Table of Contents
How Does a SOCKS5 Proxy Work?
The way a SOCKS5 proxy works is by using the SOCKS5 protocol to create a safe and secure link between the client and the proxy server. When a client requests access to a network resource, the request is passed to the proxy server, which makes the request on the client’s behalf. By having the proxy server act as an intermediary between the client and the network resource, the client can access the resource as though it were on the same local network.
By using authentication techniques, a SOCKS5 proxy ensures that only authorized users can connect to a distant server by redirecting data packets from a specified source through that server. SOCKS5 proxies are more versatile than other types of proxies, which can only re-route traffic from web browsers. Because of their adaptability, they’re not limited to web browsers but can communicate with a wide variety of programs. In addition, SOCKS5 proxy servers encrypt the client-proxy server connection, protecting users’ privacy and internet behavior. The proxy server can also assist users in evading internet restrictions and accessing banned content by hiding their IP address.
What are the Benefits of Using a SOCKS5 Proxy?
The benefits of a SOCKS5 proxy are:
1. Bypass Geo-Restrictions
A SOCKS5 proxy can help to bypass internet censorship, as the proxy server hides the user’s IP address and can access blocked content on behalf of the client. Using geo-blocking software can unfairly prevent some users from using online resources. An IP address is used to determine a user’s geographical location, and if the location isn’t authorized, you will be blocked at these digital boundaries. The SOCKS5 proxy, however, replaces the IP address with that of the proxy server, thereby increasing online user freedom and allowing unblocking geo-restricted content.
2. Compatibility with all traffic types
SOCKS5 proxies can be used with a wide range of applications and protocols and can be easily configured to work with different network settings. This makes them a flexible and versatile option for protecting your privacy and accessing network resources. Other proxies are solely designed to handle specific data types. For instance, HTTP proxies are incompatible with any protocol apart from HTTP and HTTPS. However, SOCKS5 proxies stand out from the crowd because of their limitless adaptability in terms of supported protocols, applications, and traffic types. Furthermore, unlike other proxies, SOCKS5 proxies can transport fewer data packets, which means better download speeds for P2P traffic. This means that utilizing a SOCKS5 proxy for any purpose will boost your security and anonymity.
3. Speed and Reliability
A SOCKS5 proxy can improve the performance of certain applications, such as torrent clients, by allowing them to access network resources more efficiently. SOCKS5 proxy servers do not modify data packet headers like some other proxies. As a result, SOCKS5 proxies are safer, as they are less likely to incorrectly identify or misdirect your traffic. SOCKS5 proxies are more efficient and faster than other proxy types since they cause fewer mistakes.
What are the Cons of Using a SOCKS5 Proxy?
The cons of using a SOCKS5 proxy:
1. Vulnerable to Man-in-the-Middle Attacks
A SOCKS5 proxy can make you vulnerable to MITM attacks (Man-in-the-Middle attacks) if the proxy server is not properly configured or is run by a malicious actor. In a MITM attack, the attacker intercepts the client and server communication and can access and manipulate the transmitted data. This can be a significant security risk, as the attacker can access sensitive information, such as login credentials or personal data.
This is important:
Selecting a reliable and trustworthy proxy service and double-checking the proxy server’s security are crucial steps in preventing man-in-the-middle attacks while utilizing a SOCKS5 proxy. You can use tools such as SSL/TLS scanning to check the encryption and authentication of the proxy server and to ensure that your connection is secure. Additionally, it is critical to be cautious when accessing sensitive information over the internet and to use strong passwords and other security measures to protect your data.2. Vulnerable to IP Address Eavesdropping
Using a SOCKS5 proxy to encrypt an internet connection and hide the IP address does not guarantee anonymity. A rogue proxy server can trace your online activities and identify you. IP address eavesdropping is a SOCKS5 proxy vulnerability. Choosing a reliable proxy service prevents IP address eavesdropping. Avoid free or untrustworthy proxy servers and use a service that encrypts your connection. Use a virtual private network (VPN) for more security and anonymity.
3. Lack of Encryption
Unencrypted data transmission is one potential drawback of using a SOCKS5 proxy. Ineffective encryption can occur, for instance, if the client and server employ dissimilar encryption techniques or utilize incompatible encryption keys. The data sent between the client and the server could be intercepted and decrypted by an adversary, exposing your online activities.
SOCKS5 Proxy Setup Info
Here’s how to set up a SOCKS5 proxy on Windows 10, 11, and Mac.
How to Set Up a SOCKS5 Proxy on Windows 10
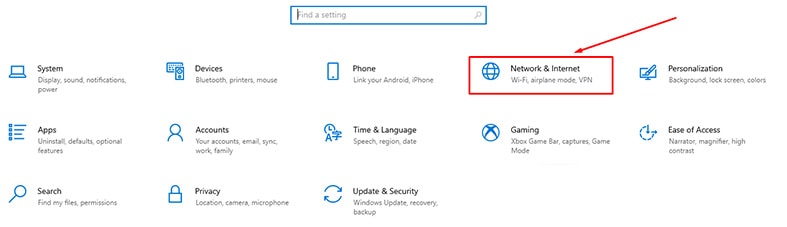
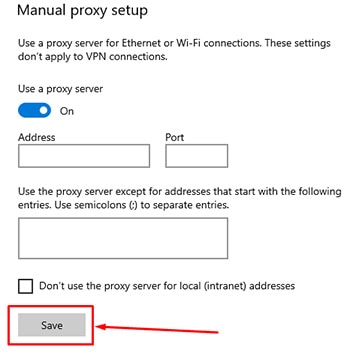
- Click on the menu icon and then go to settings.
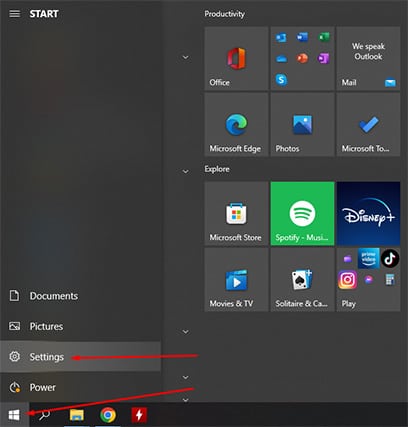
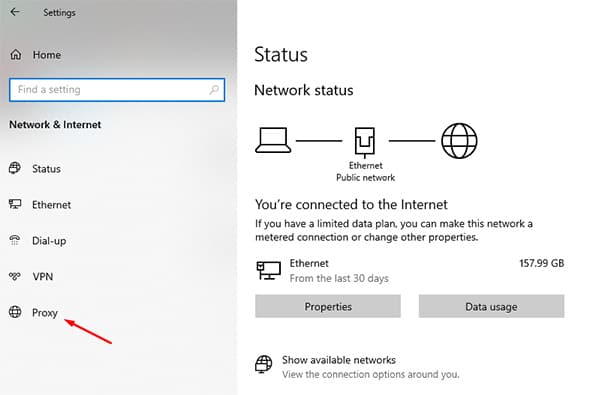
- On the settings page, head to Network and Internet, and from there, click on Proxy.
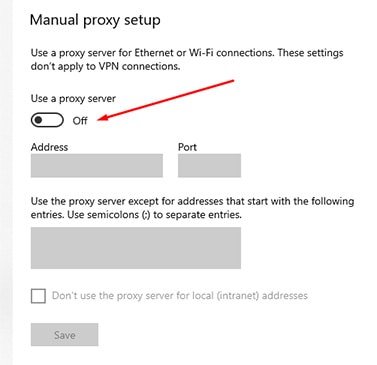
- Toggle the “On” button under “Manual proxy setup.”
- Fill in the blanks with information about your proxy server.
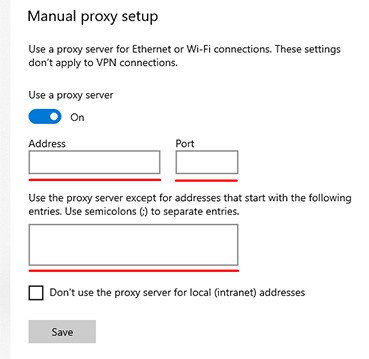
- Select “Save.”
How to Set Up a SOCKS5 Proxy on Windows 11
- Choose a reputable and trusted SOCKS5 proxy provider and sign up for their service. This will provide you with the proxy server details that you will need to configure your proxy settings, such as the server address and port number.
- Open the Windows Settings app and go to the Network & Internet section.
- Click on the Proxy tab on the left-hand side and then click on the button to add a new proxy.
- In the Add a proxy screen, select SOCKS5 as the proxy type and enter the server address and port number provided by your proxy provider.
- Enter any additional settings, such as a username and password, if your proxy provider requires them.
- Click on Save to apply the proxy settings.
- Test the proxy connection to make sure it is operating properly. You can do this by visiting a site that displays the IP address you are using and verifying that the IP address shown is the proxy server’s IP address and not your own.
How to Set Up a SOCKS5 Proxy on Mac
- Choose a proxy provider
- Sign up for a proxy account
- Open the “System Preferences” on your Mac, and go to the “Network” section.
- Select the “Advanced” button, and then go to the “Proxies” tab.
- Check the “SOCKS Proxy” box, and enter the proxy server details provided by your proxy provider.
- Test your proxy connection
- Use your proxy
SOCKS5 Proxy Vs. VPN?
While SOCKS5 is faster than a VPN, it lacks the privacy and encryption of a VPN. SOCKS5 proxies and VPNs share certain similarities. However, there are important distinctions between the two. SOCKS5, like most other proxies, will slightly slow down your connection and compromise the security of your data. If you use a reliable VPN, your data will be encrypted as it goes to the server of the VPN from your device, making it unreadable at any time. When using a VPN service, you can unblock geo-restricted content and hide the IP address you are using. However, you will do so at slower speeds than a SOCKS5 Proxy.
SOCKS5 Proxy Vs. HTTP Proxy?
SOCKS5 proxies are universally compatible with any type of traffic, while HTTP proxies can only decipher and work with HTTP and HTTPS websites. High-level proxies, such as HTTP proxies, are typically developed for a single protocol. As a result, you can expect faster connection speeds at the expense of security and flexibility. When it comes to traffic and applications, SOCKS proxies have no limits because they are low-level proxies.

Are There Free SOCKS5 Proxies?
Yes, there are. However, free socks5 proxies don’t enjoy the same capabilities as the premium ones. Examples of free socks5 proxies include:
- SOCKS5.me
- SOCKSProxy.org
- SOCKSList.net
What Are The Best SOCKS5 Proxies?
The best SOCKS5 proxies are dependable, secure, and provide fast connections. They are maintained by reliable hosts and set up to deliver robust encryption and shield user data in transit and at rest. Listed below are some examples of the best SOCKS5 proxies:

