The best cloud security tools provide real-time analytics, comprehensive threat protection and compatibility with most of the cloud environments available today. This guide will present the best cloud security tools to use in an organization. Readers will learn how each tool meets the criteria for detail, cross-platform support and updated metrics. This guide will also explore frequently asked questions about cloud security in general and share practices to increase cloud security in an organization.
Cloud security refers to a collection of security measures that aim to protect cloud-based data, applications and infrastructure. These measures help safeguard company data from malware, hackers and unauthorized users. Cloud security tools come in many forms. Security information and event management platforms provide real-time data analysis of security alerts from all aspects of the cloud environment. Other cloud tools create zero-trust networks. Spam filters and endpoint-protecting tools such as antivirus software help secure the access points of cloud data.

Cloud security tools handle a wide range of functions. Cloud backups allow for data recovery in case of data loss. Various tools allow both providers and clients to limit access to sensitive data, usually through the use of encryption. Services such as virtual private networks protect data in transit from being read. Companies also use native cloud security tools for legal compliance to protect user information from being exploited.
The top 10 cloud security tools for 2023 are given below.
- Bitglass
- SpectralOps
- Security Code Scan
- Cato Networks
- Fugue
- XM Cyber: Attack-Centric Exposure Management
- Illumio Core
- Zerospam
- Rubrik
- Splunk Enterprise Security
Table of Contents
1. Bitglass
Bitglass is an all-in-one cloud-native security platform. The platform is a product of Forcepoint, an American software company based in Austin, Texas. Forcepoint has integrated Bitglass into the Forcepoint ONE platform.
The platform routes traffic locally and can secure data coming from any device through a secure web gateway (SWG). The SWG includes dynamic capabilities such as remote browser isolation, where users can perform tasks without having to compromise company networks.

The Forcepoint ONE platform is secure and trusted by thousands of customers worldwide. Companies working remotely can take advantage of the unique “Zero Trust Network Access” feature, which limits resources to only the people who require access. ZTNA detects risky behavior and takes action when breaches occur.
One disadvantage is difficulty in deployment. Deploying the platform may be tedious since multiple servers are needed for the various services. Pricing is not publicly available, but users can schedule a demo or request a quote on the Forcepoint website.
Bitglass is a great option amongst the various cloud security monitoring tools available. The tool stands out by providing security to all types of endpoints and giving real-time feedback on possible risky behavior.
2. SpectralOps
SpectralOps is a product solution held by Check Point Software. The platform allows users to continuously scan and monitor both known and unknown resources to prevent data breaches from occurring. Spectral was built by and for developers who feel comfortable using the command line features. The scanning technology is programming language agnostic and can support over 500 different stacks.

SpectralOps uses AI-backed technology to get extensive coverage and detect issues in source code. Developers can also integrate log shipping infrastructure into Spectral for added protection.
Spectral offers the ability to create custom detectors using a unique proprietary query language known as SPEQL. The language exposes parts of the Spectral engine in an easy-to-read syntax.

The platform integrates with all leading CI systems such as Jenkins and Azure. Clients can also allow Spectral to scan static builds for technologies such as Gatsby, Netlify and JAMStack.
A possible disadvantage for Spectral is there are cases where the detectors are aggressive and may lack customization options. SprectralOps should be secure since the platform is under Check Point, a company known to be a leader in data security management.
Pricing plans are not publicly available, but organizations can request a demo through the SpectralOps website.
Spectral’s advantages are extensive coverage and compatibility with various CI systems.
3. Security Code Scan
Security Code Scan is a real static analysis tool for .NET code. The analyzer detects various security vulnerability patterns in code. The tool can be installed as a Visual Studio extension or as a stand-alone runner.
Security Code Scan is a free and open-source project that is hosted on Github, which means any developer can contribute to or inspect the code. An open-source project with a history of contributions. Since the project is free, users do not need to worry about pricing to use the tool.

The tool supports continuous integration for both Github and Gitlab pipelines. SCS can also be used to analyze .NET and .NET Core projects in a background or during a build.
A disadvantage of installing the Visual Studio code extension is that there is a high chance that the extension will slow down the Visual Studio IDE.
Security Code Scan is among the more reliable cloud-based application security testing tools for security engineers and researchers who need to scan various software products often.
4. Cato Networks
Cato Networks is the world’s first Secure Access Service Edge (SASE) platform. SASE combines network security point solutions and Software-Defined Wide Area Networks into a single cloud-native service. The product is offered by Cato Networks Ltd., which aims to deliver easily deployable and secure networking architectures to organizations.

The Cato SASE cloud can be gradually deployed by organizations to replace or improve legacy architecture and solutions. Cato delivers end-to-end optimization for both WAN and cloud traffic.

Customers can use Cato’s security-as-a-service feature to inspect Internet traffic. Additional features include application-aware firewalls, secure web gateways and a cloud access security broker. Cato also provides a zero-trust network access solution for employees to securely connect to the network. The platform continuously inspects traffic to prevent malware propagation.
Cato also includes a self-service management application to control every service on the platform. Users can configure network and security policies and explore detailed analytics on various network and security events.
A disadvantage with the Cato Networks platform is that improvements can still be made on the integrations with identity providers. The platform supports popular identity platforms such as Office365 but not all identity providers can be used for multi-factor authentication.
Pricing plans are not publicly available, but users can apply for a live demo and a free trial through the Cato Networks website.
5. Fugue
Fugue is a cloud security platform that includes both a web UI and an API. The platform includes an open-source policy engine that allows organizations to add security and compliance consistently across the entire software development lifecycle. The platform is a product of Snyk, a developer security-focused software company founded in 2015.
The platform also includes a resource data engine that captures an entire system’s cloud resource configurations and attributes. Users can use the engine to maintain full knowledge of everything running in the company’s cloud environment. This feature contains a unique view of the current infrastructure visualized as an interactive map.
The Fugue engineering team actively maintains various open-source projects like Regula, a tool used for securing infrastructure as code. This platform is used by leading companies such as AT&T and SAP.

Fugue provides a free plan for developers or those who want to use Fugue for small projects. The plan includes one cloud account and one code repository. Fugue also offers an Enterprise plan with custom pricing. This plan allows for unlimited users, cloud accounts and code repositories. Upgrading to an enterprise plan gives users access to configurable dashboards and reports, as well as a role-based access control system for controlling permissions across a company. Pricing plans for the “Enterprise” option are not publicly available, but users can request a live demo on the website.
Note:
While the platform is filled with various features to help with compliance and cloud management, there are still some services that are not covered by Fugue. Users looking for a comprehensive AWS or Azure cloud security readiness tool might have to look elsewhere for some features.6. XM Cyber: Attack-Centric Exposure Management
XM Cyber is a cloud security platform that simulates attacks on business-critical data. Companies can use XM Cyber to discover vulnerabilities in cloud architecture and identify what assets are at risk from an attack. XM Cyber is now part of the Schwarz Group, a multinational retail group based in Germany.
The tool includes a breach and attack feature that discovers attack paths and critical assets that are in danger of being compromised. XM Cyber also uses advanced analytics to assess risk levels and determine risk reduction priorities.

Users can take advantage of automated and continuous risk reduction that is easy to deploy. XM Cyber also includes a unique feature where the platform connects clients to customer-focused professionals who can help optimize an organization’s cloud platforms.
XM Cyber can be seamlessly integrated into a company’s ecosystem in various areas, including cloud infrastructure, endpoint security and SOAR solution. The tool integrates with various other cloud platforms, including AWS, CrowdStrike Falcon and Microsoft 365 Defender.
The pricing of XM Cyber is not disclosed, but interested users can book a demo with the team.
While XM Cyber is excellent for breach and attack simulation, XM Cyber’s simulation approach to cyber risks makes the software one of the top cloud security tools available today.
7. Illumio Core
Illumio Core is a cloud security platform that makes zero trust segmentation easier for companies to achieve. Illumio is an American business data center and cloud security company founded in 2013.

A zero trust architecture involves separating various stages of interactions within an organization’s network and validating data transactions at each stage. This architecture enables organizations to control workloads and granular access in multi-cloud environments.

Companies can use Illumio Core to prevent ransomware and cyberattacks from compromising sensitive data. A real-time application dependency map allows users to see how each application interacts with another. The platform also automatically identifies core services in the cloud and implements zero trust segmentation to reduce risk.
The Explorer feature gives users the ability to search through a traffic database for historical data that can be used for auditing and compliance purposes. IT teams can easily use this tool to plan, troubleshoot and investigate historical traffic when needed.
Illumio has a 4.6-star rating at Gartner Peer Insights, which gives the tool credibility security-wise. Though prices are not indicated on the website, companies who want to try out Illumio Core can sign up for hands-on virtual labs led by Illumio experts.
8. Zerospam
Zerospam is a cloud email security and anti-spam solution that companies can use to prevent email-based threats. Zerospam is now part of the Hornetsecurity Group, which is a leading cloud email security provider founded in 2009.

These email threats include ransomware, malware, phishing, DoS attacks and other harmful attachments. Zerospam uses an AI-driven anti-spam engine that can quickly catch suspicious links and attachments.
Other features include an “Allow” and “Block” list, archiving, email filtering, whitelisting/blacklisting and access controls.

Zerospam can be securely integrated into an organization’s cloud infrastructure since the tool uses TLS encryption. This encryption protects the confidentiality of email messages and the privacy of email senders.
A downside to the service is that other spam filter vendors offer similar services for a lower price.
Pricing plans for Zerospam are not publicly available, but users can request a quote on the Hornetsecurity website.
Note:
Zerospam is best for large global clients and SMBs for integration with organization email systems. The tool can be used alongside Microsoft 365 to protect against infected and malicious Office documents.9. Rubrik
Rubrik, a cloud data management company based in Palo Alto, California, offers a cloud security platform. This platform uses a Zero Trust Data Security model to protect organizations from ransomware and operational failures. Rubrik aims to replace legacy backup and recovery products such as off-the-shelf file systems and traditional enterprise backup solutions. These systems are more vulnerable to ransomware attacks and are notoriously slow and limited in scope.
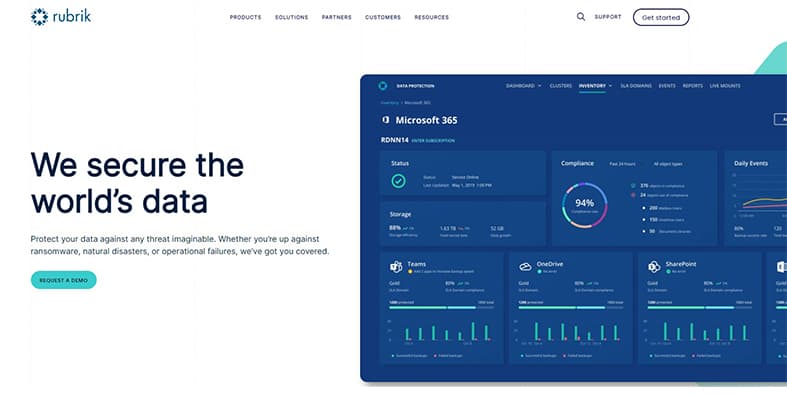
Users can take advantage of automated management across multiple cloud environments through a single interface. Rubrik includes an API that clients can use to accelerate service delivery. The website includes pre-built use cases and quick start guides so that users can easily get started with deploying.

The security platform will automatically archive and retire data based on user-defined retention policies. Since the application works in the cloud, Rubrik can scale up alongside other cloud workloads and applications.
Rubrik also offers a unique service known as the Ransomware Recovery Warranty. The warranty covers expenses related to the recovery of data in the event that data protected by Rubrik can no longer be recovered.
A downside is that there are still improvements to be made on how Rubrik deals with file management and data compression. Users have found Rubrik’s file management for archiving quite slow. Rubrik users have also noted that the compressed backups still take up more space than expected.
Plans and pricing are not indicated on the website, but users can attend a virtual camp training session to learn more about the Rubrik ecosystem.
10. Splunk Enterprise Security
Splunk is an analytics-driven cloud security information and event management tool (SIEM). The software is developed by Splunk Inc., an American software company based in San Francisco, California.
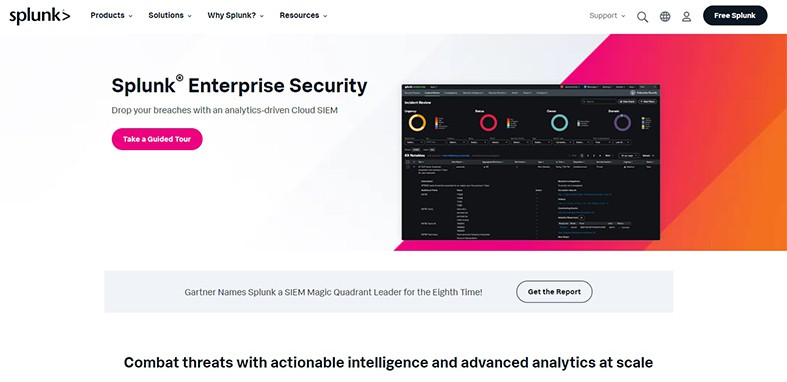
Splunk helps reduce the time needed to detect malicious threats in cloud environments. Splunk uses an analytics-driven approach to security which involves keeping track of data involving security events. Splunk offers event sequencing, risk scores, alert management and highly customizable dashboards and visualizations.

The platform offers end-to-end visibility for hybrid environments. Splunk can detect threats across multiple environments such as AWS, GCP and Microsoft Azure. This makes Splunk a preferable option among the hybrid cloud security tools available.
Customers can use Splunk’s unique Investigation Workbench to streamline investigations and incident responses. The Workbench centralizes security data so that users can see all relevant information concerning an incident. The feature eliminates the need to use multiple dashboards and screens to investigate.
A disadvantage of using Splunk is that the program can get relatively expensive for large data volumes. Pricing for the Splunk platform is available upon request, and a free trial is available as well. The free trial allows users to visualize 5GB/day of data in a Splunk-hosted cloud environment.
What Kind of Threats and Attacks are Risks for Cloud Platforms?
Tools that provide cloud security should handle threats and attacks that aim to compromise cloud platforms. Some security issues related to using cloud-based file management tools and security platforms are listed below.
- Malware: Malware attacks are a real threat to cloud applications. Unlike an architecture that relies on local servers, cloud platforms can be accessed more easily by outsiders. Cloud malware spreads quickly, and the potential damage increases as long as the threat is left undetected.
- Cloud-based Security Tools: help segment an organization’s network so that any potential malware threat only affects a small section of the entire network.
- Loss of Data: Data loss occurs when assets stored in the cloud can no longer be recovered. Cloud security platforms help clients regularly back up important data. A cloud-based SIEM is used to ensure that raw data has not been tampered with.
- Data Breach: Data breaches are a top security concern for companies that use cloud infrastructure. Members of an organization must have appropriate access levels where only relevant data is available. Cloud security tools can be used to simplify this into a role-based access control system.
- Insecure APIs: Malicious actors can take advantage of API vulnerabilities to perform DoS attacks and code injections. Some cloud security tools can scan the entire cloud environment and source code for potential vulnerabilities. A centralized cloud monitoring solution also helps keep track of which APIs are being called.
- Distributed Denial-of-Service Attack: A Distributed Denial-of-Service (DDoS) attack is a synchronized cyberattack where a single network is targeted by multiple systems that overwhelm the network with traffic, rendering the network inaccessible to the intended users. Given the wide scope, DDoS attacks are a major risk for cloud computing environments. Organizations should use cloud security tools to set up firewalls and intrusion detection systems to protect servers from possible DDoS attempts.
How Cloud Security Tools Provide Extra Security

The top cloud security tools provide protection against threats, assist in identity management and access controls and ensure the organization follows regulatory compliance.
Cloud encryption is used to transform plain text data into an unreadable format which is then stored in the cloud. This process gives the data additional protection against unauthorized users and will protect sensitive data if a breach were to occur.
There are two main encryption methods. Symmetric encryption is generally used for bulk data. The method is symmetric since the key for both encryption and decryption is the same.
Asymmetric encryption, on the other hand, has separate keys to encode and decode data. These keys are usually called public and private authentication keys. This method ensures that the data cannot be read unless a user has both the public key and personal token.
What are the Tips to Prevent Cloud Security Threats?
The best practices to prevent cloud security threats are given below.

- Encryption: Encryption allows data to be kept safe in the cloud. Encryption using multiple keys allows only the right people to be able to access sensitive data. Compliance measures may also require user data to be encrypted to maintain data privacy.
- Multi-factor Authentication: Malicious actors can use phishing methods and other techniques to try to log in to the cloud system. Multi-factor authentication allows the system to confirm a user’s identity through multiple pieces of evidence.
- Microsegmentation: Microsegmentation involves dividing an organization’s cloud network into different smaller zones. Separating technologies will minimize damage should a breach occur.
- Secure User Endpoints: Endpoints serve as access points to an organization’s cloud processes. These endpoints could be anything from a laptop or smartphone to an on-premise server. Endpoint security can be maintained by providing antivirus software, pop-up blocks and virtual private networks to all endpoint devices.
- Email Gateway and URL Filtering: Companies should also set up secure email gateways to prevent suspicious emails from propagating. A URL filter can also be implemented to prevent these devices from accessing suspicious links.

