Global protests over police brutality erupted last week after the death of George Floyd, an unarmed black man killed in police custody on Memorial Day. It all began in Minneapolis, Minnesota, where a white police officer knelt on Floyd’s neck for almost nine minutes while he was pleading that he couldn’t breathe.
The officer’s knee was still pressed on Floyd’s neck after medics arrived to find him unresponsive without a pulse, while another officer blocked bystanders from intervening. Floyd died shortly thereafter. Video footage filmed by witnesses went viral, sparking nearly two weeks and counting of daily protests.
It only took a few days for the demonstrations to evolve into a nationwide outcry for change under the #BlackLivesMatter movement.
And now, the protests have gone global as human rights advocates in countries around the world join in solidarity.
On the frontlines of the protests, most of which are being live-streamed on social media and cable news, activists need to know how to protect their online safety and privacy. Protestors and activists are under constant surveillance, and it can be used against them or their cause, especially in countries where dissidents are arrested, imprisoned, shot or killed.
In an increasingly digital world and a time of social unrest, it’s more important than ever to keep your online security and anonymity protected. This guide will show you some of the most crucial cybersecurity best practices to know and live by.
Whether you’re a journalist covering the protests on the ground, an activist organizing and leading events, or simply a supporter who wants to march with fellow protestors standing up for human rights, these digital security tips will be helpful for you.
Table of Contents
Why Is Cybersecurity Crucial to Protestors & Activists?
There are always risks involved in activism, no matter what your message is. Though there are many different types of activism, the risks will always be more severe if you live in a country with limited free speech laws and strict censorship measures implemented by governments.
In the U.S. over the past week, during the protests demanding justice for Floyd, there have been numerous cases of police attacking and injuring peaceful demonstrators.
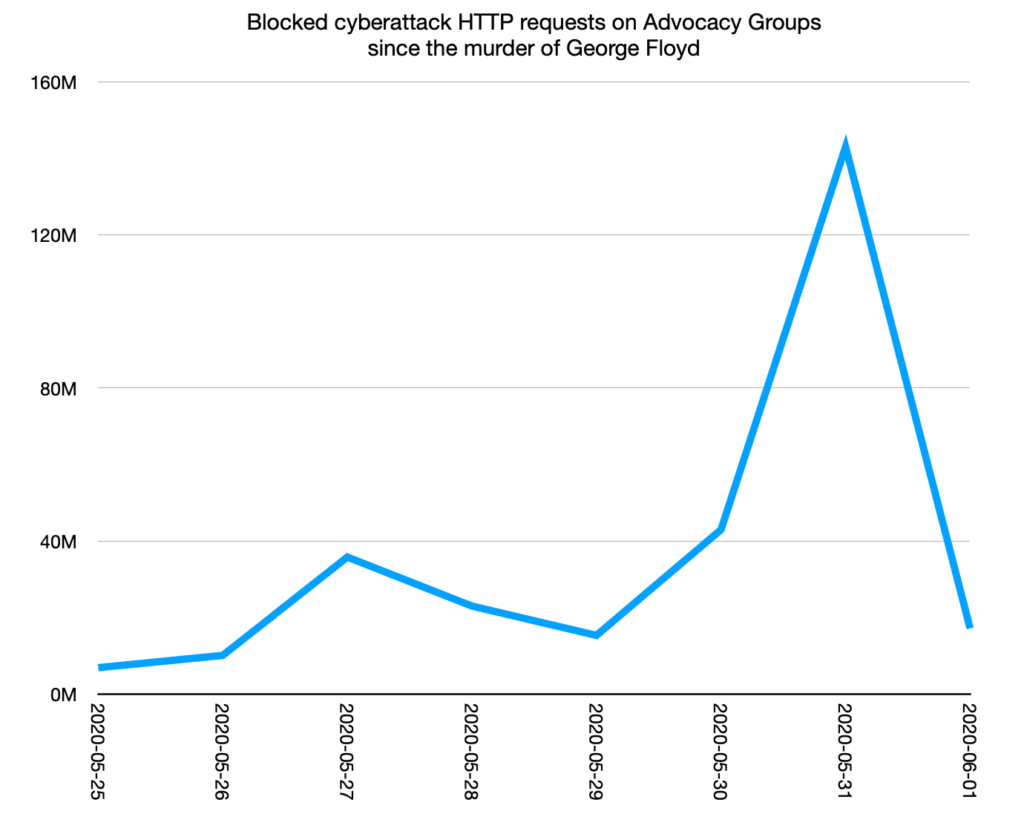
Activists’ digital security is under threat as well. Just this past week, Cloudflare data revealed that several civil rights activism organizations, including the American Civil Liberties Union (ACLU) and the National Association for the Advancement of Colored People (NAACP), are being targeted in organized cyberattacks by an unknown group.
Metadata Poses a Serious Threat to Your Privacy & Security
One of the most common cybersecurity mistakes that might compromise a protestor’s privacy is posting videos and photos with metadata to their social media accounts. The term metadata literally means “data about data.” It provides information about a file’s contents, including the date and time it was created and modified, where it was created, who has access to it, and its tags and content categories.
It’s very easy for law enforcement agencies to get access to this metadata, especially through social media posts shared by activists they’re targeting. They can also compel social media companies and your phone/internet service provider to hand over the metadata they collect on you if they suspect suspicious activity—all without you knowing.
Law enforcement agencies use metadata to their advantage in investigating and surveilling citizens, even without probable cause.
In 2013, leaked classified documents revealed that the U.S. National Security Administration holds a massive database of citizens’ online activities and location data. This data collection practice is still in place and has even ramped up in recent years.

In 2014, for example, the Federal Bureau of Investigation tracked one #BlackLivesMatter activist as they traveled across the U.S., raised money for bail funds and planned a protest against an agrochemical corporation—all without any clear indication of violence.
Since 2014, the FBI and Department of Homeland Security have monitored several other BLM activists through surveillance. If you’re a political activist/social activist, you might have been tracked at some point too.
Surveillance is a present threat now as protests continue across all 50 U.S. states.
Last week, a leaked memo revealed that the U.S. Drug Enforcement Agency is authorized to conduct covert surveillance on Black Lives Matter protestors.
In individual cities, police departments are calling for citizens to send in tips about protestors’ activities. Last week, police in Dallas, Texas encouraged anyone who has videos of protestors engaging in “illegal activity” to share evidence through an anonymous tip app called iWatch Dallas. This request quickly backfired as the app was bombarded with videos of K-pop performers instead.
Even so, this case underscores a larger point of concern: Anyone can record videos of you and share them as they please, especially in one-party consent states like Texas, where only one person involved in a conversation/interaction has to consent to share recordings of that interaction, with or without the consent of the other party.
So, now that we’ve covered the significance of metadata, here are some important tips for keeping your identity and data secure and anonymous while fighting for your cause:
Tip #1: Scrub Metadata Before Sharing Videos & Photos
If you’re posting any videos or images, be sure to scrub all the metadata first. Click here for a guide on how to remove GPS coordinates and other personal data from photos/videos.
Last week, a developer created a tool that lets users anonymize their photos and videos by quickly blurring faces, street signs or other identifiable objects. Check it out here.
i built a tool
for quickly scrubbing metadata from images and selectively blurring
faces and identifiable features. it runs on a phone or computer, and
doesn’t send info anywhere.process your
images so that you and others are safe:https://t.co/GbQu5ZweDq
pic.twitter.com/jKjABTgPRX—
everest (@everestpipkin) May
31, 2020
If you’re an iPhone user, there’s an iOS shortcut you can use to blur faces in photos and strip the photo of all metadata. The shortcut was created by a California software developer and a group of anonymous programmers last week. Download it here.
Tip #2: Turn Location Services Off
One of the most important things you can do to safeguard your metadata is to disable location services. This way, there’s no record of your whereabouts during a protest.
Here are the links to the relevant Apple and Android help pages:
- Turn off location services for iOS devices (iPhone, iPad, Mac)
- Turn off location services for Android devices
- Turn off Google Maps location services
- Turn off Apple Maps and GPS location services (note that the steps might be different depending on your country)
Tip #3: Adjust Your App Settings
Your apps know more about you than you think. If Facebook, Twitter, Gmail or any other website or online service is hacked, that information could be exposed to anyone. Also, law enforcement authorities can always get a warrant to compel Facebook or Google to hand over all their data on you.
Note:
It’s important to be aware of this and disable certain social media settings that allow companies to track your location and activities and share that data with advertisers.Here are the links to the privacy/data settings pages of the most popular social media sites:
- For Twitter
- For Facebook
- For Google (which includes YouTube, Gmail, Google Search, Google Chrome and other Google-owned services)
- For Instagram
Tip #4: Turn on Airplane Mode
You can avoid revealing your location by turning your phone on airplane mode.
- Click here for how to do it on Android devices.
- Click here for how to do it on iOS devices.
You should also avoid making phone calls or texting during a protest. Your signal will ping nearby cell phone towers, revealing your location. (We’ll get more into how to encrypt your texts in a later section of this guide.)

Valuable Apps, Resources & Tools for Activists
VPNs
A Virtual Private Network is an extremely valuable cybersecurity tool for protecting your privacy not just in a protest, but in everyday life as well. VPNs work by changing your IP address, which is a code assigned to your device by your internet service provider.Rather than connecting to your ISP’s servers, a VPN sends your internet connection to a server that’s owned by the VPN service provider. Since most VPN services have a zero-logs policy, they won’t have any data to give to law enforcement agencies even if they are asked.
It’s important to have a VPN up and running at all times to encrypt all of your data and communications in a protest. With a VPN, you can connect to a server in another city or country around the world.
So, for example, if you’re protesting in New York City, you can use your VPN to connect to a server in Berlin. That way, your connection will appear as if you’re located in Berlin since your real IP address is hidden. No website, service or stranger online will be able to find out that you’re actually in New York City.
There are VPN apps for mobile devices as well as desktop computers and laptops. We recommend using NordVPN because it’s the best value for your money, with tons of advanced encryption capabilities and extra privacy and cybersecurity services.
Encrypted Messaging Apps
Whenever you’re at a protest, always use encrypted messaging apps rather than Facebook Messenger, Skype or SMS text messaging.
One of the best encrypted messaging services is Signal, a popular open-source app that operates on its own advanced encryption protocol. Read more in our Signal review.
For emails, make sure you use PGP to encrypt your messages. We’ve compiled a separate guide on how to encrypt your emails here.
You can also use anonymous and encrypted email services such as ProtonMail and Tutanota, which allow you to create your own secure email address while safeguarding your cybersecurity.
Privacy-Focused Browsers
Some of the most popular web browsers aren’t the most privacy-friendly tools for surfing the internet. Google is even facing a lawsuit for allegedly tracking people through Google Chrome’s incognito mode, a feature that’s supposed to keep users’ data private.
Instead, use an encrypted web browser such as Tor or Brave:
- The Tor browser is an open-source encrypted web browser operated by The Tor Project, a nonprofit organization focused on free speech, human rights, cybersecurity, open access to information and censorship circumvention. Download the Tor browser here.
- Brave is a secure, fast and completely private web browser that blocks trackers and compensates users with rewards when they opt into ads through the platform. Download Brave here.
Before, during and after a protest, use Tor or Brave to access news, chat with people in your group, and post photos and videos on social media.
For an extra layer of security, turn on your VPN at the same time.
Alternative Search Engines
Google is the most popular search engine, but it is not the most private. It’s always collecting data on you to sell to advertisers or enhance other products within the Google ecosystem.
Fortunately, there are several alternative search engines that aim to protect users’ privacy by operating on a different model. The most popular Google Search alternative is DuckDuckGo, which blocks trackers and encrypts your connection. The app is available on the Google Play Store, the Apple App Store and through the Firefox web extension marketplace.
Other Tips & Resources
Here are some bonus cybersecurity tips and best practices to keep in mind as an activist participating in or leading a protest:
- Back up your phone before leaving to protest, just in case it gets lost, stolen or confiscated by police. It’s always more secure to store your backups on a hard drive, but if you have to do it through cloud services, make sure it’s encrypted. On an iPhone or Mac, you have to enable backup encryption through your settings, though iCloud automatically encrypts your backup. On an Android device, your backup is encrypted through your Google account password. Set up two-factor authentication for an added boost to your cybersecurity.
- Remove fingerprint and face ID on your phone. Biometric facial recognition services are easily bypassed if your phone is confiscated by police. All they have to do is point it toward your face or force your fingerprint onto the screen. Instead, you should opt for a secure password to unlock your device. Choose a unique code (not something like “1234”). You can disable face ID and change your passcode in your Android or iOS settings.
- Use cash: Mobile money transfer services like PayPal, Apple Pay, Google Pay and Venmo will retain your data. So always use cash for your transactions.
- Use a secure password for your phone and laptop/desktop. Check out our guide on creating a strong password for more information.
- Use an encrypted password safe/manager to store all of your passwords and generate new ones. For recommendations on which service to use, see our list of the top 5 secure password apps.
- Though this could be seen as extreme to some, you might want to consider getting a burner phone. Having a separate device only for protests is a great way to organize and communicate in real-time with other activists. Just make sure the phone isn’t tied to your real identity. Don’t log into social media apps with an account associated with your name. Use encrypted messaging apps like Signal, as suggested above.
- If your phone is stolen or lost, you should wipe your data remotely. For iPhones and iPads, you can do this through the Find My app; for Android devices, use the Find My Device service.
Know Your Rights
It’s important for activists to know their basic human rights when dealing with law enforcement officers. In the U.S., your rights to free and non-violent assembly and speech are protected under the First Amendment of the U.S. Constitution.
Under the First Amendment, you can…
- Assemble in a peaceful demonstration to speak and express your support or opposition to a subject.
- Speak about anything, no matter how favorable or unfavorable. Even the most unpopular opinions are protected under the First Amendment.
- Burn flags, as determined by a landmark Supreme Court ruling in 1989.
But, you can’t…
- Use “fighting words,” a type of reactionary speech that targets an individual and aims to incite violence.
- Engage in defamation, which involves knowingly making untrue statements about an individual, company, organization or other entity, damaging their reputation.
- Violate “time, place and manner” rules. For example, local ordinances may restrict loud noises in certain areas, foot traffic on busy streets or the size of signs carried by protestors. The exact limits and enforcement of these ordinances will depend on the town/city, state or region that implements them.
- Trespass on private property without an owner’s consent.
The Civil Liberties Defense Center has a helpful toolkit of human rights manuals for activists, immigrants and youth—read more about your rights here.
Note:
The bullet points above are meant to be a summary of the basic freedom of speech parameters outlined in the U.S. Constitution, not to be taken as legal advice. We suggest consulting a lawyer to learn more about your rights to protest in your jurisdiction.


