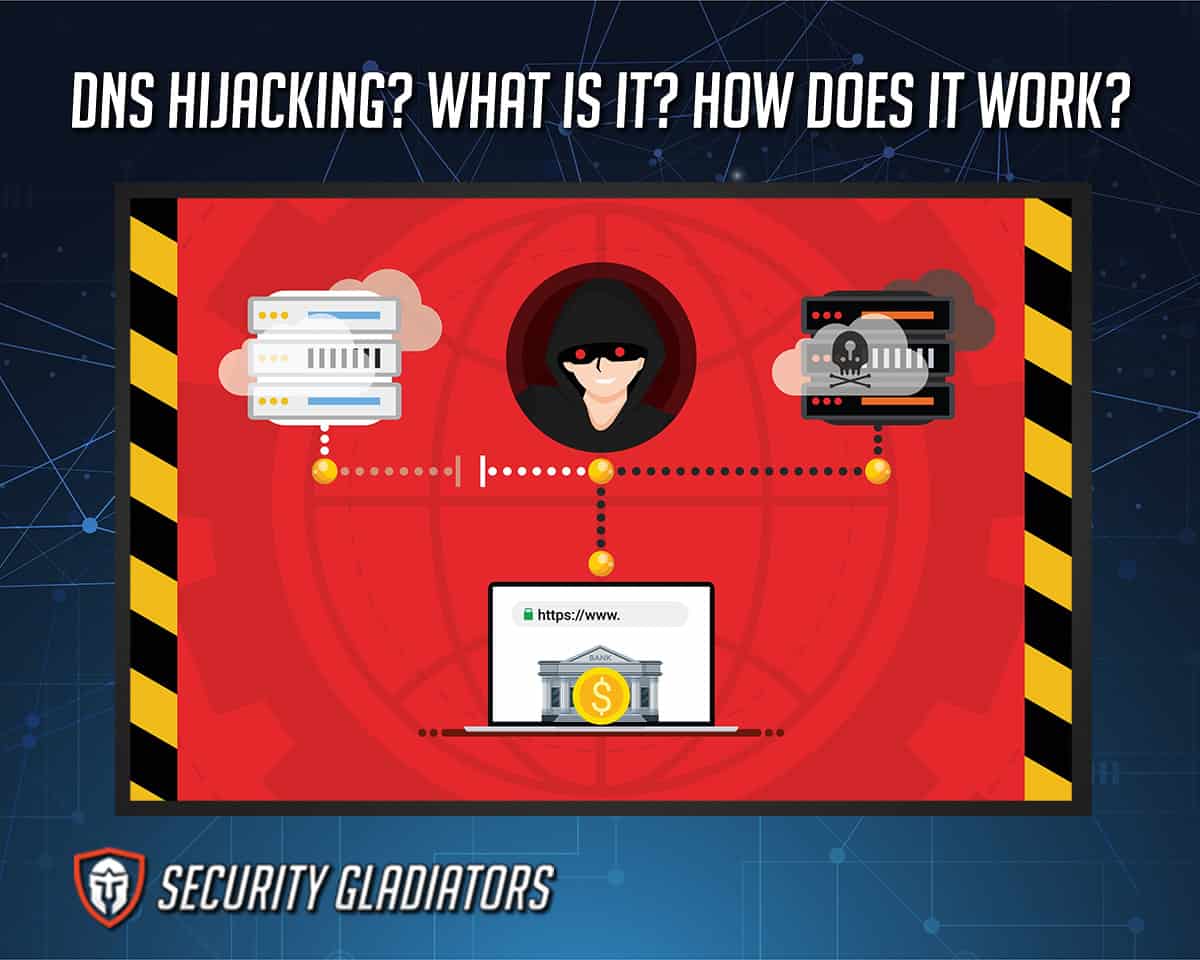
Table of Contents
What Is DNS Hijacking?
An explanation of the term DNS will help to understand DNS hijacking. The term DNS stands for Domain Name System. The Domain Name System essentially acts as the phonebook of the internet. DNS contains directories that link IP addresses to website names. Any time the user inputs the name of a website into the search bar of a web browser, the DNS comes into play. The browser communicates with the DNS by sending the URL name to the DNS server. This action is referred to as a DNS request. The DNS server then responds with the proper IP address. Upon receiving the correct IP address, the browser relays the information to the user’s device, which enables communication with the desired website.

In DNS poisoning, hackers can impersonate normal internet users or clients or even devices. Using such a disguise, hackers are able to intercept sensitive information, which is usually protected. Hackers can also interrupt communications by locking traffic. Generally, after compromising a DNS server, hackers set up spoofed DNS. This is where a user is forced to go to a specific website that is not the website that was requested. The problem is compounded by the fact that hackers set up malicious websites to look exactly like the websites the user intended to go to. Diverting genuine internet users to illegitimate DNS servers is how DNS poisoning begins. After that, hackers can use other techniques, such as man in the middle attacks to steal login information and download viruses to the user’s device.
How Does DNS Hijacking Work?
DNS hijacking essentially leverages the security vulnerabilities inherently present in the way DNS works. When the user wants to visit a website, the web browser communicates with a DNS server. That’s how websites are usually found. But while connecting to a DNS server, the user’s device doesn’t check if there are malicious DNS servers. Hackers can exploit that situation and imitate DNS servers that do not respond with the correct IP addresses when DNS requests are made.
Sometimes, the user’s device doesn’t need to contact a DNS server (or name server). That happens when the browser’s cache already has a record of a previously visited website. Most of the time, though, the user’s device has to communicate with a DNS server. Internet service providers or third-party companies like Google usually provide DNS servers. And that’s where the problem lies. The exchange of information that results in a DNS query being answered usually doesn’t have any type of protection or encryption. Hackers also try to exploit the DNS because the system is mostly trusted.
DNS hijacking isn’t always about hackers compromising DNS servers. Sometimes, because of bugs, DNS servers can respond with incorrect results with no intervention. Such problems usually manifest as missing IP addresses or IP addresses leading users to completely different websites. DNS hijacking is only the start of a cyberattack. Once DNS hijacking has been carried out successfully, hackers can launch even more potent cyberattacks, such as landing users on phishing websites, stealing personal information and compromising passwords. Fortunately, there are ways to learn how to fix DNS hijacking vulnerabilities and issues with minimal technical expertise.
What Are the Risks of DNS Hijacking?
The key risk of cyberattacks such as DNS hijacking is loss of privacy. If hackers can intercept DNS queries, the user’s browsing record can be compromised. Hackers can then use that data to either sell on the dark web or launch more cyberattacks, which may result in identity theft. Another risk of DNS hijacking is virus infection. If a hacking group can hijack DNS records and send users to malicious websites, the user may click somewhere that automatically downloads viruses on the user’s device. The worst part is that the user may not even know that the browser has downloaded a virus. That’s because the malicious websites set by hackers often look similar to legitimate ones.
An additional risk is the loss of login credentials. Hackers can set up phishing websites and use DNS hijacking to send users to that phishing website. Once the user inputs login credentials on phishing websites (for example, a phishing website that looks like Facebook), the information gets sent back to the hackers. Eventually, hackers can use that login information to carry out more damage and compromise other user accounts via the original account’s contact list.
DNS hijacking comes with even more risks when hackers have the knowledge to carry out advanced cyberattacks such as pharming, a type of hacking. This is where hackers can use scripts, among other things, to show users unwanted ads. Each user may not click on the malicious ads, but after some time, hackers can generate significant revenue. Another risk of DNS hijacking is the internet service provider collecting customers’ data. After collecting enough data, internet service providers can either sell that data or show users targeted ads whenever there is an opportunity to show a new domain.
Note:
Techniques such as DNS hijacking also come with the risk of governments being able to launch effective censorship programs. Governments can also restrict access to certain websites and promote websites with government propaganda.What Are the Different Types of DNS Hijacking Attacks?
There are many different types of DNS hijacking attacks. DNS hijacking attacks can be subdivided into five major categories. The first type of DNS hijacking is called Rogue DNS server. In Rogue DNS server hijacking, hackers first compromise a DNS server. After that, the website records available with the DNS server are modified. Finally, hackers configure the compromised DNS server to redirect specific DNS requests to different websites. Such websites are usually laden with malware.
The second type of DNS hijacking is MitM DNS attacks. The term MitM stands for Man-in-the-Middle. In MitM DNS attacks, hackers snoop on communications between a target user’s device and the DNS server. But just like before, the primary aim of hackers is to change the final destination on which the user lands. That is done by providing the user with a different IP address for the same DNS request. As always, the different IP address leads to a website with lots of malware and viruses.
Another type of DNS hijacking is local DNS hijacking. In local DNS hijacking, hackers first compromise a target user’s device. The device is then infected with malware, usually Trojan. The main objective of the Trojan is to reconfigure the DNS settings on the target device. Once the new settings are applied, the user’s DNS requests are redirected to websites containing lots of malware.
One prominent type of DNS hijacking is router DNS hijacking. In router DNS hijacking, hackers go for the router instead of attacking the user’s device directly. Most of the routers are still configured to use the default password and username. That leaves the door open for hackers to compromise the router and then reconfigure DNS settings. Not only that, but hackers can also look for routers that have not been patched up. A router with older firmware is more likely to be vulnerable to easily launched cyber attacks. The changed DNS settings, in this case, affect each and every user connected to the internet via that router.
A lesser-known type of DNS hijacking is on-path DNS hijacking. In this type of DNS hijacking, hackers intercept communications between a DNS server and a target user. Then the communications are obstructed. Afterward, DNS requests are answered with multiple IP addresses of different websites filled with viruses.
One of the most common DNS hijacking types is DNS spoofing. In DNS spoofing, hackers redirect legitimate DNS requests made for legitimate websites to websites with malware. All that hackers need to do is compromise a DNS server and then redirect users to the malicious website, which often looks like a legitimate one.
DNS Spoofing vs Redirection
DNS redirection and DNS spoofing are closely related DNS hijacking methods. DNS Spoofing is when hackers redirect traffic from a genuine website, such as YouTube, to a malicious website that looks like YouTube but isn’t YouTube. Sometimes, hackers can use DNS redirection to launch successful DNS spoofing attacks.
How To Prevent DNS Hijacking
There are many ways to prevent DNS hijacking that do not involve difficult configurations. DNS security can be enhanced by following a simple set of guidelines. More specifically, DNS security means DNS name server security. Strong security measures for DNS name servers will result in more protection against DNS hijacking. Some tips to prevent DNS hijacking are given below.
- Protect DNS resolvers with firewalls. All DNS make use of resolvers. Hackers compromise resolvers and then compromise DNS servers. That’s how legitimate resolvers are poisoned. If an IT team can protect legitimate DNS resolvers with firewalls, DNS security can be achieved.
- Take care of common security vulnerabilities, because hackers are always looking for the easiest targets. Obvious security vulnerabilities give hackers the opportunity to compromise DNS. IT teams should regularly examine DNS for potential security vulnerabilities and apply patches as needed.
- The most common measures against cache poisoning include randomization (of source ports and user identity) and generating difficult domain names that include lower and uppercase letters.
- The most common method to ensure DNS hijacking protection is to change passwords frequently.
- Always keep antivirus products updated and the operating system patched as soon as updates are available.
- Install VPN (virtual private network) apps on all devices that are used for sensitive information. Also, keep VPN apps updated at all times and set auto-connect to ON from the settings menu.
- Only a selected number of people from the IT team should have DNS access. This tip is specifically for website owners.
- Another tip for website owners is to use client locks. This would effectively disable the option to change DNS records for everyone except a selected few IP addresses. DNSSEC is a good example of a DNS provider that uses public keys and digital signatures to validate DNS requests.
Who Typically Commits DNS Hijacking?
Hacker groups typically commit DNS hijacking. But there are a variety of different people that take advantage of DNS hijacking. Internet service providers have also been known to take part in DNS hijacking. This happens when internet service providers intercept a user’s DNS request, collect relevant information, analyze the information for insights and then serve users ads. These ads are shown to users whenever users mistakenly land on unknown domain names.
Some government agencies also take the help of DNS hijacking methods to keep tabs on any content that should not be accessed. Such type of content usually contains material deemed not suitable for consumption. Other government departments can use DNS hijacking to keep access blocked to certain religious and philosophical content.
Why Does DNS Hijacking Occur?
The primary reason why DNS hijacking occurs is that DNS communications rarely have sufficient protection against hacking attempts. But the precise reasons why DNS hijacking occurs depends on the actor behind the DNS hijacking attempts.
Note:
Hackers, internet service providers and governments can carry out DNS hijacking. All three actors have different reasons for engaging in DNS hijacking. But only hackers have ill intentions behind DNS hijacking to hurt end users and organizations.
Hackers usually intend to glean personal information on users, which can then later be used for blackmail, amongst many other activities. Phishing is currently the most common and low-tech method (amongst the available advanced hacking methods) to steal personal information. DNS hijacking is an effective start for hackers, who can transition into phishing attacks once the target user is on a malicious website (enabled by DNS hijacking).
DNS hijacking also occurs because websites, internet service providers, marketing companies and other actors need user statistics. User statistics help legitimate businesses, including internet service providers, to improve services and products. Other times, via DNS hijacking, ISPs and marketing companies can serve relevant ads, which increase sales while fulfilling user needs.
Note:
Not all DNS hijacking is harmful. Even though governments can sometimes overstep the mark and tread into undue censorship territory, most DNS hijacking done on part of government agencies serves a good purpose. Governments that only aim to redirect toward government-approved websites instead of websites that promote foreign propaganda also use techniques such as DNS hijacking. The censorship in China is an example of DNS hijacking done by governments.Where Can DNS Hijacking Be Used?
Actors can use DNS hijacking methods wherever there are DNS communications taking place. DNS is one of the fundamental building blocks of the internet. Every time the user wants to visit a website, some form of DNS communication has to take place. This is exactly where DNS hijacking is used extensively.
Any time there is a need to make certain websites unavailable for access, DNS hijacking can be used. DNS hijacking is also the perfect tool for when there is a need to redirect users from a website to another website. That other website can either be safe or harmful, depending on the actor behind DNS hijacking.
What Are the Possible Consequences of DNS Hijacking?
DNS hijacking methods have affected global organizations and related operations many times in the past year alone. Since a good portion of organizations, companies and websites do not invest in DNS security, there are a lot of consequences of DNS hijacking.
The primary consequence of DNS hijacking is financial loss. A report by IDC shows that, on average, companies tend to lose around one million dollars per successful DNS attack. Other consequences include business losses, disruption of business operations and lack of interest from future investors.

Perhaps the most overlooked possible consequence of DNS hijacking for the victims is the loss of privacy. Individual users lose access to personal information privacy. Companies and organizations lose access to data generated from millions of user queries.
In the process, companies lose reputation points as well. For the end-user victim, consequences include hyper-targeted ads that may take advantage of a lapse in judgment.
For the attackers, consequences of DNS hijacking include access to people’s behaviors, the ability to block content deemed unfit, harm rival organizations and service providers, catch criminals, blackmail political opponents and promote different ideologies.
Is DNS Hijacking Illegal?
DNS hijacking can be legal or illegal, depending on the actor performing the actions. Governments, businesses and network security professionals now employ many DNS hijacking methods to test the security of computer systems and networks. Very often, professional security experts infiltrate a computer system or network the same way a hacker would. But such type of DNS hijacking cannot be considered illegal. To protect against more security vulnerabilities and loopholes, professionals may employ DNS hijacking techniques to strengthen existing countermeasures against DNS hijacking attempts. In other fields, such as cybersecurity teaching institutions, instructors may show students DNS hijacking methods. In that case, too, there isn’t any illegal activity.
Apart from ethical hacking, all other forms of DNS hijacking can be considered illegal. The United Nations Commission on International Trade Law states that a person who modifies, damages, disrupts, downloads, copies and extracts any information from a computer network or computer system without permission from the owner or related personnel may be charged with penalties. In such cases, hackers who engage in DNS jacking to steal personal information may be considered to be carrying out illegal activity. The same goes for internet service providers and marketing companies if the main aim of DNS hijacking is to hurt customers, competitors and ideas.

